Template:Networking rutos manual routing: Difference between revisions
No edit summary |
Gytispieze (talk | contribs) No edit summary |
||
| (29 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
{{Template: | {{Template: Networking_rutos_manual_fw_disclosure | ||
| | | fw_version = {{{series}}}{{#ifeq:{{{name}}}|RUT241|M|}}_R_00.07.01 | ||
| series = {{{series}}} | |||
| | |||
}} | }} | ||
{{#ifeq: {{{series}}} | RUT9 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version | {{#ifeq: {{{series}}} | RUT9 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version RUT9XX_R_00.06.08.5 and earlier) user manual page.</i>|}} | ||
{{#ifeq: {{{series}}} | RUT2 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version | {{#ifeq: {{{series}}} | RUT2 | | ||
{{#switch: {{{name}}} | |||
| RUT241 = | |||
| #default = | |||
<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version RUT2XX_R_00.01.14.4 and earlier) user manual page.</i>}} | |||
|}} | |||
==Summary== | ==Summary== | ||
| Line 194: | Line 195: | ||
</table> | </table> | ||
== | ==Advanced Static Routes== | ||
The <b> | The <b>Advanced Static Routes</b> section is used to configure policy-based routing infrastructures, which are usually used in more complex or specific networking scenarios. | ||
===Routing Tables=== | ===Routing Tables=== | ||
| Line 212: | Line 213: | ||
Refer to the table below for information on configuration fields for routing tables. | Refer to the table below for information on configuration fields for routing tables. | ||
[[File: | [[File:Networking_rutos_manual_routing_advanced_static_routes_routing_tables_routing_table_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 219: | Line 220: | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
</tr> | |||
<tr> | |||
<td>ID of Table</td> | |||
<td>integer [1..252]; default: <b>none</b></td> | |||
<td>Unique numerical identifier for the table. A table can be invoked by the both its ID or name.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 224: | Line 230: | ||
<td>string; default: <b>none</b></td> | <td>string; default: <b>none</b></td> | ||
<td>A custom name for the table. A table can be invoked by the both its ID or name.</td> | <td>A custom name for the table. A table can be invoked by the both its ID or name.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 329: | Line 330: | ||
Each protocol is described in the sections below. | Each protocol is described in the sections below. | ||
{{# | {{#ifq: {{{series}}} | RUTX | | | ||
<u><b> | <u><b> | ||
Note:</b> Dynamic Routing is additional software that can be installed from the <b> | Note:</b> Dynamic Routing is additional software that can be installed from the <b>Services → [[{{{name}}} Package Manager|Package Manager]]</b> page.</u> | ||
}} | }} | ||
===BGP=== | ===BGP=== | ||
| Line 342: | Line 343: | ||
The <b>General Settings</b> section is used to turn BGP protocol usage on or off or to upload an external BGP configuration. Below is an example of the BGP General Settings section. | The <b>General Settings</b> section is used to turn BGP protocol usage on or off or to upload an external BGP configuration. Below is an example of the BGP General Settings section. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_general_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 352: | Line 353: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns BGP protocol usage on or off.</td> | <td>Turns BGP protocol usage on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns vty access on or off.</td> | <td>Turns vty access on or off.</td> | ||
</tr> | </tr> | ||
| Line 369: | Line 370: | ||
====BGP Instance==== | ====BGP Instance==== | ||
---- | ---- | ||
The <b>BGP Instance</b> section is used to configure some of the main operating parameters of the BGP protocol. Below is an example of the BGP Instance section. | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_instance.png|border|class=tlt-border]] | |||
[[File: | |||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 386: | Line 382: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns the BGP instance on or off.</td> | <td>Turns the BGP instance on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>AS</td> | <td>AS</td> | ||
<td>integer [1.. | <td>integer [1..65535]default: <b>none</b></td> | ||
<td>AS number is an | <td>BGP Autonomous System (AS) number. It is an identifier that represents a routing domain; BGP routers can exchange routes within the same Autonomous System.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 403: | Line 399: | ||
<td>ip/netmask; default: <b>none</b></td> | <td>ip/netmask; default: <b>none</b></td> | ||
<td>Adds an announcement network(s). Routes to these networks will be shared over BGP.</td> | <td>Adds an announcement network(s). Routes to these networks will be shared over BGP.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Redistribution options</td> | <td>Redistribution options</td> | ||
<td>Connected routes | <td>Connected routes <nowiki>|</nowiki> Kernel added routes <nowiki>|</nowiki> NHRP routes <nowiki>|</nowiki> OSPF routes <nowiki>|</nowiki> Static routes <nowiki>|</nowiki> custom; default: <b>none</b></td> | ||
<td>Distributes selected routes. Route redistribution is a process that allows a network to use a routing protocol to dynamically route traffic based on information learned from a separate routing protocol.</td> | <td>Distributes selected routes. Route redistribution is a process that allows a network to use a routing protocol to dynamically route traffic based on information learned from a separate routing protocol.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Deterministic MED</td> | <td>Deterministic MED</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Compares MEDs between same AS, while ignoring their age.</td> | <td>Compares MEDs between same AS, while ignoring their age.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
====BGP Peers==== | |||
---- | ---- | ||
<b>BGP Peers</b> are routers in the same BGP Peer Group that can redistribute routes among other BGP Peers. Below is an example of the BGP Peers section, which is empty by default. | <b>BGP Peers</b> are routers in the same BGP Peer Group that can redistribute routes among other BGP Peers. Below is an example of the BGP Peers section, which is empty by default. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers.png|border|class=tlt-border]] | ||
To create a new Peer, look to the Add New Instance section under BGP Peer; type in a custom name for the BGP Peer and click the 'Add' button: | To create a new Peer, look to the Add New Instance section under BGP Peer; type in a custom name for the BGP Peer and click the 'Add' button: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_add_button.png|border|class=tlt-border]] | ||
The newly added BGP Peer configuration should look similar to this: | |||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_added.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 445: | Line 431: | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
</tr> | |||
<tr> | |||
<td>Remote AS</td> | |||
<td>integer [1..65535]; default: <b>none</b></td> | |||
<td>Remote autonomous system number of this remote BGP Neighbor.</td> | |||
</tr> | |||
<tr> | |||
<td>Remote address</td> | |||
<td>ip4; default: <b>none</b></td> | |||
<td>IPv4 address of this remote BGP Neighbor.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns turns this BGP peer on or off.</td> | |||
</tr> | |||
</table> | |||
To see more settings for a BGP Peer, click the 'Edit' button next to it: | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_edit_button.png|border|class=tlt-border]] | |||
The full BGP Peer configuration page should look similar to this: | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_bgp_peer.png|border|class=tlt-border]] | |||
<table class="nd-mantable"> | |||
<tr> | |||
<th>Field</th> | |||
<th>Value</th> | |||
<th>Description</th> | |||
</tr> | |||
<tr> | |||
<td>Enable</td> | |||
<td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | |||
