TRB142 Firewall: Difference between revisions
No edit summary |
No edit summary |
||
| Line 44: | Line 44: | ||
|- | |- | ||
! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Masquerading | ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Masquerading | ||
| style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | | | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | yes {{!}} no; Default: " " (depends on zone) | ||
| style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Enables | | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Enables Masquerading. MASQUERADE is an iptables target that can be used instead of the SNAT (source NAT) target when the external IP of the network interface is not known at the moment of writing the rule (when server gets external IP dynamically) | ||
|- | |- | ||
! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | MSS Clamping | ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | MSS Clamping | ||
| style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | | | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | yes {{!}} no; Default: " " (depends on zone) | ||
| style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | | | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Enables MSS Clamping. MSS clamping is a workaround used to change the maximum segment size (MSS) of all TCP connections passing through links with MTU lower than the Ethernet default of 1500 | ||
|- | |- | ||
! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Edit | ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Edit | ||
Revision as of 06:45, 15 October 2018
Main Page > TRB Gateways > TRB142 > TRB142 Manual > TRB142 WebUI > TRB142 Network section > TRB142 FirewallSummary
RutOS uses a standard Linux iptables package as its firewall, which uses routing chains and policies to facilitate control over inbound and outbound traffic. This chapter is an overview of the Firewall section.
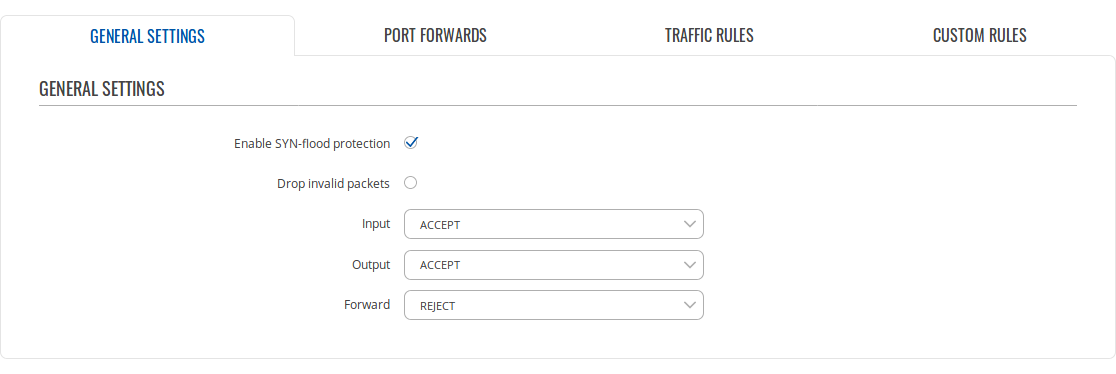
General Settings
The General Settings tab is used to configure the main policies of the device's firewall. The figure below is an example of the General Settings section and the table below provides information on the fields contained in that section:
Template:Webui network firewall general settings table
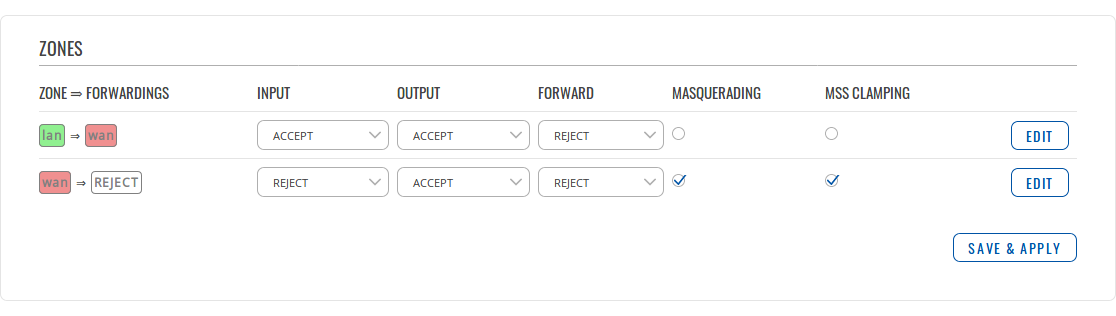
Zones
Template:Webui network firewall general settings zones
| FIELD NAME | VALUE | DESCRIPTION |
|---|---|---|
| Zone | - | The source zone |
| Forwardings | - | The destination zone |
| Input | Reject | Drop | Accept; Default: " " (depends on zone) | Action* that is to be performed for packets that pass through the Input chain |
| Output | Reject | Drop | Accept; Default: " " (depends on zone) | Action* that is to be performed for packets that pass through the Output chain |
| Forward | Reject | Drop | Accept; Default: " " (depends on zone) | Action* that is to be performed for packets that pass through the Forward chain |
| Masquerading | yes | no; Default: " " (depends on zone) | Enables Masquerading. MASQUERADE is an iptables target that can be used instead of the SNAT (source NAT) target when the external IP of the network interface is not known at the moment of writing the rule (when server gets external IP dynamically) |
| MSS Clamping | yes | no; Default: " " (depends on zone) | Enables MSS Clamping. MSS clamping is a workaround used to change the maximum segment size (MSS) of all TCP connections passing through links with MTU lower than the Ethernet default of 1500 |
| Edit | - | Opens the rule's editing page |
Template:Webui network firewall general settings zones table
Port Forwards
Template:Webui network firewall port forwards
[[]]
Template:Webui network firewall port forwards table
Traffic Rules
Template:Webui network firewall traffic rules
[[]]
Template:Webui network firewall traffic rules table