Template:Networking rutos manual vpn: Difference between revisions
Gytispieze (talk | contribs) No edit summary |
Gytispieze (talk | contribs) No edit summary |
||
| Line 30: | Line 30: | ||
To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the OpenVPN client's configuration fields: | To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the OpenVPN client's configuration fields: | ||
[[File: | [[File:Networking_trb2_vpn_openvpn_client_configuration_v3.png|border|class=tlt-border|]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 102: | Line 102: | ||
<td>Yes {{!}} No {{!}} None; default: <b>None</b></td> | <td>Yes {{!}} No {{!}} None; default: <b>None</b></td> | ||
<td>Turns LZO data compression on or off.</td> | <td>Turns LZO data compression on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Authentication</td> | <td>Authentication</td> | ||
<td> | <td>Static key {{!}} TLS {{!}} TLS/Password {{!}} Password ; default: <b>Static key</b></td> | ||
<td>Authentication mode, used to secure data sessions. | <td>Authentication mode, used to secure data sessions. | ||
<ul> | <ul> | ||
| Line 125: | Line 120: | ||
</ul> | </ul> | ||
</td> | </td> | ||
</tr> | |||
<tr> | |||
<td>Encryption</td> | |||
<td>DES-CBC 64 {{!}} RC2-CBC 128 {{!}} DES-EDE-CBC 128 {{!}} DES-EDE3-CBC 192 {{!}} DESX-CBC 192 {{!}} BF-CBC 128 {{!}} RC2-40-CBC 40 {{!}} CAST5-CBC 128 {{!}} RC2-40CBC 40 {{!}} CAST5-CBC 128 {{!}} RC2-64-CBC 64{{!}} AES-128-CBC 128 {{!}} AES-192-CBC 192 {{!}} AES-256-CBC 256 {{!}} none; default: <b>BF-CBC 128</b></td> | |||
<td>Algorithm used for packet encryption.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 172: | Line 172: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC authentication algorithm</td> | |||
<td>none {{!}} SHA1 {{!}} SHA256 {{!}} SHA384 {{!}} SHA512; default: <b>SHA1</b></td> | |||
<td>HMAC authentication algorithm type.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: #0054a6;">Password:</span> | <td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> Additional HMAC authentication</td> | ||
<td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td> | <td>An additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Extra options</td> | <td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC authentication key</td> | ||
<td>string; default: <b>none</b></td> | <td>.key file; default: <b>none</b></td> | ||
<td>Extra OpenVPN options to be used by the OpenVPN instance.</td> | <td>Uploads an HMAC authentication key file.</td> | ||
</tr> | |||
<tr> | |||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC key direction</td> | |||
<td>0 {{!}} 1 {{!}} none; default: <b>1</b></td> | |||
<td>The value of the key direction parameter should be complementary on either side (client and server) of the connection. If one side uses <i>0</i>, the other side should use <i>1</i>, or both sides should omit the parameter altogether.</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color: #0054a6;">Password:</span> User name</td> | |||
<td>string; default: <b>none</b></td> | |||
<td>Username used for authentication to the OpenVPN server.</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color: #0054a6;">Password:</span> Password</td> | |||
<td>string; default: <b>none</b></td> | |||
<td>Password used for authentication to the OpenVPN server.</td> | |||
</tr> | |||
<tr> | |||
<td>Extra options</td> | |||
<td>string; default: <b>none</b></td> | |||
<td>Extra OpenVPN options to be used by the OpenVPN instance.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 192: | Line 212: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> Certificate authority</td> | |||
<td>.ca file; default: <b>none</b></td> | |||
<td>Certificate authority is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: red;">TLS:</span> Client certificate</td> | |||
<td>.crt file; default: <b>none</b></td> | |||
<td><span style="color: red;">TLS:</span> Client certificate</td> | |||
<td>.crt file; default: <b>none</b></td> | |||
<td>Client certificate is a type of digital certificate that is used by client systems to make authenticated requests to a remote server. Client certificates play a key role in many mutual authentication designs, providing strong assurances of a requester's identity.</td> | <td>Client certificate is a type of digital certificate that is used by client systems to make authenticated requests to a remote server. Client certificates play a key role in many mutual authentication designs, providing strong assurances of a requester's identity.</td> | ||
</tr> | </tr> | ||
| Line 258: | Line 258: | ||
To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the OpenVPN server's configuration fields: | To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the OpenVPN server's configuration fields: | ||
[[File: | [[File:Networking_rutx_vpn_openvpn_server_configuration_v3.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 294: | Line 294: | ||
<li><b>User Datagram Protocol</b> (<b>UDP</b>) - packets are sent to the recipient without error-checking or back-and-forth quality control, meaning that when packets are lost, they are gone forever. This makes it less reliable but faster than TCP; therefore, it should be used when transfer speed is crucial (for example, video streaming, live calls).</li> | <li><b>User Datagram Protocol</b> (<b>UDP</b>) - packets are sent to the recipient without error-checking or back-and-forth quality control, meaning that when packets are lost, they are gone forever. This makes it less reliable but faster than TCP; therefore, it should be used when transfer speed is crucial (for example, video streaming, live calls).</li> | ||
</ul> | </ul> | ||
</td> | </td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 305: | Line 305: | ||
<td>Yes {{!}} No {{!}} None; default: <b>None</b></td> | <td>Yes {{!}} No {{!}} None; default: <b>None</b></td> | ||
<td>Turns LZO data compression on or off.</td> | <td>Turns LZO data compression on or off.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Authentication</td> | <td>Authentication</td> | ||
<td> | <td>Static key {{!}} TLS {{!}} TLS/Password {{!}} Password ; default: <b>Static key</b></td> | ||
<td>Authentication mode, used to secure data sessions. | <td>Authentication mode, used to secure data sessions. | ||
<ul> | <ul> | ||
| Line 324: | Line 319: | ||
</ul>All mentioned certificates can be generated using OpenVPN or Open SSL utilities on any type of host machine. One of the most popular utilities used for this purpose is called Easy-RSA. | </ul>All mentioned certificates can be generated using OpenVPN or Open SSL utilities on any type of host machine. One of the most popular utilities used for this purpose is called Easy-RSA. | ||
</li> | </li> | ||
<li><b>Password</b> is a simple username/password based authentication where the owner of the OpenVPN server provides the login data.</li> | |||
<li><b>TLS/Password</b> uses both TLS and username/password authentication.</li> | <li><b>TLS/Password</b> uses both TLS and username/password authentication.</li> | ||
</ul> | </ul> | ||
| Line 329: | Line 325: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: purple;">Static key:</span> Local tunnel endpoint IP</td> | <td>Encryption</td> | ||
<td>DES-CBC 64 {{!}} RC2-CBC 128 {{!}} DES-EDE-CBC 128 {{!}} DES-EDE3-CBC 192 {{!}} DESX-CBC 192 {{!}} BF-CBC 128 {{!}} RC2-40-CBC 40 {{!}} CAST5-CBC 128 {{!}} RC2-40CBC 40 {{!}} CAST5-CBC 128 {{!}} RC2-64-CBC 64{{!}} AES-128-CBC 128 {{!}} AES-192-CBC 192 {{!}} AES-256-CBC 256 {{!}} none; default: <b>BF-CBC 128</b></td> | |||
<td>Algorithm used for packet encryption.</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color: purple;">Static key:</span> Local tunnel endpoint IP</td> | |||
<td>ip; default: <b>none</b></td> | <td>ip; default: <b>none</b></td> | ||
<td>IP address of the local OpenVPN network interface.</td> | <td>IP address of the local OpenVPN network interface.</td> | ||
| Line 394: | Line 395: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: #0054a6;">TLS/Password:</span> | <td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC authentication algorithm</td> | ||
<td> | <td>none {{!}} SHA1 {{!}} SHA256 {{!}} SHA384 {{!}} SHA512; default: <b>SHA1</b></td> | ||
<td> | <td>HMAC authentication algorithm type.</td> | ||
</tr> | |||
<tr> | |||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> Additional HMAC authentication</td> | |||
<td>off {{!}} on; default: <b>off</b></td> | |||
<td>An additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks.</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC authentication key</td> | |||
<td>.key file; default: <b>none</b></td> | |||
<td>Uploads an HMAC authentication key file.</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color: red;">TLS</span>/<span style="color: #0054a6;">Password:</span> HMAC key direction</td> | |||
<td>0 {{!}} 1 {{!}} none; default: <b>1</b></td> | |||
<td>The value of the key direction parameter should be complementary on either side (client and server) of the connection. If one side uses <i>0</i>, the other side should use <i>1</i>, or both sides should omit the parameter altogether.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td><span style="color: #0054a6;">TLS/Password:</span> | <td><span style="color: #0054a6;">TLS/Password:</span>Usernames & Passwords</td> | ||
<td> | <td>text file; default: <b>none</b></td> | ||
<td> | <td>File containing usernames and passwords against which the server can authenticate clients. Each username and password pair should be placed on a single line and separated by a space.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 508: | Line 524: | ||
To begin configuration, click the button that looks like a pencil located next to the instance. Refer to the figure and table below for information on the fields located in the GRE instance configuration section. | To begin configuration, click the button that looks like a pencil located next to the instance. Refer to the figure and table below for information on the fields located in the GRE instance configuration section. | ||
[[File: | [[File:Networking_rutx_vpn_gre_gre_configuration_main_settings_v3.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 523: | Line 539: | ||
<tr> | <tr> | ||
<td>Tunnel source</td> | <td>Tunnel source</td> | ||
<td>network interface; default: <b> | <td>network interface; default: <b>LAN</b></td> | ||
<td>Network interface used to establish the GRE Tunnel.</td> | <td>Network interface used to establish the GRE Tunnel.</td> | ||
</tr> | </tr> | ||
| Line 533: | Line 549: | ||
<tr> | <tr> | ||
<td>MTU</td> | <td>MTU</td> | ||
<td>integer; default: <b>1476</b></td> | <td>integer [68..9200]; default: <b>1476</b></td> | ||
<td>Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction.</td> | <td>Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 553: | Line 564: | ||
<tr> | <tr> | ||
<td>Path MTU Discovery</td> | <td>Path MTU Discovery</td> | ||
<td>off {{!}} on; default: <b> | <td>off {{!}} <span style="color:blue">on</span>; default: <b>off</b></td> | ||
<td>When unchecked, sets the <i>nopmtudisc</i> option for tunnel. Can not be used together with the TTL option.</td> | <td>When unchecked, sets the <i>nopmtudisc</i> option for tunnel. Can not be used together with the TTL option.</td> | ||
</tr> | |||
<tr> | |||
<td><span style="color:blue">TTL</span></td> | |||
<td>integer [0..255]; default: <b>255</b></td> | |||
<td>Sets a custom TTL (Time to Live) value for encapsulated packets. TTL is a field in the IP packet header which is initially set by the sender and decreased by 1 on each hop. When it reaches 0 it is dropped and the last host to receive the packet sends an ICMP "Time Exceeded" message back to the source.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Keep alive</td> | <td>Keep alive</td> | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} <span style="color:red">on</span>; default: <b>off</b></td> | ||
<td>Turns "keep alive" on or off. The "keep alive" feature sends packets to the remote instance in order to determine the health of the connection. If no response is received, the device will attempt to re-establish the tunnel.</td> | <td>Turns "keep alive" on or off. The "keep alive" feature sends packets to the remote instance in order to determine the health of the connection. If no response is received, the device will attempt to re-establish the tunnel.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Keep alive interval</td> | <td><span style="color:red">Keep alive interval</span></td> | ||
<td>integer [0..255]; default: <b>none</b></td> | <td>integer [0..255]; default: <b>none</b></td> | ||
<td>Frequency (in seconds) at which "keep alive" packets are sent to the remote instance.</td> | <td>Frequency (in seconds) at which "keep alive" packets are sent to the remote instance.</td> | ||
| Line 632: | Line 648: | ||
<tr> | <tr> | ||
<td>Authentication method</td> | <td>Authentication method</td> | ||
<td>Pre-shared key {{!}} X.509; default: <b>Pre-shared key</b></td> | <td>Pre-shared key {{!}} X.509 {{!}} EAP; default: <b>Pre-shared key</b></td> | ||
<td>Specify authentication method. Choose between Pre-shared key and X.509 certificates.</td> | <td>Specify authentication method. Choose between Pre-shared key and X.509 certificates.</td> | ||
</tr> | </tr> | ||
| Line 640: | Line 656: | ||
