Template:Networking rutos configuration example guest wifi: Difference between revisions
| Line 239: | Line 239: | ||
<tr> | <tr> | ||
<th width=355; style="border-bottom: 1px solid white;></th> | <th width=355; style="border-bottom: 1px solid white;></th> | ||
<th width=790; style="border-bottom: 1px solid white;" rowspan=2>[[File: | <th width=790; style="border-bottom: 1px solid white;" rowspan=2>[[File:Networking rutos configuration examples guest wifi 13 v1.jpg|border|class=tlt-border|728px|right]]</th> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
Revision as of 11:29, 22 July 2020
Introduction
Most of us are aware, that network security is extremely important. If your WiFi network is not properly secured, it makes you and all of your home or office resources vulnerable to a variety of security threats. To stay ahead of the curve, many companies and home users have guest WiFi. Unlike your regular WiFi network that you or your company members use, the guest WiFi network restricts what your guests can do in your network. It gives visitors access to the Internet connection, but nothing else making you or your company a lot more secure. This chapter is a guide on configuring a guest WiFi.
Configuring router (RUTX)
Before you start configuring the router turn on "Advanced WebUI" mode. You can do that by clicking the "Basic" button under "Mode", which is located at the top-right corner of the WebUI.
New WiFi AP
 |
|
|---|---|
|
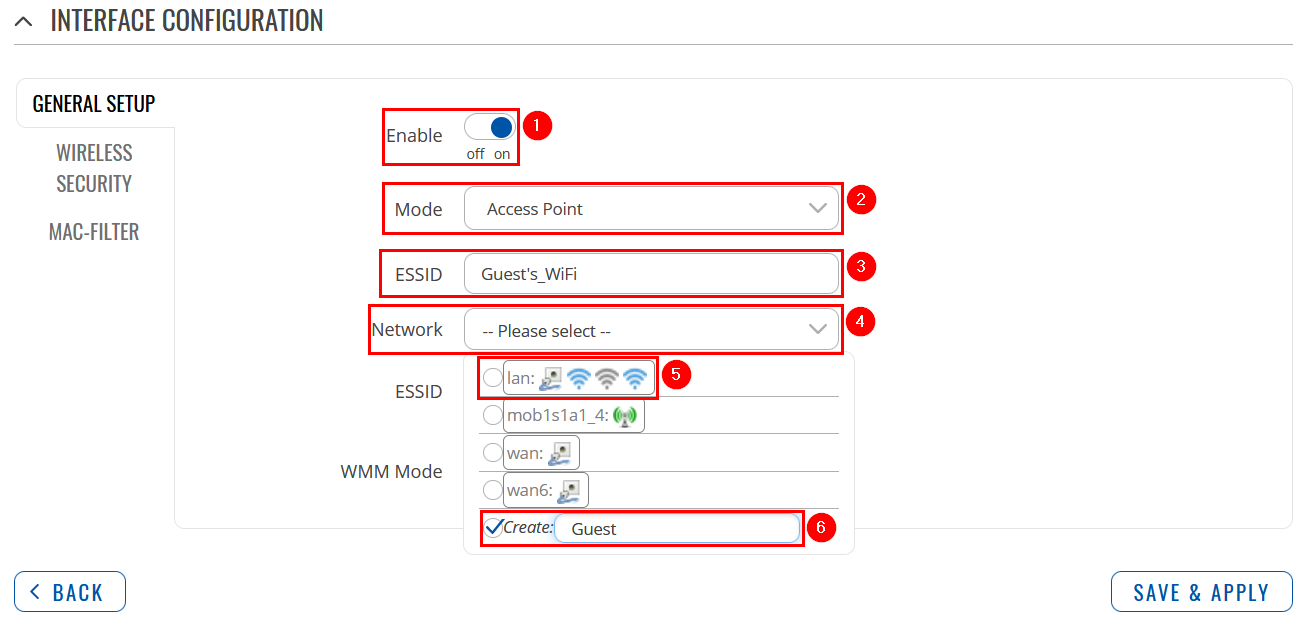
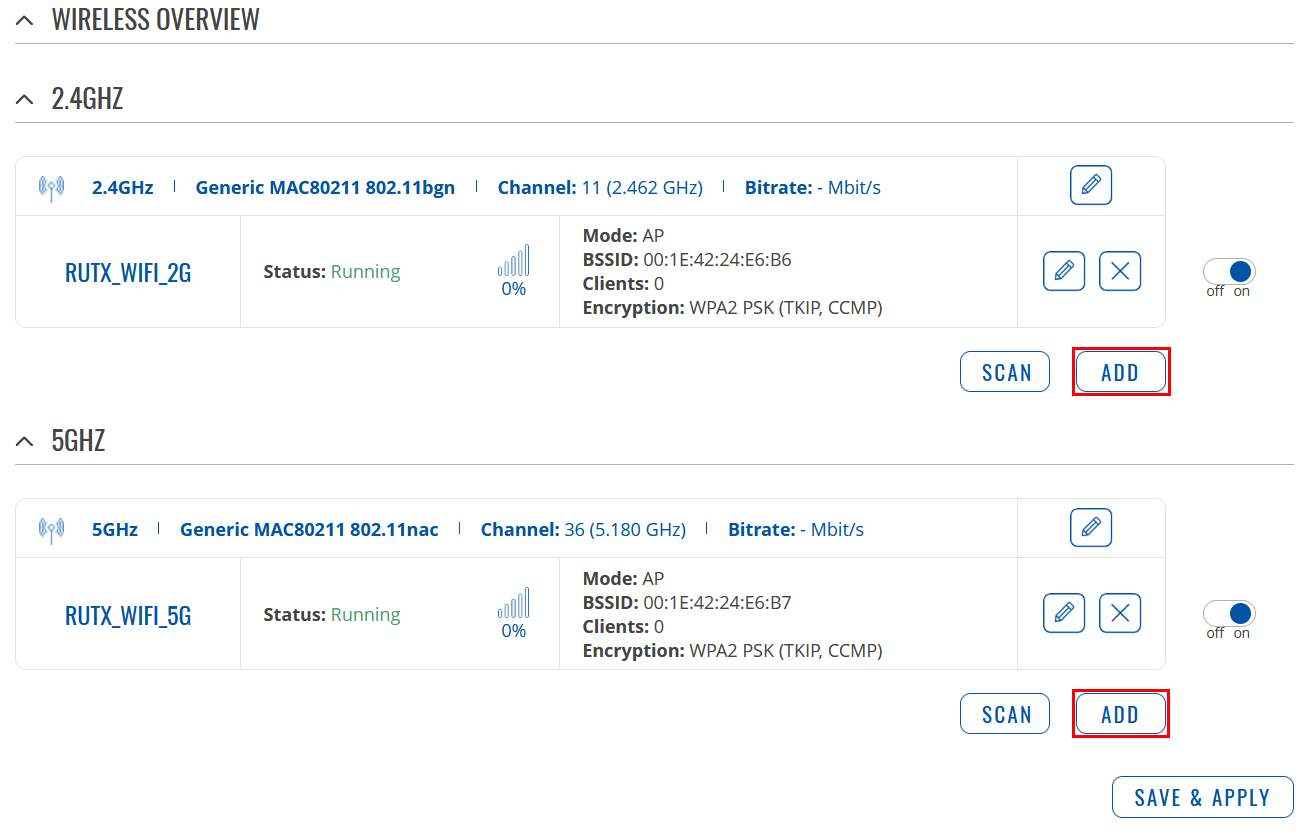
Login to the router's WebUI, navigate to the Network → Wireless page. Click Add. You can