Difference between revisions of "Azure IoT Hub Cloud Connection"
From Teltonika Networks Wiki
| (13 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
| + | <b>Azure IoT Hub</b> is an open and flexible cloud platform that supports open-source SDKs and multiple protocols. | ||
| + | |||
| + | __TOC__ | ||
| + | ==Introduction== | ||
| + | |||
| + | This article contains instructions on how to configure a RUT router in order to connect to the Azure IoT Hub.<br> | ||
{{Template:Networking_rutx_manual_fw_disclosure | {{Template:Networking_rutx_manual_fw_disclosure | ||
| Line 4: | Line 10: | ||
}} | }} | ||
| − | |||
| − | |||
| − | |||
==Prerequisites== | ==Prerequisites== | ||
You will need: | You will need: | ||
| − | *A | + | *A router from the RUTX09 or RUTX11 |
| − | *An Azure IoT Hub account | + | *An Azure IoT Hub account |
==Azure account creation== | ==Azure account creation== | ||
| Line 84: | Line 87: | ||
</ul> | </ul> | ||
| − | ==Configuring Azure IoT Hub | + | ==Configuring RUTX Azure IoT Hub== |
| − | |||
<ul> | <ul> | ||
| − | <li> | + | <li>First open router WebUI, go to '''System > Package Manager''' and install Azure IoT Hub package </li> |
| − | [[File: | + | [[File:Networking_rutx_configuration_examples_package_manager_v1.png|border|class=tlt-border]] |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <li>Now navigate to ''' Services > Cloud solutions > Azure IoT Hub''' </li> | |
| + | <div>1. Select Enable '''Azure IoT Hub monitoring'''</div> | ||
| + | <div>2. Paste previously copied Connection String (For this test we leave other values as default)</div> | ||
| + | <div>3. Select what kind of information you want to send to Azure IoT Hub</div> | ||
| + | <div>4. Press '''Save''' </div> | ||
| + | [[File:Networking_rutx_configuration_examples_azure_iot_hub_v1.png|border|class=tlt-border]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</ul> | </ul> | ||
| − | ==== | + | ==Checking if Data reaches Azure IoT Hub== |
| − | |||
| − | |||
<ul> | <ul> | ||
| − | <div> | + | <li>From router side, connect to it with CLI or SSH client and write in command '''azure_iothub''' and press Enter </li> |
| − | + | <div>- You should get answer that looks something like that, depending on what information you chose to send. </div> | |
| − | < | + | [[File:Azure19_RUTX.png|border|class=tlt-border]] |