<td>Turns this BGP peer on or off.</td> | <td>Turns this BGP peer on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Remote AS</td> | <td>Remote AS</td> | ||
<td>integer [1.. | <td>integer [1..65535]; default: <b>none</b></td> | ||
<td>Remote autonomous system number of this remote BGP Neighbor.</td> | <td>Remote autonomous system number of this remote BGP Neighbor.</td> | ||
</tr> | </tr> | ||
| Line 459: | Line 476: | ||
<td>Remote address</td> | <td>Remote address</td> | ||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
<td>IPv4 address of this remote BGP Neighbor | <td>IPv4 address of this remote BGP Neighbor.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 470: | Line 487: | ||
<td>integer; default: <b>none</b></td> | <td>integer; default: <b>none</b></td> | ||
<td>Time to Live value for packets associated with this remote BGP Neighbor.</td> | <td>Time to Live value for packets associated with this remote BGP Neighbor.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Default originate</td> | <td>Default originate</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Announces default routes to this peer.</td> | <td>Announces default routes to this peer.</td> | ||
</tr> | </tr> | ||
| Line 500: | Line 497: | ||
<td>string; default: <b>none</b></td> | <td>string; default: <b>none</b></td> | ||
<td>A custom description for this BGP peer. Used for easier management purposes only.</td> | <td>A custom description for this BGP peer. Used for easier management purposes only.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
====BGP Peer Groups==== | |||
---- | ---- | ||
A <b>BGP Peer Group</b> is a collection of routers that use the BGP protocol to dynamically redistribute routes among peers (other routers). The figure below is an example of the BGP Peer Groups section, which is empty by default. | A <b>BGP Peer Group</b> is a collection of routers that use the BGP protocol to dynamically redistribute routes among peers (other routers). The figure below is an example of the BGP Peer Groups section, which is empty by default. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups.png|border|class=tlt-border]] | ||
To create a new Peer Group, look to the Add New Instance section under BGP Peer Groups; type in a custom name for the BGP Peer Group and click the 'Add' button: | To create a new Peer Group, look to the Add New Instance section under BGP Peer Groups; type in a custom name for the BGP Peer Group and click the 'Add' button: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_add_button.png|border|class=tlt-border]] | ||
The newly added BGP Peer Group configuration should look similar to this: | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups_added.png|border|class=tlt-border]] | |||
<table class="nd-mantable"> | |||
<tr> | |||
<th>Field</th> | |||
<th>Value</th> | |||
<th>Description</th> | |||
</tr> | |||
<tr> | |||
<td>Remote AS</td> | |||
<td>integer [1..65535]; default: <b>none</b></td> | |||
<td>Remote autonomous system number.</td> | |||
</tr> | |||
</table> | |||
To see more settings for a BGP Peer Group, click the 'Edit' button next to it: | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups_edit_button.png|border|class=tlt-border]] | |||
[[File: | The full BGP Peer Group configuration page should look similar to this: | ||
[[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups_bgp_peer_group.png|border|class=tlt-border]] | |||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 530: | Line 543: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns the BGP Peer Group configuration on or off.</td> | <td>Turns the BGP Peer Group configuration on or off.</td> | ||
</tr> | </tr> | ||
| Line 536: | Line 549: | ||
<td>Remote AS</td> | <td>Remote AS</td> | ||
<td>integer [1..65535]; default: <b>none</b></td> | <td>integer [1..65535]; default: <b>none</b></td> | ||
<td> | <td>Remote autonomous system number.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Neighbor address</td> | <td>Neighbor address</td> | ||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
<td> | <td>IPv4 address(es) of a remote BGP Neighbor.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Advertisement interval</td> | <td>Advertisement interval</td> | ||
<td>integer; default: <b>none</b></td> | <td>integer; default: <b>none</b></td> | ||
<td> | <td>BGP advertisement frequency (in seconds).</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Neighbor configuration</td> | <td>Neighbor configuration</td> | ||
<td>None | <td>None <nowiki>|</nowiki> Route Reflector client <nowiki>|</nowiki> Route Server client; default: <b>None</b></td> | ||
<td>Defines the role of a BGP Neighbor. | <td>Defines the role of a BGP Neighbor. | ||
<ul> | <ul> | ||
| Line 565: | Line 573: | ||
<tr> | <tr> | ||
<td>Disable next hop calculation</td> | <td>Disable next hop calculation</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns next hop calculation for this BGP Peer Group on or off.</td> | <td>Turns next hop calculation for this BGP Peer Group on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Inbound soft-reconfiguration</td> | <td>Inbound soft-reconfiguration</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns inbound soft-reconfiguration for this Neighbor on or off.</td> | <td>Turns inbound soft-reconfiguration for this Neighbor on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Disable connected check</td> | <td>Disable connected check</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>When turned on, Disable connected check enables a directly connected eBGP Neighbor to peer using a loopback address without adjusting the default TTL of 1.</td> | <td>When turned on, Disable connected check enables a directly connected eBGP Neighbor to peer using a loopback address without adjusting the default TTL of 1.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 627: | Line 592: | ||
The <b>Access List Filters</b> section is used to configure special filters that restrict or allow access to specified networks for BGP Peers. Below is an example of the Access List Filters section which is empty by default. You can add a new filter by clicking the 'Add' button | The <b>Access List Filters</b> section is used to configure special filters that restrict or allow access to specified networks for BGP Peers. Below is an example of the Access List Filters section which is empty by default. You can add a new filter by clicking the 'Add' button | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_access_list_filters_add_button.png|border|class=tlt-border]] | ||
An Access List Filter configuration for BGP should look similar to this: | An Access List Filter configuration for BGP should look similar to this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_access_list_filters_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 641: | Line 606: | ||
<tr> | <tr> | ||
<td>Peer</td> | <td>Peer</td> | ||
<td>bgp peer; default: <b> | <td>bgp peer; default: <b>none</b></td> | ||
<td>Applies the filter rule for the specified peer.</td> | <td>Applies the filter rule for the specified peer.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Action</td> | <td>Action</td> | ||
<td>Permit | <td>Permit <nowiki>|</nowiki> Deny; default: <b>Permit</b></td> | ||
<td>When BGP traffic matches this rule, the device will take the action specified in this field, which is to either allow or block traffic.</td> | <td>When BGP traffic matches this rule, the device will take the action specified in this field, which is to either allow or block traffic.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td> | <td>Network</td> | ||
<td>Any | <td>ip/netmask <nowiki>|</nowiki> Any; default: <b>Any</b></td> | ||
<td> | <td>Matches traffic destined or originating from (depends on 'Direction' selection) to the network specified in this field.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Direction</td> | <td>Direction</td> | ||
<td>Inbound | <td>Inbound <nowiki>|</nowiki> Outbound; default: <b>Inbound</b></td> | ||
