Difference between revisions of "Template:Networking rutos manual routing"
| (18 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
| − | {{Template: | + | {{Template: Networking_device_manual_fw_disclosure |
| − | | fw_version ={{Template: | + | | series = {{{series}}} |
| + | | name = {{{name}}} | ||
| + | | fw_version ={{Template: Networking_device_manual_latest_fw | ||
| series = {{{series}}} | | series = {{{series}}} | ||
| name = {{{name}}} | | name = {{{name}}} | ||
}} | }} | ||
}} | }} | ||
| − | {{#ifeq: {{{series}}} | RUT9 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version {{Template: | + | {{#ifeq: {{{series}}} | RUT9 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version {{Template: Networking_device_manual_latest_fw | series = RUT9XX}} and earlier) user manual page.</i>|}} |
| − | {{#ifeq: {{{series}}} | RUT2 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version {{Template: | + | {{#ifeq: {{{series}}} | RUT2 |<br><i><b>Note</b>: <b>[[{{{name}}} Routing (legacy WebUI)|click here]]</b> for the old style WebUI (FW version {{Template: Networking_device_manual_latest_fw | series = RUT2XX}} and earlier) user manual page.</i>|}} |
==Summary== | ==Summary== | ||
| Line 192: | Line 194: | ||
</table> | </table> | ||
| − | == | + | ==Policy Based Routing== |
| − | The <b> | + | The <b>Policy Based Routing</b> section is used to configure policy-based routing infrastructures, which are usually used in more complex or specific networking scenarios. |
===Routing Tables=== | ===Routing Tables=== | ||
| Line 327: | Line 329: | ||
Each protocol is described in the sections below. | Each protocol is described in the sections below. | ||
| − | {{# | + | {{#switch: {{{series}}} | RUTX | RUTM= | #default= |
<u><b> | <u><b> | ||
| − | Note:</b> Dynamic Routing is additional software that can be installed from the <b> | + | Note:</b> Dynamic Routing is additional software that can be installed from the <b>System → [[{{{name}}} Package Manager|Package Manager]]</b> page.</u> |
}} | }} | ||
===BGP=== | ===BGP=== | ||
| Line 340: | Line 342: | ||
The <b>General Settings</b> section is used to turn BGP protocol usage on or off or to upload an external BGP configuration. Below is an example of the BGP General Settings section. | The <b>General Settings</b> section is used to turn BGP protocol usage on or off or to upload an external BGP configuration. Below is an example of the BGP General Settings section. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_general_settings_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 367: | Line 369: | ||
====BGP Instance==== | ====BGP Instance==== | ||
---- | ---- | ||
| − | |||
| − | [[File: | + | To create a new BGP instance, look to the Add New Instance section under BGP instances; type in a custom name for the BGP instance and click the 'Add' button or you can 'Edit' a general instance: |
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_instance_edit.png|border|class=tlt-border]] | ||
| + | |||
| + | You will be redirected to general BGP instance settings: | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_instance_v2.png|border|class=tlt-border]] | ||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 384: | Line 391: | ||
<tr> | <tr> | ||
<td>AS</td> | <td>AS</td> | ||
| − | <td>integer [1.. | + | <td>integer [1..4294967295]; default: <b>none</b></td> |
| − | <td> | + | <td>AS number is an identification of an autonomous system. BGP protocol uses the AS number for detecting whether the BGP connection is an internal one or external one.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 396: | Line 403: | ||
<td>ip/netmask; default: <b>none</b></td> | <td>ip/netmask; default: <b>none</b></td> | ||
<td>Adds an announcement network(s). Routes to these networks will be shared over BGP.</td> | <td>Adds an announcement network(s). Routes to these networks will be shared over BGP.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>VRF interface</td> | ||
| + | <td>VRF interface; default: <b>Default</b></td> | ||
| + | <td>To create new VRF interface, please visit: [[{{{name}}} VRF|VRF]] </td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 406: | Line 418: | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>Compares MEDs between same AS, while ignoring their age.</td> | <td>Compares MEDs between same AS, while ignoring their age.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>eBGP Requires Policy</td> | ||
| + | <td>off {{!}} on; default: <b>on</b></td> | ||
| + | <td>Enable/Disable eBGP Import or Export policy requirement. Enabled by default as per RFC 8212.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| − | ====BGP Peers==== | + | =====BGP Peers===== |
---- | ---- | ||