| − | < | + | <li>From Azure IoT Hub side you can check if it receives data. Go to IoT Hub that you created previously. Select '''Overview''', there you can see: |
| − | < | + | </li> |
| + | <div>1. How many devices are connected to hub, and how many messages it sent during chosen period of time.</div> | ||
| + | <div>2. Device to cloud messages, that your router is sending.</div><br> | ||
| + | <div>It should look something like that if IoT Hub is receiving data. </div> | ||
| + | [[File:Azure20_RUTX.png|border|class=tlt-border|800px]] | ||
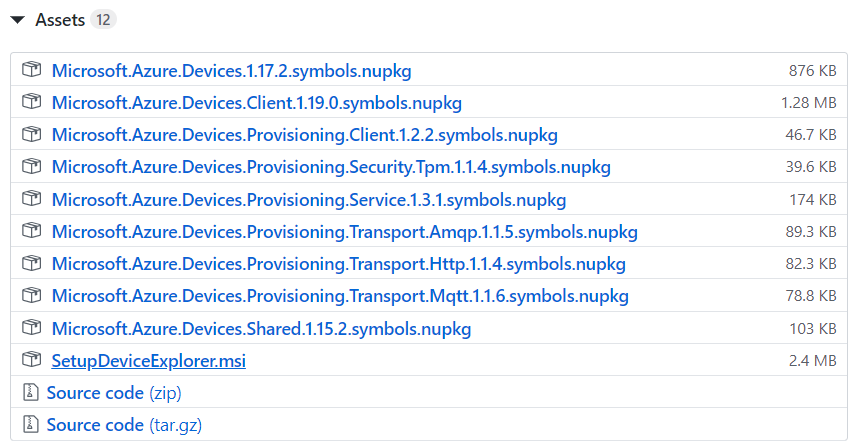
| + | <li>To capture logs you will need '''Device Explorer''' for IoT Hub Devices.</li> | ||
| + | <div>For Windows you can get here: https://github.com/Azure/azure-iot-sdk-csharp/releases/tag/2019-1-4 </div><br> | ||
| + | <div>Scroll down to Assets, download and install '''SetupDeviceExplorer.msi''' </div> | ||
| + | [[File:Azure21.png|border|class=tlt-border]] | ||
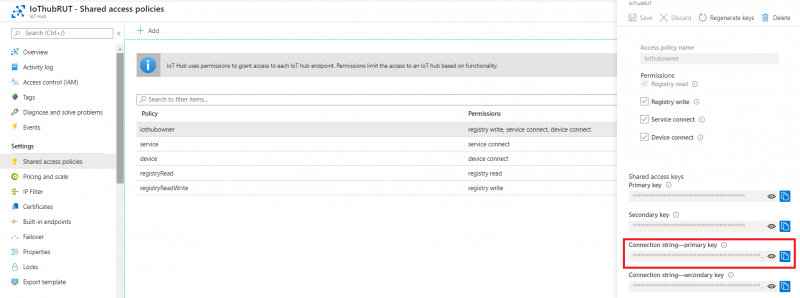
| + | <li>Now you will need connection string of yours Azure IoT Hub, Not device. Navigate to IoT hub in your browser, then:</li> | ||
| + | <div>1. Click '''Shared access policies'''</div> | ||
| + | <div>2. Next choose '''iothubowner'''</div> | ||
| + | <div>3. And copy '''Connection string – primary key'''</div> | ||
| + | [[File:Azure22-1_RUTX.png|border|class=tlt-border|800px]] | ||
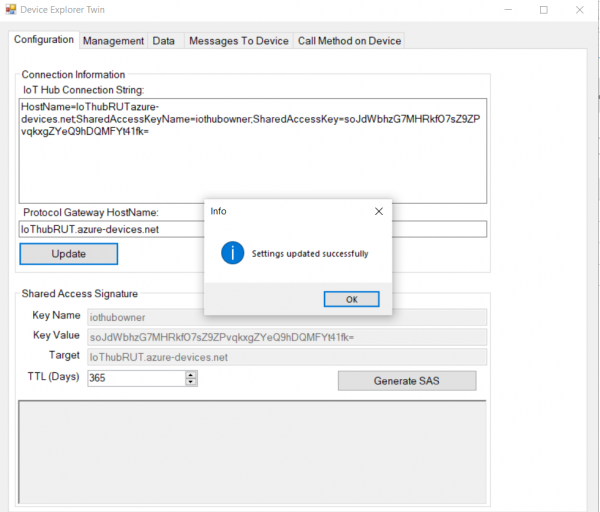
| − | + | <li>After that go back to Device Explorer: </li> | |
| + | <div>1. In Configuration tab paste in Connection string that you just copied</div> | ||
| + | <div>2. Copy HostName part from connection string and paste it in '''Protocol Gateway HostName'''</div> | ||
| + | <div>3. Click '''Update''' </div> | ||
| + | [[File:Azure23_RUTX.png|border|class=tlt-border|600px]] | ||
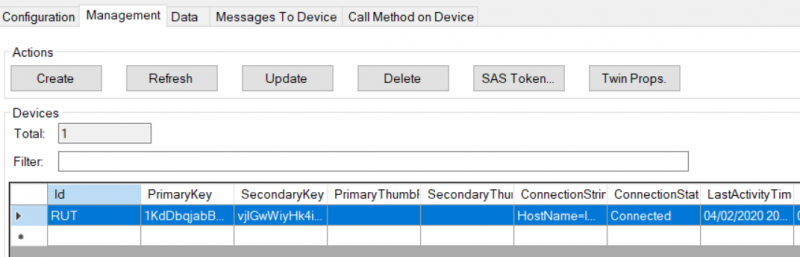
| − | + | <li>Open Management tab </li> | |
| − | + | <div>1. Click Update </div> | |
| − | + | <div>2. You should see your device in the list below and '''Connection state''' </div> | |
| − | + | [[File:Azure24_RUTX.png|border|class=tlt-border|800px]] | |
| − | |||
| − | [[File: | ||
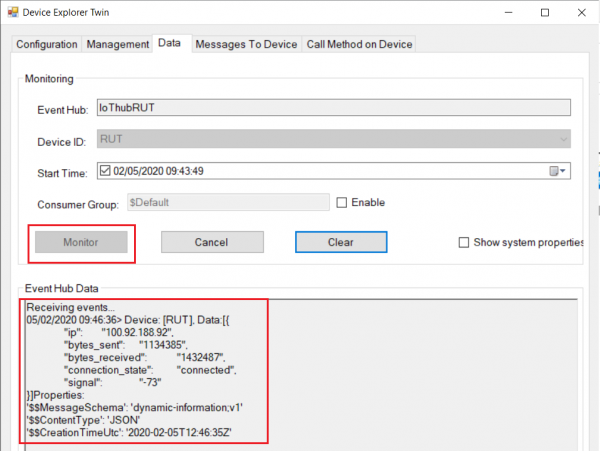
| − | + | <li>Go to Data tab</li> | |
| − | </ | + | <div>1. Click monitor, and wait for '''Event Hub Data''' to update (Depends on yours chosen interval)</div> |
| − | <div> | + | <div>2. Messages like this should start appearing. </div> |
| − | + | [[File:Azure25_RUTX.png|border|class=tlt-border|600px]] | |
