RUT240 Routing: Difference between revisions
No edit summary |
|||
| Line 18: | Line 18: | ||
<tr> | <tr> | ||
<td>Routing table</td> | <td>Routing table</td> | ||
<td>Main | <td>Main | WAN | WAN2 | WAN3; Default: '''WAN'''</td> | ||
<td>Defines which table will be used for the route in question</td> | <td>Defines which table will be used for the route in question</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Interface</td> | <td>Interface</td> | ||
<td>LAN | <td>LAN | WAN(wired) | WAN2(Mobile) | WAN3(WiFi) | VPN instances; Default: '''WAN(wired)'''</td> | ||
<td>The zone where the target network resides</td> | <td>The zone where the target network resides</td> | ||
</tr> | </tr> | ||
| Line 110: | Line 110: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles the BGP protocol ON or OFF</td> | <td>Toggles the BGP protocol ON or OFF</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles vty access from LAN ON or OFF</td> | <td>Toggles vty access from LAN ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 138: | Line 138: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles the BGP instance ON or OFF</td> | <td>Toggles the BGP instance ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 171: | Line 171: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles the BGP peer ON or OFF</td> | <td>Toggles the BGP peer ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 199: | Line 199: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles the Access filter ON or OFF</td> | <td>Toggles the Access filter ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 209: | Line 209: | ||
<tr> | <tr> | ||
<td>Action</td> | <td>Action</td> | ||
<td>Permit | <td>Permit | Deny; Default: '''Permit'''</td> | ||
<td>Denies or permits matched entry</td> | <td>Denies or permits matched entry</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Network</td> | <td>Network</td> | ||
<td>Any | <td>Any | ip; Default: '''Any'''</td> | ||
<td>Applies filter rule for this source network</td> | <td>Applies filter rule for this source network</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Direction</td> | <td>Direction</td> | ||
<td>Inbound | <td>Inbound | Outbound; Default: '''Inbound'''</td> | ||
<td>If direction is '''Inbound''', the access list is applied to input routes. If direction is '''Outbound''' the access list is applied to advertised routes</td> | <td>If direction is '''Inbound''', the access list is applied to input routes. If direction is '''Outbound''' the access list is applied to advertised routes</td> | ||
</tr> | </tr> | ||
| Line 241: | Line 241: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles RIP Protocol ON or OFF</td> | <td>Toggles RIP Protocol ON or OFF</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles vty access from LAN ON or OFF</td> | <td>Toggles vty access from LAN ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 256: | Line 256: | ||
<tr> | <tr> | ||
<td>Version</td> | <td>Version</td> | ||
<td>2 | <td>2 | 1; Default: '''2'''</td> | ||
<td>Specifies the version of RIP</td> | <td>Specifies the version of RIP</td> | ||
</tr> | </tr> | ||
| Line 279: | Line 279: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles RIP Interface ON or OFF</td> | <td>Toggles RIP Interface ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 289: | Line 289: | ||
<tr> | <tr> | ||
<td>Passive interface</td> | <td>Passive interface</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and ripd does not send either multicast or unicast RIP packets</td> | <td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and ripd does not send either multicast or unicast RIP packets</td> | ||