<td>A shared password used for authentication between IPsec peers before a secure channel is established.</td> | <td>A shared password used for authentication between IPsec peers before a secure channel is established.</td> | ||
</tr> | </tr> | ||
<!-- removed on 7.0, to return | <!-- removed on 7.0, to return in the future <tr> | ||
<td><span style="color:darkred">Certificate files from device</span></td> | <td><span style="color:darkred">Certificate files from device</span></td> | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
| Line 716: | Line 732: | ||
<tr> | <tr> | ||
<td>Type</td> | <td>Type</td> | ||
<td> | <td>PSK {{!}} XAUTH {{!}} EAP {{!}} RSA; default: <b>PSK</b></td> | ||
<td>IPSec secret type.</br><b>NOTE:</b> XAUTH secrets are IKEv1 only.</td> | <td>IPSec secret type.</br><b>NOTE:</b> XAUTH secrets are IKEv1 only.</td> | ||
</tr> | </tr> | ||
| Line 759: | Line 775: | ||
---- | ---- | ||
[[File: | [[File:Networking_rutos_vpn_ipsec_connection_settings_general_settings_v2.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 811: | Line 827: | ||
</ul> | </ul> | ||
</td> | </td> | ||
</tr> | |||
<tr> | |||
<td>Enable XAUTH</td> | |||
<td>off {{!}} on; default: <b>off</b></td> | |||
<td>Enables XAUTH authentication before allowing access for remote users.</td> | |||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 1,485: | Line 1,506: | ||
<tr> | <tr> | ||
<td>Tunnel source</td> | <td>Tunnel source</td> | ||
<td>network interface; default: <b> | <td>network interface; default: <b>LAN</b></td> | ||
<td>Network interface used to establish the GRE Tunnel.</td> | <td>Network interface used to establish the GRE Tunnel.</td> | ||
</tr> | </tr> | ||
| Line 1,560: | Line 1,581: | ||
<tr> | <tr> | ||
<td>DH/PFS group</td> | <td>DH/PFS group</td> | ||
<td>MODP768 {{!}} MODP1024 {{!}} MODP1536 {{!}} MODP2048 {{!}} MODP3072 {{!}} MODP4096 {{!}} ECP192 {{!}} ECP224 {{!}} ECP256 {{!}} ECP384 {{!}} ECP521; default: <b> | <td>MODP768 {{!}} MODP1024 {{!}} MODP1536 {{!}} MODP2048 {{!}} MODP3072 {{!}} MODP4096 {{!}} ECP192 {{!}} ECP224 {{!}} ECP256 {{!}} ECP384 {{!}} ECP521; default: <b>MODP1024</b></td> | ||
<td>Diffie-Hellman (DH) group used in the key exchange process. Higher group numbers provide more security, but take longer and use more resources to compute the key. Must match with another incoming connection to establish IPSec. </td> | <td>Diffie-Hellman (DH) group used in the key exchange process. Higher group numbers provide more security, but take longer and use more resources to compute the key. Must match with another incoming connection to establish IPSec. </td> | ||
</tr> | </tr> | ||
| Line 1,586: | Line 1,607: | ||
<tr> | <tr> | ||
<td>NHRP network ID</td> | <td>NHRP network ID</td> | ||
<td>integer; default: <b> | <td>integer; default: <b>none</b></td> | ||
<td>An identifier used to define the NHRP domain. This is a local parameter and its value does not need to match the values specified on other domains. However, the NHRP ID is added to packets which arrive on the GRE interface; therefore, it may be helpful to use the same ID for troubleshooting purposes.</td> | <td>An identifier used to define the NHRP domain. This is a local parameter and its value does not need to match the values specified on other domains. However, the NHRP ID is added to packets which arrive on the GRE interface; therefore, it may be helpful to use the same ID for troubleshooting purposes.</td> | ||
</tr> | </tr> | ||
| Line 1,596: | Line 1,617: | ||
<tr> | <tr> | ||
<td>NHRP hold time</td> | <td>NHRP hold time</td> | ||
<td>integer; default: <b> | <td>integer; default: <b>none</b></td> | ||
<td>Specifies the holding time for NHRP Registration Requests and Resolution Replies sent from this interface or shortcut-target. The hold time is specified in seconds and defaults to two hours.</td> | <td>Specifies the holding time for NHRP Registration Requests and Resolution Replies sent from this interface or shortcut-target. The hold time is specified in seconds and defaults to two hours.</td> | ||
</tr> | </tr> | ||
| Line 1,605: | Line 1,626: | ||
In computer networking, <b>Layer 2 Tunneling Protocol</b> (<b>L2TP</b>) is a tunneling protocol used to support virtual private networks (VPNs). It is more secure than PPTP but, because it encapsulates the transferred data twice, but it is slower and uses more CPU power. | In computer networking, <b>Layer 2 Tunneling Protocol</b> (<b>L2TP</b>) is a tunneling protocol used to support virtual private networks (VPNs). It is more secure than PPTP but, because it encapsulates the transferred data twice, but it is slower and uses more CPU power. | ||
===L2TP | ===L2TP Global Settings=== | ||
---- | |||
[[File:Networking_rutos_manual_vpn_l2tp_global_settings_v1.png|border|class=tlt-border]] | |||
<table class="nd-mantable"> | |||
<tr> | |||
<th>Field</th> | |||
<th>Value</th> | |||
<th>Description</th> | |||
</tr> | |||
<tr> | |||
<td>Require CHAP</td> | |||
<td>off {{!}} on; default: <b>on</b></td> | |||
<td>When enabled, peer will be required to authenticate itself using standard CHAP authentication.</td> | |||
</tr> | |||
<tr> | |||
<td>Refuse PAP</td> | |||
<td>off {{!}} on; default: <b>on</b></td> | |||
<td>When enabled, pppd will not agree to authenticate itself to the peer using Password Authentication Protocol (PAP).</td> | |||
</tr> | |||
</table> | |||
===L2TP Client=== | |||
---- | ---- | ||
An <b>L2TP client</b> is an entity that initiates a connection to an L2TP server. To create a new client instance, go to the <i>Services → VPN → L2TP</i> section, select <i>Role: Client</i>, enter a custom name and click the 'Add' button. An L2TP client instance with the given name will appear in the "L2TP Configuration" list. | An <b>L2TP client</b> is an entity that initiates a connection to an L2TP server. To create a new client instance, go to the <i>Services → VPN → L2TP</i> section, select <i>Role: Client</i>, enter a custom name and click the 'Add' button. An L2TP client instance with the given name will appear in the "L2TP Configuration" list. | ||
| Line 1,611: | Line 1,654: | ||
To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the L2TP client's configuration fields: | To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the L2TP client's configuration fields: | ||
[[File: | [[File:Networking_rutos_manual_vpn_l2tp_client_v1.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,640: | Line 1,683: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Default route</td> | <td>CHAP Secret</td> | ||
<td>string; default: <b>none</b></td> | |||
<td>A secret used for L2TP Tunnel Authentication.</td> | |||
</tr> | |||
<tr> | |||
<td>Default route</td> | |||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>When turned on, this connection will become device default route. This means that all traffic directed to the Internet will go through the L2TP server and the server's IP address will be seen as this device's source IP to other hosts on the Internet.{{#ifeq:{{{series}}}|RUTX|<br><b>NOTE</b>: this can only be used when [[{{{name}}} Failover|Failover]] is turned off.}}</td> | <td>When turned on, this connection will become device default route. This means that all traffic directed to the Internet will go through the L2TP server and the server's IP address will be seen as this device's source IP to other hosts on the Internet.{{#ifeq:{{{series}}}|RUTX|<br><b>NOTE</b>: this can only be used when [[{{{name}}} Failover|Failover]] is turned off.}}</td> | ||
| Line 1,646: | Line 1,694: | ||
</table> | </table> | ||
===L2TP | ===L2TP Server=== | ||
---- | ---- | ||
An <b>L2TP server</b> is an entity that waits for incoming connections from L2TP clients. To create a new server instance, go to the <i>Services → VPN → L2TP</i> section, select <i>Role: Server</i>, enter a custom name and click the 'Add' button. An L2TP server instance with the given name will appear in the "L2TP Configuration" list. Only one L2TP server instance is allowed to be added. | An <b>L2TP server</b> is an entity that waits for incoming connections from L2TP clients. To create a new server instance, go to the <i>Services → VPN → L2TP</i> section, select <i>Role: Server</i>, enter a custom name and click the 'Add' button. An L2TP server instance with the given name will appear in the "L2TP Configuration" list. Only one L2TP server instance is allowed to be added. | ||
| Line 1,654: | Line 1,702: | ||
To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the L2TP server's configuration fields: | To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the L2TP server's configuration fields: | ||
[[File: | [[File:Networking_rutx_vpn_l2tp_server_configuration_v3.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,681: | Line 1,729: | ||
<td>ip; default: <b>192.168.0.30</b></td> | <td>ip; default: <b>192.168.0.30</b></td> | ||
<td>L2TP IP address leases will end with the address specified in this field.</td> | <td>L2TP IP address leases will end with the address specified in this field.</td> | ||
</tr> | |||
<tr> | |||
<td>Enable CHAP</td> | |||
<td>off {{!}} <span style="color:blue">on</span>; default: <b>user</b></td> | |||
<td>Enables Challenge-Handshake Authentication Protocol for L2TP</td> | |||
</tr> | |||
<tr> | |||
<td><span style="color:blue">CHAP Secret</span></td> | |||
<td>string; default: <b>user</b></td> | |||
<td>A secret used for L2TP Tunnel Authentication.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
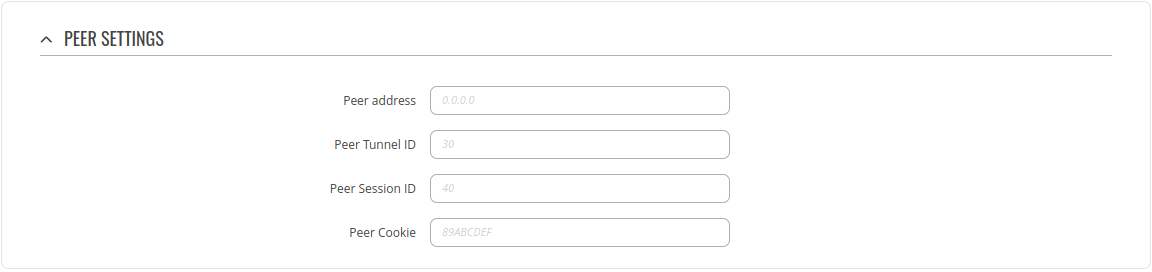
| Line 1,768: | Line 1,826: | ||
<td>Must be specified in hexidecimal form and be length of 8 or 16. eg.: 89ABCDEF. It must match other end Cookie.</td> | <td>Must be specified in hexidecimal form and be length of 8 or 16. eg.: 89ABCDEF. It must match other end Cookie.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
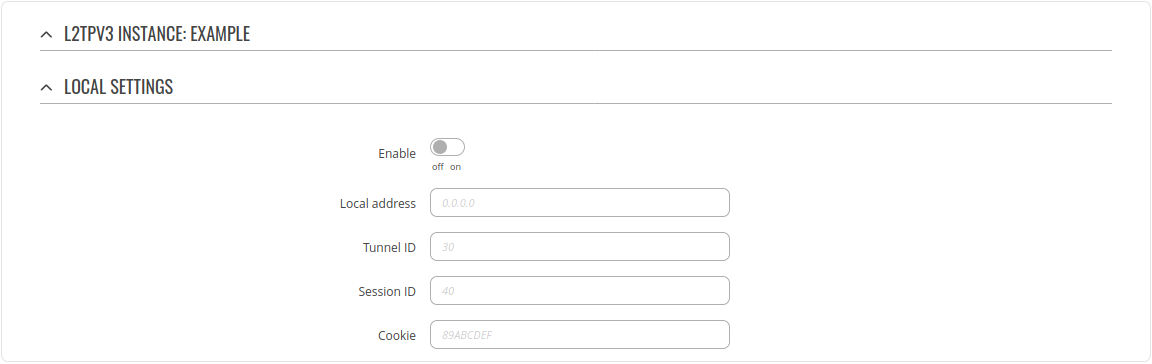
===Instance Settings=== | ===Instance Settings=== | ||
---- | ---- | ||
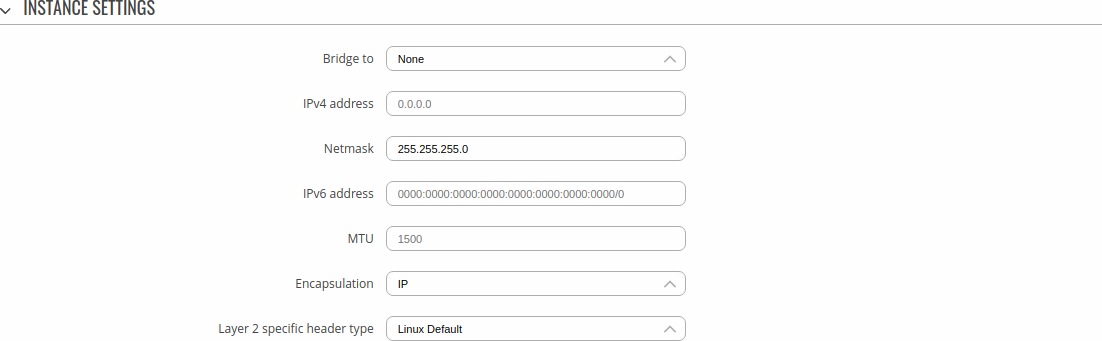
[[File: | [[File:Networking_rutos_vpn_l2tpv3_configuration_instance_settings_v2.png]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
<tr> | <tr> | ||
<th>Field</th> | <th>Field</th> | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
</tr> | |||
<tr> | |||
<td>Bridge to</td> | |||
<td>None {{!}} LAN; default: <b>None</b></td> | |||
<td>Peer Endpoint IP address.</td> | |||
</tr> | |||
<tr> | |||
<td>IPv4 Address</td> | |||
<td>ip4; default: <b>none</b></td> | |||
<td>IPv4 address of standalone L2TPv3 interface.<td> | |||
</tr> | |||
<tr> | |||
<td>Netmask</td> | |||
<td>netmask; default: <b>255.255.255.0</b></td> | |||
<td>Netmask of standalone L2TPv3 interface. </td> | |||
</tr> | |||
<tr> | |||
<td>IPv6 Address</td> | |||
<td>ip6; default: <b>none</b></td> | |||
<td>IPv6 address of standalone L2TPv3 interface. CIDR notation: address/prefix.<td> | |||
</tr> | |||
<tr> | |||
<td>MTU</td> | |||
<td>integer [64..9000]; default: <b>none</b></td> | |||
<td>Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction.</td> | |||
</tr> | |||
<tr> | |||
<td>Encapsulation</td> | |||
<td>IP {{!}} <span style="color:blue">UDP</span>; default: <b>IP</b></td> | |||
<td>Specify technology to use when connecting to other end.</td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td> | <td><span style="color:blue">UDP source port</span></td> | ||
<td> | <td>port; default: <b>none</b></td> | ||
<td> | <td>Specifies source port.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td> | <td><span style="color:blue">UDP destination port</span></td> | ||
<td>port; default: <b>none</b></td> | |||
<td>Specifies destination port.</td> | |||
<td> | |||
<td> | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 1,865: | Line 1,938: | ||
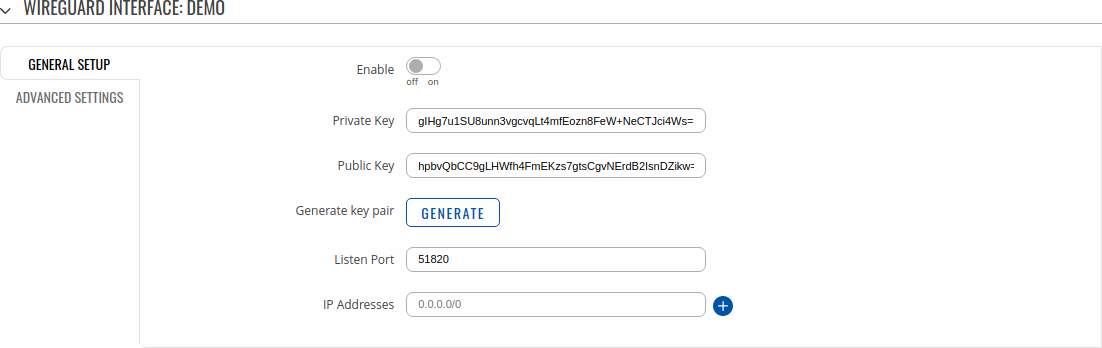
Private keys and generate them, specify Port and IP addresses for communication. | Private keys and generate them, specify Port and IP addresses for communication. | ||
[[File: | [[File:Networking_rutx_vpn_wireguard_instance_general_v2.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,880: | Line 1,953: | ||
<tr> | <tr> | ||
<td>Private Key</td> | <td>Private Key</td> | ||
<td>string; default: <b> | <td>Base64-encoded string; default: <b>generated</b></td> | ||
<td>Private Key used in authentication.</td> | <td>Private Key used in authentication. Required.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Public Key</td> | <td>Public Key</td> | ||
<td>string; default: <b> | <td>Base64-encoded string; default: <b>generated</b></td> | ||
<td>Public Key used in authentication.</td> | <td>Public Key used in authentication.</td> | ||
</tr> | </tr> | ||
| Line 1,895: | Line 1,968: | ||
<tr> | <tr> | ||
<td>Listen Port</td> | <td>Listen Port</td> | ||
<td>integer [0..65535]; default: <b> | <td>integer [0..65535]; default: <b>51820</b></td> | ||
<td>Specify port to listen for incomming connections. It will be set to a random integer if left empty.</td> | <td>Specify port to listen for incomming connections. It will be set to a random integer if left empty.</td> | ||
</tr> | </tr> | ||
Revision as of 17:19, 28 March 2022
Template:Networking rutos manual fw disclosure
Summary
Virtual Private Network (VPN) is a method of connecting multiple private networks across the Internet. VPNs can serve to achieve many different goals, but some of its main purposes are:
- access between remote private networks;
- data encryption;
- anonymity when browsing the Internet.
