OpenVPN Access Control: Difference between revisions
(Start) |
m (Edit 1) |
||
| Line 1: | Line 1: | ||
<h1>Introduction</h1> | <h1>Introduction</h1> | ||
| Line 11: | Line 12: | ||
3) In Certificate Manager download Server certificate | 3) In Certificate Manager download Server certificate | ||
[[File:Certificate download.png|thumb]] | |||
For any OpenVPN clients, You will need to generate “Client” certificates, download certificate and key, and send them to the client | |||
<h1>Creating an OpenVPN server</h1> | |||
1) Connect to WebUI and enable Advanced mode | |||
[[File:Advanced mode toggle.png|thumb|Advanced mode toggle]] | |||
2) Navigate to Services -> VPN -> OpenVPN | |||
3) Add a new OpenVPN instance with a Server role | |||
4) Create an OpenVPN server with these settings | |||
[[File:OpenVPN server settings.png|thumb|OpenVPN server settings]] | |||
Virtual network IP address – 10.0.0.0 | |||
Virtual network netmask – 255.255.255.240 | |||
Client to client – disabled | |||
Revision as of 08:18, 26 March 2024
Introduction
In this example, we will configure an OpenVPN server and will manage which resources can be accessed by separate clients
Generating certificates for an OpenVPN server
1)Navigate to System -> Administration -> Certificates 2)Generate 2 certificates with a keysize 1024: 2.1) CA 2.2) Server 3) In Certificate Manager download Server certificate
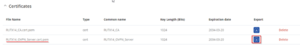
For any OpenVPN clients, You will need to generate “Client” certificates, download certificate and key, and send them to the client
Creating an OpenVPN server
1) Connect to WebUI and enable Advanced mode

2) Navigate to Services -> VPN -> OpenVPN 3) Add a new OpenVPN instance with a Server role 4) Create an OpenVPN server with these settings
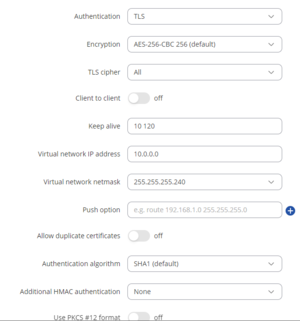
Virtual network IP address – 10.0.0.0 Virtual network netmask – 255.255.255.240 Client to client – disabled