<td> | <td>Matches network traffic direction, which can either be traffic destined to this device (Inbound) or traffic originating from this device (Outbound).</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns an Access filter on or off.</td> | <td>Turns an Access filter on or off.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
===RIP Protocol=== | |||
===RIP=== | |||
---- | ---- | ||
The <b>Routing Information Protocol (RIP)</b> is one of the oldest distance-vector routing protocols which employ the hop count as a routing metric. RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from source to destination. The maximum number of hops allowed for RIP is 15, which limits the size of networks that RIP can support. A hop count of 16 is considered an infinite distance and the route is considered unreachable. RIP implements the split horizon, route poisoning and holddown mechanisms to prevent incorrect routing information from being propagated. | The <b>Routing Information Protocol (RIP)</b> is one of the oldest distance-vector routing protocols which employ the hop count as a routing metric. RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from source to destination. The maximum number of hops allowed for RIP is 15, which limits the size of networks that RIP can support. A hop count of 16 is considered an infinite distance and the route is considered unreachable. RIP implements the split horizon, route poisoning and holddown mechanisms to prevent incorrect routing information from being propagated. | ||
| Line 716: | Line 639: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the RIP protocol. Below is an example of the RIP General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the RIP protocol. Below is an example of the RIP General Settings section. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_general_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 726: | Line 649: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns RIP Protocol usage on or off.</td> | <td>Turns RIP Protocol usage on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns vty access on or off.</td> | <td>Turns vty access on or off.</td> | ||
</tr> | </tr> | ||
| Line 741: | Line 664: | ||
<tr> | <tr> | ||
<td>Version</td> | <td>Version</td> | ||
<td>2 | <td>2 <nowiki>|</nowiki> 1; default: <b>2</b></td> | ||
<td>Specifies the used version of the RIP protocol.</td> | <td>Specifies the used version of the RIP protocol.</td> | ||
</tr> | </tr> | ||
| Line 763: | Line 686: | ||
RIP Interface configuration should look similar to this: | RIP Interface configuration should look similar to this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_rip_interfaces_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 770: | Line 693: | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
</tr> | |||
<tr> | |||
<td>Enable</td> | |||
<td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | |||
<td>Turns a RIP Interface on or off.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 778: | Line 706: | ||
<tr> | <tr> | ||
<td>Passive interface</td> | <td>Passive interface</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and <b>ripd</b> does not send either multicast or unicast RIP packets.</td> | <td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and <b>ripd</b> does not send either multicast or unicast RIP packets.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 799: | Line 717: | ||
[[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters.png|border|class=tlt-border]] | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters.png|border|class=tlt-border]] | ||
To add a new filter, look to the Add New | To add a new filter, look to the Add New Filter section; enter a custom name and click the 'Add' button: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters_add_button.png|border|class=tlt-border]] | ||
An Access List Filter configuration for RIP should look similar to this: | An Access List Filter configuration for RIP should look similar to this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 820: | Line 738: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns an Access filter on or off.</td> | <td>Turns an Access filter on or off.</td> | ||
</tr> | </tr> | ||
| Line 830: | Line 748: | ||
<tr> | <tr> | ||
<td>Action</td> | <td>Action</td> | ||
<td>Permit | <td>Permit <nowiki>|</nowiki> Deny; default: <b>Permit</b></td> | ||
<td>When RIP traffic matches this rule, the device will take the action specified in this field, which is to either allow or block traffic.</td> | <td>When RIP traffic matches this rule, the device will take the action specified in this field, which is to either allow or block traffic.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Network</td> | <td>Network</td> | ||
<td>ip/netmask | <td>ip/netmask <nowiki>|</nowiki> Any; default: <b>Any</b></td> | ||
<td>Matches traffic destined or originating from (depends on 'Direction' selection) to the network specified in this field.</td> | <td>Matches traffic destined or originating from (depends on 'Direction' selection) to the network specified in this field.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Direction</td> | <td>Direction</td> | ||
<td>Inbound | <td>Inbound <nowiki>|</nowiki> Outbound; default: <b>Inbound</b></td> | ||
<td>Matches network traffic direction, which can either be traffic destined to this device (Inbound) or traffic originating from this device (Outbound).</td> | <td>Matches network traffic direction, which can either be traffic destined to this device (Inbound) or traffic originating from this device (Outbound).</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
===OSPF=== | ===OSPF Protocol=== | ||
---- | ---- | ||
<b>Open Shortest Path First</b> (<b>OSPF</b>) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS). It is defined as OSPF Version 2 in RFC 2328 for IPv4. | <b>Open Shortest Path First</b> (<b>OSPF</b>) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS). It is defined as OSPF Version 2 in RFC 2328 for IPv4. | ||
| Line 853: | Line 771: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the OSPF protocol. Below is an example of the OSPF General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the OSPF protocol. Below is an example of the OSPF General Settings section. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_ospf_protocol_general_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 863: | Line 781: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns OSPF Protocol usage on or off.</td> | <td>Turns OSPF Protocol usage on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns vty access on or off.</td> | <td>Turns vty access on or off.</td> | ||
</tr> | </tr> | ||
| Line 896: | Line 814: | ||
</ul> | </ul> | ||
</td> | </td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 927: | Line 840: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns an OSPF Interface on or off.</td> | <td>Turns an OSPF Interface on or off.</td> | ||
</tr> | </tr> | ||
| Line 938: | Line 851: | ||
You should directed to a window such as this: | You should directed to a window such as this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_ospf_protocol_ospf_interface_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 948: | Line 861: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns the OSPF area on or off.</td> | <td>Turns the OSPF area on or off.</td> | ||
</tr> | </tr> | ||
| Line 978: | Line 891: | ||
<tr> | <tr> | ||
<td>Type</td> | <td>Type</td> | ||
<td>Broadcast | <td>Broadcast <nowiki>|</nowiki> Nonbroadcast <nowiki>|</nowiki> Point-to-point <nowiki>|</nowiki> Point-to-multipointl default: <b>none</b></td> | ||
<td>OSPF interface configuration type.</td> | <td>OSPF interface configuration type.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Authentication</td> | <td>Authentication</td> | ||
<td>None | <td>None <nowiki>|</nowiki> Password <nowiki>|</nowiki> MD5 HMAC; default: <b>None</b></td> | ||
<td>Specifies the Authentication method.</td> | <td>Specifies the Authentication method.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 1,034: | Line 913: | ||
