Openvpn naujas: Difference between revisions
| Line 1: | Line 1: | ||
== | ===Configuration=== | ||
---- | |||
When you have a Static key, you can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and Static key for Authentication. We will be using two RUT routers: '''RUT1''' ('''Server'''; LAN IP: '''192.168.1.1'''; WAN (Public static) IP: '''213.***.***.***''') and '''RUT2''' ('''Client'''; LAN IP: '''192.168.2.1'''); the two routers will be connected via OpenVPN; the Server's Virtual IP address will be '''172.16.0.1'''; the Client's - '''172.16.0.2''': | |||
====Server configuration==== | |||
---- | |||
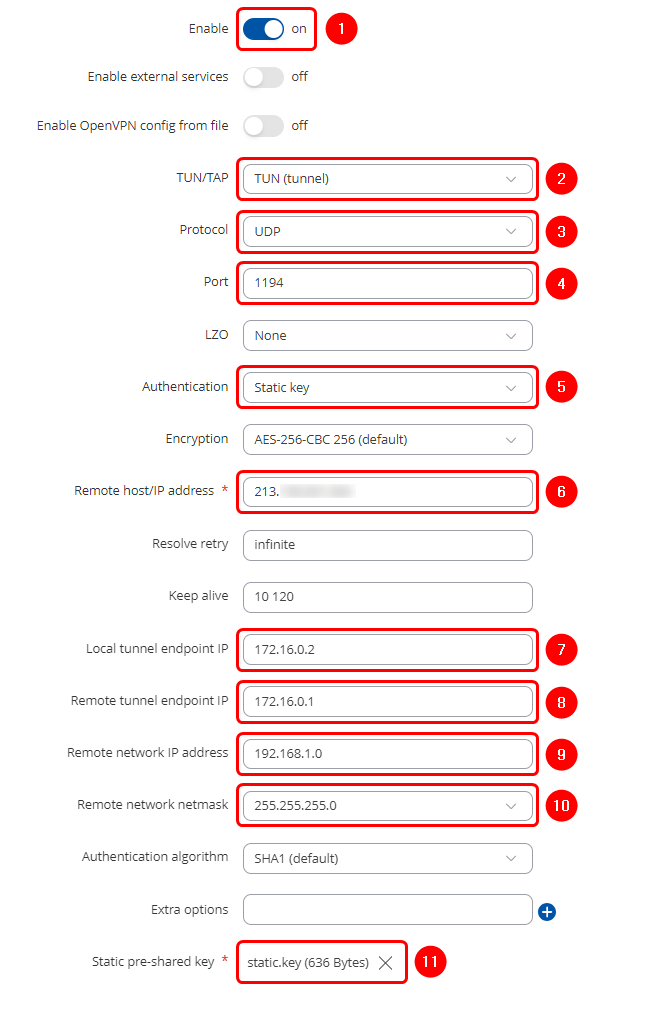
Start by configuring OpenVPN Server on '''RUT1''' device. Login to the WebUI, navigate to '''Services → VPN → OpenVPN''' enter any name and select role as '''Server'''. After pressing the '''Add button''', make the following changes: | |||
'''Note:''' ''Not specified fields can be left as is or changed according to your needs.'' | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=440; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:VPN server static key rev1.png|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
# '''Enable''' the instance | |||
# Select '''Tunnel''' mode | |||
# Select '''UDP''' protocol | |||
# Select '''Port''' | |||
# Select '''Static key''' | |||
# Set '''Local''' tunnel endpoint IP (virtual IP of '''RUT1''') | |||
# Set '''Remote''' tunnel endpoint IP (virtual IP of '''RUT2''') | |||
# Set '''Remote''' network IP address (LAN network of '''RUT2''') | |||
# Set remote network '''Netmask''' | |||
# Select '''Static key''' | |||
#[[File:Networking_save_apply_button_fw76_v1.png|70px]] | |||
</td> | |||
</tr> | |||
</table> | |||
====Client configuration==== | |||
---- | |||
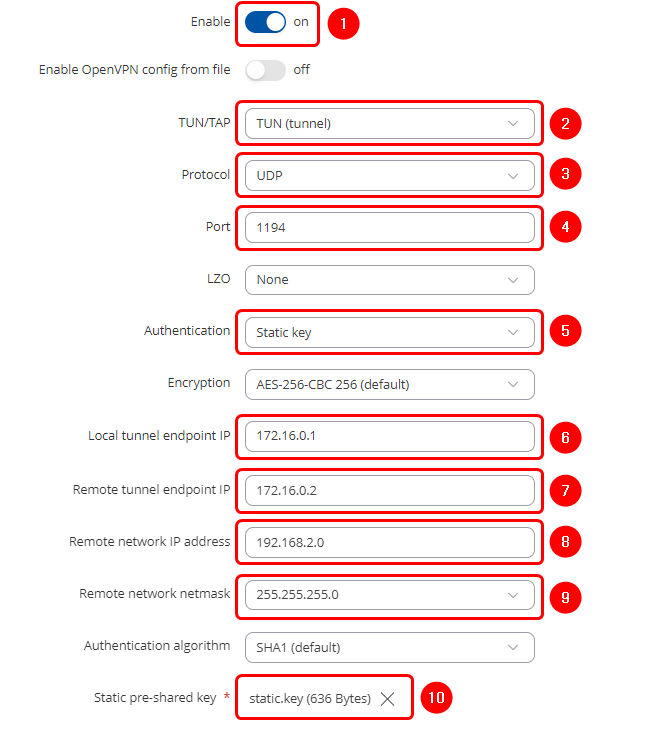
Next, configure OpenVPN Client on '''RUT2''' device. Login to the WebUI, navigate to '''Services → VPN → OpenVPN''', enter any name and select role as '''Client'''. After pressing the '''Add button''', make the following changes: | |||
'''Note:''' ''Not specified fields can be left as is or changed according to your needs.'' | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=440; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:VPN client static key rev1.png|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