</tr> | </tr> | ||
| Line 307: | Line 307: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles the Access filter ON or OFF</td> | <td>Toggles the Access filter ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 317: | Line 317: | ||
<tr> | <tr> | ||
<td>Action</td> | <td>Action</td> | ||
<td>Permit | <td>Permit | Deny; Default: '''Permit'''</td> | ||
<td>Denies or permits matched entry</td> | <td>Denies or permits matched entry</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Network</td> | <td>Network</td> | ||
<td>Any | <td>Any | ip; Default: '''Any'''</td> | ||
<td>Applies filter rule for this source network</td> | <td>Applies filter rule for this source network</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Direction</td> | <td>Direction</td> | ||
<td>Inbound | <td>Inbound | Outbound; Default: '''Inbound'''</td> | ||
<td>If direction is '''Inbound''', the access list is applied to input routes. If direction is '''Outbound''' the access list is applied to advertised routes</td> | <td>If direction is '''Inbound''', the access list is applied to input routes. If direction is '''Outbound''' the access list is applied to advertised routes</td> | ||
</tr> | </tr> | ||
| Line 348: | Line 348: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles OSPF Protocol ON or OFF</td> | <td>Toggles OSPF Protocol ON or OFF</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Enable vty</td> | <td>Enable vty</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles vty access from LAN ON or OFF</td> | <td>Toggles vty access from LAN ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 380: | Line 380: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles OSPF interface ON or OFF</td> | <td>Toggles OSPF interface ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 410: | Line 410: | ||
<tr> | <tr> | ||
<td>Type</td> | <td>Type</td> | ||
<td>Broadcast | <td>Broadcast | Nonbroadcast | Point-to-point | Point-to-multipoint; Default: " "</td> | ||
<td>Set explicit network type for the specified interface</td> | <td>Set explicit network type for the specified interface</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Authentication</td> | <td>Authentication</td> | ||
<td>None | <td>None | Password | MD5 HMAC; Default: " "</td> | ||
<td>Specifies the authentication mode that should be used for the interface</td> | <td>Specifies the authentication mode that should be used for the interface</td> | ||
</tr> | </tr> | ||
| Line 433: | Line 433: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles OSPF area ON or OFF</td> | <td>Toggles OSPF area ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 456: | Line 456: | ||
<tr> | <tr> | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>yes | <td>yes | no; Default: '''no'''</td> | ||
<td>Toggles OSPF network ON or OFF</td> | <td>Toggles OSPF network ON or OFF</td> | ||
</tr> | </tr> | ||
| Line 470: | Line 470: | ||
</tr> | </tr> | ||
</table> | </table> | ||
[[Category:RUT240 WebUI]] | |||
Revision as of 07:54, 1 March 2019
Main Page > EOL Products > RUT240 > RUT240 Manual > RUT240 WebUI > RUT240 Network section > RUT240 RoutingSummary
This chapter is an overview of the Routing section in RUT devices.
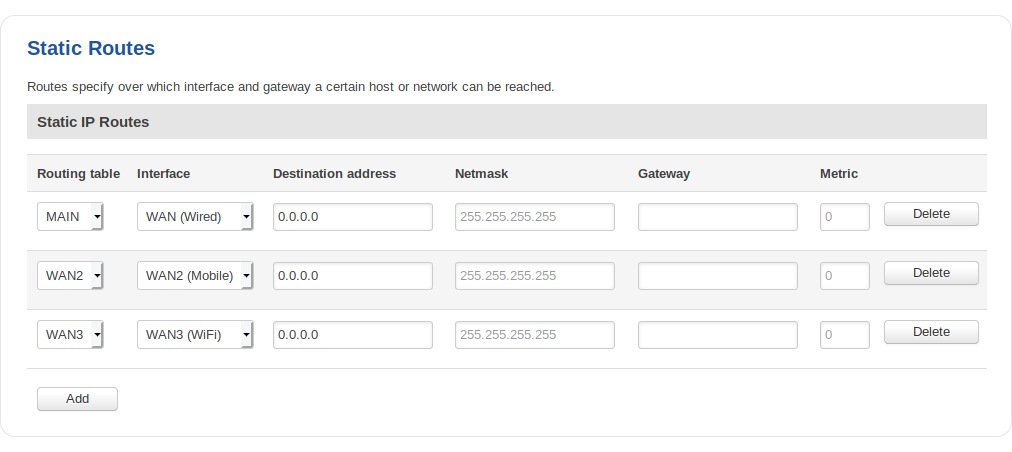
Static Routes
Static routes specify over which interface and gateway a certain host or network can be reached. In this page you can configure your own custom routes.