The newly added new Area will appear in the OSPF Area list. | The newly added new Area will appear in the OSPF Area list. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_ospf_protocol_ospf_area_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,051: | Line 930: | ||
<td>32-bit integer; default: <b>none</b></td> | <td>32-bit integer; default: <b>none</b></td> | ||
<td>OSPF Area ID. OSPF Networks that are meant to communicate with each other should belong to the same Area (have the Area ID).</td> | <td>OSPF Area ID. OSPF Networks that are meant to communicate with each other should belong to the same Area (have the Area ID).</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns an OSPF Area on or off.</td> | <td>Turns an OSPF Area on or off.</td> | ||
</tr> | </tr> | ||
| Line 1,103: | Line 977: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns the usage of this network (in OSPF) on or off.</td> | <td>Turns the usage of this network (in OSPF) on or off.</td> | ||
</tr> | </tr> | ||
| Line 1,116: | Line 990: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the EIGRP protocol. Below is an example of the EIGRP General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the EIGRP protocol. Below is an example of the EIGRP General Settings section. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_eigrp_general_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,126: | Line 1,000: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns EIGRP protocol usage on or off.</td> | <td>Turns EIGRP protocol usage on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable logging</td> | <td>Enable logging</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns logging of EIGRP traffic on or off.</td> | <td>Turns logging of EIGRP traffic on or off.</td> | ||
</tr> | </tr> | ||
| Line 1,151: | Line 1,025: | ||
<tr> | <tr> | ||
<td>Redistribution options</td> | <td>Redistribution options</td> | ||
<td>Connected routes | <td>Connected routes <nowiki>|</nowiki> Kernel added routes <nowiki>|</nowiki> NHRP routes <nowiki>|</nowiki> OSPF routes <nowiki>|</nowiki> Static routes <nowiki>|</nowiki> custom; default: <b>none</b></td> | ||
<td>Distributes selected routes. Route redistribution is a process that allows a network to use a routing protocol to dynamically route traffic based on information learned from a separate routing protocol.</td> | <td>Distributes selected routes. Route redistribution is a process that allows a network to use a routing protocol to dynamically route traffic based on information learned from a separate routing protocol.</td> | ||
</tr> | </tr> | ||
| Line 1,169: | Line 1,043: | ||
The <b>General Settings</b> section is used to turn NHRP protocol usage on or off. Below is an example of the NHRP General Settings section. | The <b>General Settings</b> section is used to turn NHRP protocol usage on or off. Below is an example of the NHRP General Settings section. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_general_settings.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,179: | Line 1,053: | ||
<tr> | <tr> | ||
<td>Enable service</td> | <td>Enable service</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns NHRP protocol usage on or off.</td> | <td>Turns NHRP protocol usage on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable logging</td> | <td>Enable logging</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns NHRP traffic logging on or off.</td> | <td>Turns NHRP traffic logging on or off.</td> | ||
</tr></table> | </tr></table> | ||
| Line 1,192: | Line 1,066: | ||
The <b>Interfaces</b> section is used to define which existing network interfaces can participate in NHRP communication. Below is an example of the NHRP Interfaces section which is empty by default. | The <b>Interfaces</b> section is used to define which existing network interfaces can participate in NHRP communication. Below is an example of the NHRP Interfaces section which is empty by default. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces.png|border|class=tlt-border]] | ||
To create a new NHRP Interface, look to the Add New Interface section; enter a custom name and click the 'Add' button. | To create a new NHRP Interface, look to the Add New Interface section; enter a custom name and click the 'Add' button. | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_add_button.png|border|class=tlt-border]] | ||
The newly added NHRP interface will appear in the Interfaces list and should look similar to this: | The newly added NHRP interface will appear in the Interfaces list and should look similar to this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_begin_to_edit.png|border|class=tlt-border]] | ||
To see more settings for an NHRP Interface, click the 'Edit' button next to it: | |||
[[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_edit_button.png|border|class=tlt-border]] | |||
You should redirected to a windows that looks similar to this: | |||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_interface_configuration.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,214: | Line 1,092: | ||
<tr> | <tr> | ||
<td>Enabled</td> | <td>Enabled</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns the NHRP Interface on or off.</td> | <td>Turns the NHRP Interface on or off.</td> | ||
</tr> | </tr> | ||
| Line 1,234: | Line 1,112: | ||
<tr> | <tr> | ||
<td>NHS</td> | <td>NHS</td> | ||
<td> | <td>Dynamic <nowiki>|</nowiki> custom(ip4); default: <b>none</b></td> | ||
<td>IP address of a Next-Hop server.</td> | <td>IP address of a Next-Hop server.</td> | ||
</tr> | </tr> | ||
| Line 1,249: | Line 1,127: | ||
<tr> | <tr> | ||
<td>IPsec support</td> | <td>IPsec support</td> | ||
<td>off | <td>off <nowiki>|</nowiki> <span style="color: red;">on</span>; default: <b>off</b></td> | ||
<td>Turns usage of NHRP over IPsec for this Interface on or off.</td> | <td>Turns usage of NHRP over IPsec for this Interface on or off.</td> | ||
</tr> | </tr> | ||
| Line 1,263: | Line 1,141: | ||
The <b>NHRP Mappings Configuration</b> section is used to configure (map) associations between NHRP router IP address and NBMAs. Below is an example of the NHRP Mappings Configuration section which is empty by default. To add a new configuration, simply click the 'Add' button: | The <b>NHRP Mappings Configuration</b> section is used to configure (map) associations between NHRP router IP address and NBMAs. Below is an example of the NHRP Mappings Configuration section which is empty by default. To add a new configuration, simply click the 'Add' button: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_nhrp_mappings_configuration_add_button.png|border|class=tlt-border]] | ||
The newly added configuration should appear in the NHRP Mappings Configuration list and look similar to this: | The newly added configuration should appear in the NHRP Mappings Configuration list and look similar to this: | ||
[[File: | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_interfaces_nhrp_mappings_configuration_edit.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,274: | Line 1,152: | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enabled</td> | <td>Enabled</td> | ||
<td>off | <td>off <nowiki>|</nowiki> on; default: <b>off</b></td> | ||
<td>Turns this mapping configuration on or off.</td> | <td>Turns this mapping configuration on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>IP Address</td> | |||
<td> | |||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
<td> | <td>Network ID of another NHRP router.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>NBMA</td> | <td>NBMA</td> | ||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
<td> | <td>IP address of a Next-Hop server.</td> | ||
</tr> | </tr> | ||
</table>|}} | </table>|}} | ||
[[Category:{{{name}}} Network section]] | [[Category:{{{name}}} Network section]] | ||
Revision as of 11:13, 6 October 2021
Template:Networking rutos manual fw disclosure
Summary
The Routing page is used to set up static routes, routing tables and rules.