# '''Enable''' the instance | |||
# Select '''Tunnel''' mode | |||
# Select '''UDP''' protocol | |||
# Select '''Port''' | |||
# Select '''Static key''' | |||
# Enter '''Public IP address''' of server (WAN IP of '''RUT1''') | |||
# Set '''Local tunnel endpoint IP''' (virtual IP of '''RUT2''') | |||
# Set '''Remote tunnel endpoint IP''' (virtual IP of '''RUT1''') | |||
# Set '''Remote network IP address''' (LAN network of '''RUT1''') | |||
# Set remote network '''Netmask''' | |||
# Select '''Static key''' | |||
#[[File:Networking_save_apply_button_fw76_v1.png|70px]] | |||
</td> | |||
</tr> | |||
</table> | |||
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). Other important aspects are the '''Local tunnel endpoint IP''' and the '''Remote tunnel endpoint IP'''. Take note these two particular parameter values are reversed for the individual Client and the Server configurations since these values represent opposite things depending on the instance's perspective. | |||
From the Client side, make sure to enter the correct '''Remote host/IP address''' (213.***.***.*** in this case). This is the Server's Public IP address, not the virtual IP address. | |||
==TUN (tunnel) OpenVPN== | ==TUN (tunnel) OpenVPN== | ||
Latest revision as of 07:05, 25 August 2025
Configuration
When you have a Static key, you can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and Static key for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 213.***.***.***) and RUT2 (Client; LAN IP: 192.168.2.1); the two routers will be connected via OpenVPN; the Server's Virtual IP address will be 172.16.0.1; the Client's - 172.16.0.2:
Server configuration
Start by configuring OpenVPN Server on RUT1 device. Login to the WebUI, navigate to Services → VPN → OpenVPN enter any name and select role as Server. After pressing the Add button, make the following changes:
Note: Not specified fields can be left as is or changed according to your needs.
 |
|
|---|---|
Client configuration
Next, configure OpenVPN Client on RUT2 device. Login to the WebUI, navigate to Services → VPN → OpenVPN, enter any name and select role as Client. After pressing the Add button, make the following changes:
Note: Not specified fields can be left as is or changed according to your needs.
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). Other important aspects are the Local tunnel endpoint IP and the Remote tunnel endpoint IP. Take note these two particular parameter values are reversed for the individual Client and the Server configurations since these values represent opposite things depending on the instance's perspective.
From the Client side, make sure to enter the correct Remote host/IP address (213.***.***.*** in this case). This is the Server's Public IP address, not the virtual IP address.
