OpenVPN configuration examples (Legacy Firmware): Difference between revisions
No edit summary |
No edit summary |
||
| (44 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
'''OpenVPN''' is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. | |||
==Summary== | |||
This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our '''[[VPN#OpenVPN|VPN manual page]]'''. | This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our '''[[VPN#OpenVPN|VPN manual page]]'''. | ||
| Line 7: | Line 7: | ||
==OpenVPN configuration type== | ==OpenVPN configuration type== | ||
Before configuring anything you should first know what type of OpenVPN connection suits your needs the best. The key things to be considered here are the type of connection ('''TUN''' ('''tunnel''') or '''TAP''' ('''bridged''')), the data transfer protocol ('''User Datagram Protocol''' ('''UDP''') or '''Transmission Control Protocol''' ('''TCP''')) and authentication | Before configuring anything you should first know what type of OpenVPN connection suits your needs the best. The key things to be considered here are the type of connection ('''TUN''' ('''tunnel''') or '''TAP''' ('''bridged''')), the data transfer protocol ('''User Datagram Protocol''' ('''UDP''') or '''Transmission Control Protocol''' ('''TCP''')) and authentication ('''TLS''' or '''Static key'''). Here is a short overview of the differences: | ||
*Type | * Type | ||
**TUN (tunnel) - simulates a network layer device and it operates with layer 3 packets like IP packets. TUN is used for routing and connecting | ** TUN (tunnel) - simulates a network layer device and it operates with layer 3 packets like IP packets. TUN is used for routing and connecting multiple clients to a single server. | ||
**TAP (bridged) - simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TAP is used for creating a network bridge between '''two''' Ethernet segments in different locations. | ** TAP (bridged) - simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TAP is used for creating a network bridge between '''two''' Ethernet segments in different locations. | ||
*Protocol | * Protocol | ||
**UDP - is used by apps to deliver a faster stream of information by doing away with error-checking. | ** UDP - is used by apps to deliver a faster stream of information by doing away with error-checking. | ||
**TCP - a suite of protocols used by devices to communicate over the Internet and most local networks. It provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network. | ** TCP - a suite of protocols used by devices to communicate over the Internet and most local networks. It provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network. | ||
*Authentication | * Authentication | ||
**TLS - uses SSL/TLS + certificates for authentication and key exchange. | ** TLS - uses SSL/TLS + certificates for authentication and key exchange. | ||
**Static key - uses a pre-shared Static key. Can only be used between two peers. | ** Static key - uses a pre-shared Static key. Can only be used between two peers. | ||
An overview of most of these types is provided in this article. Concerning TCP vs UDP, we will be using UDP for all examples. Choosing between TCP and UDP doesn't affect the rest of the configuration, so you can still follow the given examples no matter which protocol you are using. Simply choose the one that suits your purposes. | |||
==TLS Authentication== | ==TLS Authentication== | ||
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the '''TLS''' Authentication method on | This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the '''TLS''' Authentication method on RUT routers. | ||
===Generating TLS certificates/keys=== | ===Generating TLS certificates/keys=== | ||
| Line 31: | Line 31: | ||
A connection that uses TLS requires multiple certificates and keys for authentication: | A connection that uses TLS requires multiple certificates and keys for authentication: | ||
* | * Server | ||
**The root certificate file ( | ** The root certificate file (Cetificate Authority) | ||
**Server certificate | ** Server certificate | ||
**Server key | ** Server key | ||
**Diffie Hellman Parameters | ** Diffie Hellman Parameters | ||
* | * Client | ||
**The root certificate file ( | ** The root certificate file (Cetificate Authority) | ||
**Client certificate | ** Client certificate | ||
**Client key | ** Client key | ||
Detailed instruction on how to obtain these files can be found '''[[How_to_generate_TLS_certifates%3F|here]]'''. | |||