<b>BGP Peers</b> are routers in the same BGP Peer Group that can redistribute routes among other BGP Peers. Below is an example of the BGP Peers section, which is empty by default. | <b>BGP Peers</b> are routers in the same BGP Peer Group that can redistribute routes among other BGP Peers. Below is an example of the BGP Peers section, which is empty by default. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_v2.png|border|class=tlt-border]] |
To create a new Peer, look to the Add New Instance section under BGP Peer; type in a custom name for the BGP Peer and click the 'Add' button: | To create a new Peer, look to the Add New Instance section under BGP Peer; type in a custom name for the BGP Peer and click the 'Add' button: | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_add_button_v1.png|border|class=tlt-border]] |
| − | + | You will be redirected to general peer settings: | |
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_bgp_peer_v4.png|border|class=tlt-border]] |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 467: | Line 453: | ||
<tr> | <tr> | ||
<td>Remote AS</td> | <td>Remote AS</td> | ||
| − | <td>integer [1.. | + | <td>integer [1..4294967295]; default: <b>none</b></td> |
<td>Remote autonomous system number of this remote BGP Neighbor.</td> | <td>Remote autonomous system number of this remote BGP Neighbor.</td> | ||
</tr> | </tr> | ||
| Line 473: | Line 459: | ||
<td>Remote address</td> | <td>Remote address</td> | ||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
| − | <td>IPv4 address of this remote BGP Neighbor.</td> | + | <td>IPv4 address of this remote BGP Neighbor. This option is required.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 484: | Line 470: | ||
<td>integer; default: <b>none</b></td> | <td>integer; default: <b>none</b></td> | ||
<td>Time to Live value for packets associated with this remote BGP Neighbor.</td> | <td>Time to Live value for packets associated with this remote BGP Neighbor.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Weight</td> | ||
| + | <td>integer [0..65535]; default: <b>none</b></td> | ||
| + | <td>Specifies a default weight value for the neighbor’s routes. Higher weight is preferred.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 517: | Line 508: | ||
</table> | </table> | ||
| − | ====BGP Peer Groups==== | + | =====BGP Peer Groups===== |
---- | ---- | ||
A <b>BGP Peer Group</b> is a collection of routers that use the BGP protocol to dynamically redistribute routes among peers (other routers). The figure below is an example of the BGP Peer Groups section, which is empty by default. | A <b>BGP Peer Group</b> is a collection of routers that use the BGP protocol to dynamically redistribute routes among peers (other routers). The figure below is an example of the BGP Peer Groups section, which is empty by default. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups_v2.png|border|class=tlt-border]] |
To create a new Peer Group, look to the Add New Instance section under BGP Peer Groups; type in a custom name for the BGP Peer Group and click the 'Add' button: | To create a new Peer Group, look to the Add New Instance section under BGP Peer Groups; type in a custom name for the BGP Peer Group and click the 'Add' button: | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peers_groups_add_button_v1.png|border|class=tlt-border]] |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | You will be redirected to general peer groups settings: | |
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_bgp_peer_groups_bgp_peer_group_v2.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 566: | Line 536: | ||
<td>Remote AS</td> | <td>Remote AS</td> | ||
<td>integer [1..65535]; default: <b>none</b></td> | <td>integer [1..65535]; default: <b>none</b></td> | ||
| − | <td> | + | <td>Neighbour's remote AS.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Neighbor address</td> | <td>Neighbor address</td> | ||
<td>ip4; default: <b>none</b></td> | <td>ip4; default: <b>none</b></td> | ||
| − | <td>IPv4 address | + | <td>Neighbour's remote IPv4 address.</td> |
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Listen Range</td> | ||
| + | <td>ip4 with mask; default: <b>none</b></td> | ||
| + | <td>Accept connections from any peers in the specified prefix.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Advertisement interval</td> | <td>Advertisement interval</td> | ||
<td>integer; default: <b>none</b></td> | <td>integer; default: <b>none</b></td> | ||
| − | <td> | + | <td>Delay between updates for a neighbor session (in seconds).</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 594: | Line 569: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| − | <td | + | <td>Apply also to ibgp-learned routes</td> |