| field name | value | description |
|---|---|---|
| Routing table | Main | WAN | WAN2 | WAN3; Default: WAN | Defines which table will be used for the route in question |
| Interface | LAN | WAN(wired) | WAN2(Mobile) | WAN3(WiFi) | VPN instances; Default: WAN(wired) | The zone where the target network resides |
| Destination address* | ip; Default: 0.0.0.0 | The address of the destination network |
| Netmask* | ip; Default: 0.0.0.0 | A Mask that is applied to the Target to determine to what actual IP addresses the routing rule applies |
| Gateway | ip; Default: " " | Defines where the router should send all the traffic that applies to the rule |
| Metric | integer; Default: 0 | The Metric value is used as a sorting measure. If a packet about to be routed fits two rules, the one with the higher metric is applied |
*Additional notes on Destination & Netmask:
You can define a rule that applies to a single IP like this: Destination - some IP; Netmask - 255.255.255.255. Furthermore, you can define a rule that applies to a segment of IPs like this: Destination – some IP that STARTS some segment; Netmask – Netmask that defines how large the segment is. e.g.:
| field name | value | description |
|---|---|---|
| 192.168.55.161 | 255.255.255.255 | Only applies to 192.168.55.161 |
| 192.168.55.0 | 255.255.255.240 | Applies to IPs in the 192.168.55.0 - 192.168.55.255 |
| 192.168.55.240 | 255.255.255.240 | 192.168.55.240 - 192.168.55.255 |
| 192.168.55.161 | 255.255.255.0 | 192.168.55.0 - 192.168.55.255 |
| 192.168.0.0 | 255.255.0.0 | 192.168.0.0 - 192.168.255.255 |
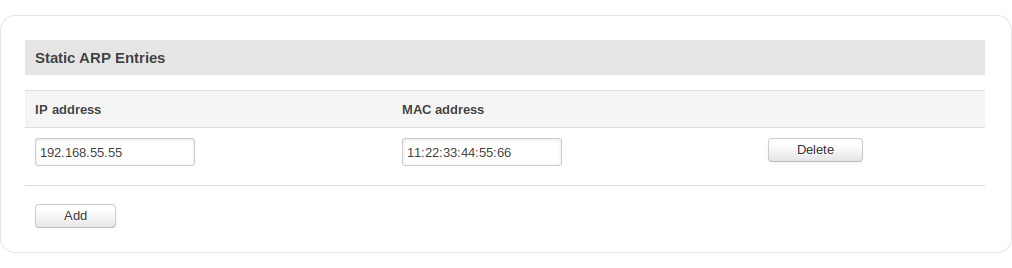
Static ARP entries
Static ARP entries are used to bind a MAC address to a specific IP address. For example, if you want a device to get the same IP every time it connects to the router, you can create a Static ARP entry by binding that device’s MAC address to the desired IP address. The router will then create an entry in the ARP table, which in turn will make sure that that device will get the specified IP address every time.
Dynamic Routes
BGP Protocol
Border Gateway Protocol (BGP) is a standardized exterior gateway protocol designed to exchange routing and reachability information among autonomous systems (AS) on the Internet. The protocol is often classified as a path vector protocol but is sometimes also classed as a distance-vector routing protocol. The Border Gateway Protocol makes routing decisions based on paths, network policies, or rule-sets configured by a network administrator and is involved in making core routing decisions.