This manual page provides an overview of the Routing windows in {{{name}}} devices.
If you're having trouble finding this page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Advanced" button, located at the top of the WebUI.
Static Routes
Routes ensure that network traffic finds its path to a specified host or network, both in local and remote network scenarios. Static routes are simply fixed routing entries in the routing table(s).
This section provides the possibility to configure custom static routes.
Static IPv4 Routes
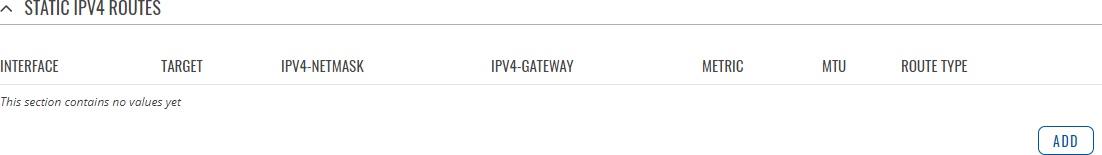
The Static IPv4 Routes section displays a list of user defined static IPv4 routes and provides the possibility to add and configure new ones. The list is empty by default.
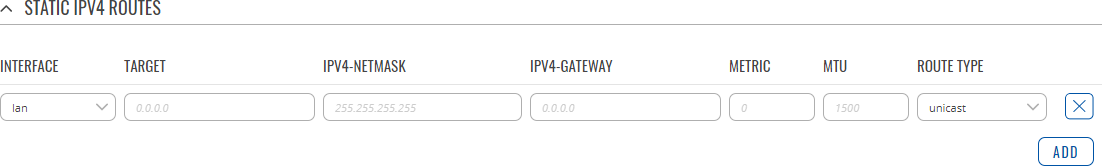
To add a new route and begin editing, simply click the 'Add' button. Refer to the table below for information on static route configuration fields.
| Field | Value | Description |
|---|---|---|
| Interface | network interface; default: lan | Network interface of the target network. |
| Target* | ip4; default: none | Destination network address. |
| IPv4-Netmask* | netmask; default: none | A netmask is used to divide an IP address into sub-networks (subnets). Combined together, the 'Netmask' and 'Target' values define the exact destination network or IP address to which this route applies. |
| IPv4-Gateway | ip4; default: none | A gateway can be any machine in a network that is capable of serving as an access point to another network. Traffic that matches this route will be directed over the IP address specified in this field. |
| Metric | integer [0..255]; default: none | The metric value acts as a measurement of priority. If a packet about to be routed matches two or more rules, the one with the lower metric is applied. |
| MTU | integer [64..9000]; default: 1500 | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| Route Type | unicast | local | broadcast | multicast | unreachable | prohibit | backhole | anycast | -- custom -- ; default: unicast | Selects route type. Each type specifies a different behavior for the route:
|
*Additional notes on 'Target' & 'Netmask' fields:
You can define a rule that applies to a single IP like this:
- Target: some IP
- Netmask: 255.255.255.255
Furthermore, you can create target/netmask combinations that apply to a range of IPs. Refer to the table below for examples.
| Target | Netmask | Network range |
|---|---|---|
| 192.168.2.0 | 255.255.255.240 | 192.168.2.0 - 192.168.2.15 |
| 192.168.2.240 | 255.255.255.240 | 192.168.2.240 - 192.168.2.255 |
| 192.168.2.161 | 255.255.255.0 | 192.168.2.0 - 192.168.55.255 |
| 192.168.0.0 | 255.255.0.0 | 192.168.0.0 - 192.168.255.255 |
| 192.168.2.161 | 255.255.255.255 | 192.168.2.161 |
Static IPv6 Routes
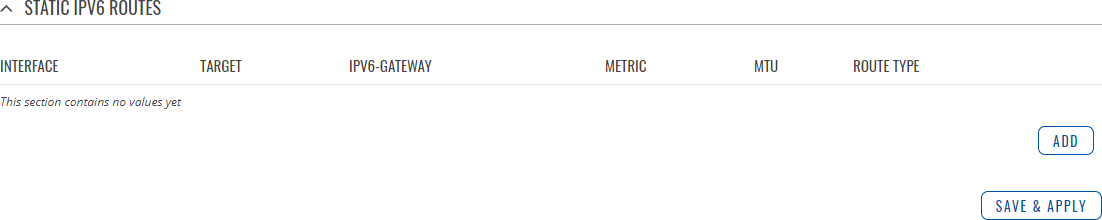
The Static IPv6 Routes section displays a list of user defined static IPv6 routes and provides the possibility to add and configure new ones. The list is empty by default.