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>When acting as a route reflector, applies to ibgp-learned routes as well. This field becomes visible when 'Disable next hop calculation' is turned on.</td> | <td>When acting as a route reflector, applies to ibgp-learned routes as well. This field becomes visible when 'Disable next hop calculation' is turned on.</td> | ||
| Line 607: | Line 582: | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>When turned on, Disable connected check enables a directly connected eBGP Neighbor to peer using a loopback address without adjusting the default TTL of 1.</td> | <td>When turned on, Disable connected check enables a directly connected eBGP Neighbor to peer using a loopback address without adjusting the default TTL of 1.</td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | |||
| + | =====Route Map Filters===== | ||
| + | ---- | ||
| + | The <b>Route Map Filters</b> section is used to configure special filters that changes direction for BGP Peers. Below is an example of the Route Map Filters section which is empty by default. You can add a new filter by clicking the 'Add' button | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_route_maps_filters_add_button_v1.png|border|class=tlt-border]] | ||
| + | |||
| + | An Route Map Filters configuration for BGP should look similar to this: | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_route_maps_filters_configuration_v1.png|border|class=tlt-border]] | ||
| + | |||
| + | <table class="nd-mantable"> | ||
| + | <tr> | ||
| + | <th>Field</th> | ||
| + | <th>Value</th> | ||
| + | <th>Description</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Peer</td> | ||
| + | <td>bgp peer; default: <b>-</b></td> | ||
| + | <td>Applies the filter rule for the specified peer.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Route map</td> | ||
| + | <td>route map; default: <b>-</b></td> | ||
| + | <td>Route map filter to apply.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Direction</td> | ||
| + | <td>Inbound {{!}} Outbound; default: <b>Inbound</b></td> | ||
| + | <td>If direction is Inbound, the access list is applied to input routes. If direction is Outbound the access list is applied to advertised routes.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Enable</td> | ||
| + | <td>off {{!}} on; default: <b>off</b></td> | ||
| + | <td>Turns an Route Map filter on or off.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 614: | Line 627: | ||
The <b>Access List Filters</b> section is used to configure special filters that restrict or allow access to specified networks for BGP Peers. Below is an example of the Access List Filters section which is empty by default. You can add a new filter by clicking the 'Add' button | The <b>Access List Filters</b> section is used to configure special filters that restrict or allow access to specified networks for BGP Peers. Below is an example of the Access List Filters section which is empty by default. You can add a new filter by clicking the 'Add' button | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_access_list_filters_add_button_v1.png|border|class=tlt-border]] |
An Access List Filter configuration for BGP should look similar to this: | An Access List Filter configuration for BGP should look similar to this: | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_access_list_filters_configuration_v2.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 628: | Line 641: | ||
<tr> | <tr> | ||
<td>Peer</td> | <td>Peer</td> | ||
| − | <td>bgp peer; default: <b> | + | <td>bgp peer; default: <b>-</b></td> |
<td>Applies the filter rule for the specified peer.</td> | <td>Applies the filter rule for the specified peer.</td> | ||
</tr> | </tr> | ||
| Line 637: | Line 650: | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| − | <td> | + | <td>Filter network</td> |
| − | <td> | + | <td>Any {{!}} custom; default: <b>Any</b></td> |
| − | <td> | + | <td>Applies filter rule for this source network.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
<td>Direction</td> | <td>Direction</td> | ||
<td>Inbound {{!}} Outbound; default: <b>Inbound</b></td> | <td>Inbound {{!}} Outbound; default: <b>Inbound</b></td> | ||
| − | <td> | + | <td>If direction is Inbound, the access list is applied to input routes. If direction is Outbound the access list is applied to advertised routes.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 650: | Line 663: | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>Turns an Access filter on or off.</td> | <td>Turns an Access filter on or off.</td> | ||
| + | </tr> | ||
| + | </table> | ||
| + | |||
| + | ====Route Maps==== | ||
| + | ---- | ||
