RUTX10 SNMP
The information in this page is updated in accordance with firmware version RUTX_R_00.07.20.
Summary
Simple Network Management Protocol (SNMP) is a network management protocol used for collecting information and configuring network devices. This page is an overview of the SNMP function in RUTX10 devices.
SNMP settings
The SNMP settings page is used to configure SNMP accessibility and general SNMP information for your device.
SNMP agent settings
| Field | Value | Description |
|---|---|---|
| Enable SNMP service | off | on; default: off | Enable SNMP (Simple Network Management Protocol) service on system startup. |
| Enable remote access | off | on; default: off | Create a firewall rule that allows access to SNMP for remote hosts. |
| IP type | IPv4 | IPv6 | IPv4v6; default: IPv4 | IP type used by SNMP. |
| Port | integer [0..65535]; default: 161 | TCP/UDP port number used for the connection. |
| SNMP v1 Mode | off | on; default: on | Enable/disable SNMP v1 Mode. |
| SNMP v2c Mode | off | on; default: on | Enable/disable SNMP v2c Mode. |
| SNMP v3 Mode | off | on; default: off | Enable/disable SNMP v3 Mode. |
SNMP System Summary
The SNMP System Summary section contains general information about SNMP on this device. You can also download this device's MIB file from this section.
| Field | Value | Description |
|---|---|---|
| MIB file | -(interactive button) | Download the MIB file containing custom Teltonika module tree for this device. |
| Teltonika OID path | 1.3.6.1.4.1.48690 | The OID path containing Teltonika IANA Private Enterprise Number (PEN). All custom private SNMP modules are referenced under this OID path. |
| Location | string; default: location | Location of the system. If the field is empty, the option will have read-write permissions. If not, the option will become read-only. |
| Contact | string; default: [email protected] | Contact information. If the field is empty, the option will have read-write permissions. If not, the option will become read-only. |
| Name | string; default: name | Name of the system. If the field is empty, the option will have read-write permissions. If not, the option will become read-only. |
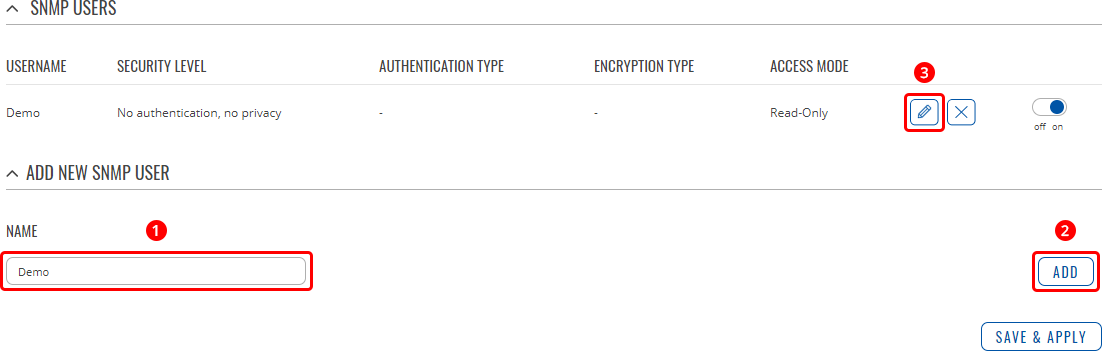
SNMP v3 users
The SNMP v3 users page is used to create and manage users, who can be authenticated using SNMP v3. To configure an SNMP user, you must first create it:
- Enter a custom name for the new user in the 'Name' field.
- Click the 'Add' button.
- Click the 'Edit' button next to the newly created user.
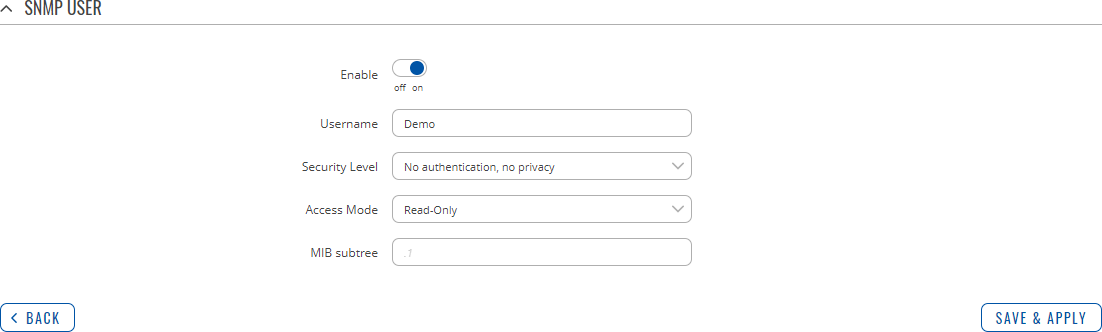
The SNMP user configuration window should look similar to this:
Note: this table has coloring scheme to indicate which fields can be seen with different configuration.