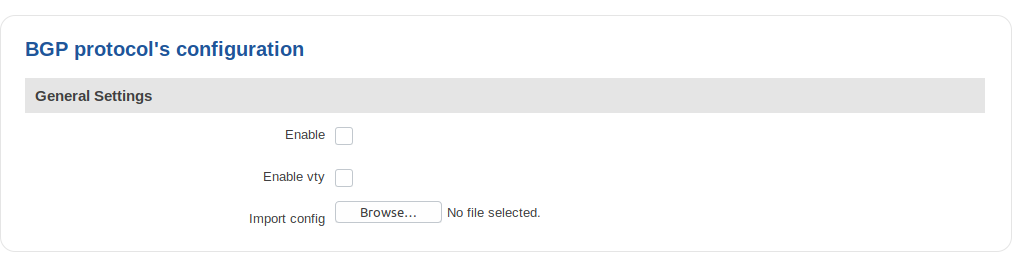
General Settings
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles the BGP protocol ON or OFF |
| Enable vty | yes | no; Default: no | Toggles vty access from LAN ON or OFF |
| Import config | - | Uploads an external BGP configuration |
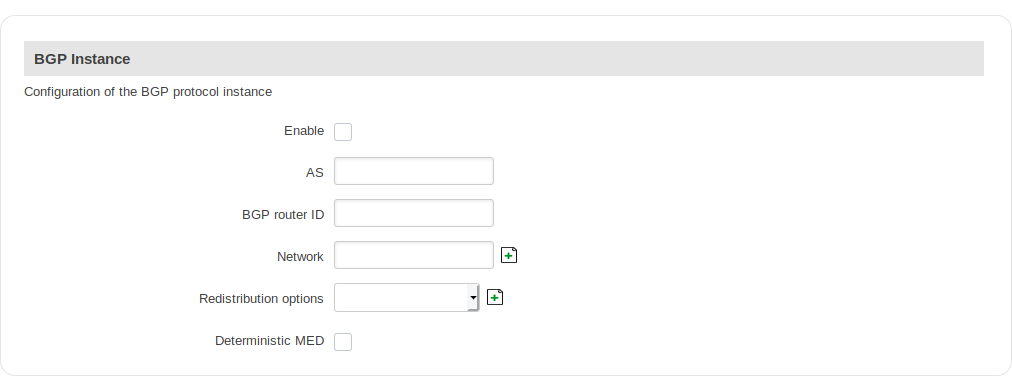
BGP Instance
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles the BGP instance ON or OFF |
| AS | integer: " " | AS number is an identification of an autonomous system. BGP protocol uses the AS number for detecting whether the BGP connection is an internal one or external one. [Required] |
| BGP router ID | string; Default: " " | The router id is used by BGP to identify the routing device from which a packet originated. Default router ID value is selected as the largest IP Address of the interface. |
| Network | string; Default: " " | Add an announcement network(s) |
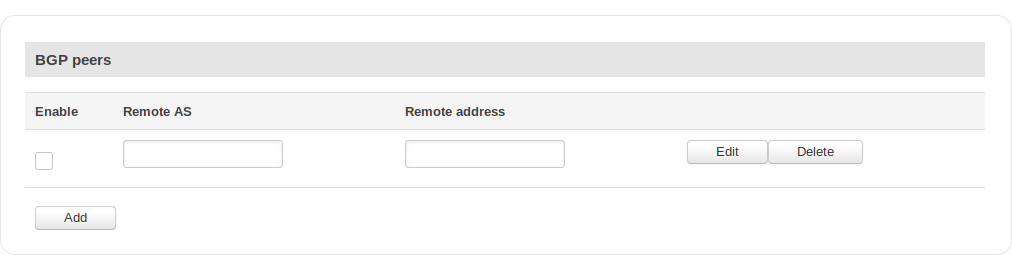
BGP Peers
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles the BGP peer ON or OFF |
| Remote AS | integer: " " | Neighbour's remote AS |
| Remote address | ip; Default: " " | Neighbour's remote IPv4 address |
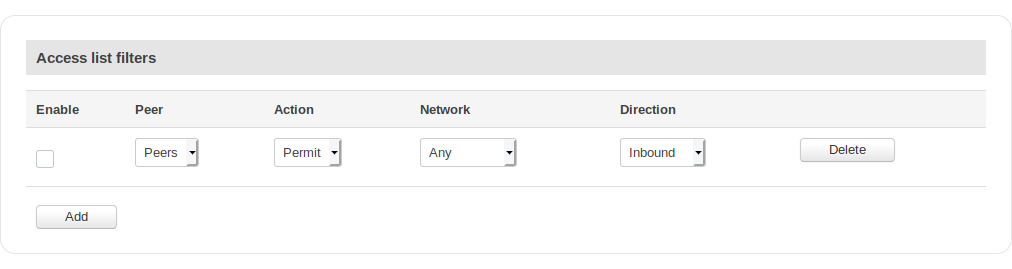
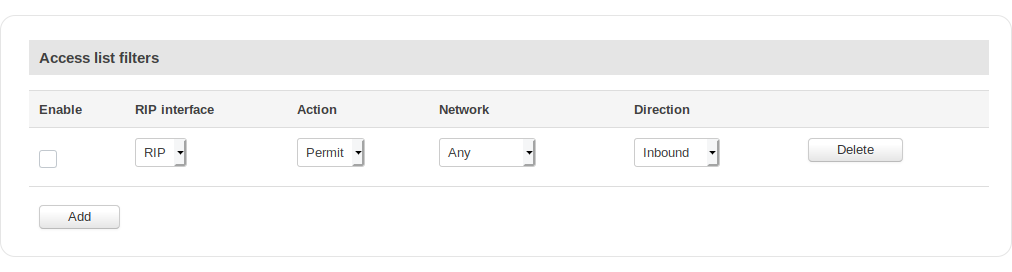
Access List Filters
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles the Access filter ON or OFF |
| Peer | bgp peer; Default: first peer on list | Applies the rule for the specified peer |
| Action | Permit | Deny; Default: Permit | Denies or permits matched entry |
| Network | Any | ip; Default: Any | Applies filter rule for this source network |
| Direction | Inbound | Outbound; Default: Inbound | If direction is Inbound, the access list is applied to input routes. If direction is Outbound the access list is applied to advertised routes |
RIP Protocol
The Routing Information Protocol (RIP) is one of the oldest distance-vector routing protocols which employ the hop count as a routing metric. RIP prevents routing loops by implementing a limit on the number of hops allowed in a path from source to destination. The maximum number of hops allowed for RIP is 15, which limits the size of networks that RIP can support. A hop count of 16 is considered an infinite distance and the route is considered unreachable. RIP implements the split horizon, route poisoning and holddown mechanisms to prevent incorrect routing information from being propagated.