| + | A <b>Route Maps</b> allow you to configure a filtering criteria by defining a set of rules or match statements with a permit or deny condition. It includes a series of match statements to determine if a route matches the criteria defined in the statement and then apply the permit or deny rule accordingly. | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_route_maps_v1.png|border|class=tlt-border]] | ||
| + | |||
| + | To create a new Route Maps, look to the Add New Instance section under Route Maps; type in a custom name for the Route Map and click the 'Add' button: | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_route_maps_add_button_v1.png|border|class=tlt-border]] | ||
| + | |||
| + | You will be redirected to general route maps settings: | ||
| + | |||
| + | [[File:Networking_rutos_manual_routing_dynamic_routes_bgp_route_maps_edit_v1.png|border|class=tlt-border]] | ||
| + | |||
| + | <table class="nd-mantable"> | ||
| + | <tr> | ||
| + | <th>Field</th> | ||
| + | <th>Value</th> | ||
| + | <th>Description</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Enable</td> | ||
| + | <td>off {{!}} on; default: <b>off</b></td> | ||
| + | <td>Turns the Route Maps configuration on or off.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Action</td> | ||
| + | <td>Permit {{!}} Deny; default: <b>Permit</b></td> | ||
| + | <td>IPv4 address of this remote BGP Neighbor.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Local preference</td> | ||
| + | <td>integer [0..4294967295]; default: <b>none</b></td> | ||
| + | <td>Used to determine best route towards a certain destination.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Metric</td> | ||
| + | <td>ip4 with mask; default: <b>none</b></td> | ||
| + | <td>Sets a metric value for determining the preferred path into an AS.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 661: | Line 716: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the RIP protocol. Below is an example of the RIP General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the RIP protocol. Below is an example of the RIP General Settings section. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_general_settings_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 708: | Line 763: | ||
RIP Interface configuration should look similar to this: | RIP Interface configuration should look similar to this: | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_rip_interfaces_configuration_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 715: | Line 770: | ||
<th>Value</th> | <th>Value</th> | ||
<th>Description</th> | <th>Description</th> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 730: | Line 780: | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
<td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and <b>ripd</b> does not send either multicast or unicast RIP packets.</td> | <td>Sets the specified interface to passive mode. On passive mode interface, all receiving packets are processed as normal and <b>ripd</b> does not send either multicast or unicast RIP packets.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Enable</td> | ||
| + | <td>off {{!}} on; default: <b>off</b></td> | ||
| + | <td>Turns a RIP Interface on or off.</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>Delete</td> | ||
| + | <td>- (interactive button)</td> | ||
| + | <td>Deletes RIP inerfaces instance.</td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
| Line 739: | Line 799: | ||
[[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters.png|border|class=tlt-border]] | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters.png|border|class=tlt-border]] | ||
| − | To add a new filter, look to the Add New | + | To add a new filter, look to the Add New Instance section; enter a custom name and select RIP interface then click the 'Add' button: |
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters_add_button_v1.png|border|class=tlt-border]] |
An Access List Filter configuration for RIP should look similar to this: | An Access List Filter configuration for RIP should look similar to this: | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_rip_access_list_filters_configuration_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 793: | Line 853: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the OSPF protocol. Below is an example of the OSPF General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the OSPF protocol. Below is an example of the OSPF General Settings section. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_ospf_protocol_general_settings_v3.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 943: | Line 1,003: | ||
<td>Enable</td> | <td>Enable</td> | ||
<td>off {{!}} on; default: <b>off</b></td> | <td>off {{!}} on; default: <b>off</b></td> | ||
