|
|
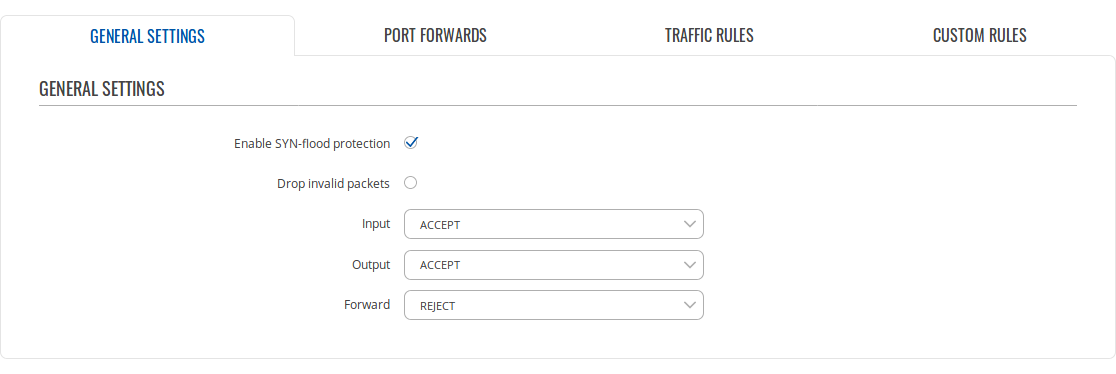
| Line 16: |
Line 16: |
|
| |
|
| [[File:Trb142 webui network firewall general settings zones v1.png]] | | [[File:Trb142 webui network firewall general settings zones v1.png]] |
|
| |
| {| class="wikitable"
| |
| |+
| |
| ! style="width: 250px; border: 1px solid white; border-bottom: 2px solid #0054A6; background: white; color: #0054A6; text-align: left;" | FIELD NAME
| |
| ! style="width: 250px; border: 1px solid white; border-bottom: 2px solid #0054A6; background: white; color: #0054A6; text-align: left;" | VALUE
| |
| ! style="width: 579px; border: 1px solid white; border-bottom: 2px solid #0054A6; background: white; color: #0054A6; text-align: left;" | DESCRIPTION
| |
| |-
| |
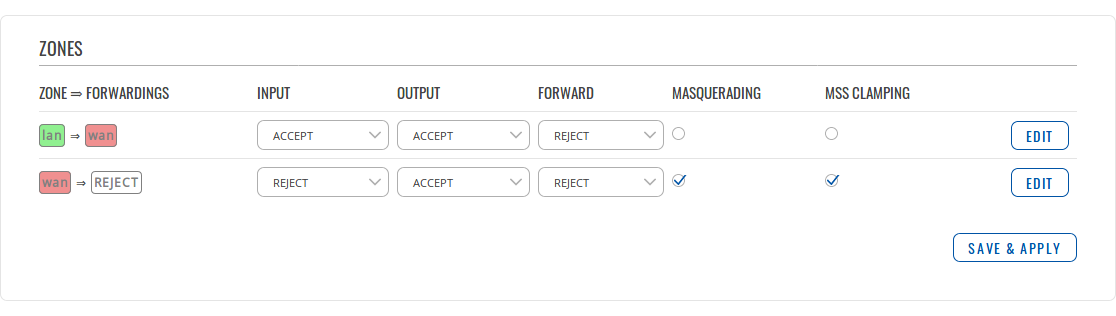
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Zone
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | -
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | The source zone
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Forwardings
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | -
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | The destination zone
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Input
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Reject {{!}} Drop {{!}} Accept; Default: " " (depends on zone)
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Action'''*''' that is to be performed for packets that pass through the Input chain
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Output
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Reject {{!}} Drop {{!}} Accept; Default: " " (depends on zone)
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Action'''*''' that is to be performed for packets that pass through the Output chain
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Forward
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Reject {{!}} Drop {{!}} Accept; Default: " " (depends on zone)
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Action'''*''' that is to be performed for packets that pass through the Forward chain
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Masquerading
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | yes {{!}} no; Default: " " (depends on zone)
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Enables Masquerading. MASQUERADE is an iptables target that can be used instead of the SNAT (source NAT) target when the external IP of the network interface is not known at the moment of writing the rule (when server gets external IP dynamically)
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | MSS Clamping
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | yes {{!}} no; Default: " " (depends on zone)
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Enables MSS Clamping. MSS clamping is a workaround used to change the maximum segment size (MSS) of all TCP connections passing through links with MTU lower than the Ethernet default of 1500
| |
| |-
| |
| ! style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Edit
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | -
| |
| | style="border: 1px solid white; border-bottom: 2px solid #E8E8E8; text-align: left; vertical-align: top; background: white;" | Opens the rule's editing page
| |
| |-
| |
| |}
| |
|
| |
|
| |
|
| {{Template: webui_network_firewall_general_settings_zones_table}} | | {{Template: webui_network_firewall_general_settings_zones_table}} |