use either, 2.4GHz or 5GHz WiFi. Then you will be forwarded to the configuration window. |
 |
|
|---|---|
|
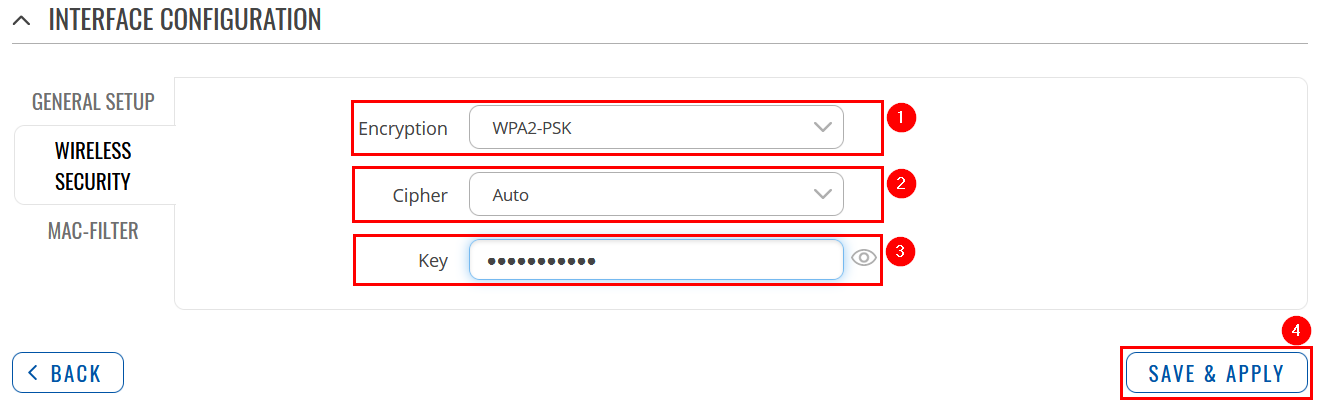
Switch to Wireless Security tab and do the following:
|
 |
|
|---|---|
|
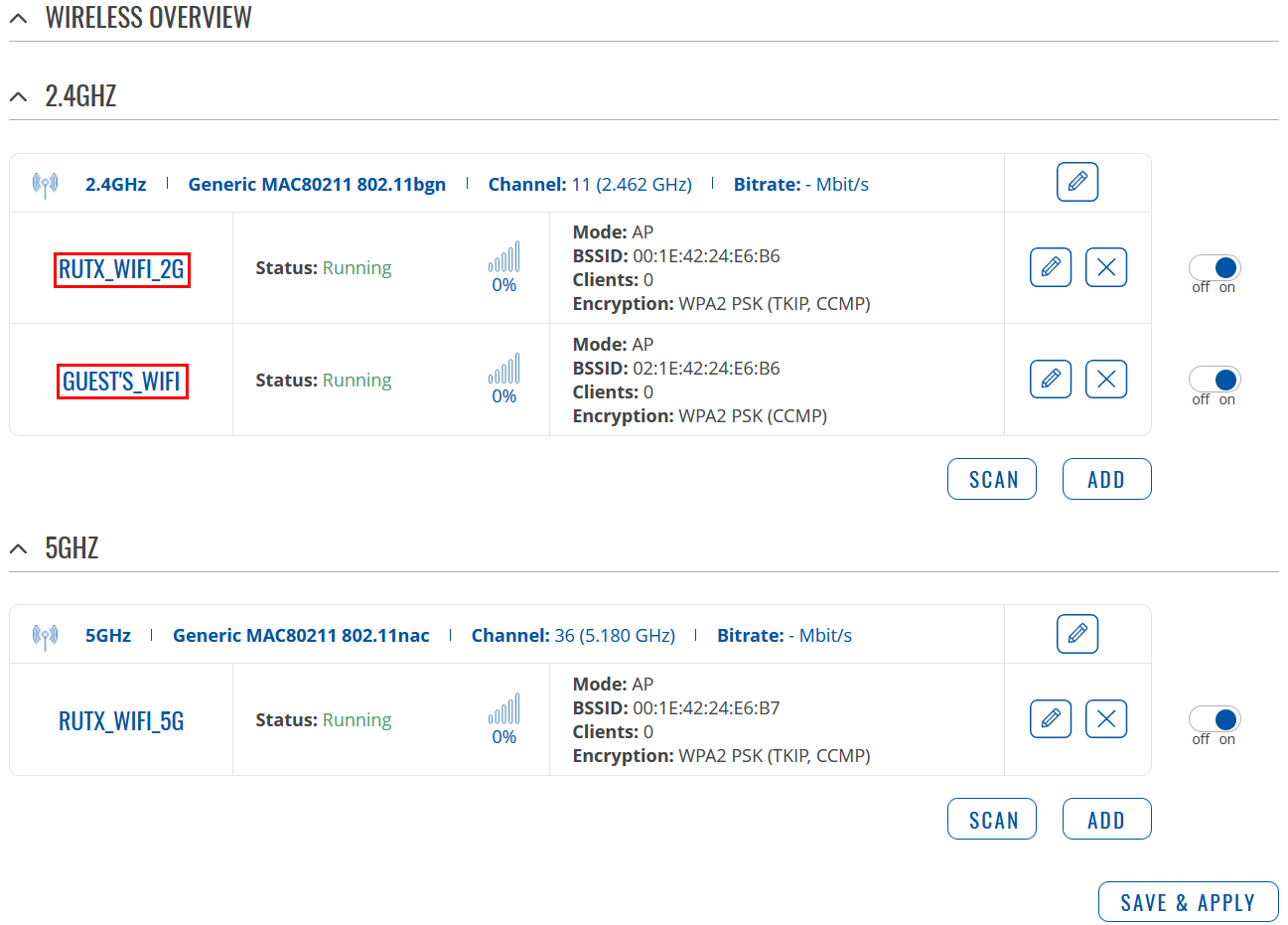
Wait for configuration to apply. Two Wireless Access Points should be enabled |
New LAN interface
 |
|
|---|---|
|
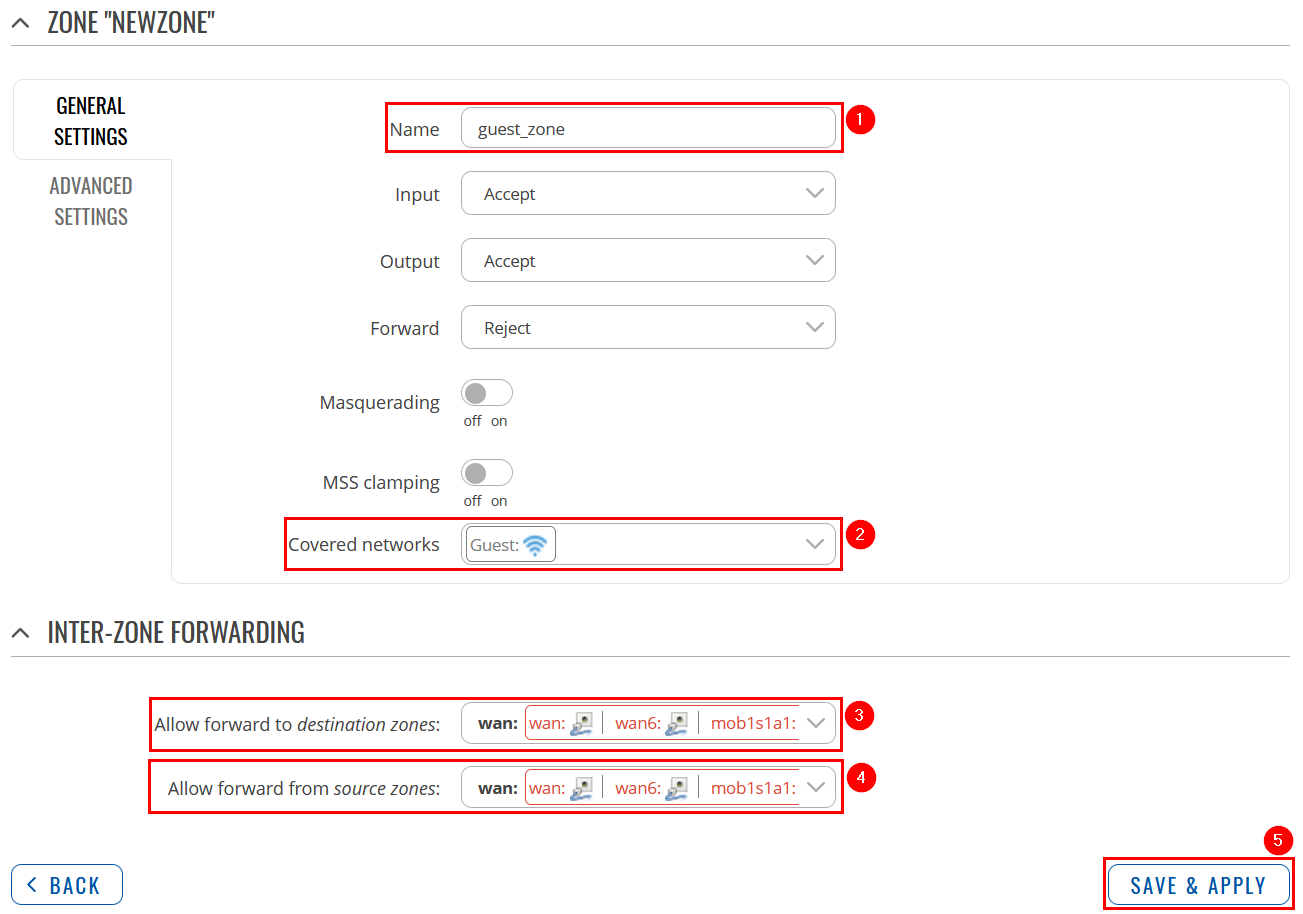