Once you have all the required files, continue following this section of the guide. | |||
===Configuration=== | ===Configuration=== | ||
| Line 79: | Line 79: | ||
If you are using a Linux-based OS, extracting files from the router is simple. Just go to the directory on your PC where you want to relocate the files, right click anywhere and choose the '''Open in Terminal''' option. In the Terminal command line use the '''Secure Copy''' ('''scp''') command to copy the files from the router. The full command should look something like this: | If you are using a Linux-based OS, extracting files from the router is simple. Just go to the directory on your PC where you want to relocate the files, right click anywhere and choose the '''Open in Terminal''' option. In the Terminal command line use the '''Secure Copy''' ('''scp''') command to copy the files from the router. The full command should look something like this: | ||
$ scp [email protected]:/etc/ | $ scp [email protected]:/etc/esy-rsa/keys/static.key ./ | ||
The '''[email protected]:/etc/easy-rsa/keys/static.key''' specifies the path to where the Static key is located (replace the IP address with your router's LAN IP); the '''./''' denotes that you want to copy the contents to the directory you are in at the moment. | The '''[email protected]:/etc/easy-rsa/keys/static.key''' specifies the path to where the Static key is located (replace the IP address with your router's LAN IP); the '''./''' denotes that you want to copy the contents to the directory you are in at the moment. | ||
If you are using Windows, you can copy files from the router using '''WinSCP''', an Open source freeware SFTP, SCP and FTP client for Windows OS. Use the same login information with WinSCP as with CLI or SSH. Once you've connected to the router with WinSCP, copying the files should be simple enough: just relocate to directory where you generated the key, select the Static key file and drag it to directory on your PC where you would like to store it. | If you are using Windows, you can copy files from the router using '''WinSCP''', an Open source freeware SFTP, SCP and FTP client for Windows OS. Use the same login information with WinSCP as with CLI or SSH. Once you've connected to the router with WinSCP, copying the files should be simple enough: just relocate to directory where you generated the key, select the Static key file and drag it to directory on your PC where you would like to store it. | ||
====On a Linux PC==== | ====On a Linux PC==== | ||
| Line 112: | Line 110: | ||
===Configuration=== | ===Configuration=== | ||
---- | ---- | ||
TAP is used for creating a network bridge between Ethernet segments in different locations. For this example we will be creating a TAP (bridged) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: '''RUT1''' ('''Server'''; LAN IP: '''192.168.1.1'''; WAN (Public static) IP: '''193.186.223.42''') and '''RUT2''' ('''Client'''; LAN IP: '''192.168.1.2'''); the two routers will be connected via OpenVPN. | TAP is used for creating a network bridge between two Ethernet segments in different locations. For this example we will be creating a TAP (bridged) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: '''RUT1''' ('''Server'''; LAN IP: '''192.168.1.1'''; WAN (Public static) IP: '''193.186.223.42''') and '''RUT2''' ('''Client'''; LAN IP: '''192.168.1.2'''); the two routers will be connected via OpenVPN. | ||
[[File:Openvpn tap example.png]] | [[File:Openvpn tap example.png]] | ||
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). | To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). The most important aspect of a TAP configuration is that it just bridges two network segments and '''doesn't create a different virtual network'''. Therefore, as in the example provided above, the routers have to be in the '''same subnet''' (192.168.1.0 in this case). While making sure of that, don't forget that the routers can't have the same IP address, just the same subnet (for example, if both routers have the LAN IP 192.168.1.1, the connection won't work; if one has, for example, 192.168.1.1 and the other 192.168.1.100, then the connection will work). | ||
For this example we used TLS Authentication. If you want to use a different Authentication method, refer to the relevant section of this article. The authentication configuration will not be different because of the chosen OpenVPN type (TUN or TAP). | For this example we used TLS Authentication. If you want to use a different Authentication method, refer to the relevant section of this article. The authentication configuration will not be different because of the chosen OpenVPN type (TUN or TAP). | ||