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Turns this SNMP user on or off. |
| Username | string; default: none | Name of the SNMP user configuration. |
| Security level | No authentication, no privacy | Authentication, no privacy | Authentication and privacy; default: No authentication, no privacy | A security level is an authentication strategy that is set up for the user.
No authentication, no privacy - authenticates with a username. Authentication - provides MD5 or SHA algorithms for authentication. Privacy - Provides DES or AES encryption. |
| Authentication, no privacy | Authentication and privacy: Authentication type | SHA | MD5; default: SHA | Set authentication type to use with SNMP v3. |
| Authentication, no privacy | Authentication and privacy: Authentication passphrase | string; default: none | Set authentication passpharse to generate key for SNMP v3. |
| Authentication and privacy: Privacy type | DES | AES; default: DES | Set privacy type to use with SNMP v3. |
| Authentication and privacy: Privacy passphrase | string; default: none | Set privacy passpharse to generate key for SNMP v3. |
| Access Mode | Read-Only | Read-Write; default: Read-Only | Access mode specifies which access the host has in the community and if they are allowed to retrieve and modify MIB variables from a specific SNMP agent. |
| MIB subtree | string; default: none | Leave empty to access full MIB tree. |
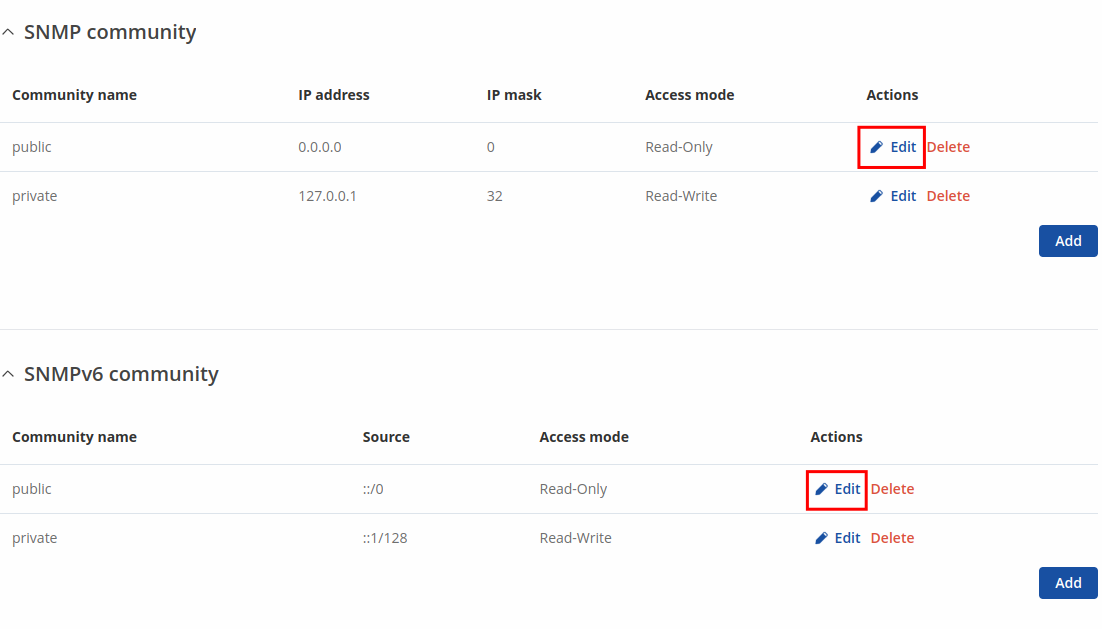
Communities
The SNMP Community section is used to manage access rights. You can edit an SNMP community by clicking the 'Edit' button next to it:
This will redirect you to the community's configuration page.
| Field | Value | Description |
|---|---|---|
| Community name | string; default: none | SNMP community name is an ID that allows access to a routers SNMP data. |
| IP Address | ip; default: none | IP address of the community. |
| IP Mask | ip; default: none | Netmask for IP of the community. |
| Access Mode | Read-Only | Read-Write; default: Read-Only | Access mode specifies if you can only read or read and write information from and to the device. |
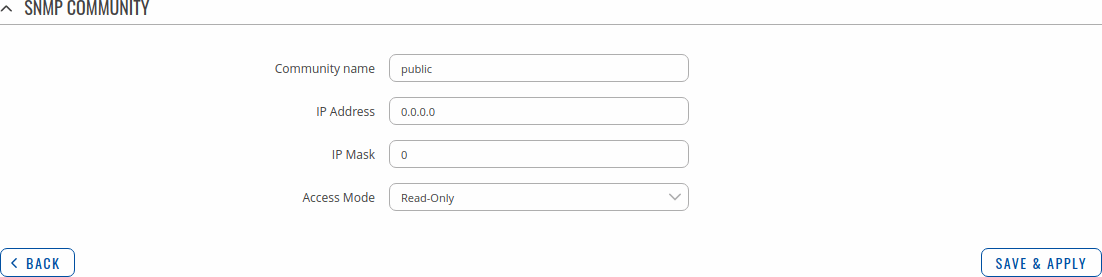
SNMPv6 community configuration page:
| Field | Value | Description |
|---|---|---|
| Community name | string; default: public | Name of the community. |
| Source | ip6 | domain name; default: default | Source of the community. |
| Access Mode | Read-Only | Read-Write; default: Read-Only | Access mode for current community. |
Trap Settings
SNMP Traps are used to send alert messages to a central collector, the “SNMP manager” when an important event happens. A benefit of using Traps for reporting alarms is that they trigger instantaneously, rather than waiting for a status request from the manager.
Trap settings page is divided in two sections - Trap service settings and Trap rules. Trap service settings lets you manage hosts which will get configured alert messages, Trap rules lets you manage rules which when triggered will send alerts.
Trap Service Settings
The Trap Service Settings is used to manage host which will be alerted when an SNMP trap is triggered
| Field | Value | Description |
|---|---|---|
| Enable | off | on; default: off | Enables Trap service. |
| Host | url | ip; default: none | Host to transfer SNMP (Simple Network Management Protocol) traffic to. |
| Port | integer [0..65535]; default: 162 | Port for trap host. |
| Community | string; default: public | The SNMP (Simple Network Management Protocol) community is an ID that allows access to a routers SNMP data. |
Trap Rules
SNMP Trap Rules are alerts that trigger when certain user-specified events occur. When the trigger event happens, the trap will notify known SNMP hosts.
You can create a new trap rule by clicking the 'Add' button.
You should be redirected to the rule's configuration page which should look something like this:
Above is an example of what rule configuration window looks like. Below is a table with detailed explanations on how to configure the rule and what each of the fields mean.
To avoid redundancy, screenshots for the other rules will not be provided, since the structures, syntax and the overall look of the configuration windows for each rule are very similar. Instead, only tables containing information on how to edit each rule will be provided.
Input/Output Trap type
| field name | value | description |
|---|---|---|
| Trigger | Input(3) | Output(4); default: Input(3) | The trigger which invokes the rule. |
| State change | High level | Low level | Both; default: Both | Selects which pin state will trigger the SNMP trap. |
Events log Trap type
| Event | Event subtype | Description |
|---|---|---|
| Config change | All | Specific config change; default: all | Informs on changes to the device's configuration. |
| Reboot | All | From Web UI | From ping reboot | From reboot scheduler | From button; default: All | Informs on if the device was rebooted. |
| Startup | Device startup completed | After unexpected shutdown | Informs on when the device is fully booted. |
| New DHCP client | All | Connected from LAN; default All | Informs on new DHCP lease give outs. |
| Reboot | All | From button | From Input/Output | From Ping Reboot | From wget Reboot | From Reboot Scheduler | From WebUI; default: All | Informs after device reboot occurrences. |
| SSH | All | Successful authentication | Unsuccessful authentication; default: All | Informs on successful or unsuccessful SSH login attempts. |
| WebUI | ALL | Successful authentication | Unsuccessful authentication; default: All | Informs on successful or unsuccessful HTTP/HTTPS login attempts. |
| Fota | Firmware update is now available | Informs if firmware update is now available |
Hotspot client Trap type
| Field | Value | Description |
|---|---|---|
| Trigger | Connected | Disconnected; default: Connected | The trigger which invokes the rule. |
SNMP variables list
| Name | OID | Description |
|---|---|---|
| Device | ||
| serial | .1.3.6.1.4.1.48690.1.1.0 | Device serial number |
| deviceName.0 | .1.3.6.1.4.1.48690.1.2.0 | Device name |
| productCode | .1.3.6.1.4.1.48690.1.3.0 | Device product (ordering) code |
| batchNumber | .1.3.6.1.4.1.48690.1.4.0 | Device batch number |
| hardwareRevision | .1.3.6.1.4.1.48690.1.5.0 | Device hardware revision |
| fwVersion | .1.3.6.1.4.1.48690.1.6.0 | Device RutOS firmware version |
| deviceUptime | .1.3.6.1.4.1.48690.1.7.0 | Device uptime |
| cpuUsage | .1.3.6.1.4.1.48690.1.8.0 | CPU usage |
| Input/Output notifications | ||
| digitalInputNotification | .1.3.6.1.4.1.48690.4.2.1 | Digital input trap |
| digitalOutputNotification | .1.3.6.1.4.1.48690.4.2.2 | Digital output trap |
| Hotspot Notifications | ||
| clientConnectedNotification | .1.3.6.1.4.1.48690.4.3.1 | Hotspot client connected trap |
| clientDisconnectedNotification | .1.3.6.1.4.1.48690.4.3.2 | Hotspot client disconnected trap |
| Hotspot | ||
| hsState | .1.3.6.1.4.1.48690.5.1.0 | Current Hotspot state |
| hsIP | .1.3.6.1.4.1.48690.5.2.0 | Hotspot IP address |
| hsNet | .1.3.6.1.4.1.48690.5.3.0 | WiFi interface ID |
| hsAuth | .1.3.6.1.4.1.48690.5.4.0 | Hotspot authentication type |
| hsSessionCount | .1.3.6.1.4.1.48690.5.5.0 | Hotspot current active session (connected user) count |
| Hotspot Sessions | ||
| hssIndex | .1.3.6.1.4.1.48690.5.6.1.1.1 | Connected Hotspot user indexes |
| hssMAC | .1.3.6.1.4.1.48690.5.6.1.2.1 | Hotspot user MAC addresses |
| hssIP | .1.3.6.1.4.1.48690.5.6.1.3.1 | Hotspot user local IP addresses |
| hssID | .1.3.6.1.4.1.48690.5.6.1.4.1 | Hotspot user session unique IDs |
| hssUsername | .1.3.6.1.4.1.48690.5.6.1.5.1 | Hotspot connected user usernames |
| hssState | .1.3.6.1.4.1.48690.5.6.1.6.1 | Hotspot user session states |
| hssDwLimit | .1.3.6.1.4.1.48690.5.6.1.7.1 | Hotspot user download limits |
| hssUpLimit | .1.3.6.1.4.1.48690.5.6.1.8.1 | Hotspot user upload limits |
| hssTimeLimit | .1.3.6.1.4.1.48690.5.6.1.9.1 | Hotspot user session time limit |
| hssIdleTimeout | .1.3.6.1.4.1.48690.5.6.1.10.1 | Hotspot user maximum idle timeout values |
| hssDwBandwidth | .1.3.6.1.4.1.48690.5.6.1.11.1 | Hotspot user maximum download speed |
| hssUpBandwidth | .1.3.6.1.4.1.48690.5.6.1.12.1 | Hotspot user maximum upload speed |
| hssURL | .1.3.6.1.4.1.48690.5.6.1.13.1 | Hotspot URL |
| Input/Output | ||
| ioCount | .1.3.6.1.4.1.48690.6.1 | Count of I/O |
| ioTable | .1.3.6.1.4.1.48690.6.2 | A list of I/O. The number of entries is given by the value of ioCount |
| ioEntry | .1.3.6.1.4.1.48690.6.2.1 | An entry containing information of a particular I/O |
| ioIndex | .1.3.6.1.4.1.48690.6.2.1.1 | A unique value, greater than zero, for each session |
| ioSystemName | .1.3.6.1.4.1.48690.6.2.1.2 | The name of the I/O |
| ioName | .1.3.6.1.4.1.48690.6.2.1.3 | The name of the I/O, as displayed in WebUI |
| ioType | .1.3.6.1.4.1.48690.6.2.1.4 | A description of I/O type |
| ioBidirectional | .1.3.6.1.4.1.48690.6.2.1.5 | Is I/O bidirectional? |
| ioState | .1.3.6.1.4.1.48690.6.2.1.6 | State of I/O |
| ioInput | .1.3.6.1.4.1.48690.6.2.1.7 | Is I/O an input? |
| ioInverted | .1.3.6.1.4.1.48690.6.2.1.8 | Is value of I/O inverted? |
| ioCurrent | .1.3.6.1.4.1.48690.6.2.1.9 | Current amount flowing though ACL |
| ioPercentage | .1.3.6.1.4.1.48690.6.2.1.10 | Percentage of ACL |
| ioStateNumeric | .1.3.6.1.4.1.48690.6.2.1.11 | Numeric state of I/O |