| − | <td>Turns | + | <td>Turns this OSPF neighbor configuration on or off.</td> |
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 974: | Line 1,034: | ||
The newly added new Area will appear in the OSPF Area list. | The newly added new Area will appear in the OSPF Area list. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_ospf_protocol_ospf_area_configuration_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 991: | Line 1,051: | ||
<td>32-bit integer; default: <b>none</b></td> | <td>32-bit integer; default: <b>none</b></td> | ||
<td>OSPF Area ID. OSPF Networks that are meant to communicate with each other should belong to the same Area (have the Area ID).</td> | <td>OSPF Area ID. OSPF Networks that are meant to communicate with each other should belong to the same Area (have the Area ID).</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td>STUB</td> | ||
| + | <td>off {{!}} on; default: <b>off</b></td> | ||
| + | <td>A stub area is an area in which advertisements of external routes are not allowed, reducing the size of the database.</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 1,051: | Line 1,116: | ||
The <b>General Settings</b> section is used to configure some of the main operating parameters of the EIGRP protocol. Below is an example of the EIGRP General Settings section. | The <b>General Settings</b> section is used to configure some of the main operating parameters of the EIGRP protocol. Below is an example of the EIGRP General Settings section. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_eigrp_general_settings_v1.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
| Line 1,104: | Line 1,169: | ||
The <b>General Settings</b> section is used to turn NHRP protocol usage on or off. Below is an example of the NHRP General Settings section. | The <b>General Settings</b> section is used to turn NHRP protocol usage on or off. Below is an example of the NHRP General Settings section. | ||
| − | [[File: | + | [[File:Networking_rutos_manual_routing_dynamic_routes_nhrp_general_settings_v2.png|border|class=tlt-border]] |
<table class="nd-mantable"> | <table class="nd-mantable"> | ||
Latest revision as of 10:40, 17 April 2024
The information in this page is updated in accordance with firmware version .
Summary
The Routing page is used to set up static routes, routing tables and rules.
This manual page provides an overview of the Routing windows in {{{name}}} devices.
If you're having trouble finding this page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Advanced" button, located at the top of the WebUI.
Static Routes
Routes ensure that network traffic finds its path to a specified host or network, both in local and remote network scenarios. Static routes are simply fixed routing entries in the routing table(s).
This section provides the possibility to configure custom static routes.
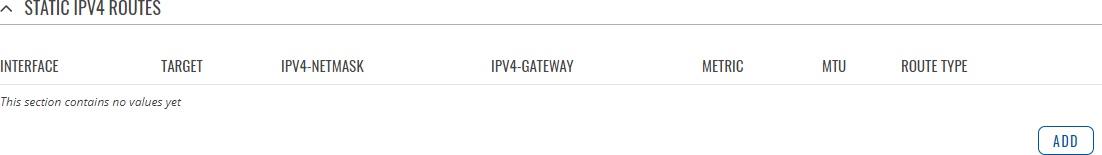
Static IPv4 Routes
The Static IPv4 Routes section displays a list of user defined static IPv4 routes and provides the possibility to add and configure new ones. The list is empty by default.
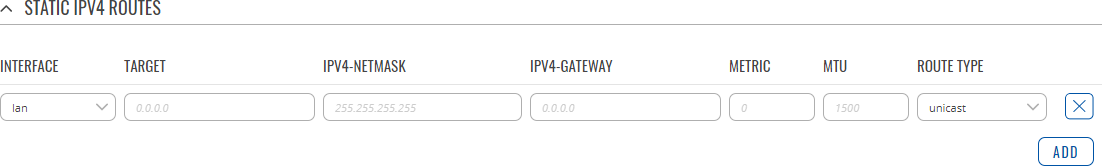
To add a new route and begin editing, simply click the 'Add' button. Refer to the table below for information on static route configuration fields.
| Field | Value | Description |
|---|---|---|
| Interface | network interface; default: lan | Network interface of the target network. |
| Target* | ip4; default: none | Destination network address. |
| IPv4-Netmask* | netmask; default: none | A netmask is used to divide an IP address into sub-networks (subnets). Combined together, the 'Netmask' and 'Target' values define the exact destination network or IP address to which this route applies. |
| IPv4-Gateway | ip4; default: none | A gateway can be any machine in a network that is capable of serving as an access point to another network. Traffic that matches this route will be directed over the IP address specified in this field. |
| Metric | integer [0..255]; default: none | The metric value acts as a measurement of priority. If a packet about to be routed matches two or more rules, the one with the lower metric is applied. |
| MTU | integer [64..9000]; default: 1500 | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| Route Type | unicast | local | broadcast | multicast | unreachable | prohibit | backhole | anycast | -- custom -- ; default: unicast | Selects route type. Each type specifies a different behavior for the route:
|
*Additional notes on 'Target' & 'Netmask' fields:
You can define a rule that applies to a single IP like this:
- Target: some IP
- Netmask: 255.255.255.255
Furthermore, you can create target/netmask combinations that apply to a range of IPs. Refer to the table below for examples.