| − | [[File: | ||
| − | |||
| − | + | ==Setting router to Forward MQTT messages/commands to Azure IoT Hub== | |
| + | <div>First you will need MQTT broker to subscribe to, for testing purposes we will set MQTT Broker in same router, and will use PC from LAN to sent MQTT messages.</div> | ||
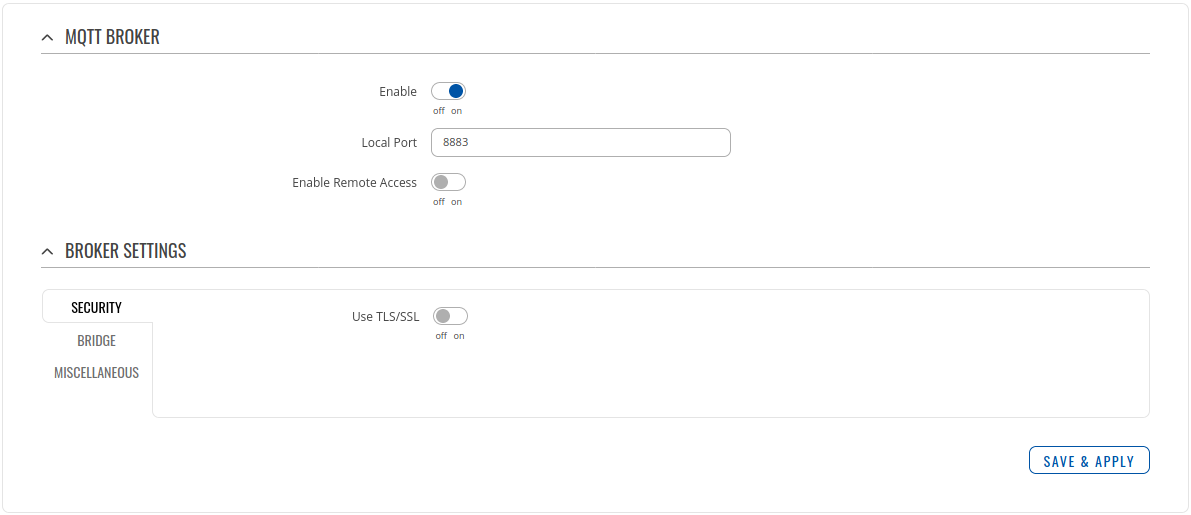
| − | + | <li>Go to Services > MQTT > Broker </li> | |
| − | [[File: | + | <div>1. Click '''Enable'''</div> |
| + | <div>2. Use same port in MQTT Broker and Azure IoT Hub settings.</div> | ||
| + | <div>3. Press '''Save'''</div> | ||
| + | [[File:Azure26-1_RUTX.png]] | ||
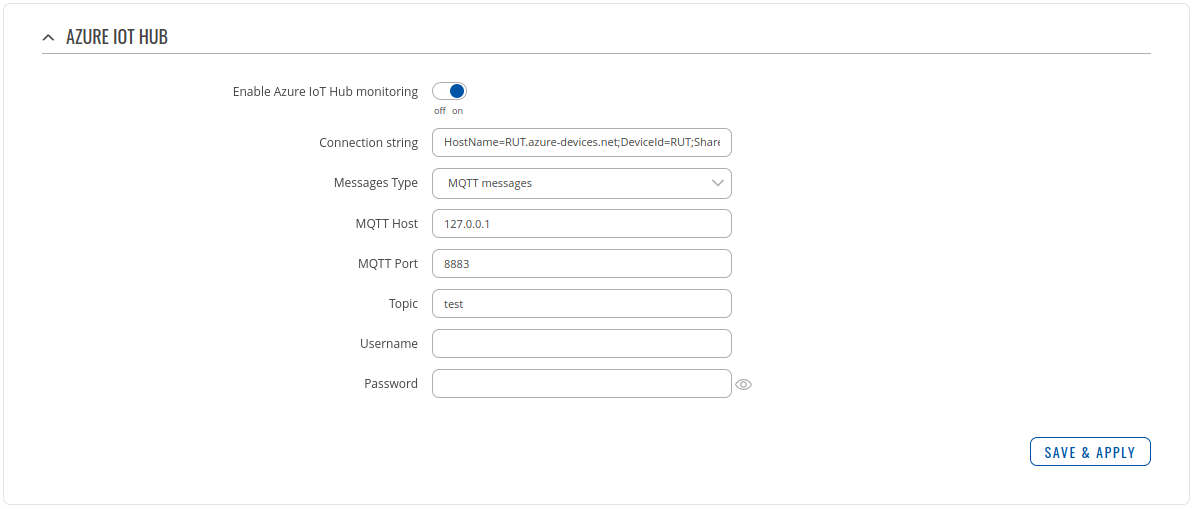
| − | + | <li>Go to '''Services > Cloud solutions > Azure IoT Hub'''</li> | |
| − | + | <div>1. Enable monitoring </div> | |
| − | 4. | + | <div>2. Use same Connection string as before (GSM values configuration) </div> |
| − | + | <div>3. Messages Type choose '''MQTT messages''' </div> | |
| − | + | <div>4. Enter MQTT Host address, we are using 127.0.0.1 since our broker is set up on same router.</div> | |
| + | <div>5. Port '''Same as MQTT Broker'''</div> | ||
| + | <div>6. And Topic under which router will subscribe to MQTT Broker</div> | ||
| + | <div>7. Press '''Save''', we will not need username or password.</div> | ||
| + | [[File:Azure27-2_RUTX.png]] | ||
| − | + | </ul> | |
| − | + | ==Checking if MQTT messages are being forwarded to Azure IoT Hub== | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | ===Linux=== | ||
<ul> | <ul> | ||
| − | < | + | <div>Connect to router with SSH, in logread you should see Router establishing connection to Azure IoT Hub: </div> |
| − | <li> | + | [[File:Azure27-1.png|border|class=tlt-border]] |
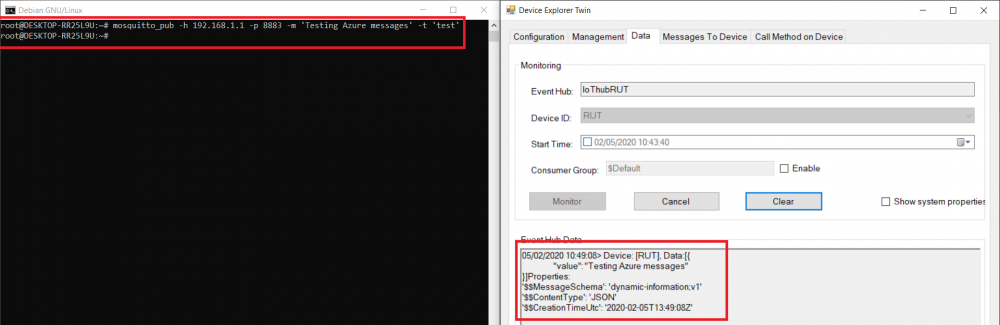
| − | < | + | <li>Open terminal and publish to MQTT Broker message with previously chosen topic.<br> |
| + | For our example we are using example: '''mosquito_pub -h 192.168.1.1 -p 8883 -m ‘testing Azure MQTT messages’ -t test''' </li> | ||
| + | <br><div>If everything was configured correctly in Device Explorer Data tab you should receive message like: </div> | ||
| + | [[File:Azure28_RUTX.png|border|class=tlt-border|1000px]] | ||
| + | <div>This means our router Forwards MQTT messages to Azure IoT Hub. </div> | ||
</ul> | </ul> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===Windows=== | |
| − | + | <ul> | |