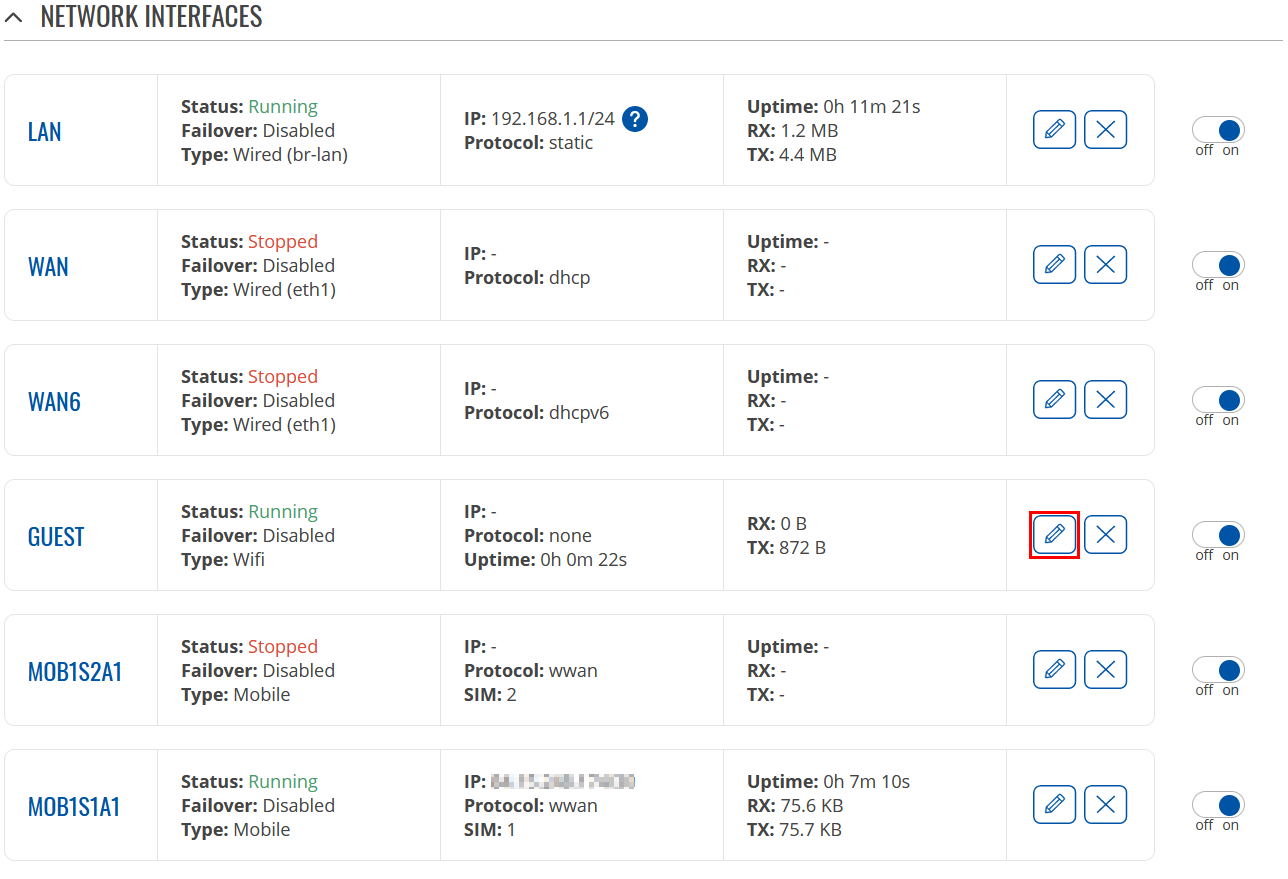
Now go to Network → Interfaces and press Edit next to your newly created LAN interface: |
 |
|
|---|---|
|
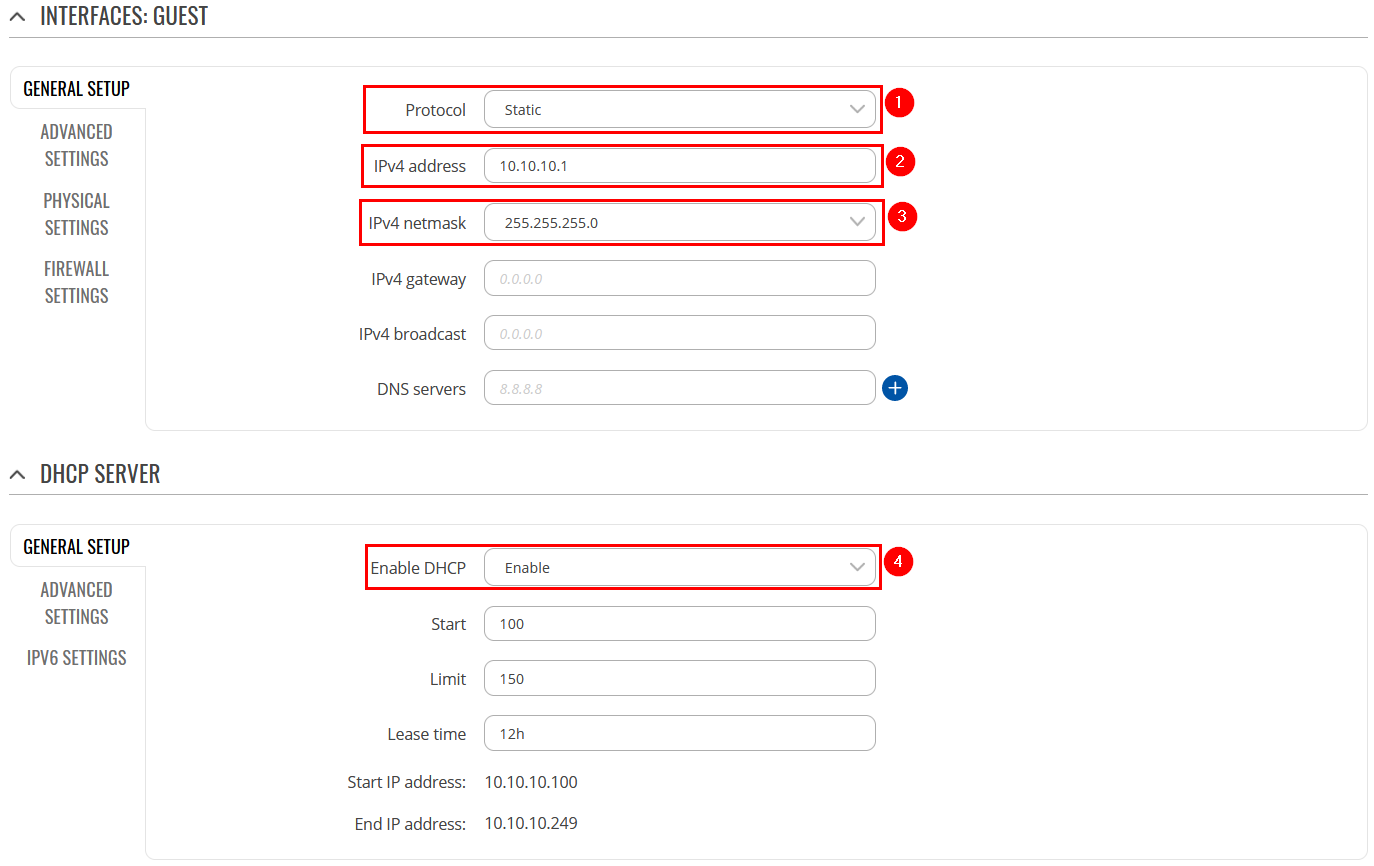
In the General setup section, do the following:
|
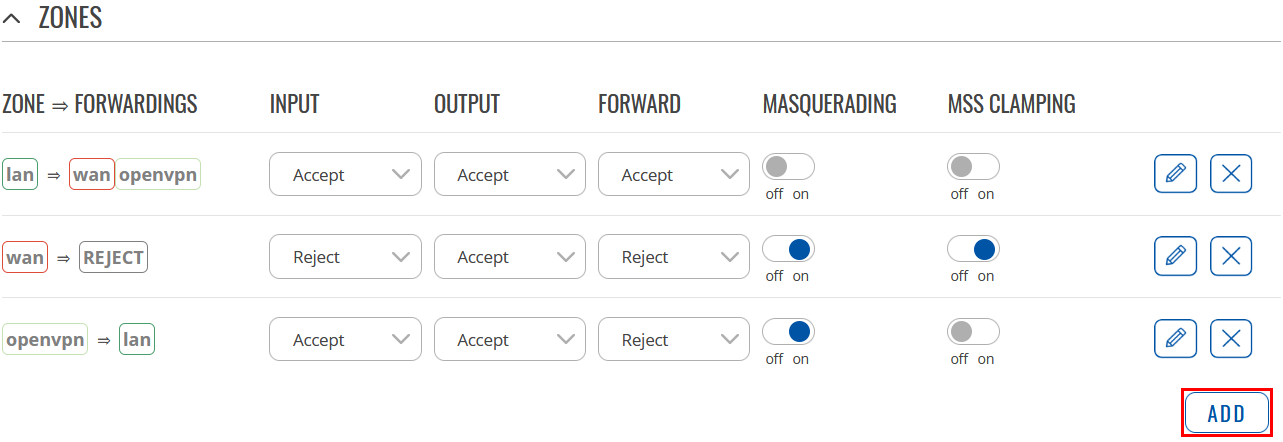
Firewall rules
 |
|
|---|---|
|
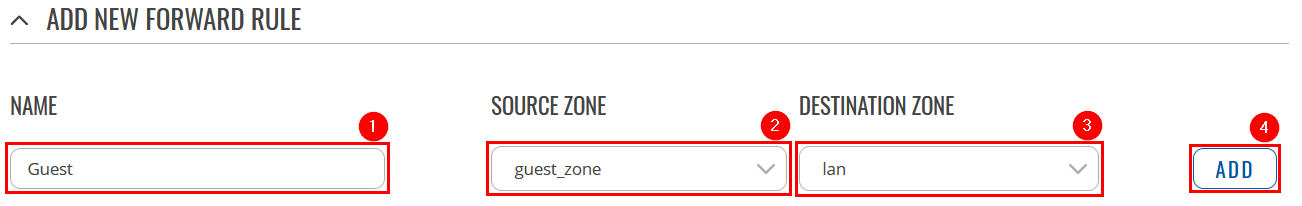
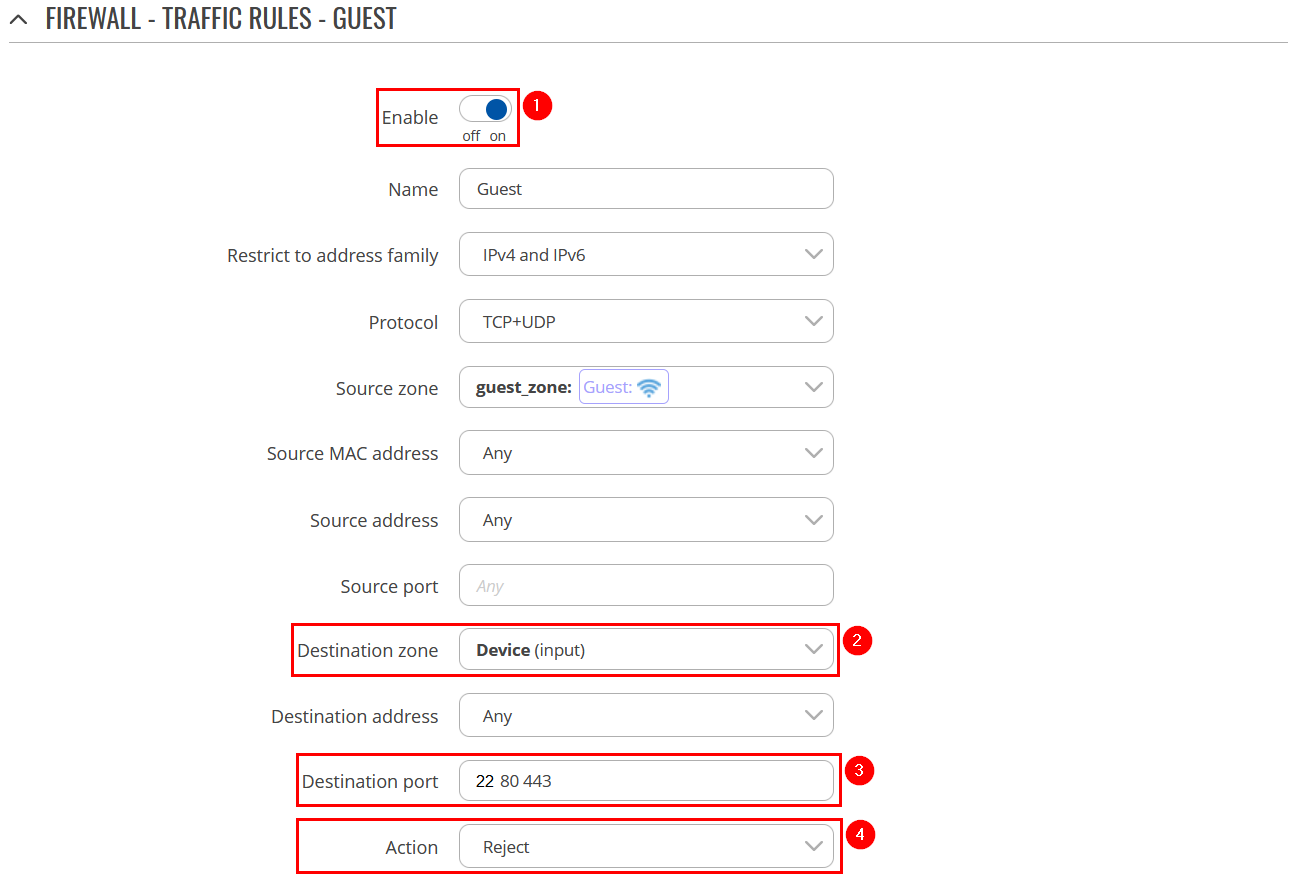
Navigate to Network → Firewall → General Settings. There create a new Zone rule by pressing Add button. Then you will be forwarded to the configuration window. |
Results
If you've followed all the steps presented above, your configuration should be finished. If you are near a RUT, that is, in a wireless zone, turn on WiFi on your device and view the available networks. You should see the available SSID - "RUTX_WiFi_2G" and "Guest_WiFi". Select one of them and enter the appropriate WiFi password.
Wireless users connected to SSID: “RUTX_WIFI”, will be assign to “LAN”, and will get IP from main pool 192.168.1.0/24.
Wireless users connected to SSID: “GUEST'S_WIFI”, will be assign to LAN “Guest”, and will get IP from new pool 10.10.10.0/24.
Guest hosts are unable to access any data from pool 192.168.1.0/24.