This page is an overview of the different types of VPNs supported by {{{name}}} devices.
OpenVPN
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It is often regarded as being the most universal VPN protocol because of its flexibility, support of SSL/TLS security, multiple encryption methods, many networking features and compatibility with most OS platforms.
{{{name}}} devices run OpenVPN version 2.5.3.
OpenVPN Client
An OpenVPN client is an entity that initiates a connection to an OpenVPN server. To create a new client instance, go to the Services → VPN → OpenVPN section, select Role: Client, enter a custom name and click the 'Add' button. An OpenVPN client instance with the given name will appear in the "OpenVPN Configuration" list.
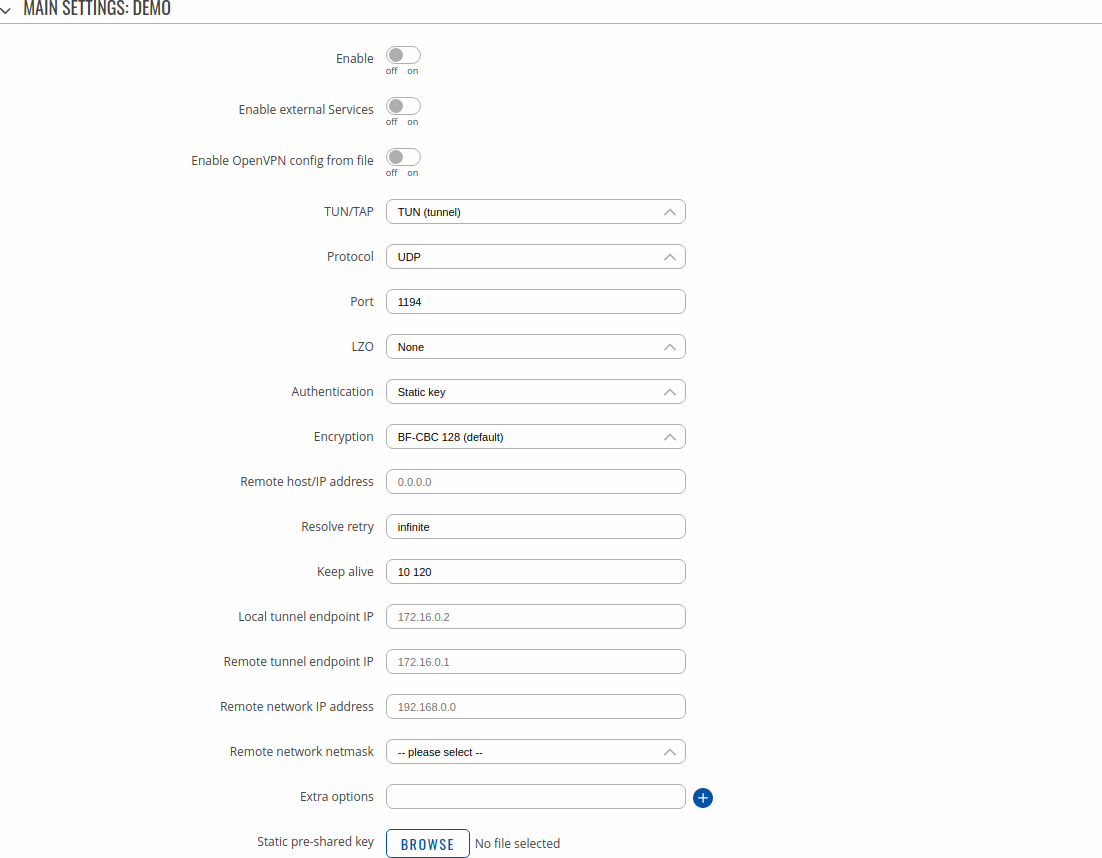
To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the OpenVPN client's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the OpenVPN instance on or off. |
| Enable external Services | off | on; default: off | Turns the OpenVPN external Services on or off. |
| VPN providers | Express VPN | Nord VPN; default: Nord VPN | Represents a list of available VPN providers. |
| VPN servers | United Kingdom | USA | Australia | South Africa | Custom; default: United Kingdom | Represents a list of available VPN servers. |
| Enable OpenVPN config from file | off | on; default: off | Enables or disables custom OpenVPN config from file. |
| Username | string; default: none | Username used for authentication to the VPN server. |
| Password | string; default: none | Password used for authentication to the VPN server. |
| TUN/TAP | TUN (tunnel) | TAP (bridged); default: TUN (tunnel) | Virtual network device type.
|
| Protocol | UDP | TCP; default: UDP | Transfer protocol used by the OpenVPN connection.
|
| Port | integer [0..65535]; default: 1194 | TCP/UDP port number used for the connection. Make sure it matches the port number specified on the server side. NOTE: traffic on the selected port will be automatically allowed in the device firewall rules. |
| LZO | Yes | No | None; default: None | Turns LZO data compression on or off. |
| Authentication | Static key | TLS | TLS/Password | Password ; default: Static key | Authentication mode, used to secure data sessions.
|
| Encryption | DES-CBC 64 | RC2-CBC 128 | DES-EDE-CBC 128 | DES-EDE3-CBC 192 | DESX-CBC 192 | BF-CBC 128 | RC2-40-CBC 40 | CAST5-CBC 128 | RC2-40CBC 40 | CAST5-CBC 128 | RC2-64-CBC 64| AES-128-CBC 128 | AES-192-CBC 192 | AES-256-CBC 256 | none; default: BF-CBC 128 | Algorithm used for packet encryption. |
| TLS: TLS cipher | All | DHE+RSA | Custom; default: All | Packet encryption algorithm cipher. |
| TLS: Allowed TLS ciphers | All | DHE+RSA | Custom; default: All | A list of TLS ciphers accepted by this connection. |
| Remote host/IP address | ip; default: none | IP address or hostname of an OpenVPN server. |
| Resolve retry | integer | infinite; default: infinite | In case server hostname resolve fails, this field indicates the amount of time (in seconds) to retry the resolve. Specify infinite to retry indefinitely. |
| Keep alive | two integers separated by a space; default: none | Defines two time intervals: the first is used to periodically send ICMP requests to the OpenVPN server, the second one defines a time window, which is used to restart the OpenVPN service if no ICMP response is received during the specified time slice. When this value is specfiied on the OpenVPN server, it overrides the 'keep alive' values set on client instances. Example: 10 120 |
| Static key: Local tunnel endpoint IP | ip; default: none | IP address of the local OpenVPN network interface. |
| Static key: Remote tunnel endpoint IP | ip; default: none | IP address of the remote OpenVPN network (server) interface. |
| Remote network IP address | ip; default: none | LAN IP address of the remote network (server). |
| Remote network IP netmask | netmask; default: none | LAN IP subnet mask of the remote network (server). |
| TLS/Password: HMAC authentication algorithm | none | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | HMAC authentication algorithm type. |
| TLS/Password: Additional HMAC authentication | off | on; default: off | An additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks. |
| TLS/Password: HMAC authentication key | .key file; default: none | Uploads an HMAC authentication key file. |
| TLS/Password: HMAC key direction | 0 | 1 | none; default: 1 | The value of the key direction parameter should be complementary on either side (client and server) of the connection. If one side uses 0, the other side should use 1, or both sides should omit the parameter altogether. |
| Password: User name | string; default: none | Username used for authentication to the OpenVPN server. |
| Password: Password | string; default: none | Password used for authentication to the OpenVPN server. |
| Extra options | string; default: none | Extra OpenVPN options to be used by the OpenVPN instance. |
| Certificate files from device | off | on; default: off | Turn on this option if you want to select generated certificate files from device. |
| TLS/Password: Certificate authority | .ca file; default: none | Certificate authority is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. |
| TLS: Client certificate | .crt file; default: none | Client certificate is a type of digital certificate that is used by client systems to make authenticated requests to a remote server. Client certificates play a key role in many mutual authentication designs, providing strong assurances of a requester's identity. |
| TLS: Client key | .key file; default: none | Authenticates the client to the server and establishes precisely who they are. |
| TLS: Private key decryption password (optional) | string; default: none | A password used to decrypt the server's private key. Use only if server's .key file is encrypted with a password. |
| Static key: Static pre-shared key | .key file; default: none | Uploads a secret key file used for server–client authentication. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Authentication: TLS
- Purple for Authentication: Static key
- Blue for Authentication: Password
- After changing any of the parameters, don't forget to click the Save & Apply button located at the bottom-right side of the page.
OpenVPN Server
An OpenVPN server is an entity that waits for incoming connections from OpenVPN clients. To create a new server instance, go to the Services → VPN → OpenVPN section, select Role: Server, enter a custom name and click the 'Add' button. An OpenVPN server instance with the given name will appear in the "OpenVPN Configuration" list. Only one OpenVPN server instance is allowed to be added.
A server needs to have a public IP address in order to be available from the public network (the Internet).
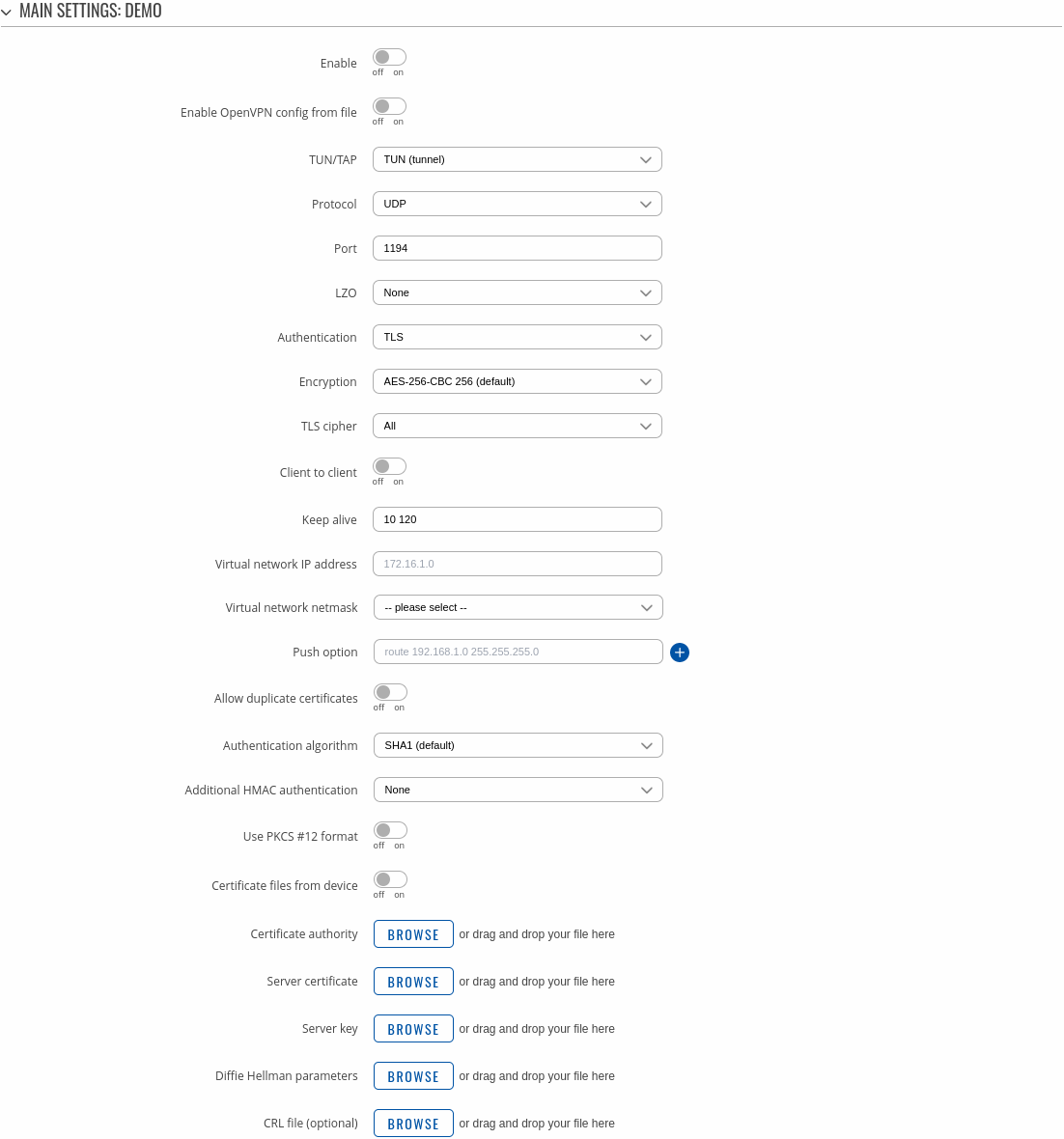
To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the OpenVPN server's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the OpenVPN instance on or off. |
| Enable OpenVPN config from file | off | on; default: off | Enables or disables custom OpenVPN config from file. |
| TUN/TAP | TUN (tunnel) | TAP (bridged); default: TUN (tunnel) | Virtual network device type.