| − | == | + | <li>Install a MQTT client software to do the test, for this example we used MQTT.fx</li> |
| − | + | <div>1. Setup your Router IP Address</div> | |
| − | + | <div>2. Use the '''same broker port'''</div> | |
| − | + | <div>3. Paste your '''Connection string – primary key''' and click '''Apply'''</div> | |
| − | + | [[File:Azure29-1_RUTX.png|border|class=tlt-border|800px]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <div>1. Connect to the server broker</div> | |
| + | <div>2. Use the created topic. For this example '''test'''</div> | ||
| + | <div>3. Send a message</div> | ||
| + | [[File:Azure30_RUTX.png|border|class=tlt-border|1000px]] | ||
| − | + | <li>If you did everything right this message will be shown in the device explorer</li> | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | <li> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</ul> | </ul> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Revision as of 12:33, 20 February 2020
Azure IoT Hub is an open and flexible cloud platform that supports open-source SDKs and multiple protocols.
Introduction
This article contains instructions on how to configure a RUT router in order to connect to the Azure IoT Hub.
The information in this page is updated in accordance with the RUTX_R_00.02.01.1 firmware version.
Prerequisites
You will need:
- A router from the RUTX09 or RUTX11
- An Azure IoT Hub account
Azure account creation
Visit https://azure.microsoft.com/en-us/ and create an account that will suit your needs, for testing purposes we will be using free Azure account.
Managing Azure services
- First you will want to create a Resource group for easier management of resources that you will add later. In Microsoft Azure home page.
- In new window, select Add
- And then finish creating yours Resource group Select your subscription, we are using Free Trial for this test.
- Name your group
- Finally, choose server location for meta data. We will choose (South America) Brazil South and will use it during test where available.
- At this moment we will skip adding Tags since we will be able to do that later if needed, so simply press Review + create at the bottom of screen and then click Create to finish setup.
- You will be redirected to Homepage, then click on Resource groups. You should see yours newly created group, select it, and press Add.
- Select Internet of Things or simply search IoT Hub and press Create.