| Target | Netmask | Network range |
|---|---|---|
| 192.168.2.0 | 255.255.255.240 | 192.168.2.0 - 192.168.2.15 |
| 192.168.2.240 | 255.255.255.240 | 192.168.2.240 - 192.168.2.255 |
| 192.168.2.161 | 255.255.255.0 | 192.168.2.0 - 192.168.55.255 |
| 192.168.0.0 | 255.255.0.0 | 192.168.0.0 - 192.168.255.255 |
| 192.168.2.161 | 255.255.255.255 | 192.168.2.161 |
Static IPv6 Routes
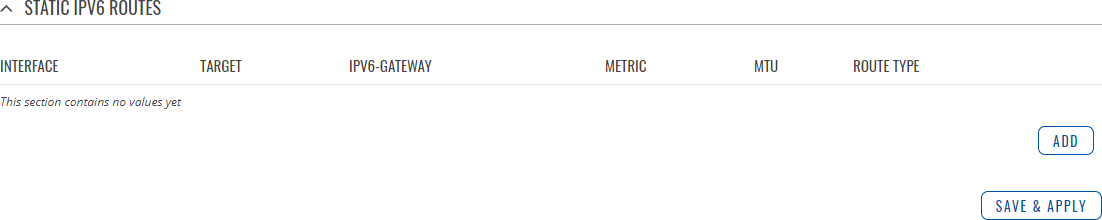
The Static IPv6 Routes section displays a list of user defined static IPv6 routes and provides the possibility to add and configure new ones. The list is empty by default.
To add a new route and begin editing, simply click the 'Add' button. Refer to the table below for information on static route configuration fields.
| Field | Value | Description |
|---|---|---|
| Interface | network interface; default: lan | Network interface of the target network. |
| Target | ip6; default: none | Destination network address. |
| IPv6-Gateway | ip6; default: none | A gateway can be any machine in a network that is capable of serving as an access point to another network. Traffic that matches this route will be directed over the IP address specified in this field. |
| Metric | integer [0..255]; default: none | The metric value acts as a measurement of priority. If a packet about to be routed matches two or more rules, the one with the lower metric is applied. |
| MTU | integer [64..9000]; default: 1500 | Sets the maximum transmission unit (MTU) size. It is the largest size of a protocol data unit (PDU) that can be transmitted in a single network layer transaction. |
| Route Type | unicast | local | broadcast | multicast | unreachable | prohibit | backhole | anycast | -- custom -- ; default: unicast | Selects route type. Each type specifies a different behavior for the route:
|
Policy Based Routing
The Policy Based Routing section is used to configure policy-based routing infrastructures, which are usually used in more complex or specific networking scenarios.
Routing Tables
Routing Tables store network routes. Tables are checked before every routing decision until a matching route is found. Having multiple tables allows the user to set up a policy routing infrastructure. Policy-based routing is a technique where routing decisions are based on policies (rule) set by the user.