TUN (tunnel) OpenVPN
TAP (bridged) OpenVPN
TLS Authentication
This section provides a guide on how to configure a successful OpenVPN connection between an OpenVPN Client and Server, using the TLS Authentication method on RUTxxx routers.
Generating TLS certificates/keys
A connection that uses TLS requires multiple certificates and keys for authentication:
- OpenVPN server
- The root certificate file (Certificate Authority)
- Server certificate
- Server key
- Diffie Hellman Parameters
- OpenVPN client
- The root certificate file (Certificate Authority)
- Client certificate
- Client key
Before you continue you'll have to obtain the necessary certificates and keys. When you use a third-party OpenVPN service, they should provide you with their certificates and even configuration files.
If you're creating your server, you'll have to generate these files yourself. The most simple way to generate certificates is by navigating System → Administration → Certificates on WebUI and pressing the Generate button.
After devices has finished generating all the files, you can download them by navigating to System → Administration → Certificates → Certificates Manager and pressing the Export button next to the required files.
To get detailed instructions on how to generate TLS certificates and keys on RUTOS devices, check out our article on the topic of TLS Certificates.
Configuration
Now we can start configuring OpenVPN Server and Client instances. For this example we will be creating a TUN (Tunnel) type connection that uses the UDP protocol for data transfer and TLS for Authentication. We will be using two RUT routers: RUT1 (Server; LAN IP: 192.168.1.1; WAN (Public static) IP: 213.***.***.***) and RUT2 (Client; LAN IP: 192.168.2.1); that will be connected into virtual network (with the virtual address: 172.16.1.0)
OpenVPN Server configuration
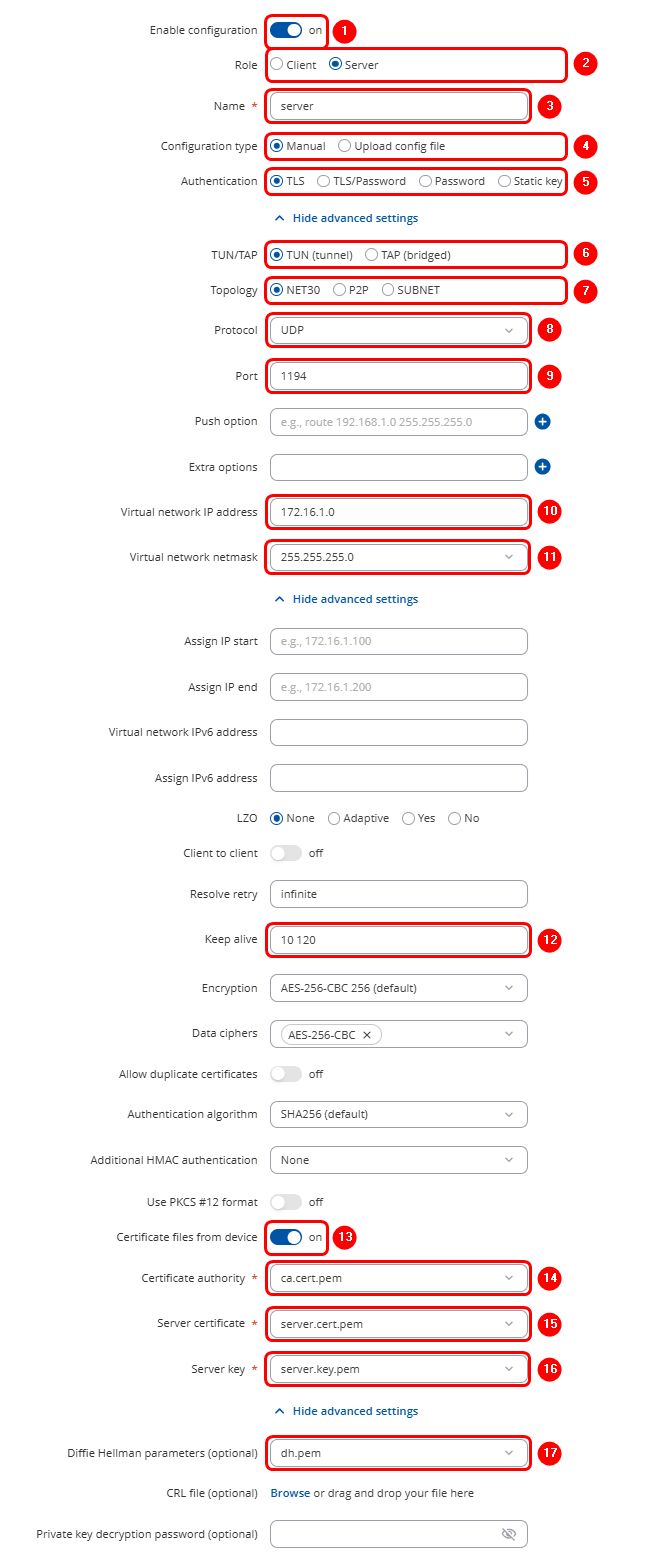
Start by configuring OpenVPN Server on RUT1 device. Login to the WebUI, navigate to Services → VPN → OpenVPN, enter any name and select role as Server. After pressing the Add button, make the following changes:
Note: Not specified fields can be left as is or changed according to your needs.