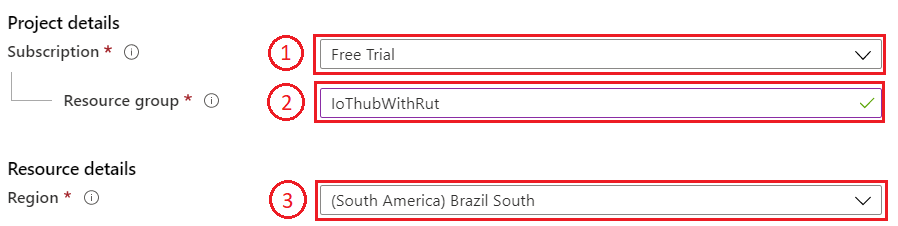
- We leave default subscription and resource group and choose:
1. Region – (South America) Brazil South as before2. Create a name for IoT Hub3. Then go to Size and scale tab
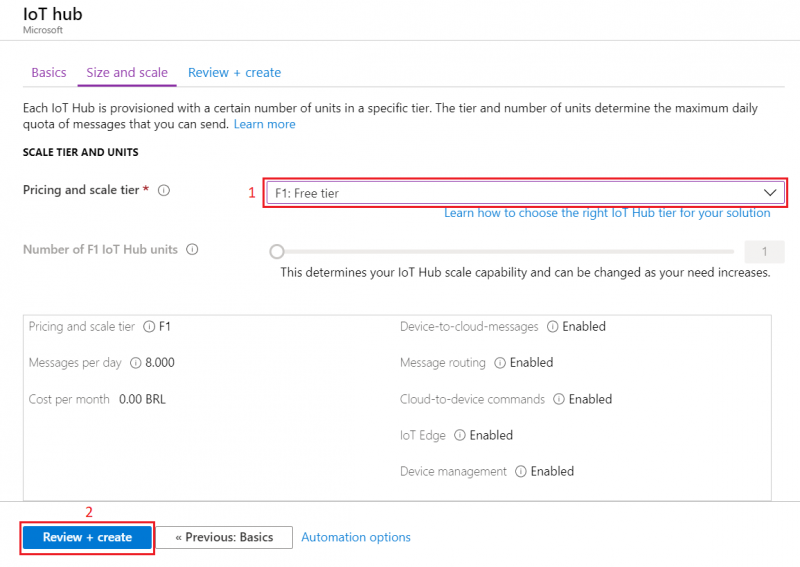
- For testing purposes, we are using F1: Free tier
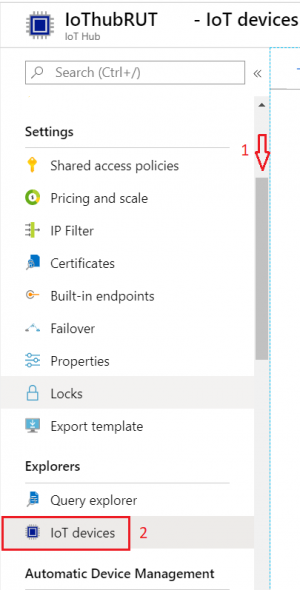
- Inside IoT Hub list:
Scroll down to Explorers and select IoT devices
- Press New
-
In new device creation1. Enter Device ID2. Leave everything else on default and press Save
- After you finish creation, you will be redirected back to IoT devices select yours newly created Device ID
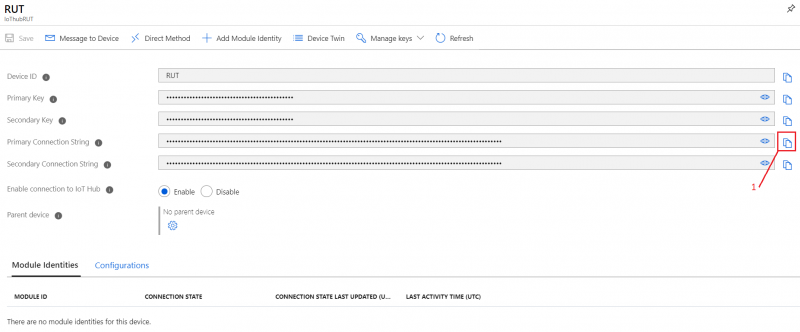