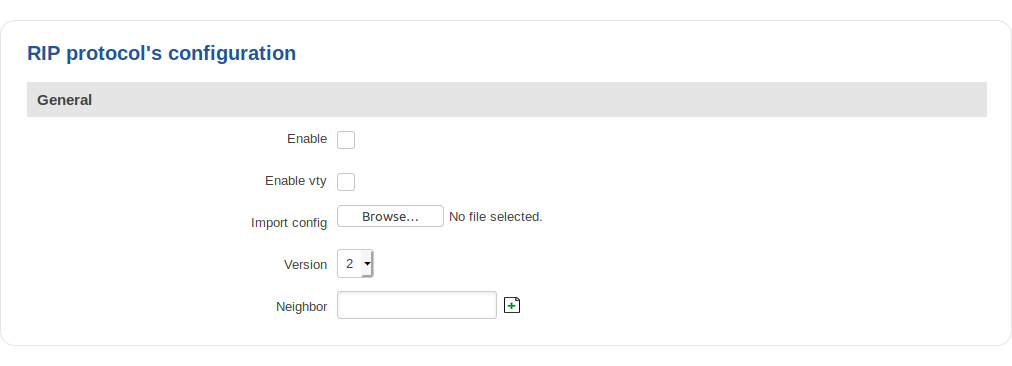
General
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles RIP Protocol ON or OFF |
| Enable vty | yes | no; Default: no | Toggles vty access from LAN ON or OFF |
| Import config | - | Uses imported RIP configurations |
| Version | 2 | 1; Default: 2 | Specifies the version of RIP |
| Neighbor | ip; Default: " " | Neighbour IP addres |
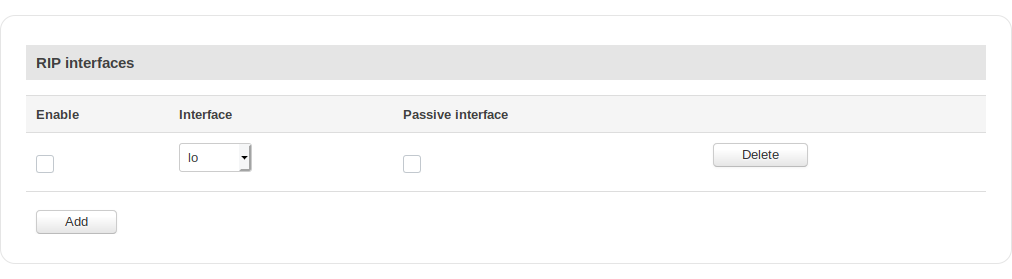
RIP Interfaces
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles RIP Interface ON or OFF |
| Interface | network interface; Default: no | Network interface to be used with the RIP interface |
| Passive interface | yes | no; Default: no | Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and ripd does not send either multicast or unicast RIP packets |
Access list filters
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles the Access filter ON or OFF |
| Peer | bgp peer; Default: first peer on list | Applies the rule for the specified peer |
| Action | Permit | Deny; Default: Permit | Denies or permits matched entry |
| Network | Any | ip; Default: Any | Applies filter rule for this source network |
| Direction | Inbound | Outbound; Default: Inbound | If direction is Inbound, the access list is applied to input routes. If direction is Outbound the access list is applied to advertised routes |
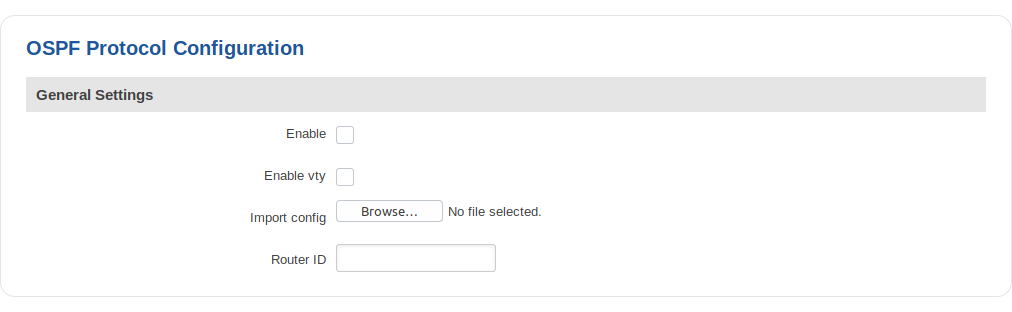
OSPF Protocol
Open Shortest Path First (OSPF) is a routing protocol for Internet Protocol (IP) networks. It uses a link state routing (LSR) algorithm and falls into the group of interior gateway protocols (IGPs), operating within a single autonomous system (AS). It is defined as OSPF Version 2 in RFC 2328 for IPv4.