To add a new route and begin editing, simply click the 'Add' button. Refer to the table below for information on static route configuration fields.
| Field | Value | Description |
|---|---|---|
| Interface | network interface; default: lan | Network interface of the target network. |
| Target | ip6; default: none | Destination network address. |
| IPv6-Gateway | ip6; default: none | A gateway can be any machine in a network that is capable of serving as an access point to another network. Traffic that matches this route will be directed over the IP address specified in this field. |
| Metric | integer [0..255]; default: none | The metric value acts as a measurement of priority. If a packet about to be routed matches two or more rules, the one with the lower metric is applied. |
| MTU | integer [64..9000]; default: 1500 | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| Route Type | unicast | local | broadcast | multicast | unreachable | prohibit | backhole | anycast | -- custom -- ; default: unicast | Selects route type. Each type specifies a different behavior for the route:
|
Advanced Static Routes
The Advanced Static Routes section is used to configure policy-based routing infrastructures, which are usually used in more complex or specific networking scenarios.
Routing Tables
Routing Tables store network routes. Tables are checked before every routing decision until a matching route is found. Having multiple tables allows the user to set up a policy routing infrastructure. Policy-based routing is a technique where routing decisions are based on policies (rule) set by the user.
The 'Routing Tables' section displays user created routing tables. By default, the list is empty.
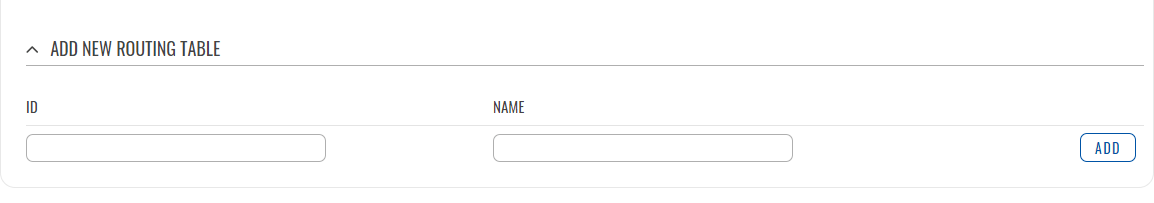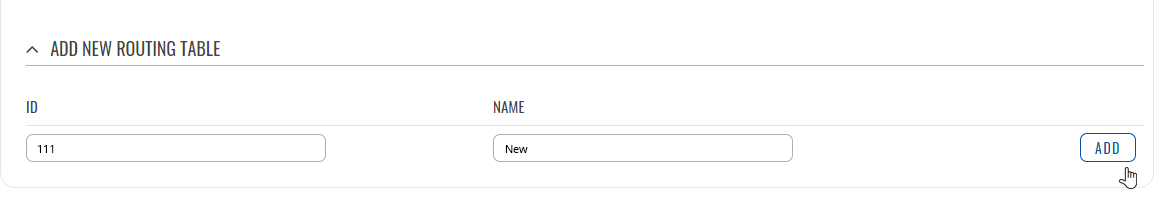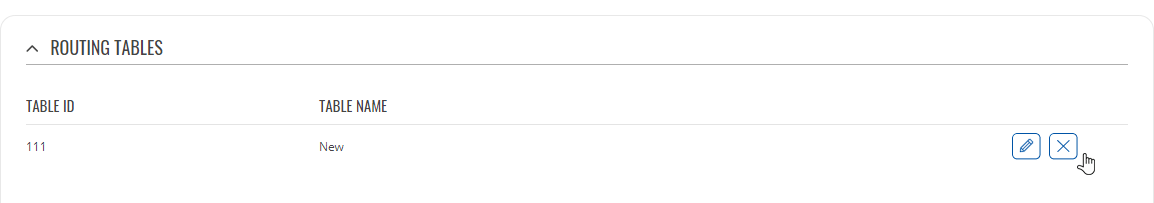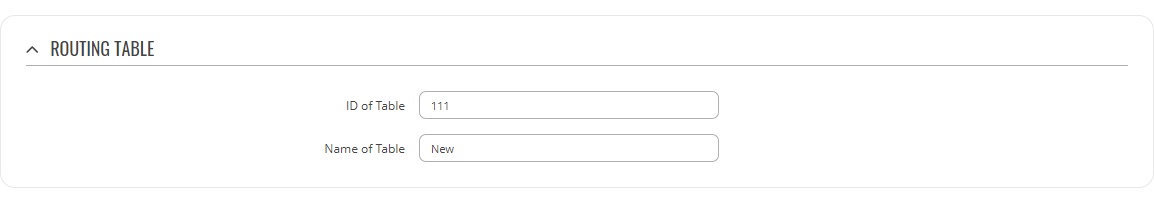
To create a new table, look to the 'Add New Routing Table' section below. Enter an ID for the new table in the range of [1..252], enter a custom name and click the 'Add' button. The new table should appear in the 'Routing Tables' list. Click the 'Edit' button next to it to begin editing.
Refer to the table below for information on configuration fields for routing tables.
| Field | Value | Description |
|---|---|---|
| ID of Table | integer [1..252]; default: none | Unique numerical identifier for the table. A table can be invoked by the both its ID or name. |
| Name of Table | string; default: none | A custom name for the table. A table can be invoked by the both its ID or name. |
Routing Rules For IPv4
Routing Rules provide a way to route certain packets with exceptions, i.e., in accordance to a rule. 'Routing Rules For IPv4' displays user defined routing rules. It is empty by default. To create a new rule, click the 'Add' button and begin editing by clicking the 'Edit' button located to the right of the newly created rule.