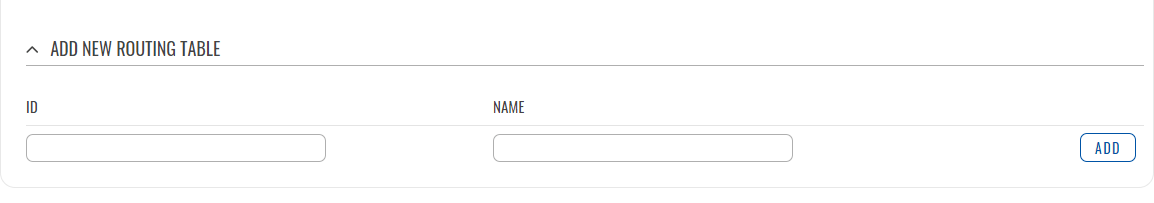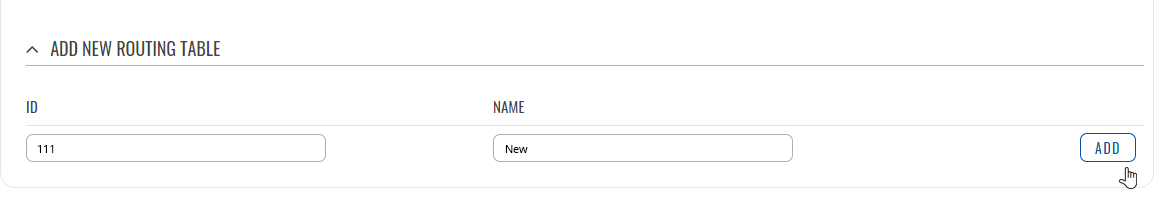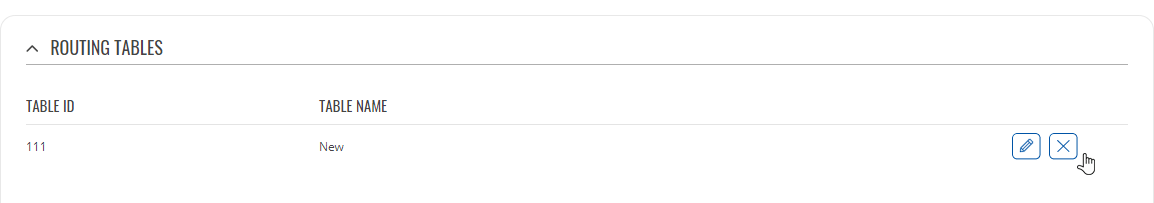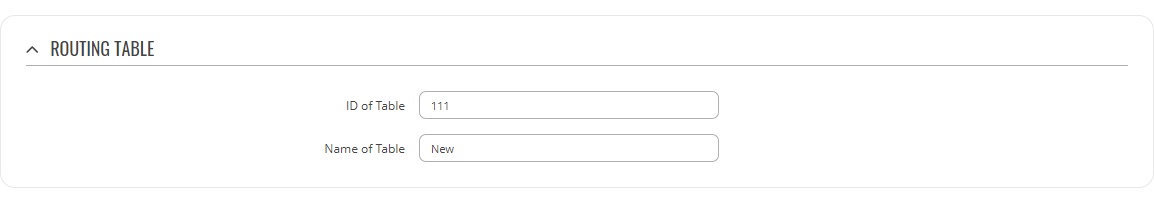
The 'Routing Tables' section displays user created routing tables. By default, the list is empty.
To create a new table, look to the 'Add New Routing Table' section below. Enter an ID for the new table in the range of [1..252], enter a custom name and click the 'Add' button. The new table should appear in the 'Routing Tables' list. Click the 'Edit' button next to it to begin editing.
Refer to the table below for information on configuration fields for routing tables.