General Settings
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles OSPF Protocol ON or OFF |
| Enable vty | yes | no; Default: no | Toggles vty access from LAN ON or OFF |
| Import config | - | Uses imported OSPF configurations |
| Router ID | ip; Default: " " | Sets the router-ID of the OSPF process. The router-ID may be an IP address of the router, but need not be - it can be any arbitrary 32bit number |
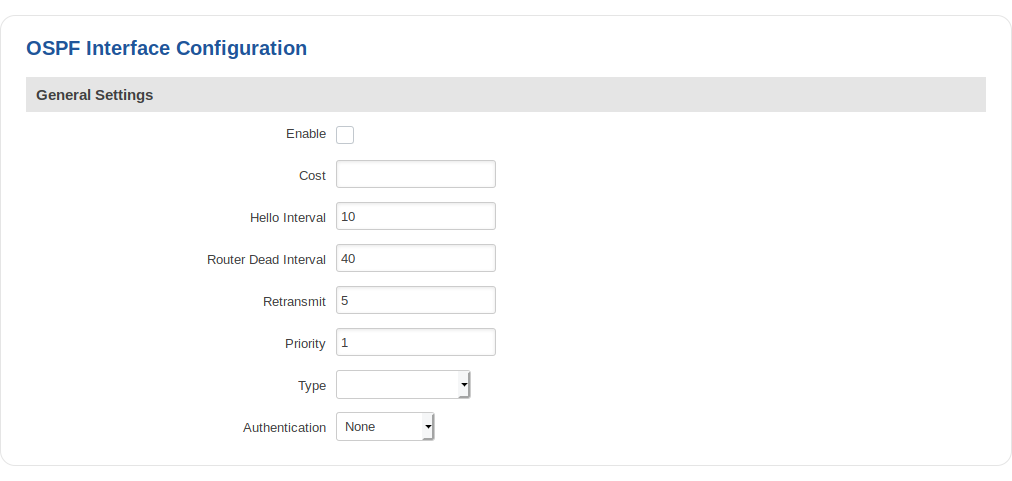
OSPF Interface
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles OSPF interface ON or OFF |
| Cost | integer [1..65535]; Default: 10 | The cost value is set to router-LSA’s metric field and used for SPF calculation |
| Hello interval | integer [1..65535]; Default: 10 | Hello packets will be sent at the frequency specified in this field (in seconds) |
| Router dead interval | integer [1..65535]; Default: 40 | This value must be the same for all routers attached to a common network |
| Retransmit | integer [1..65535]; Default: 5 | This value is used when re-transmitting Database Description and Link State Request packets |
| Priority | integer [0..255]; Default: 1 | The router with the highest priority will be more eligible to become the Designated Router. Setting the value to 0, makes the router ineligible to become the Designated Router |
| Type | Broadcast | Nonbroadcast | Point-to-point | Point-to-multipoint; Default: " " | Set explicit network type for the specified interface |
| Authentication | None | Password | MD5 HMAC; Default: " " | Specifies the authentication mode that should be used for the interface |
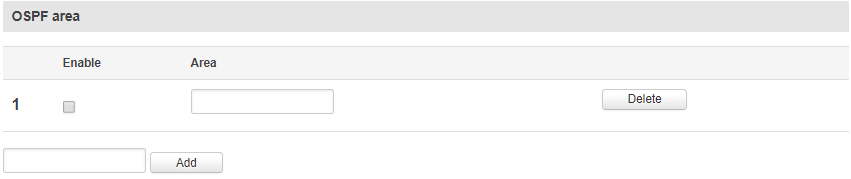
OSPF Area
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles OSPF area ON or OFF |
| Cost | [a.b.c.d]; Default: " " | Specifies OSPF area |
OSPF Networks
| field name | value | description |
|---|---|---|
| Enable | yes | no; Default: no | Toggles OSPF network ON or OFF |
| Network | [a.b.c.d/m]; Default: " " | This command specifies the OSPF enabled interface. If the interface has an address from the range a.b.c.d/m then enables OSPF on this interface so the router can provide network information to the other OSPF routers via this interface |
| Area | ospf area; Default: " " | Specifies OSPF area |