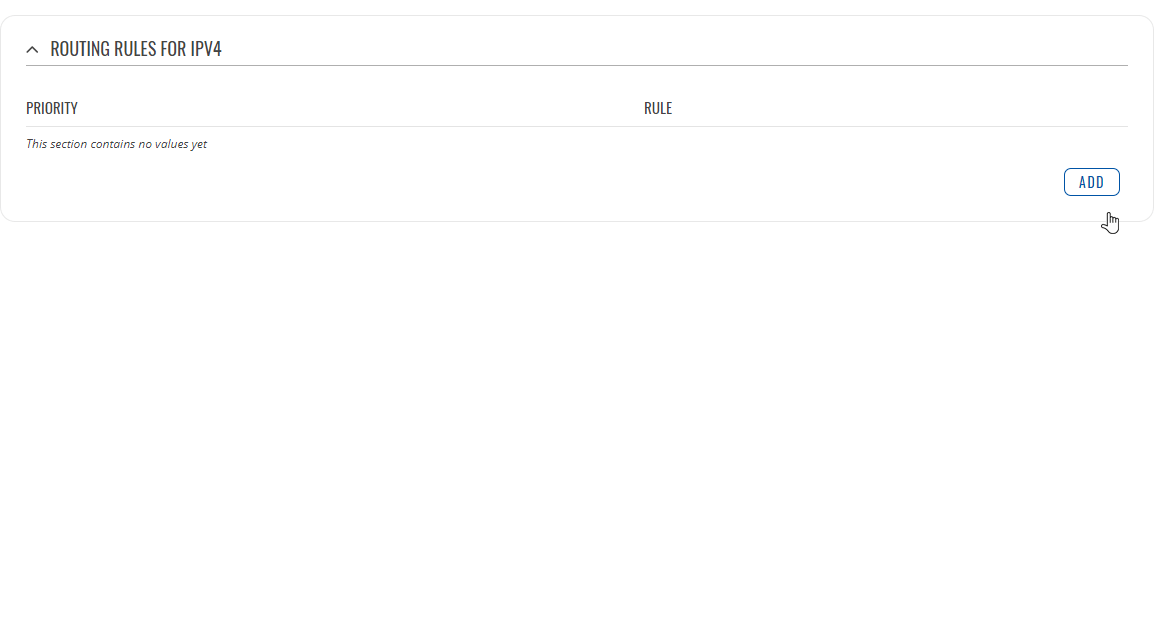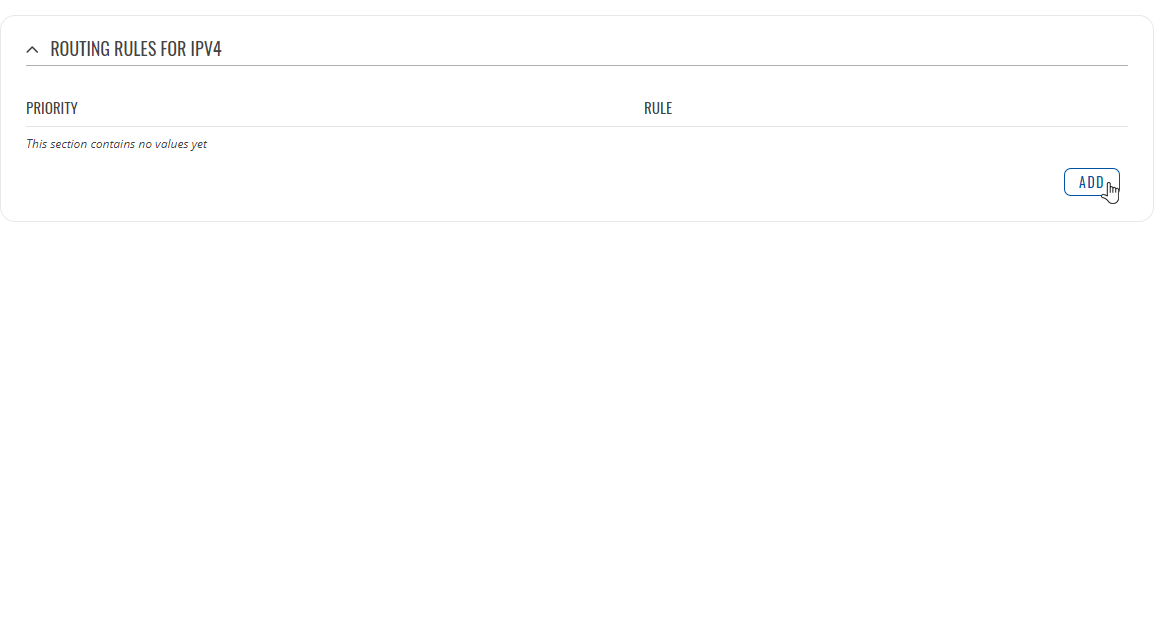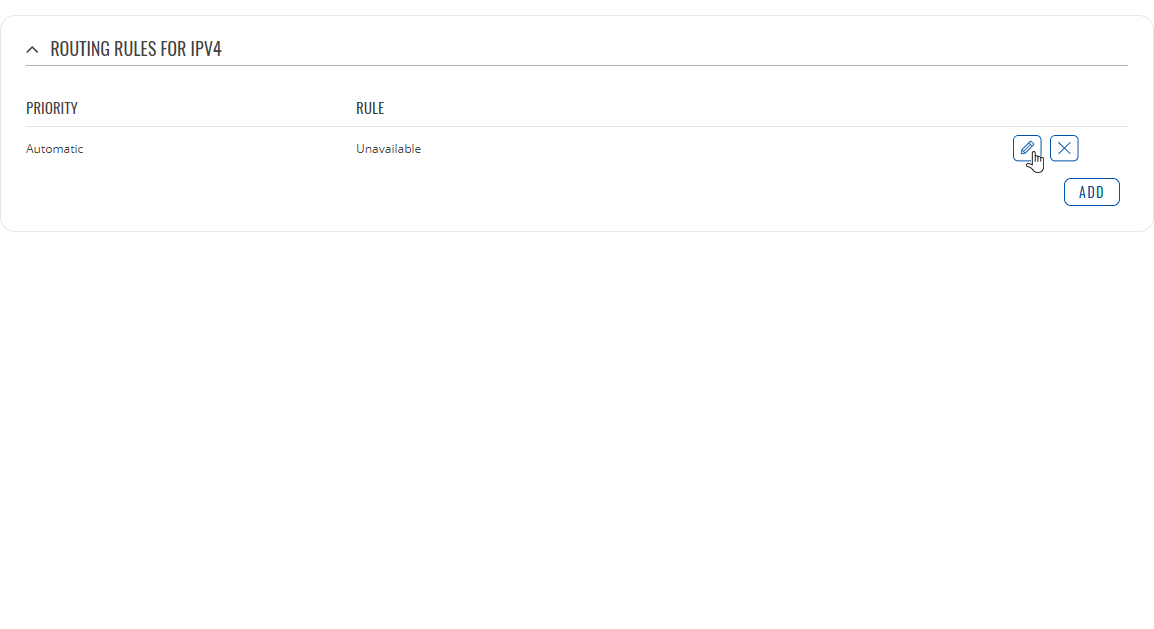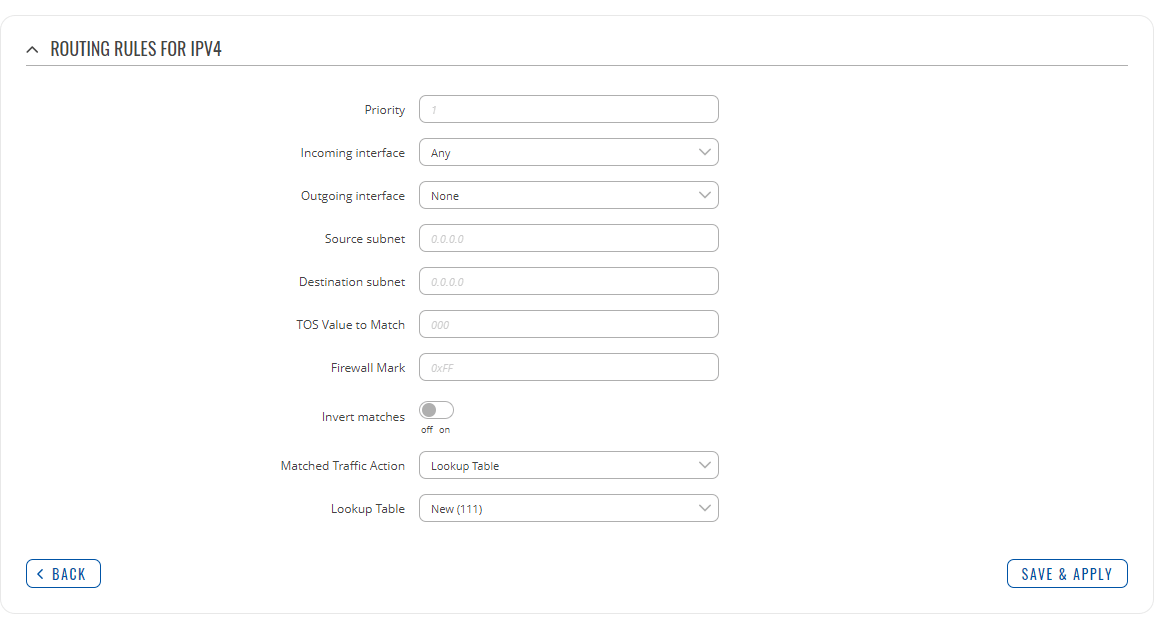
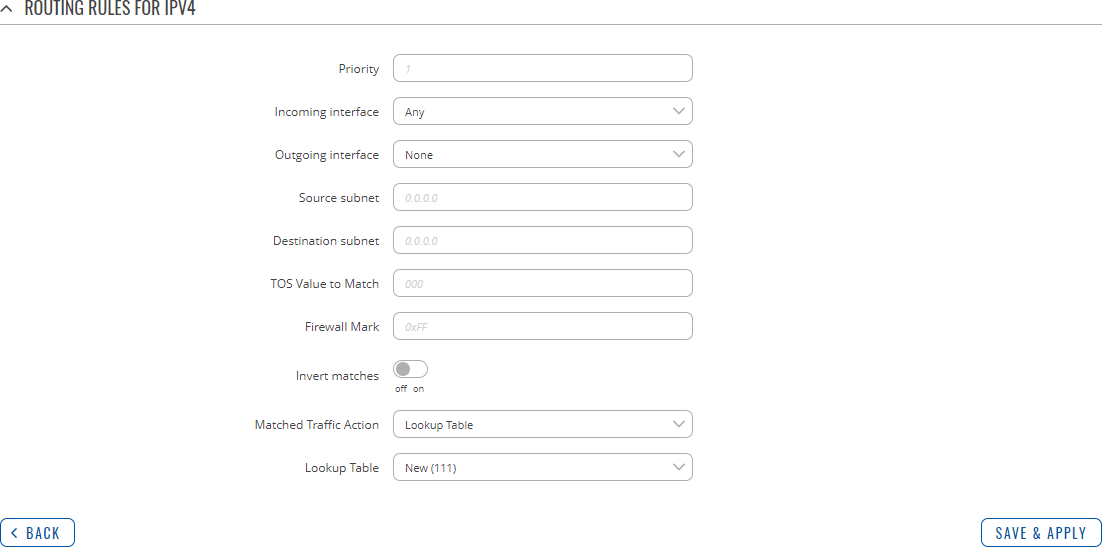
Refer to table below for information on each configuration field.
| Field | Value | Description |
|---|---|---|
| Priority | integer [0..65535]; default: none | Controls the order of IP rules. Rules with a lower priority value will be checked first. |
| Incoming interface | network interface | Any; default: Any | Logical interface name for incoming traffic. Select 'Any' to make the rule apply to all network interfaces. |
| Outgoing interface | network interface | None; default: None | Logical interface name for incoming traffic. Select 'None' to ignore outgoing interface. |
| Source subnet | netmask; default: none | Source subnet to match the rule. |
| Destination subnet | netmask; default: none | Destination subnet to match the rule. |
| TOS Value to Match | integer [0..255]; default: none | The type of service (ToS) value to match in IP headers. |
| Firewall Mark | integer [0..255] | hex [0x00..0xFF]; default: none | Specifies the fwmark and optionally its mask to match. For example, 0xFF to match mark 255 or 0x0/0x1 to match any even mark value. |
| Invert matches | off | on; default: off | If enabled, the meaning of the match options (Firewall Mark, TOS Value, Source and Destination subnets) is inverted. |
| Matched Traffic Action | Lookup Table | Jump to rule | Routing Action; default: Lookup Table | When network traffic matches this rule, the device will take an action specified in this field:
|
| Lookup Table | routing table; default: none | Specifies a table for routing traffic that matches this rule. This field is visible only when 'Matched Traffic Action' is set to Lookup Table. |
| Jump to rule | rule priority number; default: none | Specifies a another rule to follow for traffic that matches this rule. This field is visible only when 'Matched Traffic Action' is set to Jump to rule. |
| Routing Action | Prohibit | Unreachable | Blackhole | Throw; default: Prohibit | When traffic matches this rule, the action specified in this field will be executed. This field is visible only when 'Matched Traffic Action' is set to Routing Action. |
[[Category:{{{name}}} Network section]]