Difference between revisions of "L2TP over IPsec"
(→IPsec) |
|||
| Line 28: | Line 28: | ||
====Server (RUT1)==== | ====Server (RUT1)==== | ||
---- | ---- | ||
| − | * | + | * Login to the router's WebUI and navigate to '''Services → VPN → IPsec'''. Enter a custom name for your IPsec instance and click the "Add" button. Then click the "Edit" button located next to the newly created instance after which you will redirected to that instance's configuration window. Adhere to the configurations presented in the figure below: |
[[File:L2tp over ipsec ipsec server.png]] | [[File:L2tp over ipsec ipsec server.png]] | ||
| + | |||
| + | * '''Enable''' - if checked, enables the IPsec instance | ||
| + | * '''Type''' - the type of the connection. '''Transport''' encrypts only the payload and Encapsulating Security Payload (ESP) trailer; so the IP header of the original packet is not encrypted. Transport mode is usually used when another tunneling protocol (such as [[VPN#GRE_Tunnel|GRE]], [[VPN#L2TP|L2TP]]) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets. NAT traversal is not supported with the transport mode | ||
| + | * '''Pre shared key''' - a shared password used for authentication between the peers. The value of this field must match the other instance | ||
| + | * '''Remote VPN endpoint''' - IP address or hostname of the remote IPsec instance. '''Leave empty''' for the server configuration | ||
====Client (RUT2)==== | ====Client (RUT2)==== | ||
| Line 40: | Line 45: | ||
====Testing the connection==== | ====Testing the connection==== | ||
---- | ---- | ||
| − | When you're done with the configuration, you should test whether it works before you move on. The simplest way to test an IPsec connection is using the '''ipsec status''' command. You can execute this command via a command line interface (CLI). A CLI is present in all RUTxxx routers' WebUIs. To access it, login to one of the routers' | + | When you're done with the configuration, you should test whether it works before you move on. The simplest way to test an IPsec connection is using the '''ipsec status''' command. You can execute this command via a command line interface (CLI). A CLI is present in all RUTxxx routers' WebUIs. To access it, login to one of the routers' WebUI (doesn't matter which one) and navigate to '''Services → CLI'''. Login to CLI with the user name '''root''' and the router's admin password. Then simply the ''ipsec status'' and press the "Enter" key: |
[[File:Testing ipsec transport example.png]] | [[File:Testing ipsec transport example.png]] | ||
Revision as of 10:19, 8 June 2018
Introduction
Layer 2 Tunneling Protocol (L2TP) is a VPN tunneling protocol that allows remote clients to use the public IP network to securely communicate with private corporate network servers. L2TP uses PPP over UDP (port 1701) to tunnel the data.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- Two RUTxxx routers of any type (excluding RUT850)
- At least one router with a Public Static or Public Dynamic IP addresses
- At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers
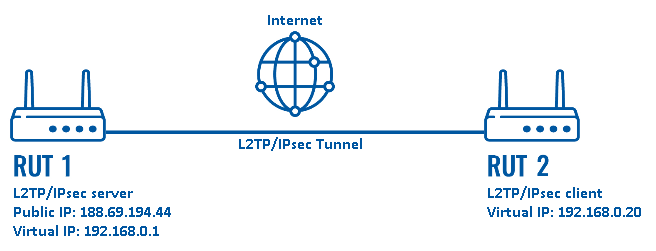
Configuration scheme:
The figure above depicts the L2TP/IPsec scheme. It is fairly similar to the L2TP and IPsec configuration schemes - the router with the Public IP address (RUT1) acts as the L2TP/IPsec server and the other router (RUT) acts a client. L2TP connects the networks of RUT1 and RUT2 and IPsec provides the encryption for the L2TP tunnel.
Router configuration
If you have familiarized yourself with the configuration scheme and have all of the devices in order, we can start configuring the routers using instructions provided in this section. To summarize, we'll be configuring an L2TP server and an IPsec Transport instance (server) on RUT1; an L2TP client and an IPsec Transport instance (client) on RUT2.
IPsec
First, you must configure a working IPsec Transport connection. This subsection contains instructions on how to do just that. The relevant parameters will be encapsulated in red rectangles. Explanations about these parameters will be provided under each example. Other used parameters will be defaults; you can find explanations for those parameters in the VPN manual page, IPsec section.