| Line 124: | Line 122: | ||
==Testing an OpenVPN connection== | ==Testing an OpenVPN connection== | ||
The most important thing after configuration is making sure that the newly established connection works. You can check the status of | The most important thing after configuration is making sure that the newly established connection works. You can check the status of the OpenVPN vonnection in the '''Status → Network → OpenVPN''' page: | ||
[[File:Openvpn connection test 2.png]] | [[File:Openvpn connection test 2.png]] | ||
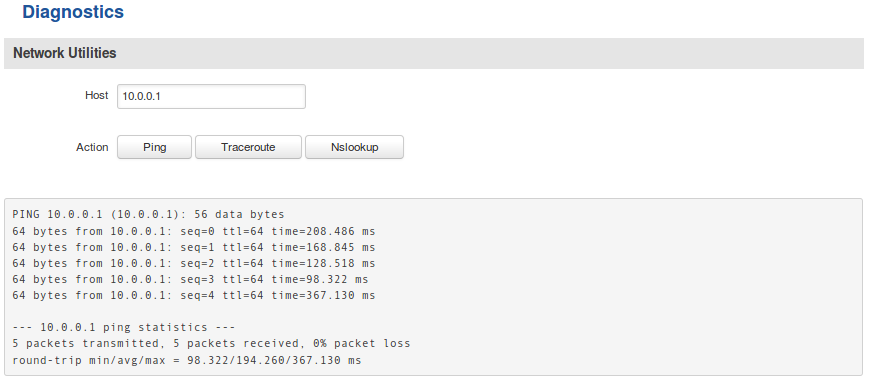
Another method of testing pinging the other instance's virtual IP address. You can send ping packets via CLI, SSH or from the ''' | Another method of testing pinging the other instance's virtual IP address. You can send ping packets via CLI, SSH or from the '''System → Administration → Diagnostics''' section of the router's WebUI: | ||
[[File:Openvpn connection test 3.png]] | [[File:Openvpn connection test 3.png]] | ||
| Line 144: | Line 142: | ||
====Server from Client==== | ====Server from Client==== | ||
---- | ---- | ||
====Clients from Server==== | ====Clients from Server==== | ||
---- | ---- | ||
==== | ====Client to client==== | ||
---- | ---- | ||
===OpenVPN Proxy=== | ===OpenVPN Proxy=== | ||
---- | ---- | ||
OpenVPN Servers can be used as Proxies by OpenVPN Clients. This means that the client will be assigned the Public IP address of the OpenVPN server and will be seen as using that IP address when browsing the Internet, transferring data or doing any other online activities. This section provides direction on how to set up and OpenVPN Proxy on RUT routers. | OpenVPN Servers can be used as Proxies by OpenVPN Clients. This means that the client will be assigned the Public IP address of the OpenVPN server and will be seen as using that IP address when browsing the Internet, transferring data or doing any other online activities. This section provides direction on how to set up and OpenVPN Proxy on RUT routers. | ||
Revision as of 12:52, 9 March 2018
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
Summary
This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our VPN manual page.
OpenVPN configuration type
Before configuring anything you should first know what type of OpenVPN connection suits your needs the best. The key things to be considered here are the type of connection (TUN (tunnel) or TAP (bridged)), the data transfer protocol (User Datagram Protocol (UDP) or Transmission Control Protocol (TCP)) and authentication (TLS or Static key). Here is a short overview of the differences:
- Type
- TUN (tunnel) - simulates a network layer device and it operates with layer 3 packets like IP packets. TUN is used for routing and connecting multiple clients to a single server.
- TAP (bridged) - simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TAP is used for creating a network bridge between two Ethernet segments in different locations.
- Protocol
- UDP - is used by apps to deliver a faster stream of information by doing away with error-checking.
- TCP - a suite of protocols used by devices to communicate over the Internet and most local networks. It provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network.
- Authentication
- TLS - uses SSL/TLS + certificates for authentication and key exchange.
- Static key - uses a pre-shared Static key. Can only be used between two peers.
An overview of most of these types is provided in this article. Concerning TCP vs UDP, we will be using UDP for all examples. Choosing between TCP and UDP doesn't affect the rest of the configuration, so you can still follow the given examples no matter which protocol you are using. Simply choose the one that suits your purposes.
TLS Authentication
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the TLS Authentication method on RUT routers.
Generating TLS certificates/keys
A connection that uses TLS requires multiple certificates and keys for authentication:
* Server ** The root certificate file (Cetificate Authority) ** Server certificate ** Server key ** Diffie Hellman Parameters
* Client ** The root certificate file (Cetificate Authority) ** Client certificate ** Client key
Detailed instruction on how to obtain these files can be found here.
Once you have all the required files, continue following this section of the guide.