|
| Protocol | UDP | TCP; default: UDP | Transfer protocol used by the OpenVPN connection.
|
| Port | integer [0..65535]; default: 1194 | TCP/UDP port number used for the connection. Make sure it matches the port number specified on the server side. NOTE: traffic on the selected port will be automatically allowed in device firewall rules. |
| LZO | Yes | No | None; default: None | Turns LZO data compression on or off. |
| Authentication | Static key | TLS | TLS/Password | Password ; default: Static key | Authentication mode, used to secure data sessions.
|
| Encryption | DES-CBC 64 | RC2-CBC 128 | DES-EDE-CBC 128 | DES-EDE3-CBC 192 | DESX-CBC 192 | BF-CBC 128 | RC2-40-CBC 40 | CAST5-CBC 128 | RC2-40CBC 40 | CAST5-CBC 128 | RC2-64-CBC 64| AES-128-CBC 128 | AES-192-CBC 192 | AES-256-CBC 256 | none; default: BF-CBC 128 | Algorithm used for packet encryption. |
| Static key: Local tunnel endpoint IP | ip; default: none | IP address of the local OpenVPN network interface. |
| Static key: Remote tunnel endpoint IP | ip; default: none | IP address of the remote OpenVPN network (client) interface. |
| Static key: Remote network IP address | ip; default: none | LAN IP address of the remote network (client). |
| Static key: Remote network IP netmask | netmask; default: none | LAN IP subnet mask of the remote network (client). |
| TLS/TLS/Password: TLS cipher | All | DHE+RSA | Custom; default: All | Packet encryption algorithm cipher. |
| TLS/Password: Allowed TLS ciphers | All | DHE+RSA | Custom; default: All | A list of TLS ciphers accepted by this connection. |
| TLS/TLS/Password: Client to client | off | on; default: off | Allows OpenVPN clients to communicate with each other on the VPN network. |
| TLS/TLS/Password: Keep alive | two integers separated by a space; default: none | Defines two time intervals: the first is used to periodically send ICMP requests to the OpenVPN server, the second one defines a time window, which is used to restart the OpenVPN service if no ICMP response is received during the specified time slice. When this value is specifiied on the OpenVPN server, it overrides the 'keep alive' values set on client instances. Example: 10 120 |
| TLS/TLS/Password: Virtual network IP address | ip4; default: none | IPv4 address of the OpenVPN network. |
| TLS/TLS/Password: Virtual network netmask | netmask; default: none | Subnet mask of the OpenVPN network. |
| TLS/TLS/Password: Virtual network IPv6 address | ip6; default: none | IPv6 address of the OpenVPN network. |
| TLS/TLS/Password: Push option | OpenVPN options; default: none | Push options are a way to "push" routes and other additional OpenVPN options to connecting clients. |
| TLS/TLS/Password: Allow duplicate certificates | off | on; default: off | When enabled allows multiple clients to connect using the same certificates. |
| TLS/Password: HMAC authentication algorithm | none | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | HMAC authentication algorithm type. |
| TLS/Password: Additional HMAC authentication | off | on; default: off | An additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks. |
| TLS/Password: HMAC authentication key | .key file; default: none | Uploads an HMAC authentication key file. |
| TLS/Password: HMAC key direction | 0 | 1 | none; default: 1 | The value of the key direction parameter should be complementary on either side (client and server) of the connection. If one side uses 0, the other side should use 1, or both sides should omit the parameter altogether. |
| TLS/Password:Usernames & Passwords | text file; default: none | File containing usernames and passwords against which the server can authenticate clients. Each username and password pair should be placed on a single line and separated by a space. |
| Static key: Static pre-shared key | .key file; default: none | Uploads a secret key file used for server–client authentication. |
| TLS/TLS/Password: Certificate authority | .ca file; default: none | Certificate authority is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. |
| TLS/TLS/Password: Server certificate | .crt file; default: none | A type of digital certificate that is used to identify the OpenVPN server. |
| TLS/TLS/Password: Server key | .key file; default: none | Authenticates clients to the server. |
| TLS/TLS/Password: Diffie Hellman parameters | .pem file; default: none | DH parameters define how OpenSSL performs the Diffie-Hellman (DH) key-exchange. |
| TLS/TLS/Password: CRL file (optional) | .pem file | .crl file; Default: none | A certificate revocation list (CRL) file is a list of certificates that have been revoked by the certificate authority (CA). It indicates which certificates are no longer acccepted by the CA and therefore cannot be authenticated to the server. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Authentication: TLS
- Purple for Authentication: Static key
- Blue for Authentication: TLS/Password
- After changing any of the parameters, don't forget to click the Save & Apply button located at the bottom-right side of the page.
TLS Clients
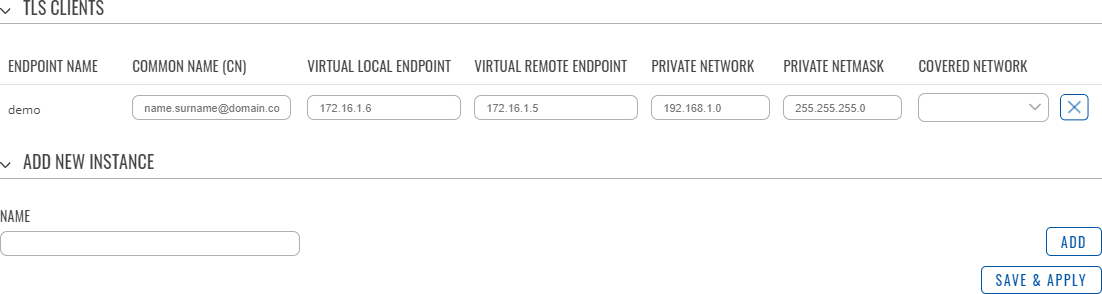
TLS Clients is a way to differentiate clients by their Common Names (CN), which are found in the client certificate file. It can be used to assign specific VPN addresses to corresponding clients and bind them to their LAN addresses, making the server aware of which client has which LAN IP address.
The TLS Clients section can be found in the OpenVPN Server configuration window, provided that the OpenVPN server uses TLS or TLS/Password authentication methods. To create a new TLS client, type in the new client‘s name in the text field found bellow the TLS Clients tab and click the 'Add' button. Refer to the figure and table below for information on the TLS Clients' configuration fields:
| Field | Value | Description |
|---|---|---|
| Endpoint name | string; default: none | A custom name for the client. |
| Common name (CN) | string; default: none | Client’s Common Name (CN) found in the client certificate file. |
| Virtual local endpoint | ip; default: none | Client’s local address in the virtual network. |
| Virtual remote endpoint | ip; default: none | Client’s remote address in the virtual network. |
| Private network | ip; default: none | Client’s private network (LAN) IP address. |
| Private netmask | netmask; default: none | Client’s private network (LAN) IP netmask. |
| Covered Network | network(); default: none | Selects which networks should be made accessible to this client. |
GRE
Generic Routing Encapsulation (GRE) is a tunneling protocol used to establish point-to-point connections between remote private networks. GRE tunnels encapsulate data packets in order to route other protocols over IP networks.
GRE: Main & Tunnel Settings
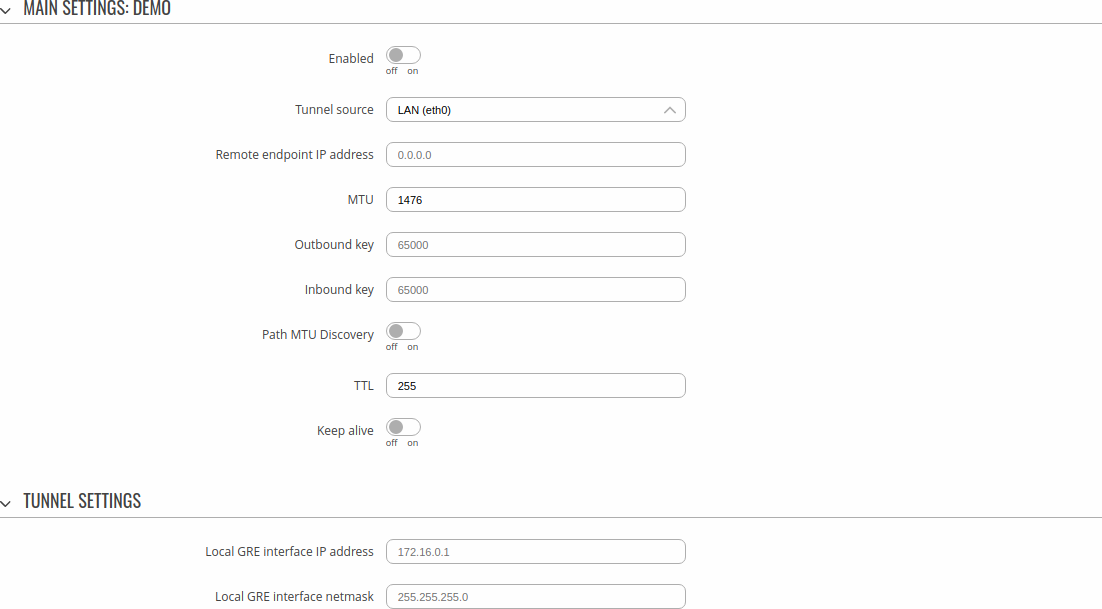
To create a new GRE instance, go to the Services → VPN → GRE section, enter a custom name and click the 'Add' button. A GRE instance with the given name will appear in the "GRE Configuration" list.
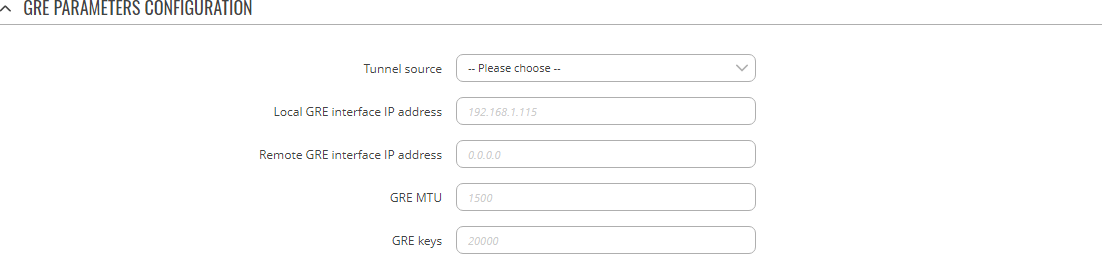
To begin configuration, click the button that looks like a pencil located next to the instance. Refer to the figure and table below for information on the fields located in the GRE instance configuration section.
| Field | Value | Description |
|---|---|---|
| Enabled | off | on; default: off | Turns the GRE instance on or off. |
| Tunnel source | network interface; default: LAN | Network interface used to establish the GRE Tunnel. |
| Remote endpoint IP address | ip; default: none | External IP address of another GRE instance used to establish the initial connection between peers. |
| MTU | integer [68..9200]; default: 1476 | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| Outbound key | integer [0..65535]; default: none | A key used to identify outgoing packets. This value should match the "Inbound key" value set on the opposite GRE instance or both key values should be omitted on both sides. |
| Inbound key | integer [0..65535]; default: none | A key used to identify incoming packets. This value should match the "Outbound key" value set on the opposite GRE instance or both key values should be omitted on both sides. |
| Path MTU Discovery | off | on; default: off | When unchecked, sets the nopmtudisc option for tunnel. Can not be used together with the TTL option. |
| TTL | integer [0..255]; default: 255 | Sets a custom TTL (Time to Live) value for encapsulated packets. TTL is a field in the IP packet header which is initially set by the sender and decreased by 1 on each hop. When it reaches 0 it is dropped and the last host to receive the packet sends an ICMP "Time Exceeded" message back to the source. |
| Keep alive | off | on; default: off | Turns "keep alive" on or off. The "keep alive" feature sends packets to the remote instance in order to determine the health of the connection. If no response is received, the device will attempt to re-establish the tunnel. |
| Keep alive interval | integer [0..255]; default: none | Frequency (in seconds) at which "keep alive" packets are sent to the remote instance. |
| Local GRE interface IP address | ip; default: none | IP address of the local GRE Tunnel network interface. |
| Local GRE interface netmask | netmask; default: none | Subnet mask of the local GRE Tunnel network interface. |
GRE: Routing Settings
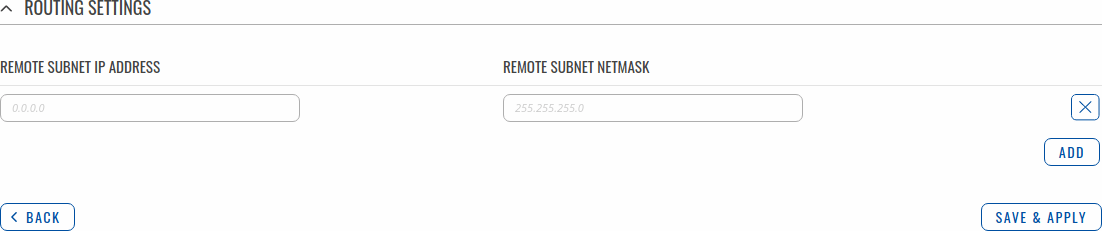
Routing settings are used to configure routes to networks that are behind the device that hosts the opposite GRE instance. To add a new route, simply click the 'Add' button. For information on configuring the route refer to the figure and table below.
| Field | Value | Description |
|---|---|---|
| Remote subnet IP address | ip; default: none | IP address of the network behind the device that hosts the remote GRE instance. |
| Remote subnet netmask | netmask; default: none | Subnet mask of the network behind the device that hosts the remote GRE instance. |
IPsec
To create a new IPsec instance, go to the Services → VPN → IPsec section, enter a custom name and click the 'Add' button. An IPsec instance with the given name will appear in the "IPsec Configuration" list.
To begin configuration, click the button that looks like a pencil located next to the instance.
IPsec Instance
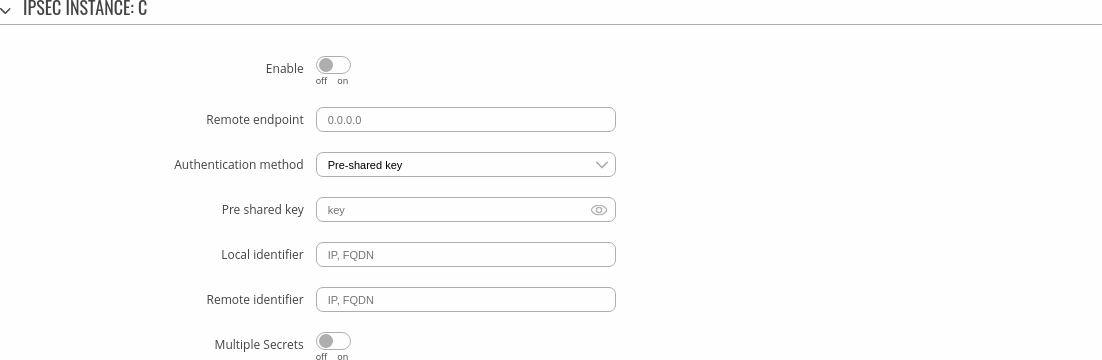
The general settings section is used to configure the main IPsec parameters. Refer to the figure and table below for information on the configuration fields located in the general settings section.
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the IPsec instance on or off. |
| Remote endpoint | host | ip; default: none | IP address or hostname of the remote IPsec instance. |
| Authentication method | Pre-shared key | X.509 | EAP; default: Pre-shared key | Specify authentication method. Choose between Pre-shared key and X.509 certificates. |
| Pre-shared key: Pre shared key | string; default: none | A shared password used for authentication between IPsec peers before a secure channel is established. |
| X.509: Key | .der file; default: none | A public key file. |
| X.509: Local Certificate | .der file; default: none | A local certificate file. |
| X.509: CA Certificate | .der file; default: none | A certificate authority file. |
| Local identifier | ip | string; default: none | Defines how the user (left participant) will be identified during authentication.
|
| Remote identifier | ip | string; default: none | Defines how the right participant will be identified during authentication.
|
| Multiple secrets | off | on; default: off | Enable to show Global Secret Settings section for configuring multiple secrets. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Chocolate for Authentication method: Pre-shared key
- Dark red for Authentication method: X.509
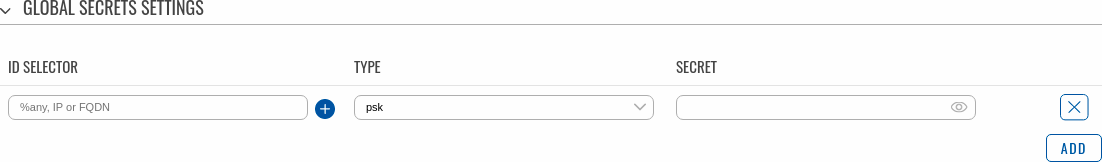
Global Secrets Settings
This section is displayed when Multiple secrets is enabled in General settings. You can add new instances by pressing Add.
| Field | Value | Description |
|---|---|---|
| ID Selector | %any, IP or FQDN; default: none | Each secret can be preceded by a list of optional ID selectors. A selector is an IP address, a Fully Qualified Domain Name, user@FQDN or %any. When using IKEv1 use IP address. NOTE: IKEv1 only supports IP address ID selector. |
| Type | PSK | XAUTH | EAP | RSA; default: PSK | IPSec secret type. NOTE: XAUTH secrets are IKEv1 only. |
| Secret | string; default: none | A shared password to authenticate between the peers. Minimum length is 5 symbols. All characters are allowed except `. |
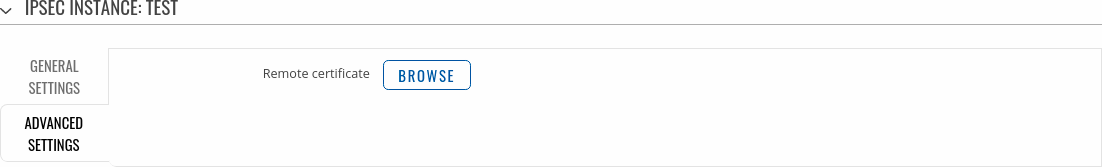
Advanced Settings
The Advanced settings section is only visible when X.509 is selected as Authentication method.
| Field | Value | Description |
|---|---|---|
| Remote Certificate | .crt file; default: none | Selects a certificate file from a computer. |
IPsec Instance: Connection Settings
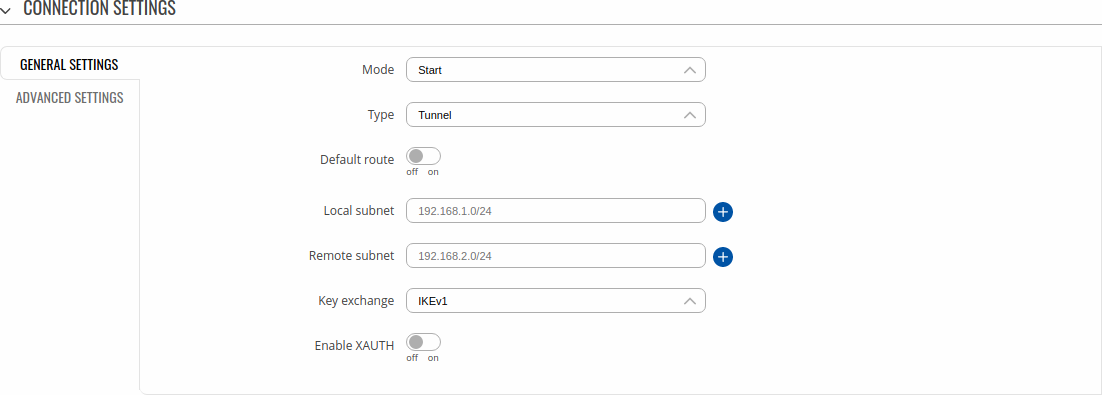
The connection settings section is used to configure the main parameters of an IPsec connection. Refer to the figure and table below for information on the configuration fields located in the connection settings section.
General Settings
| Field | Value | Description |
|---|---|---|
| Mode | Start | Add | Route; default: Start | Specifies which operation will be done automatically at IPSec startup. |
| Type | Tunnel | Transport; default: Tunnel | Type of connection.
|
| Tunnel: Default route | off | on; default: off | Turn on to route all traffic through IPSec tunnel. |
| Tunnel: Local subnet | ip/netmask | default: none | Local IP address and subnet mask used to determine which part of the network can be accessed in the VPN network. Netmask range [0..32]. If left empty, IP address will be selected automatically. |
| Tunnel: Remote subnet | ip/netmask; default: none | Remote network IP address and subnet mask used to determine which part of the network can be accessed in the VPN network. Netmask range [0..32]. This value must differ from the device’s LAN IP. |
| Transport: Bind to | GRE interface; default: none | Bind to GRE interface to create GRE over IPsec. |
| Key exchange | IKEv1 | IKEv2; default: IKEv1 | Internet Key Exchange (IKE) version used for key exchange.
|
| Enable XAUTH | off | on; default: off | Enables XAUTH authentication before allowing access for remote users. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Type: Tunnel
- Purple for Type: Transport
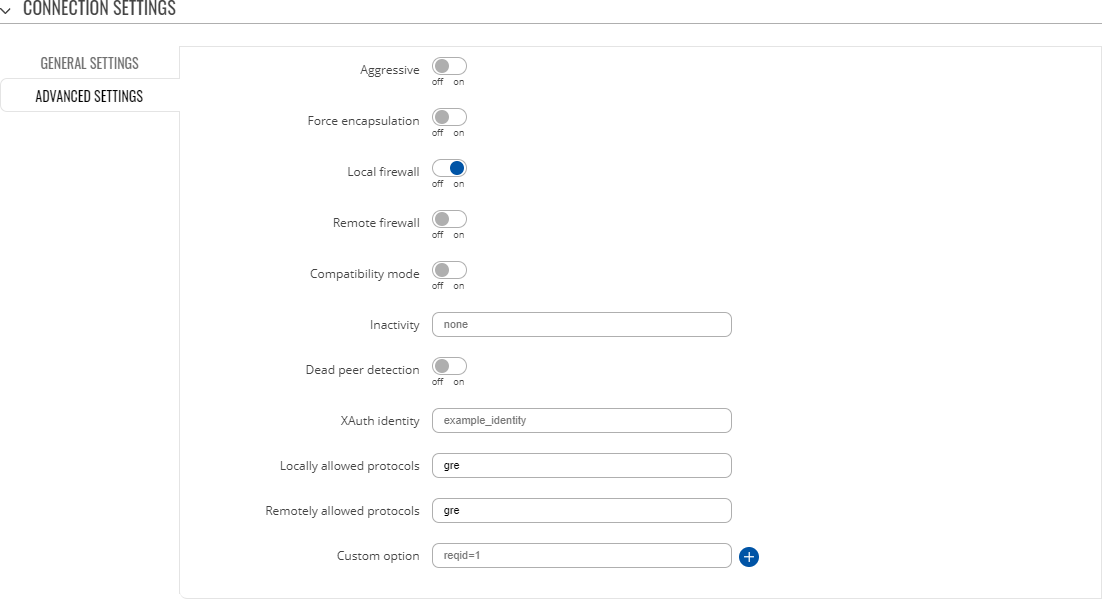
Advanced settings
| Field | Value | Description |
|---|---|---|
| Aggressive | off | on; default: off | Turn aggressive mode on or off for outgoing connections. Aggressive mode performs fewer exchanges (a total of 4 messages) than Main mode (a total of 6 messages) by storing most data into the first exchange. In aggressive mode, the information is exchanged before there is a secure channel, making it less secure but faster than main mode. Aggressive mode is available only with IKEv1; if IKEv2 is selected this field becomes hidden. |
| Force encapsulation | off | on; default: off | Forces UDP encapsulation for ESP packets even if a "no NAT" situation is detected. |
| Local firewall | off | on; default: on | Adds necessary firewall rules to allow traffic of this IPsec instance on this device. |
| Remote firewall | off | on; default: on | Adds necessary firewall rules to allow traffic of from the opposite IPsec instance on this device. |
| Compatibility mode | off | on; default: off | Turns on compatibility mode to help deal with a 3rd party remote peer with multiple subnets. |
| Inactivity | integer; default: none | Defines timeout interval, after which a CHILD_SA is closed if it did not send or receive any traffic. |
| Dead Peer Detection | off | on; default: off | A function used during Internet Key Exchange (IKE) to detect a "dead" peer. It used to reduce traffic by minimizing the number of messages when the opposite peer in unavailable and as failover mechanism. |
| Dead Peer Detection: DPD action | Restart | Hold | Clear | None; default: Restart | Controls the use of the Dead Peer Detection protocol where notification messages are periodically sent in order to check the liveliness of the IPsec peer. |
| Dead Peer Detection: DPD Delay | integer; default: none | The frequency of sending R_U_THERE messages or INFORMATIONAL exchanges to peer. |
| Dead Peer Detection: DPD Timeout | integer; default: none | Defines the timeout interval, after which all connections to a peer are deleted in case of inactivity. |
| XAuth identity | string; default: none | The identity/username the client uses to reply to an XAuth request. If not defined, the IKEv1 identity will be used as XAuth identity. |
| Tunnel: Remote source IP | ip; default: none | The internal source IP to use in a tunnel for the remote (right) peer. |
| Tunnel: Local source IP | ip; default: none | The internal (left) source IP to use in a tunnel, also known as virtual IP. |
| Tunnel: Remote DNS | ip; default: none | List of DNS server addresses to exchange as configuration attributes. On the responder, only fixed IPv4/IPv6 addresses are allowed and define DNS servers assigned to the client. |
| Locally allowed protocols | string; default: none | Allowed protocols and ports over connection, also called Port Selectors. Defines in form of 'protocol/port' eg:'17/1701' or '17/%any' or 'udp/l2f'. |
| Remotely allowed protocols | string; default: none | Allowed protocols and ports over connection, also called Port Selectors. Defines in form of 'protocol/port' eg:'17/1701' or '17/%any' or 'udp/l2f'. |
| Custom option | string; default: none | Add custom connection parameters. |
| Local source IP | ip; default: none | The internal (left) source IP to use in a tunnel, also known as virtual IP. |
| Tunnel: Passthrough interfaces | network interfaces; default: none | Network interfaces to include in IPsec Passthrough. |
| Tunnel: Passthrough subnets | ip/netmask; default: none | Networks to include in IPsec Passthrough. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Type: Tunnel
- Blue for Dead Peer Detection: Enabled
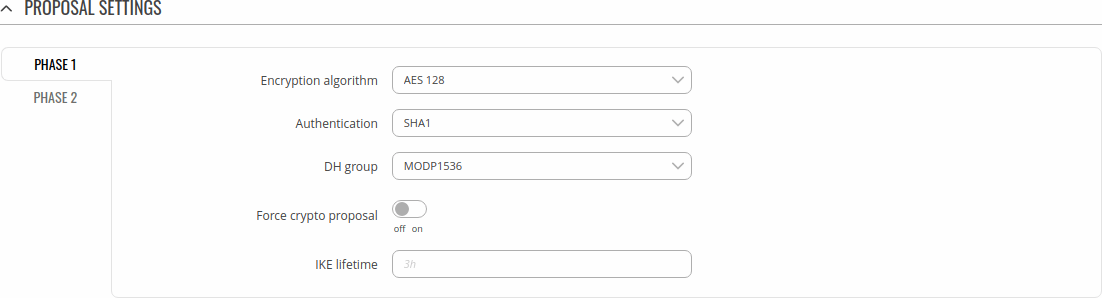
IPsec instance: proposal settings
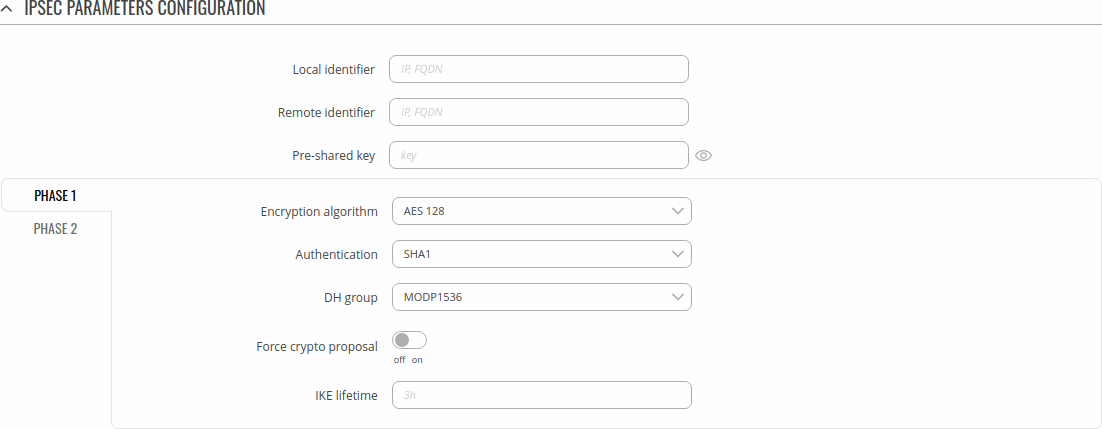
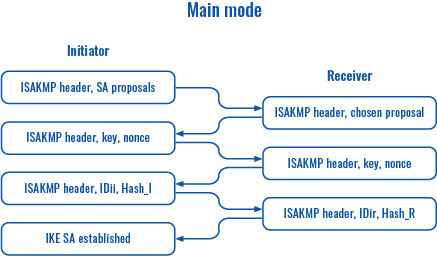
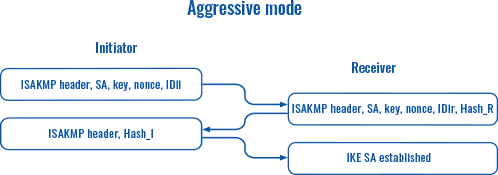
The proposal settings section is used to configure IKE (Internet Key Exchange) phase 1 & 2 settings. IKE is a protocol used to set up security associations (SAs) for the IPsec connection. This process is required before any IPsec tunnel can be established. It is done in two phases:
| Phase | Mode | |
|---|---|---|
Phase 1
|
Main mode (figure 1)
|
Aggressive mode (figure 2)
|
Phase 2
|
Quick mode
|
|
| Figure 1 |
Figure 2 |
 |
 |
Phase 1
| Field | Value | Description |
|---|---|---|
| Encryption algorithm | 3DES | AES 128 | AES 192 | AES 256 | AES128 GCM8 | AES192 GCM8 | AES256 GCM8 | AES128 GCM12 | AES192 GCM12 | AES256 GCM12 | AES128 GCM16 | AES192 GCM16 | AES256 GCM16; default: AES 128 | Algorithm used for data encryption. |
| Authentication | MD5 | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | Algorithm used for exchanging authentication and hash information. |
| DH group | MODP768 | MODP1024 | MODP1536 | MODP2048 | MODP3072 | MODP4096 | ECP192 | ECP224 | ECP256 | ECP384 | ECP521 | No PFS; default: MODP1536 | Diffie-Hellman (DH) group used in the key exchange process. Higher group numbers provide more security, but take longer and use more resources to compute the key. Must match with another incoming connection to establish IPSec. |
| Force crypto proposal | off | on; default: off | Only chosen proposals will be used when turned on. |
| IKE Lifetime | string; default: none | How long the keying channel of a connection (ISAKMP or IKE SA) should last before being renegotiated. The time is specified in seconds. The s, m, h and d suffixes explicitly define the units for seconds, minutes, hours and days, respectively. |
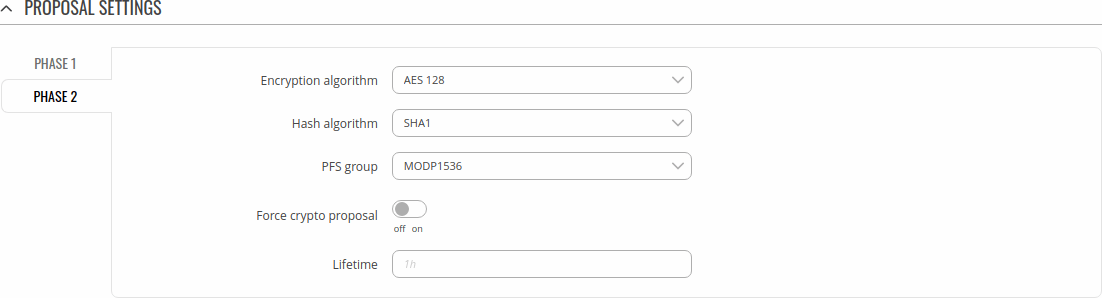
Phase 2
| Field | Value | Description |
|---|---|---|
| Encryption algorithm | 3DES | AES 128 | AES 192 | AES 256 | AES128 GCM8 | AES192 GCM8 | AES256 GCM8 | AES128 GCM12 | AES192 GCM12 | AES256 GCM12 | AES128 GCM16 | AES192 GCM16 | AES256 GCM16; default: 3DES | Algorithm used for data encryption. |
| Hash algorithm | MD5 | SHA1 | SHA256 | SHA384 | SHA512; default: MD5 | Algorithm used for exchanging authentication and hash information. |
| PFS group | MODP768 | MODP1024 | MODP1536 | MODP2048 | MODP3072 | MODP4096 | ECP192 | ECP224 | ECP256 | ECP384 | ECP521 | No PFS; default: MODP768 | The PFS (Perfect Forward Secrecy). Must match with another incoming connection to establish IPSec. |
| Force crypto proposal | off | on; default: off | Only chosen proposals will be used when turned on. |
| Lifetime | string; default: none | How long the keying channel of a connection (ISAKMP or IKE SA) should last before being renegotiated. The time is specified in seconds. The s, m, h and d suffixes explicitly define the units for seconds, minutes, hours and days, respectively. |
PPTP
Point-to-Point Tunneling Protocol (PPTP) is a type of VPN protocol that uses a TCP control channel and a Generic Routing Encapsulation tunnel to encapsulate PPP packets.
PPTP client
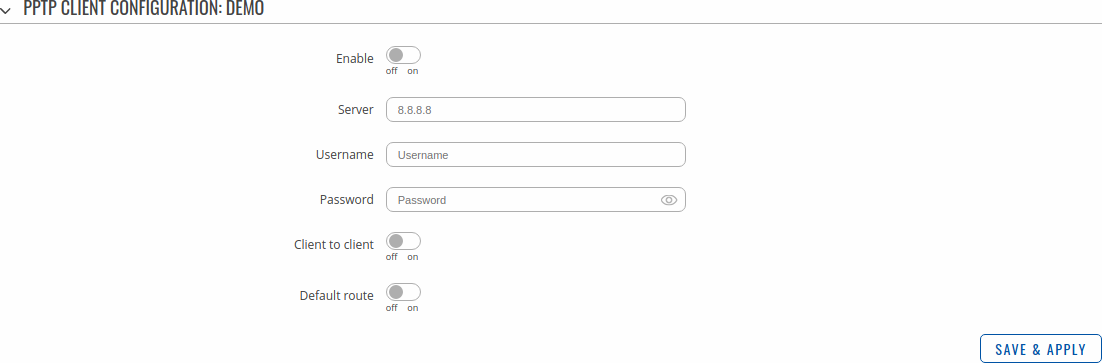
A PPTP client is an entity that initiates a connection to a PPTP server. To create a new client instance, go to the Services → VPN → PPTP section, select Role: Client, enter a custom name and click the 'Add' button:
You should be redirected to the configuration page for the newly added PPTP Client which should look similar to this:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the PPTP instance on or off. |
| Server | ip | host; default: none | IP address or hostname of a PPTP server. |
| Username | string; default: none | Username used for authentication to the PPTP server. |
| Password | string; default: none | Password used for authentication to the PPTP server. |
| Client to client | off | on; default: off | Adds route to make other PPTP clients reachable. |
| Default route | off | on; default: off | When turned on, this connection will become the device default route. This means that all traffic directed to the Internet will go through the PPTP server and the server's IP address will be seen as this device's source IP to other hosts on the Internet. |
PPTP server
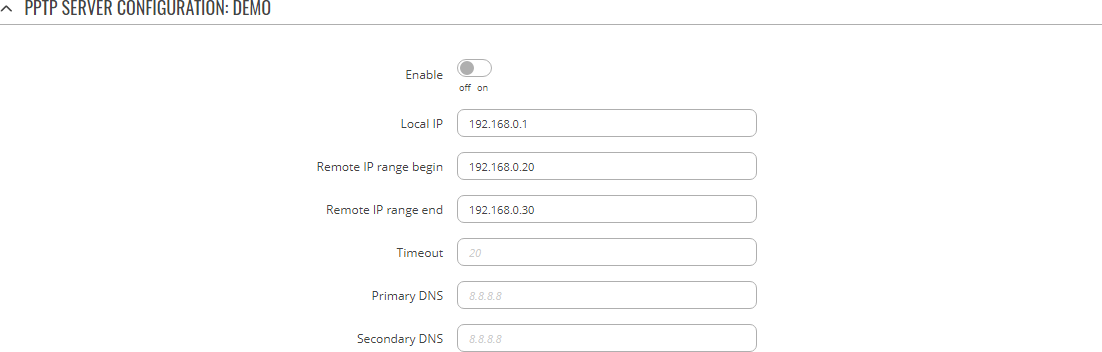
A PPTP server is an entity that waits for incoming connections from PPTP clients. To create a new server instance, go to the Services → VPN → PPTP section, select Role: Server, enter a custom name and click the 'Add' button:
You should be redirected to the configuration page for the newly added PPTP Server which should look similar to this:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the PPTP instance on or off. |
| Local IP | ip; default: 192.168.0.1 | IP address of this PPTP network interface. |
| Remote IP range start | ip; default: 192.168.0.20 | PPTP IP address leases will begin from the address specified in this field. |
| Remote IP range end | ip; default: 192.168.0.30 | PPTP IP address leases will end with the address specified in this field. |
| Timeout | integer; default: none | Time in seconds. If no packets pass through the tunnel between this server and a client, the server will terminate the connection to that client after the amount of time specified in this field passes. |
| Primary DNS | ip; default: none | IP address of the primary DNS server. |
| Secondary DNS | ip; default: none | IP address of the secondary DNS server. |
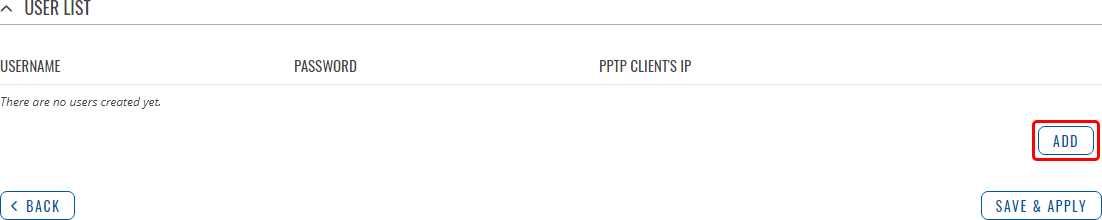
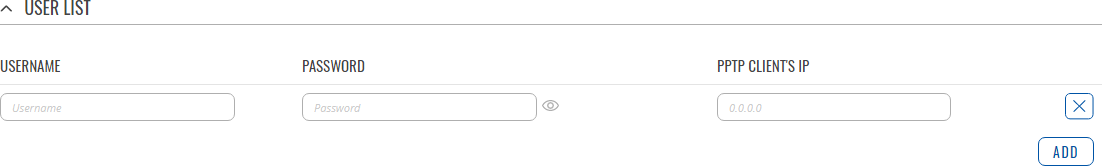
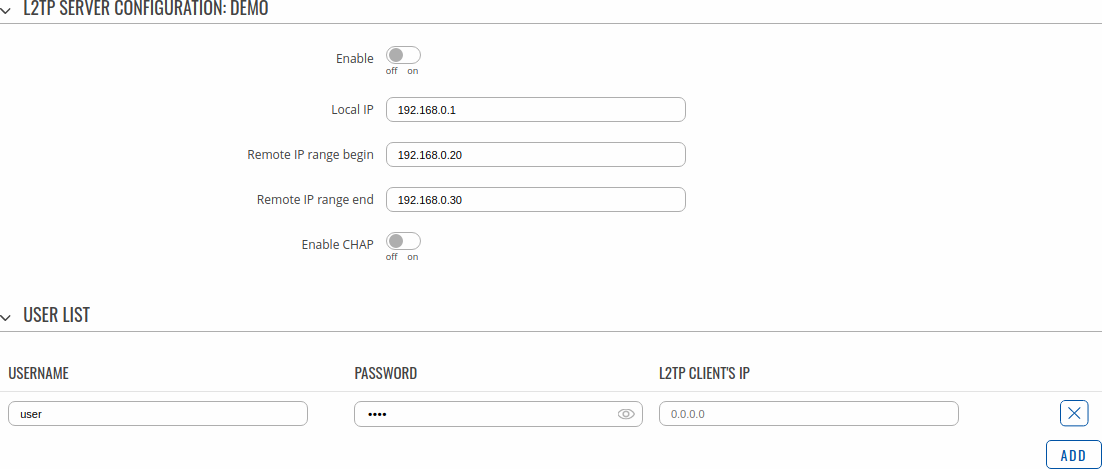
The User List section is used to user authentication settings required to successfully connect to this server. The list is empty by default. Click the 'Add' button to create a new PPTP User:
| Field | Value | Description |
|---|---|---|
| Username | string; default: none | Username used for authentication to this PPTP server. |
| Password | string; default: none | Password used for authentication to this PPTP server. |
| PPTP Client's IP | ip; default: none | Assigns an IP address to the client that uses the adjacent authentication info. This field is optional and if left empty the client will simply receive an IP address from the IP pool defined above. |
Note: there can only one PPTP Server configuration on the device.
SSTP
Secure Socket Tunneling Protocol (SSTP) is a VPN protocol designed to transport PPP traffic via a secure SSL/TLS channel.
Note: SSTP is additional software that can be installed from the Services → [[{{{name}}} Package Manager|Package Manager]] page.
SSTP configuration
To create a new SSTP instance, go to the Services → VPN → SSTP section, enter a custom name and click the 'Add' button. An SSTP instance with the given name will appear in the "SSTP Configuration" list.
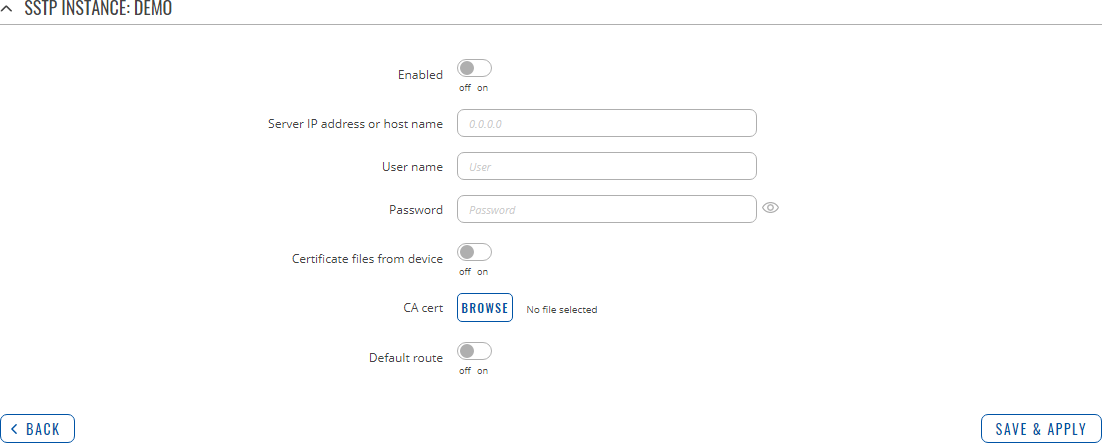
To begin configuration, click the 'Edit' button located next to the instance. Refer to the figure and table below for information on the SSTP instance's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the SSTP instance on or off. |
| Server IP address | ip | host; default: none | IP address or hostname of a SSTP server. |
| User name | string; default: none | Username used for authentication to the SSTP server. |
| Password | string; default: none | Password used for authentication to the SSTP server. |
| Certificate files from device | off | on; default: off | Turn on this option if you want to select generated certificate files from device. |
| CA cert | .crt file; default: none | Upload a Certificate authority (CA) file. |
| Default route | off | on; default: off | When turned on, this connection will become the device default route. This means that all traffic directed to the Internet will go through the SSTP server and the server's IP address will be seen as this device's source IP to other hosts on the Internet. NOTE: this can only be used when [[{{{name}}} Failover|Failover]] is turned off. |
Stunnel
Stunnel is an open-source a proxy service that adds TLS encryption to clients and servers already existing on a VPN network. TLS encryption provided by Stunnel can be used as an additional layer of encryption for data sent by VPN. This procedure increases the security of the established connection and provides higher chances of passing a Deep packet inspection (DPI) check.
Stunnel globals
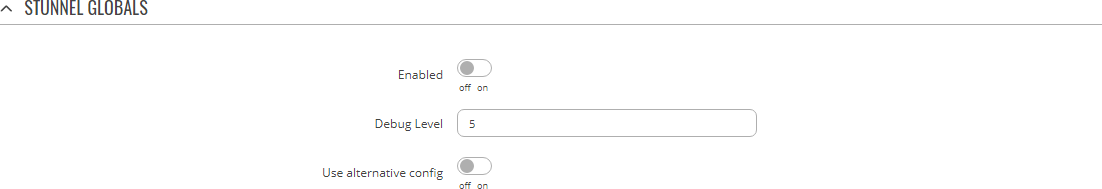
The Stunnel Globals section is used to manage the Stunnel service as a whole.
Refer to the figure and table below for information on the fields contained in the Stunnel Globals section.
Note: Stunnel is additional software that can be installed from the Services → [[{{{name}}} Package Manager|Package Manager]] page.
| Field | Value | Description |
|---|---|---|
| Enabled | off | on; default: off | Turns the Stunnel service on or off. If this is unchecked, Stunnel instances will not start (even if they are enabled individually); therefore, it is necessary to check this field in order to make Stunnel active on the router. |
| Debug Level | integer [0..7]; default: 5 | Debugging to log output level.
|
| Use alternative config | off | on; default: off | Turns the possibility to upload an external Stunnel configuration file on or off.if you turn this on, other Stunnel configurations present in the router will become inactive. |
| Upload alternative config | file; default: none | Uploads an Stunnel configuration file. |
Stunnel instance
To create a new Stunnel instance, go to the Services → VPN → Stunnel section, enter a custom name and click the 'Add' button. An Stunnel instance with the given name will appear in the "Stunnel Configuration" list.
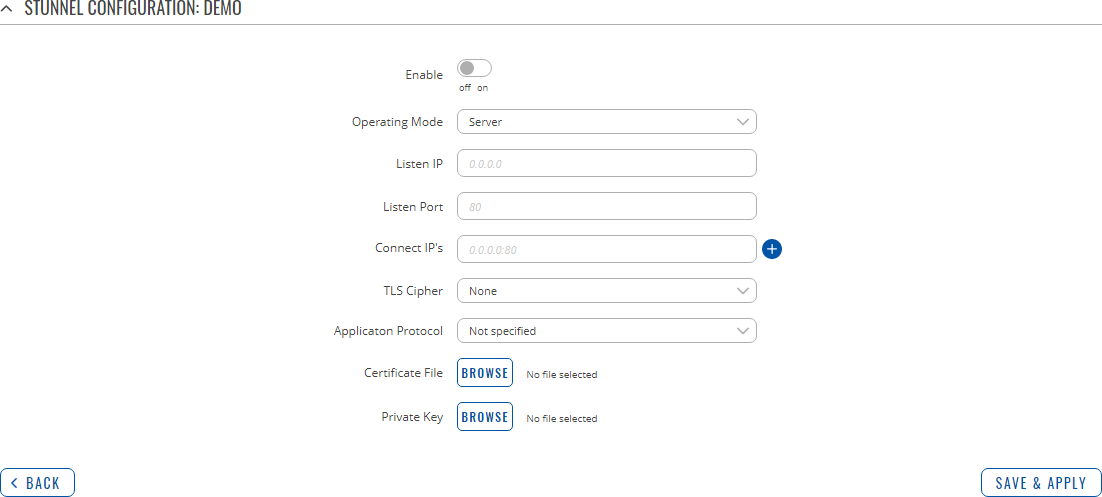
To begin configuration, click the 'Edit' button located next to the instance. Refer to the figure and table below for information on the Stunnel instance's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the Stunnel instance on or off. |
| Operating Mode | Server | Client; default: Server | Selects the Stunnel instance's role.
|
| Listen IP | ip; default: none | Makes the instance "listen" for incoming connections on the specified IP address. When left empty, the value of this field defaults to localhost (127.0.0.1). |
| Listen Port | integer [0..65535]; default: none | Makes the instance "listen" for incoming connections on the specified TCP port. Make sure you chose a port that is not being used by another service. You will also have to allow traffic on the specified port. |
| Connect IP's | ip:port; default: none | IP:Port to listen for VPN connections. When left empty the value of this field is interpreted as localhost. Must contain at least one item. If multiple options are specified, remote address is chosen using a round-robin algorithm. |
| TLS Cipher | None | Secure | Custom; default: None | Packet encryption algorithm cipher. |
| Custom: Allowed TLS Ciphers | string; default: none | A list of TLS ciphers accepted for this connection. |
| Application Protocol | Connect | SMTP | Not specified; default: Not specified | This option enables initial, protocol-specific negotiation of the TLS encryption. The protocol option should not be used with TLS encryption on a separate port. |
| Connect: Protocol Authentication | Basic | NTLM; default: Basic | Authentication type for the protocol negotiations. |
| SMTP: Protocol Authentication | Plain | Login; default: Plain | Authentication type for the protocol negotiations. |
| Certificate File | .crt file; default: none | TLS client or server certificate file. |
| Private Key | .key file; default: none | TLS client or server key file. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Blue for TLS Cipher: Custom
- Dark red for Application Protocol: Connect
- Chocolate for Application Protocol: SMTP
DMVPN
Dynamic Multipoint VPN (DMVPN) is a method of building scalable IPsec VPNs. DMVPN is configured as a hub-and-spoke network, where tunnels between spokes are built dynamically; therefore, no change in configuration is required on the hub in order to connect new spokes.
Note: DMPVN is additional software that can be installed from the Services → [[{{{name}}} Package Manager|Package Manager]] page.
DMVPN configuration
To create a new DMVPN instance, go to the Services → VPN → DMVPN section, enter a custom name and click the 'Add' button. A DMVPN instance with the given name will appear in the "DMVPN Configuration" list.
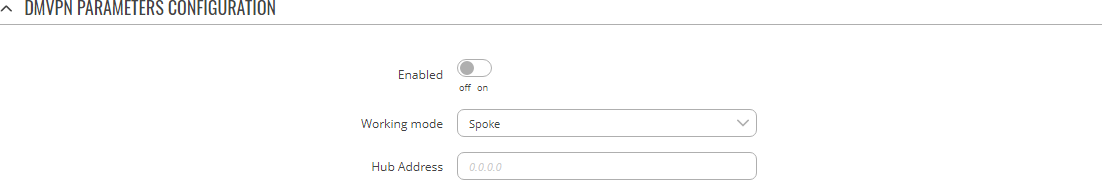
To begin configuration, click the button that looks like a pencil located next to the instance. Refer to the figures and tables below for information on the DMVPN instance configuration:
| Field | Value | Description |
|---|---|---|
| Enabled | off | on; default: off | Turns the DMVPN instance on or off. |
| Working mode | Spoke | Hub; default: Spoke | Selects the role of this instance
|
| Hub address | ip | host; default: none | IP address or hostname of a DMVPN hub. |
| Field | Value | Description |
|---|---|---|
| Tunnel source | network interface; default: LAN | Network interface used to establish the GRE Tunnel. |
| Local GRE interface IP address | ip; default: none | IP address of the local GRE Tunnel instance. |
| Spoke: Remote GRE interface IP address | ip; default: none | IP address of the remote GRE Tunnel instance. |
| Hub: Local GRE interface netmask | netmask; default: none | Subnet mask of the local GRE Tunnel instance. |
| GRE MTU | integer; default: none | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| GRE keys | integer [0..65535]; default: none | A key used to identify incoming and outgoing GRE packets. |
| Field | Value | Description |
|---|---|---|
| Local identifier | ip | string; default: none | Defines how the user (IPsec instance) will be identified during authentication.
|
| Remote identifier | ip | string; default: none | Defines how the right participant will be identified during authentication.
|
| Pre-shared key | string; default: none | A shared password used for authentication between IPsec peers. |
| Encryption algorithm | 3DES | AES 128 | AES 192 | AES 256 | AES128 GCM8 | AES192 GCM8 | AES256 GCM8 | AES128 GCM12 | AES192 GCM12 | AES256 GCM12 | AES128 GCM16 | AES192 GCM16 | AES256 GCM16; default: AES 128 | Algorithm used for data encryption. |
| Authentication/Hash algorithm | MD5 | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | Algorithm used for exchanging authentication and hash information. |
| DH/PFS group | MODP768 | MODP1024 | MODP1536 | MODP2048 | MODP3072 | MODP4096 | ECP192 | ECP224 | ECP256 | ECP384 | ECP521; default: MODP1024 | Diffie-Hellman (DH) group used in the key exchange process. Higher group numbers provide more security, but take longer and use more resources to compute the key. Must match with another incoming connection to establish IPSec. |
| Force crypto proposal | off | on; default: off | Only chosen proposals will be used when turned on. |
| IKE Lifetime | string; default: none | How long the keying channel of a connection (ISAKMP or IKE SA) should last before being renegotiated. The time is specified in seconds. The s, m, h and d suffixes explicitly define the units for seconds, minutes, hours and days, respectively. |
| Field | Value | Description |
|---|---|---|
| NHRP network ID | integer; default: none | An identifier used to define the NHRP domain. This is a local parameter and its value does not need to match the values specified on other domains. However, the NHRP ID is added to packets which arrive on the GRE interface; therefore, it may be helpful to use the same ID for troubleshooting purposes. |
| NHRP authentication key | string; default: none | A key used in NHRP authentication. |
| NHRP hold time | integer; default: none | Specifies the holding time for NHRP Registration Requests and Resolution Replies sent from this interface or shortcut-target. The hold time is specified in seconds and defaults to two hours. |
L2TP
In computer networking, Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs). It is more secure than PPTP but, because it encapsulates the transferred data twice, but it is slower and uses more CPU power.