Server (RUT1)
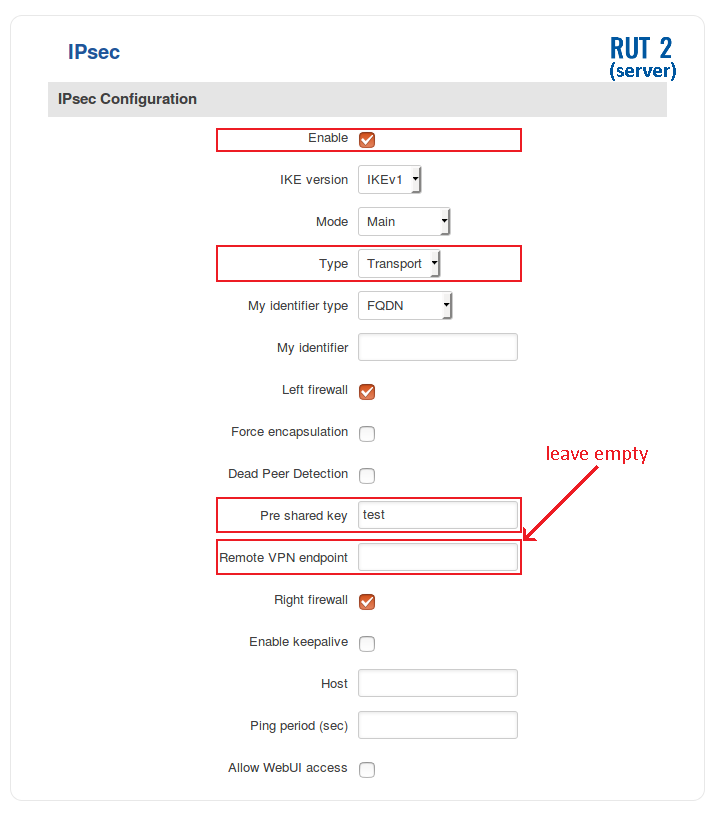
- Login to the router's WebUI and navigate to Services → VPN → IPsec. Enter a custom name for your IPsec instance and click the "Add" button. Then click the "Edit" button located next to the newly created instance after which you will redirected to that instance's configuration window. Adhere to the configurations presented in the figure below:
- Enable - if checked, enables the IPsec instance
- Type - the type of the connection. Transport encrypts only the payload and Encapsulating Security Payload (ESP) trailer; so the IP header of the original packet is not encrypted. Transport mode is usually used when another tunneling protocol (such as GRE, L2TP) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets. NAT traversal is not supported with the transport mode
- Pre shared key - a shared password used for authentication between the peers. The value of this field must match the other instance
- Remote VPN endpoint - IP address or hostname of the remote IPsec instance. Leave empty for the server configuration
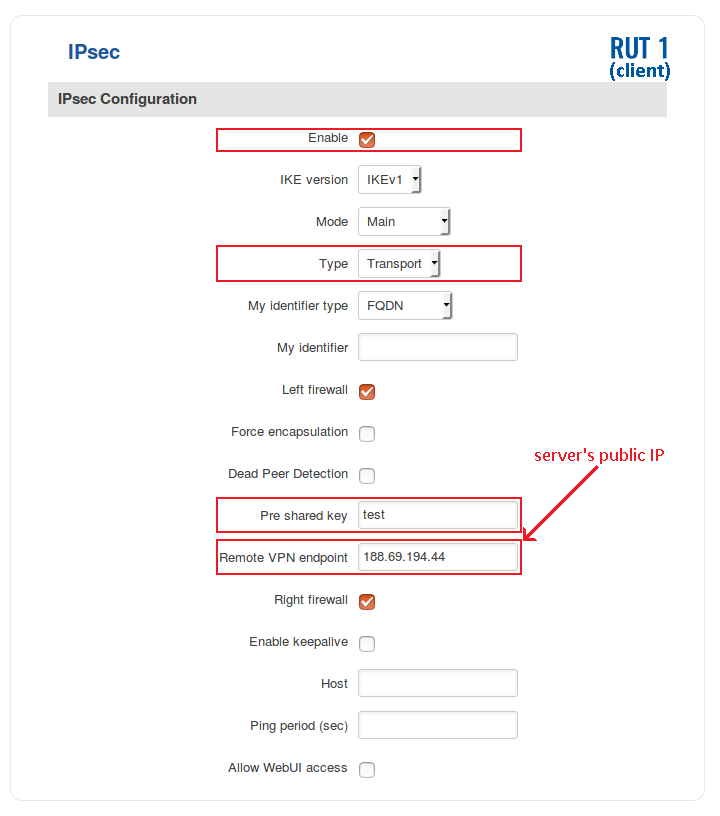
Client (RUT2)
Testing the connection
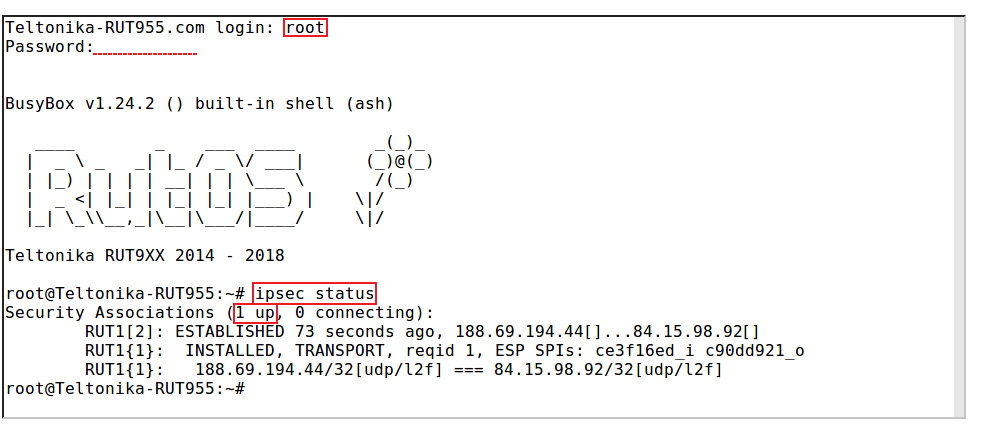
When you're done with the configuration, you should test whether it works before you move on. The simplest way to test an IPsec connection is using the ipsec status command. You can execute this command via a command line interface (CLI). A CLI is present in all RUTxxx routers' WebUIs. To access it, login to one of the routers' WebUI (doesn't matter which one) and navigate to Services → CLI. Login to CLI with the user name root and the router's admin password. Then simply the ipsec status and press the "Enter" key:
As you can see, executing ipsec status displays the number of active/inactive IPsec connections. If the connection you just configured is the only IPsec connection that you're using, you should a 1 up indication next to Security Associations.
L2TP
See also
- Other types of VPNs suported by RUTxxx devices: