OpenVPN configuration examples (Legacy Firmware): Difference between revisions
No edit summary |
|||
| Line 4: | Line 4: | ||
This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our '''[[VPN#OpenVPN|VPN manual page]]'''. | This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our '''[[VPN#OpenVPN|VPN manual page]]'''. | ||
==OpenVPN configuration type== | |||
Before configuring anything you should first know what type of OpenVPN connection suits your needs the best. The key things to be considered here are the type of connection ('''TUN''' ('''tunnel''') or '''TAP''' ('''bridged''')), the data transfer protocol ('''User Datagram Protocol''' ('''UDP''') or '''Transmission Control Protocol''' ('''TCP''')) and authentication ('''TLS''' or '''Static key'''). Here is a short overview of the differences: | |||
* Type | |||
** TUN (tunnel) - simulates a network layer device and it operates with layer 3 packets like IP packets. TUN is used for routing and connecting multiple clients to a single server. | |||
** TAP (bridged) - simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TAP is used for creating a network bridge between '''two'' Ethernet segments in different locations. | |||
* Protocol | |||
** UDP - is used by apps to deliver a faster stream of information by doing away with error-checking. | |||
** TCP - a suite of protocols used by devices to communicate over the Internet and most local networks. It provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network. | |||
* Authentication | |||
** TLS - uses SSL/TLS + certificates for authentication and key exchange. | |||
** Static key - use a pre-shared Static key. | |||
An overview of most of these types is provided in this article. Concerning TCP vs UDP, we will be using UDP for all examples. Choosing between TCP and UDP doesn't affect the rest of the configuration, so you can still follow the given examples no matter which protocol you are using. Simply choose the one that suits your purposes. | |||
==TLS Authentication== | ==TLS Authentication== | ||
| Line 13: | Line 31: | ||
A connection that uses TLS requires multiple certificates and keys for authentication: | A connection that uses TLS requires multiple certificates and keys for authentication: | ||
* Server | * Server | ||
** The root certificate file (Cetificate Authority) | ** The root certificate file (Cetificate Authority) | ||
** Server certificate | ** Server certificate | ||
| Line 26: | Line 44: | ||
Detailed instruction on how to obtain these files can be found '''[[How_to_generate_TLS_certifates%3F|here]]'''. | Detailed instruction on how to obtain these files can be found '''[[How_to_generate_TLS_certifates%3F|here]]'''. | ||
Once you have all the required files, continue following this guide | Once you have all the required files, continue following this section of the guide. | ||
===Configuration=== | ===Configuration=== | ||
---- | ---- | ||
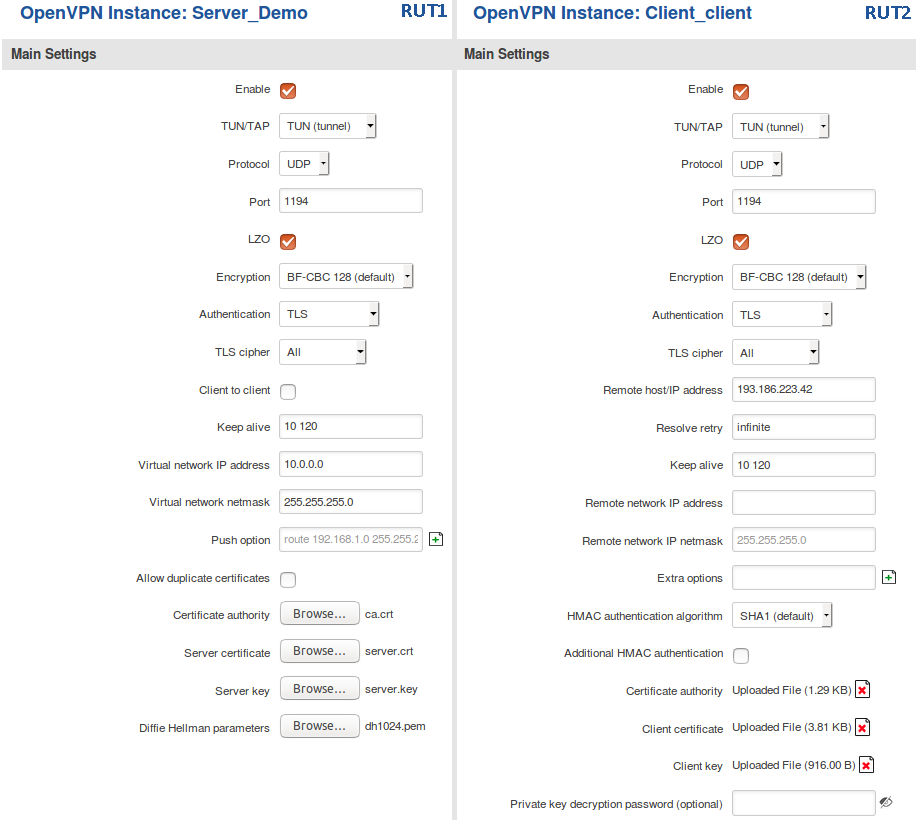
Now we can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: '''RUT1''' (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 193.186.223.42) and '''RUT2''' (Client; LAN IP: 192.168.2.1): | |||
[[File:Tls client server.png]] | |||
==Static key Authentication== | ==Static key Authentication== | ||
Revision as of 09:06, 9 March 2018
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
Summary
This article contains various OpenVPN configuration examples that require more in depth explanations in order to achieve a successful configuration. All of the examples given concern two or more RUT routers. For more basic explanations on the OpenVPN WebUI section, visit our VPN manual page.
OpenVPN configuration type
Before configuring anything you should first know what type of OpenVPN connection suits your needs the best. The key things to be considered here are the type of connection (TUN (tunnel) or TAP (bridged)), the data transfer protocol (User Datagram Protocol (UDP) or Transmission Control Protocol (TCP)) and authentication (TLS or Static key). Here is a short overview of the differences:
- Type
- TUN (tunnel) - simulates a network layer device and it operates with layer 3 packets like IP packets. TUN is used for routing and connecting multiple clients to a single server.
- TAP (bridged) - simulates a link layer device and it operates with layer 2 packets like Ethernet frames. TAP is used for creating a network bridge between 'two Ethernet segments in different locations.
- Protocol
- UDP - is used by apps to deliver a faster stream of information by doing away with error-checking.
- TCP - a suite of protocols used by devices to communicate over the Internet and most local networks. It provides apps a way to deliver (and receive) an ordered and error-checked stream of information packets over the network.
- Authentication
- TLS - uses SSL/TLS + certificates for authentication and key exchange.
- Static key - use a pre-shared Static key.
An overview of most of these types is provided in this article. Concerning TCP vs UDP, we will be using UDP for all examples. Choosing between TCP and UDP doesn't affect the rest of the configuration, so you can still follow the given examples no matter which protocol you are using. Simply choose the one that suits your purposes.
TLS Authentication
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the TLS Authentication method on RUT routers.
Generating TLS certificates/keys
A connection that uses TLS requires multiple certificates and keys for authentication:
* Server ** The root certificate file (Cetificate Authority) ** Server certificate ** Server key ** Diffie Hellman Parameters
* Client ** The root certificate file (Cetificate Authority) ** Client certificate ** Client key
Detailed instruction on how to obtain these files can be found here.
Once you have all the required files, continue following this section of the guide.
Configuration
Now we can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 193.186.223.42) and RUT2 (Client; LAN IP: 192.168.2.1):
Static key Authentication
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the Static key Authentication method on RUT routers.
Creating a Static key
First, lets create a Static key.