- In your device window you will find information needed to connect RUT devices to Azure IoT Hub.
- Select Resource groups
If it is not in very first page, click More services and locate it there.
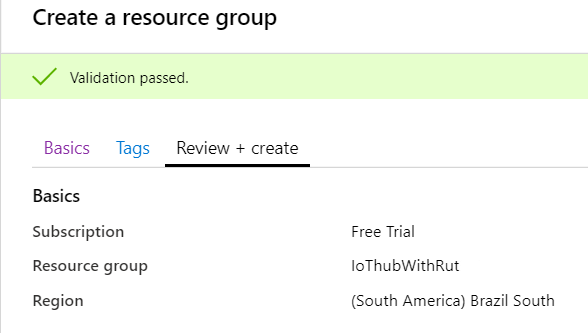
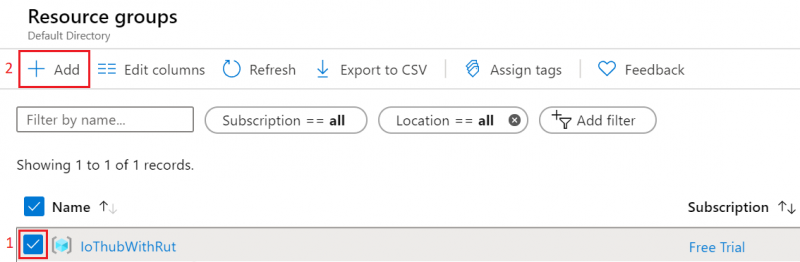
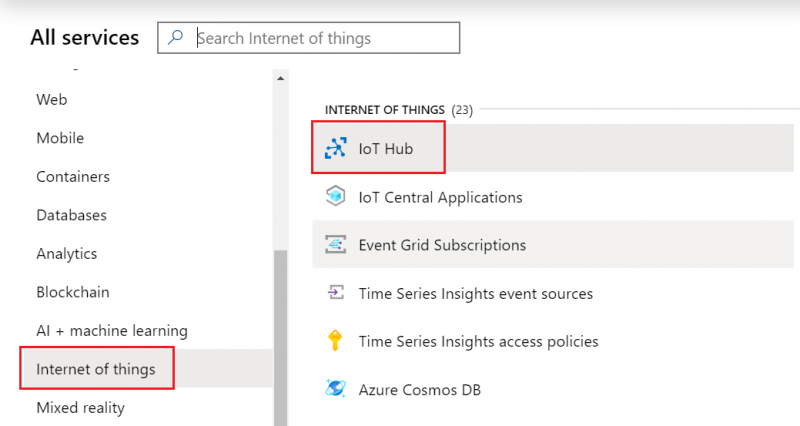
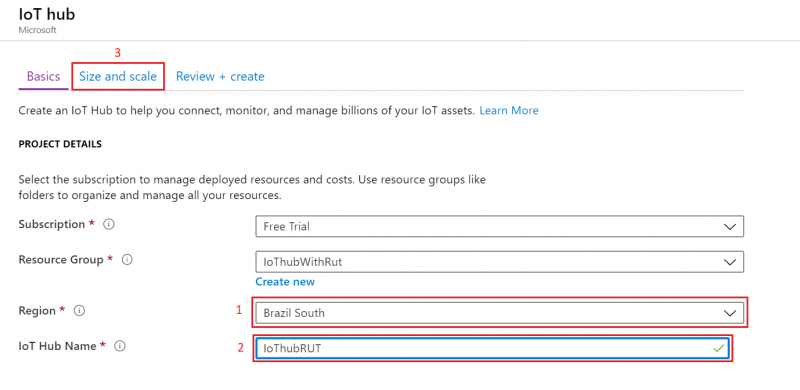
At the bottom of the screen Review + create
And finally, Click on >> Create
Note: Wait until resource deploys and press Go to Resources
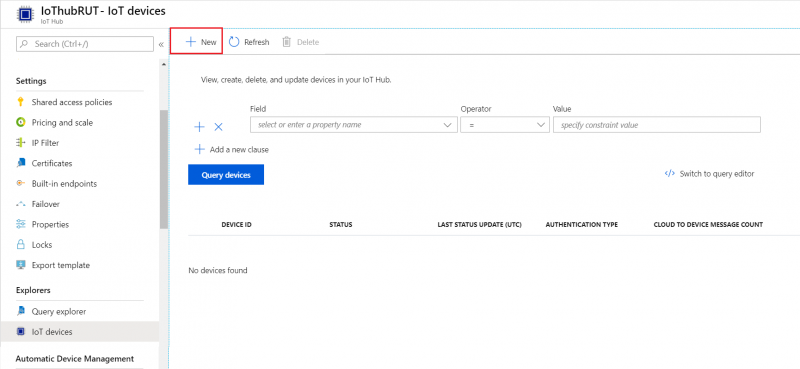
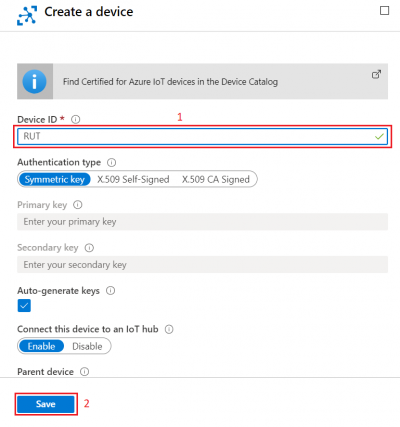
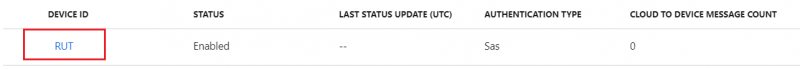
For now, we will only need connection string. Copy Primary Connection string by pressing copy icon next to it.