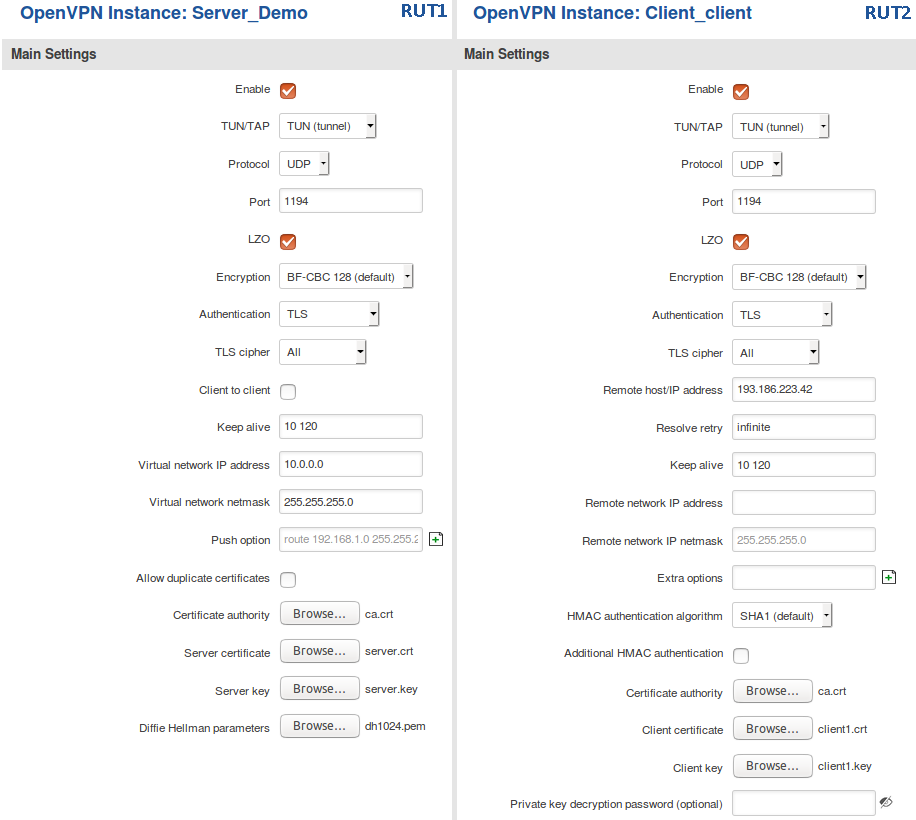
Configuration
Now we can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 193.186.223.42) and RUT2 (Client; LAN IP: 192.168.2.1); that will be connected into virtual network (with the virtual address: 10.0.0.0):
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). Another important aspect is the Virtual network IP address (10.0.0.0 in this case). The Server and the connected Clients will be given IP address that belong to this network. If you're creating an exceptionally large network, you might want to change the Virtual network netmask.
From the Client side, make sure to enter the correct Remote host/IP address (193.186.223.42 in this case). This is the Server's Public IP address, not the virtual IP address.
Static key Authentication
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the Static key Authentication method on RUT routers.
Creating a Static key
A Static key connection uses a pre-shared for authentication between a Server and one Client. You can generate a Static key within the router itself or with PC that uses a Linux-based OS.
Within the router
In order to generate a Static key within the router connect to the device via the Command Line Interface (CLI) or SSH (the default username is root, the password is your router's admin password, admin01 by default). CLI can be found in the router's WebUI, under Services. To connect to the router via SSH, use Terminal app (type ssh [email protected]; replace 192.168.1.1 with your router's LAN IP address) if you're using a Linux-based OS. Or download PuTTY, a free SSH and telnet client, if you're using Windows.
When you have connected to the router, relocate to the directory (for example, cd /etc/easy-rsa/keys/) where you want to store your Static key and use this command:
# openvpn --genkey --secret static.key
The newly generated Static key will appear in the same directory where you issued the command above.
Extracting the key
If you are using a Linux-based OS, extracting files from the router is simple. Just go to the directory on your PC where you want to relocate the files, right click anywhere and choose the Open in Terminal option. In the Terminal command line use the Secure Copy (scp) command to copy the files from the router. The full command should look something like this:
$ scp [email protected]:/etc/esy-rsa/keys/static.key ./
The [email protected]:/etc/easy-rsa/keys/static.key specifies the path to where the Static key is located (replace the IP address with your router's LAN IP); the ./ denotes that you want to copy the contents to the directory you are in at the moment.
If you are using Windows, you can copy files from the router using WinSCP, an Open source freeware SFTP, SCP and FTP client for Windows OS. Use the same login information with WinSCP as with CLI or SSH. Once you've connected to the router with WinSCP, copying the files should be simple enough: just relocate to directory where you generated the key, select the Static key file and drag it to directory on your PC where you would like to store it.