L2TP Global Settings
| Field | Value | Description |
|---|---|---|
| Require CHAP | off | on; default: on | When enabled, peer will be required to authenticate itself using standard CHAP authentication. |
| Refuse PAP | off | on; default: on | When enabled, pppd will not agree to authenticate itself to the peer using Password Authentication Protocol (PAP). |
L2TP Client
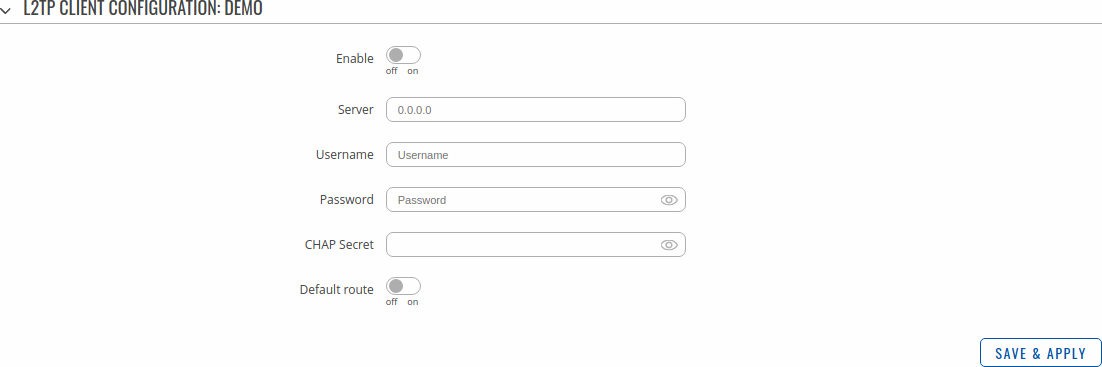
An L2TP client is an entity that initiates a connection to an L2TP server. To create a new client instance, go to the Services → VPN → L2TP section, select Role: Client, enter a custom name and click the 'Add' button. An L2TP client instance with the given name will appear in the "L2TP Configuration" list.
To begin configuration, click the button that looks like a pencil next to the client instance. Refer to the figure and table below for information on the L2TP client's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the L2TP instance on or off. |
| Server | ip | host; default: none | IP address or hostname of an L2TP server. |
| Username | string; default: none | Username used for authentication to the L2TP server. |
| Password | string; default: none | Password used for authentication to the L2TP server. |
| CHAP Secret | string; default: none | A secret used for L2TP Tunnel Authentication. |
| Default route | off | on; default: off | When turned on, this connection will become device default route. This means that all traffic directed to the Internet will go through the L2TP server and the server's IP address will be seen as this device's source IP to other hosts on the Internet. |
L2TP Server
An L2TP server is an entity that waits for incoming connections from L2TP clients. To create a new server instance, go to the Services → VPN → L2TP section, select Role: Server, enter a custom name and click the 'Add' button. An L2TP server instance with the given name will appear in the "L2TP Configuration" list. Only one L2TP server instance is allowed to be added.
A server needs to have a public IP address in order to be available from the public network (the Internet).
To begin configuration, click the button that looks like a pencil next to the server instance. Refer to the figure and table below for information on the L2TP server's configuration fields:
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns the L2TP instance on or off. |
| Local IP | ip; default: 192.168.0.1 | IP address of this L2TP network interface. |
| Remote IP range begin | ip; default: 192.168.0.20 | L2TP IP address leases will begin from the address specified in this field. |
| Remote IP range end | ip; default: 192.168.0.30 | L2TP IP address leases will end with the address specified in this field. |
| Enable CHAP | off | on; default: user | Enables Challenge-Handshake Authentication Protocol for L2TP |
| CHAP Secret | string; default: user | A secret used for L2TP Tunnel Authentication. |
| User name | string; default: user | Username used for authentication to this L2TP server. |
| Password | string; default: pass | Password used for authentication to this L2TP server. |
| L2TP Client's IP | ip; default: none | Assigns an IP address to the client that uses the adjacent authentication info. This field is optional and if left empty the client will simply receive an IP address from the IP pool defined above. |
L2TPv3
L2TPv3 (Layer Two Tunneling Protocol Version 3) is a point-to-point layer two over IP tunnel. This means you can tunnel L2 protocols like Ethernet, Frame-relay, ATM, HDLC, PPP, etc. over an IP network.
Local settings
| Field | Value | Description | |
|---|---|---|---|
| Enable | off | on; default: off | Turns the L2TPv3 instance on or off. | |
| Local address | ip; default: none | IP address of device's WAN. Note: If left empty, it will take IP address automatically from main WAN interface. | |
| Tunnel ID | integer [1..4294967295]; default: none | Uniquely identifies the tunnel. The value used must match the peer tunnel ID value being used at the peer. | |
| Session ID | integer [1..4294967295]; default: none | The value used must match the tunnel ID value being used at the peer. | |
| Cookie | string; default: none | Must be specified in hexidecimal form and be length of 8 or 16. eg.: 89ABCDEF. |
Peer settings
| Field | Value | Description | |
|---|---|---|---|
| Peer address | ip; default: none | Peer Endpoint IP address. | |
| Peer Tunnel ID | integer [1..4294967295]; default: none | ID of peer's tunnel is specified from 1 to 4294967295. It must match other end tunnel ID. | |
| Peer Session ID | integer [1..4294967295]; default: none | UID of peer's session is specified from 1 to 4294967295. It must match other end session ID. | |
| Peer Cookie | string; default: none | Must be specified in hexidecimal form and be length of 8 or 16. eg.: 89ABCDEF. It must match other end Cookie. |
Instance Settings
| Field | Value | Description | |
|---|---|---|---|
| Bridge to | None | LAN; default: None | Peer Endpoint IP address. | |
| IPv4 Address | ip4; default: none | IPv4 address of standalone L2TPv3 interface. | |
| Netmask | netmask; default: 255.255.255.0 | Netmask of standalone L2TPv3 interface. | |
| IPv6 Address | ip6; default: none | IPv6 address of standalone L2TPv3 interface. CIDR notation: address/prefix. | |
| MTU | integer [64..9000]; default: none | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. | |
| Encapsulation | IP | UDP; default: IP | Specify technology to use when connecting to other end. | |
| UDP source port | port; default: none | Specifies source port. | |
| UDP destination port | port; default: none | Specifies destination port. | |
| Layer 2 specific header type | None | Linux Default; default: Linux Default | It might be neccessary to set this option to none when using other hardware. |
ZeroTier
ZeroTier One is an open source software which can establish Peer to Peer VPN (P2PVPN) connection between various devices running various operating systems. It also provides network management possibilities such as routing and creating firewall rules.
Note: ZeroTier is additional software that can be installed from the Services → [[{{{name}}} Package Manager|Package Manager]] page.
In order to create a new ZeroTier Instance, look to the Add New ZeroTier Configuration section; enter a custom name and click the 'Add' button:
You should be redirected to the configuration page for the newly added ZeroTier Instance which should look similar to this:
| Field | Value | Description |
|---|---|---|
| Enabled | off | on; default: off | Turns the ZeroTier Instance on or off. |
| Networks | hex string; default: none | ZeroTier Network ID. Log in to your ZeroTier account in order to locate the ZeroTier Network ID, which should be a string of hexadecimal characters. |
| Port | integer [0..65535]; default: none | ZeroTier Network port. |
WireGuard
WireGuard is simple, fast, lean, and modern VPN that utilizes secure and trusted cryptography. It intends to be more performant than OpenVPN. WireGuard is designed as general purpose VPN, fit for many different circumstances and while it is currently under heavy development, it already might be regarded as the most secure, easiest to use, and simplest VPN solution.
WireGuard works by adding an interface which acts as a tunnel. To create one enter its name and click the Add button. This should add a new Wireguard instance and open a configuration window.
General Instance Settings
This section contains General settings of created WireGuard Instance. Here you can find its Public and Private keys and generate them, specify Port and IP addresses for communication.
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns WireGuard Instance on or off. |
| Private Key | Base64-encoded string; default: generated | Private Key used in authentication. Required. |
| Public Key | Base64-encoded string; default: generated | Public Key used in authentication. |
| Generate | -(interactive button) | Click to generate Public Key and Private Key. |
| Listen Port | integer [0..65535]; default: 51820 | Specify port to listen for incomming connections. It will be set to a random integer if left empty. |
| IP Addresses | ip; default: none | A single IP address or a list of them for this instance associated with public keys. |
Advanced Settings
Advanced Settings section contains Metric and MTU configuration for this WireGuard interface.

| Field | Value | Description |
|---|---|---|
| Metric | positive integer; default: none | Specify metric for this tunnel interface. Lower number means higher priority. |
| MTU | integer [1280..1420]; default: none | Maximum Transmission Unit for this tunnel interface. |
Peers
The Peers section is used to create and configure all the peers for this interface.
To create one enter its name and click the Add button.
To configure it click the Edit ![]() button.
button.
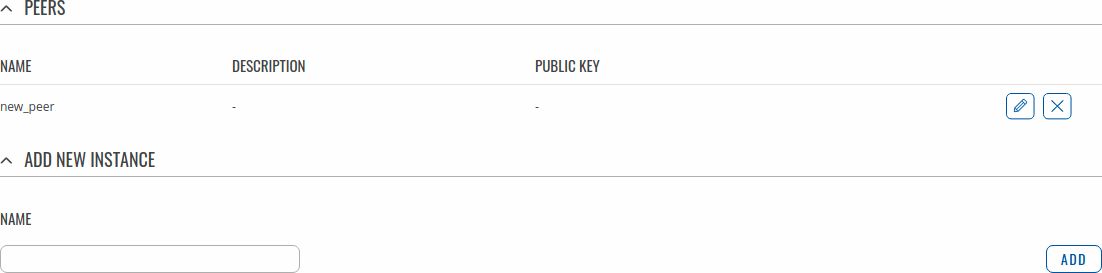
General Peer Settings
In the General section of Peer instance you can configure basic information about the endpoint to allow communications.

| Field | Value | Description |
|---|---|---|
| Public Key | string; default: none | Endpoint's Public Key. |
| Allowed IPs | ip; default: none | A single IP address or a list of them which are allowed to communicate with this peer. |
Advanced Peer Settings
In the Advanced section of Peer instance you are able to configure additional
settings such as its Description, Endpoint Host and Port, Preshared Key and other.
See more information below.
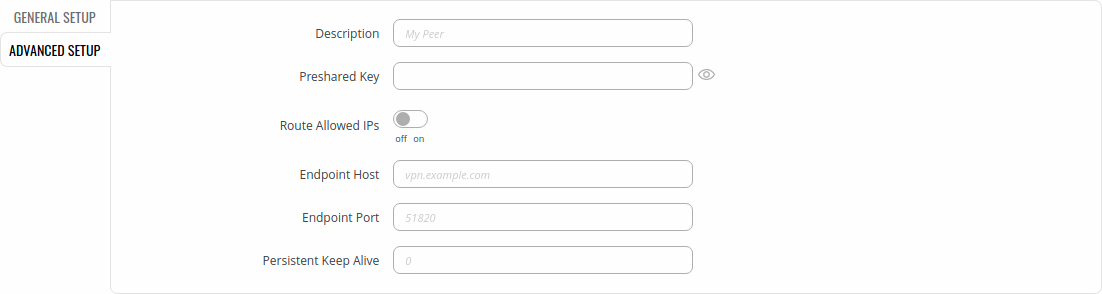
| Field | Value | Description |
|---|---|---|
| Description | string; default: none | Description of this peer. |
| Pre-Shared Key | string; default: none | Base64-encoded preshared key. Adds in an additional layer of symmetric-key cryptography for post-quantum resistance. |
| Route Allowed IPs | off | on; default: off | Enable to create routes for Allowed IPs for this peer. |
| Endpoint Host | ip | url; default: none | IP or URL of Remote Endpoint. |
| Endpoint Port | integer [0..65535]; default: none | Specify port to connect to Remote Endpoint. It will be set to 51820 if left empty. |
| Persistent Keep Alive | integer [0..65535]; default: none | Specify time amount in seconds between Keep Alive messages. By default this option is 0 which means it is disabled. Recommended value for a device behind NAT is 25. |
[[Category:{{{name}}} Services section]]