OpenVPN Client configuration
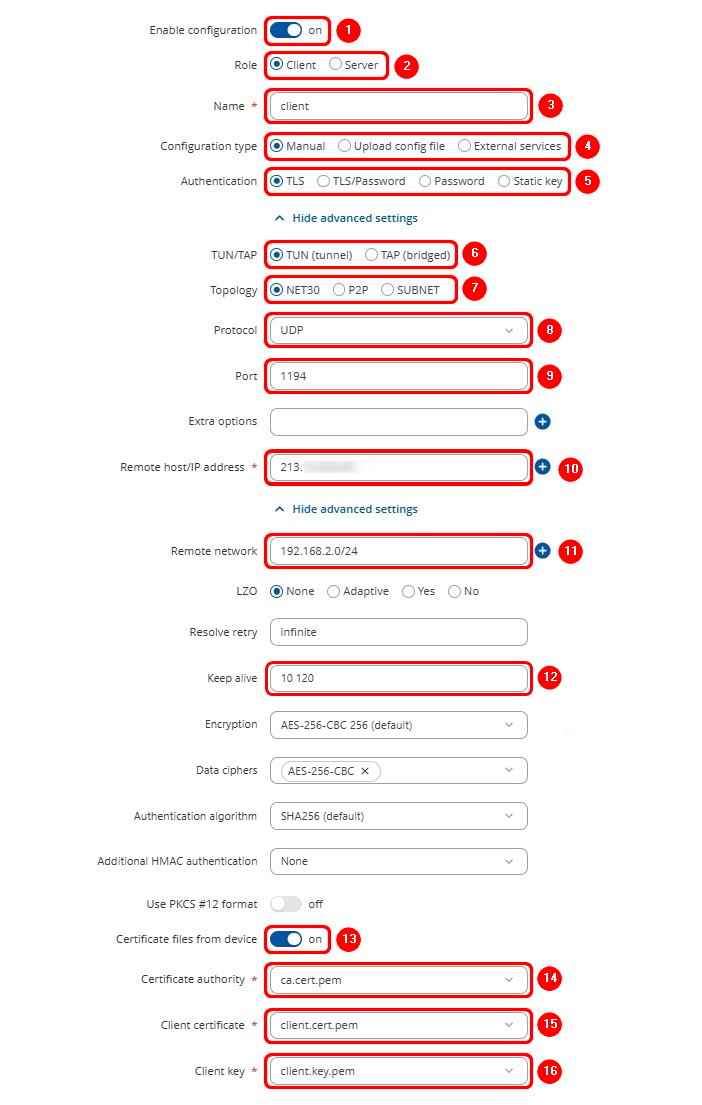
Next, configure OpenVPN Client on RUT2 device. Login to the WebUI, navigate to Services → VPN → OpenVPN, enter any name and select role as Client. After pressing the Add button, make the following changes:
Note: Not specified fields can be left as is or changed according to your needs.
To sum up, just make sure the Server and the Clients use the same parameters (same authentication, same port, same protocol, etc.). Another important aspect is the Virtual network IP address (172.16.1.0 in this case). The Server and the connected Clients will be given IP addresses that belong to this network. If you're creating an exceptionally large network, you might want to change the Virtual network netmask.
From the Client side, make sure to enter the correct Remote host/IP address (213.***.***.*** in this case). This is the Server's Public IP address, not the virtual IP address.