On a Linux PC
To generate a Static key on a Linux PC, go to the directory where you want the key to appear, right click anywhere in that directory and chose the option Open in Terminal. In the Terminal window execute this command:
$ openvpn --genkey --secret static.key
The newly generated key should then appear in the directory you were in.
Configuration
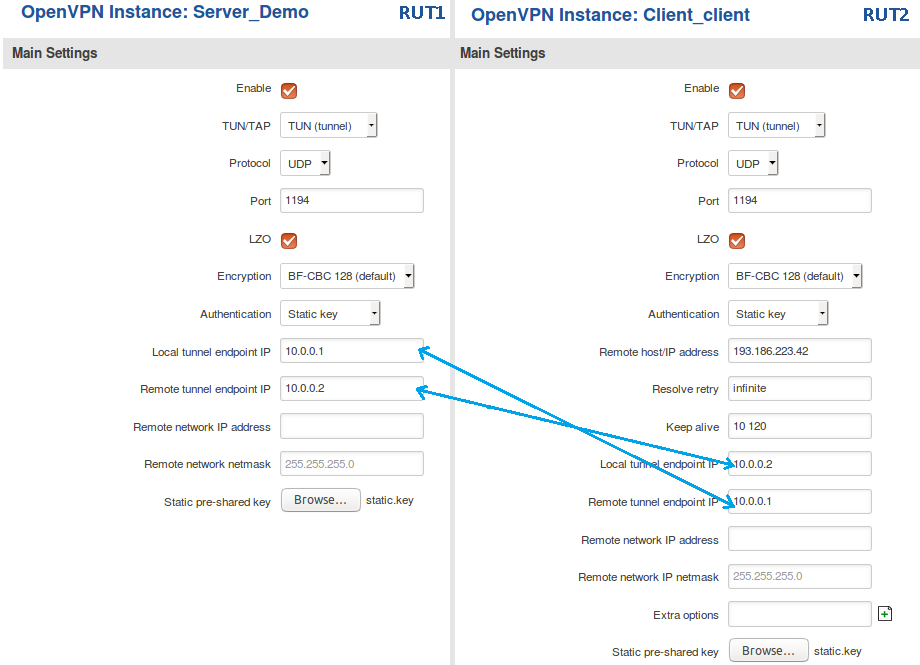
When you have a Static key, you can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and Static key for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 193.186.223.42) and RUT2 (Client; LAN IP: 192.168.2.1); the two routers will be connected via OpenVPN; the Server's Virtual IP address will be 10.0.0.1; the Client's - 10.0.0.2:
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). Other important aspects are the Local tunnel endpoint IP and the Remote tunnel endpoint IP. Take note these two particular parameter values are reversed for the individual Client and the Server configurations since these values represent opposite things depending on the instance's perspective.
From the Client side, make sure to enter the correct Remote host/IP address (193.186.223.42 in this case). This is the Server's Public IP address, not the virtual IP address.
TAP (bridged) OpenVPN
This section provides a guide on how to configure a successful OpenVPN TAP (bridged) connection between an OpenVPN Client and Server on RUT routers.
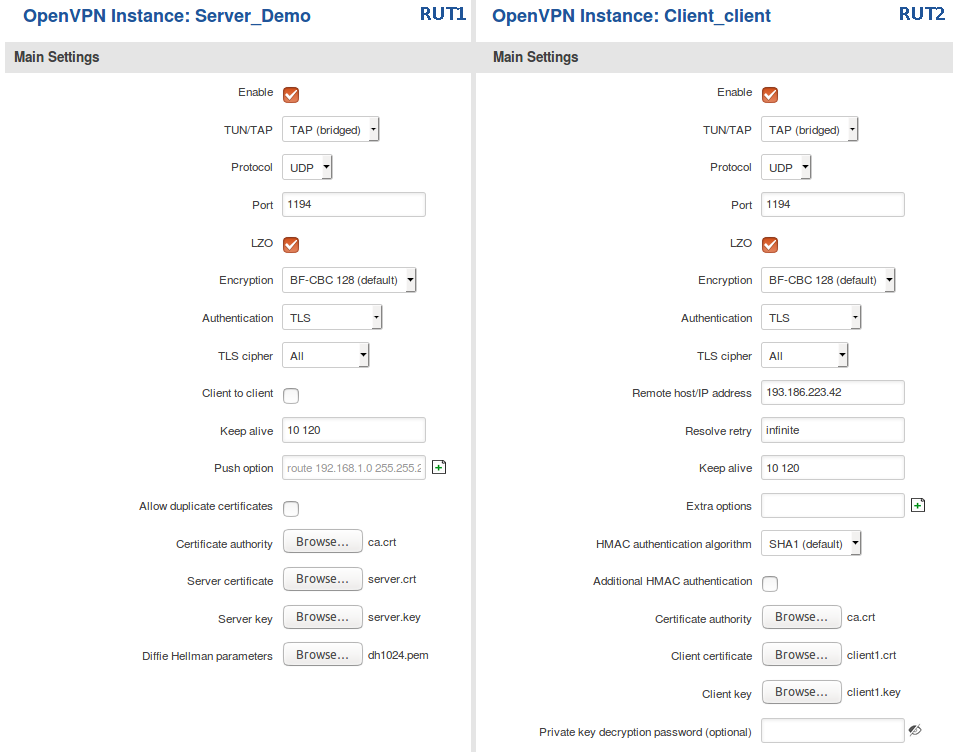
Configuration
TAP is used for creating a network bridge between two Ethernet segments in different locations. For this example we will be creating a TAP (bridged) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 193.186.223.42) and RUT2 (Client; LAN IP: 192.168.1.2); the two routers will be connected via OpenVPN.