Configuring RUTX Azure IoT Hub
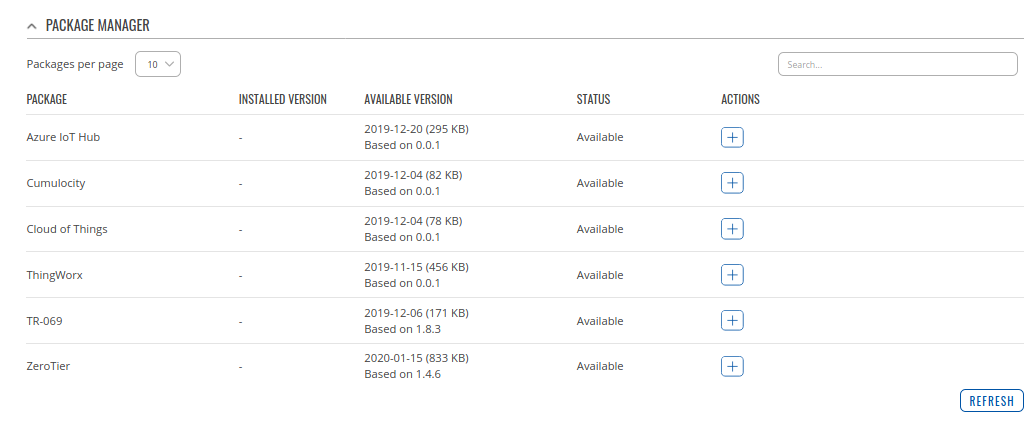
- First open router WebUI, go to System > Package Manager and install Azure IoT Hub package
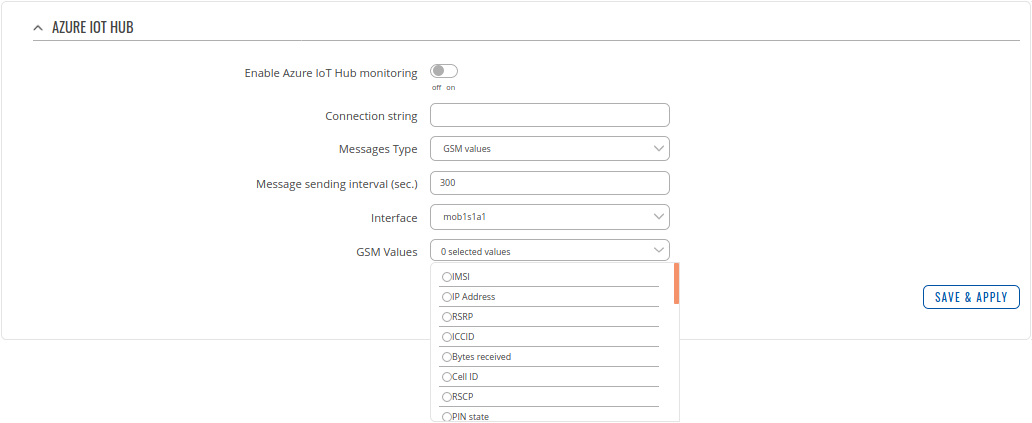
- Now navigate to Services > Cloud solutions > Azure IoT Hub
1. Select Enable Azure IoT Hub monitoring
2. Paste previously copied Connection String (For this test we leave other values as default)
3. Select what kind of information you want to send to Azure IoT Hub
4. Press Save
Checking if Data reaches Azure IoT Hub
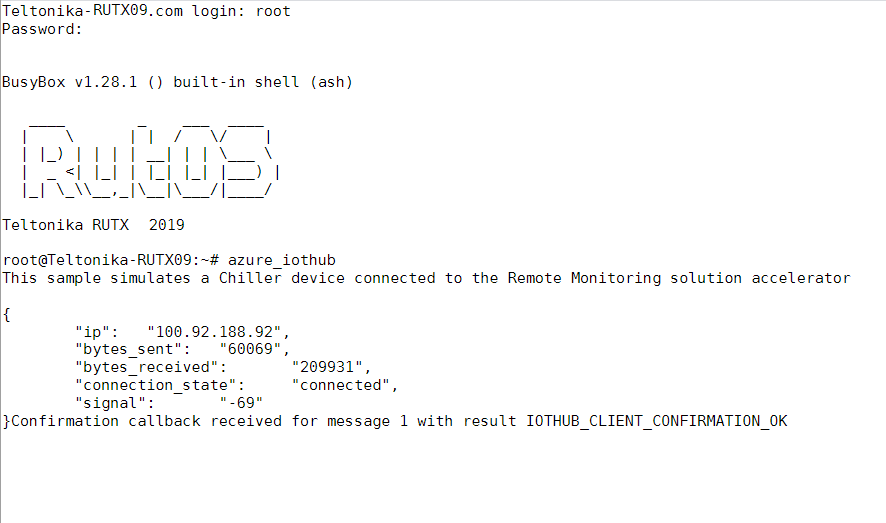
- From router side, connect to it with CLI or SSH client and write in command azure_iothub and press Enter
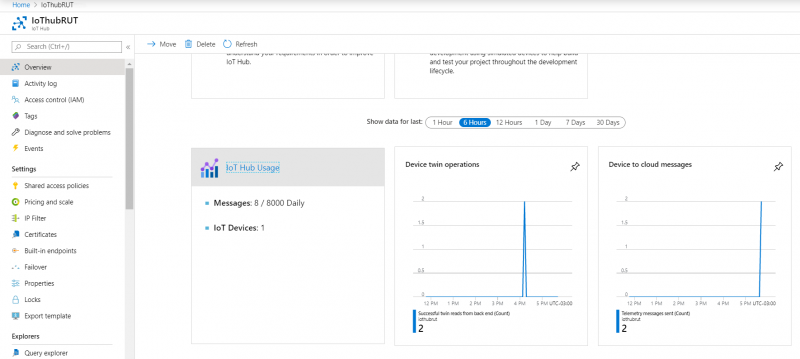
- From Azure IoT Hub side you can check if it receives data. Go to IoT Hub that you created previously. Select Overview, there you can see:
- To capture logs you will need Device Explorer for IoT Hub Devices.
- Now you will need connection string of yours Azure IoT Hub, Not device. Navigate to IoT hub in your browser, then:
- After that go back to Device Explorer:
- Open Management tab
- Go to Data tab
- Go to Services > MQTT > Broker
- Go to Services > Cloud solutions > Azure IoT Hub
- You should get answer that looks something like that, depending on what information you chose to send.
