OpenVPN server on Windows: Difference between revisions
No edit summary |
|||
| Line 68: | Line 68: | ||
</li> | </li> | ||
<li>You can also set the size for the Diffie Hellman parameters: | <li>You can also set the key size for the Diffie Hellman parameters: | ||
<ul> | <ul> | ||
<pre>set DH_KEY_SIZE=2048</pre> | <pre>set DH_KEY_SIZE=2048</pre> | ||
Revision as of 11:24, 17 September 2018
Main Page > General Information > Configuration Examples > PC > Windows > OpenVPN server on WindowsIntroduction
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
This article contains step-by-step instructions on how to create and run an OpenVPN server on a PC that runs on Windows OS. The information provided here is geared towards users of almost any knowledge level. The instructions apply to Windows 7 and newer systems.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- A PC or Laptop running on Windows 7 or a later version
- The PC in question must have a Public IP address
- An active Internet connection
Objective:
The purpose of this article is to provide the know-how needed to configure a working OpenVPN server on a Windows PC.
Step 1: installing OpenVPN software
-
The first thing that we'll need to do is to install the necessary software needed in order to run an OpenVPN server. You can download the OpenVPN installer file from here.
Simply run the downloaded file and follow the instructions of the installation guide. -
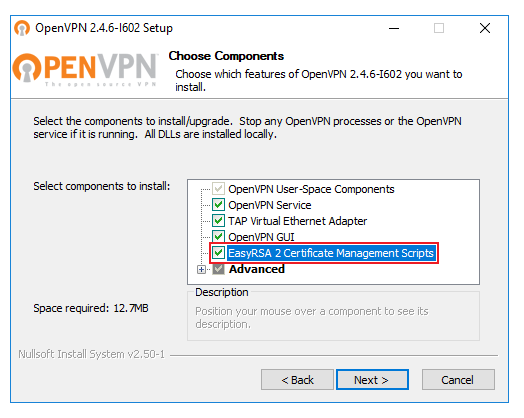
Important note: at one point before the installation begins, you will be prompted to select which components should be included in the installation. Make sure to select EasyRSA as it will be needed later on to generate keys and certificates. You can leave the rest as defaults:
Step 2: generating TLS certificates and keys
- Now we'll need to generate TLS certificates that will later be used for authentication purposes when clients connect to the OpenVPN server. For this we'll be using the EasyRSA application that was installed along with OpenVPN.
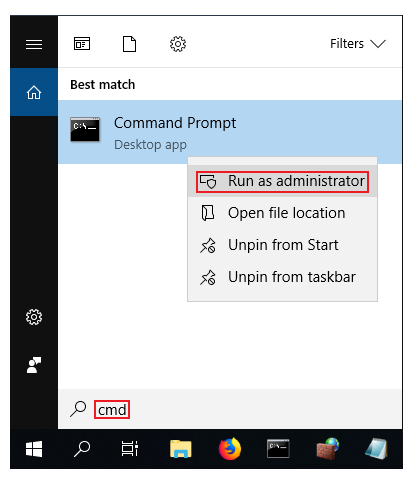
EasyRSA commands have to be executed via the Windows Command Prompt. It can be opened by typing cmd in the Windows search bar (Windows button + S). When you launch it, make sure you run it as administrator:
- Change the current directory to the EasyRSA folder. To do so, execute this command:
cd "C:\Program Files\OpenVPN\easy-rsa"
init-config
notepad vars.bat
set KEY_COUNTRY=US set KEY_PROVINCE=CA set KEY_CITY=SanFrancisco set KEY_ORG=OpenVPN set [email protected]
set DH_KEY_SIZE=2048
vars
clean-all
build-ca
NOTE: you can press the "Enter" key when prompted to enter the values set in the vars.bat file earlier. Doing this will set the values to the default specified in vars.bat. However, you should type in a meaningful Common Name.
build-key-server server
NOTE: once again, don't forget to specify a different Common Name (use the name "server" for easier management purposes). When prompted the sign and commit the certificate, type y and press "Enter".
build-key Client1
TIP: use the same Common Name as the certificate name (Client1 in this example). This will help you differentiate different clients easier. Pick meaningful names like "toms_PC", "company_maintenance", etc. Repeat this step as many times as you need, depending on the client quantity.
build-dh