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). The most important aspect of a TAP configuration is that it just bridges two network segments and doesn't create a different virtual network. Therefore, as in the example provided above, the routers have to be in the same subnet (192.168.1.0 in this case). While making sure of that, don't forget that the routers can't have the same IP address, just the same subnet (for example, if both routers have the LAN IP 192.168.1.1, the connection won't work; if one has, for example, 192.168.1.1 and the other 192.168.1.100, then the connection will work).
For this example we used TLS Authentication. If you want to use a different Authentication method, refer to the relevant section of this article. The authentication configuration will not be different because of the chosen OpenVPN type (TUN or TAP).
From the Client side, make sure to enter the correct Remote host/IP address (193.186.223.42 in this case). This is the Server's Public IP address, not the LAN IP address.
Testing an OpenVPN connection
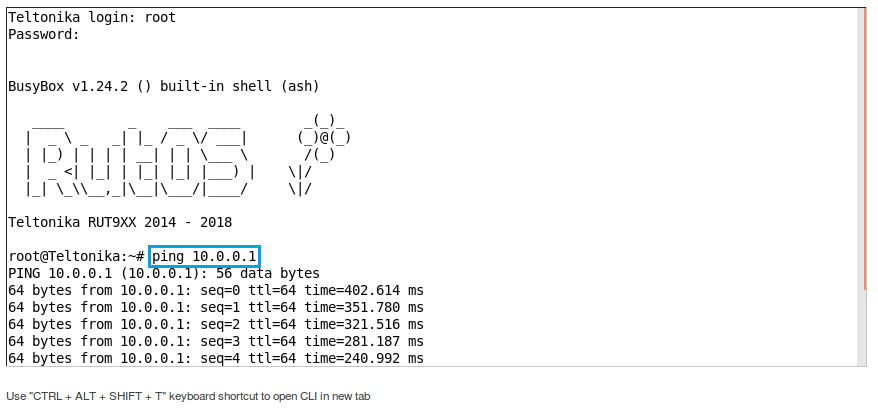
The most important thing after configuration is making sure that the newly established connection works. You can check the status of the OpenVPN vonnection in the Status → Network → OpenVPN page:
Another method of testing pinging the other instance's virtual IP address. You can send ping packets via CLI, SSH or from the System → Administration → Diagnostics section of the router's WebUI:
Ping the Server's virtual IP address from the Client or vice versa. If the ping packets are transmitted successfully, congratulations, you OpenVPN connection is working.
Additional configuration
This section will provide examples of some additional OpenVPN related configurations like how to reach another OpenVPN instance's private LAN or how to use an OpenVPN instance as a Proxy.
Reaching a device's LAN network
You may want your OpenVPN Clients to be able to reach devices that are in the Server device's private network (LAN) or vice versa. This section will provide directions on how to do that.
Server from Client
Clients from Server
Client to client
OpenVPN Proxy
OpenVPN Servers can be used as Proxies by OpenVPN Clients. This means that the client will be assigned the Public IP address of the OpenVPN server and will be seen as using that IP address when browsing the Internet, transferring data or doing any other online activities. This section provides direction on how to set up and OpenVPN Proxy on RUT routers.