1. How many devices are connected to hub, and how many messages it sent during chosen period of time.
2. Device to cloud messages, that your router is sending.
It should look something like that if IoT Hub is receiving data.
For Windows you can get here: https://github.com/Azure/azure-iot-sdk-csharp/releases/tag/2019-1-4
Scroll down to Assets, download and install SetupDeviceExplorer.msi
1. Click Shared access policies
2. Next choose iothubowner
3. And copy Connection string – primary key
1. In Configuration tab paste in Connection string that you just copied
2. Copy HostName part from connection string and paste it in Protocol Gateway HostName
3. Click Update
1. Click Update
2. You should see your device in the list below and Connection state
1. Click monitor, and wait for Event Hub Data to update (Depends on yours chosen interval)
2. Messages like this should start appearing.
Setting router to Forward MQTT messages/commands to Azure IoT Hub
First you will need MQTT broker to subscribe to, for testing purposes we will set MQTT Broker in same router, and will use PC from LAN to sent MQTT messages.
1. Click Enable
2. Use same port in MQTT Broker and Azure IoT Hub settings.
3. Press Save
1. Enable monitoring
2. Use same Connection string as before (GSM values configuration)
3. Messages Type choose MQTT messages
4. Enter MQTT Host address, we are using 127.0.0.1 since our broker is set up on same router.
5. Port Same as MQTT Broker
6. And Topic under which router will subscribe to MQTT Broker
7. Press Save, we will not need username or password.
Checking if MQTT messages are being forwarded to Azure IoT Hub
Linux
- Open terminal and publish to MQTT Broker message with previously chosen topic.
For our example we are using example: mosquito_pub -h 192.168.1.1 -p 8883 -m ‘testing Azure MQTT messages’ -t test
Connect to router with SSH, in logread you should see Router establishing connection to Azure IoT Hub:
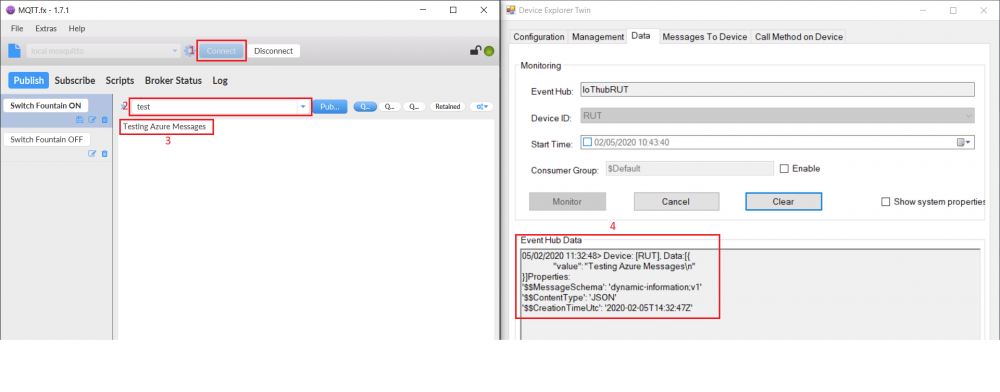
If everything was configured correctly in Device Explorer Data tab you should receive message like:
This means our router Forwards MQTT messages to Azure IoT Hub.
Windows
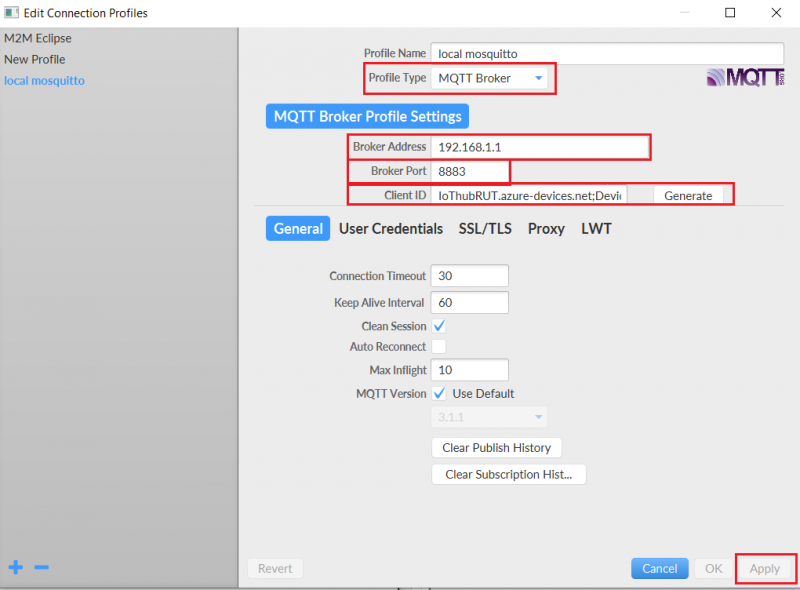
- Install a MQTT client software to do the test, for this example we used MQTT.fx
- If you did everything right this message will be shown in the device explorer
1. Setup your Router IP Address
2. Use the same broker port
3. Paste your Connection string – primary key and click Apply
1. Connect to the server broker
2. Use the created topic. For this example test
3. Send a message