| Field | Value | Description |
|---|---|---|
| Name of Table | string; default: none | A custom name for the table. A table can be invoked by the both its ID or name. |
| ID of Table | integer [1..252]; default: none | Unique numerical identifier for the table. A table can be invoked by the both its ID or name. |
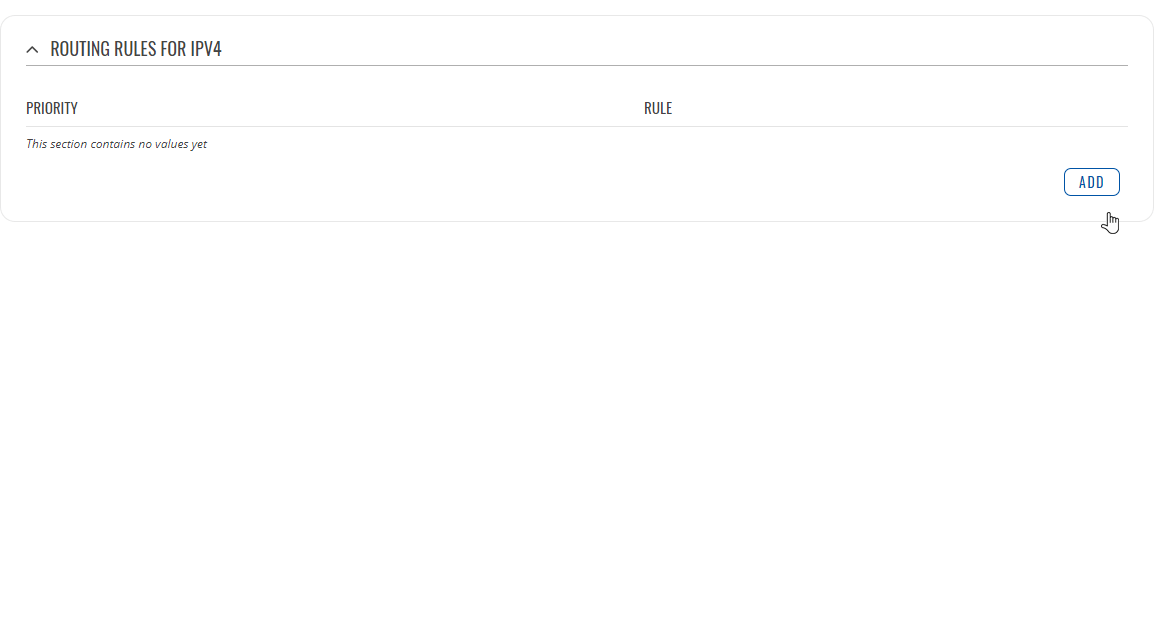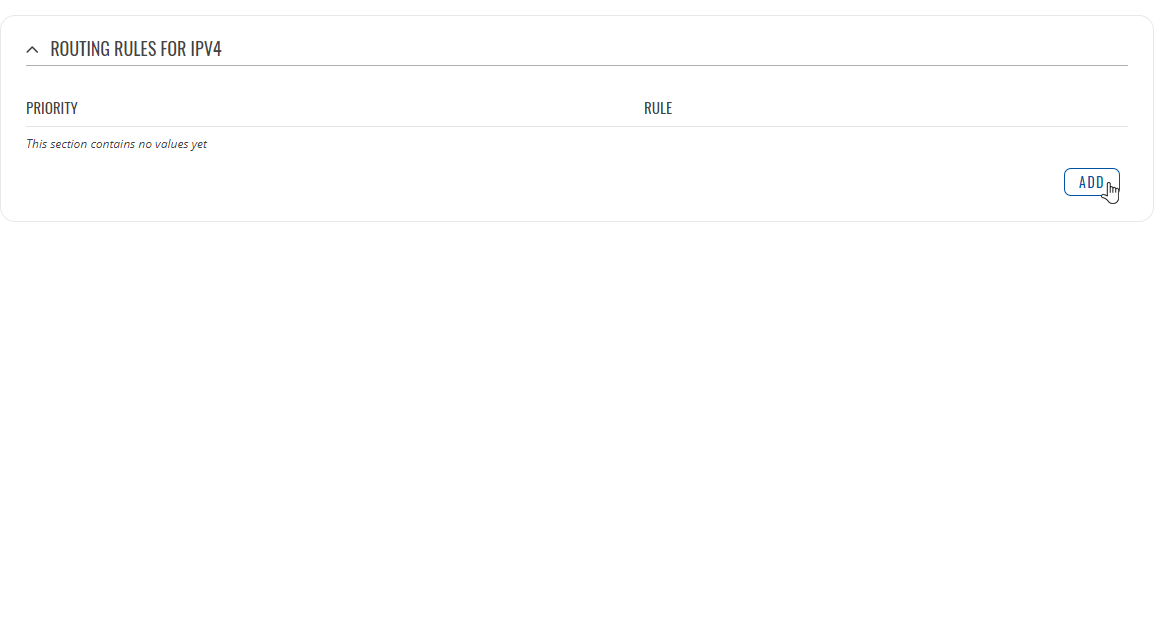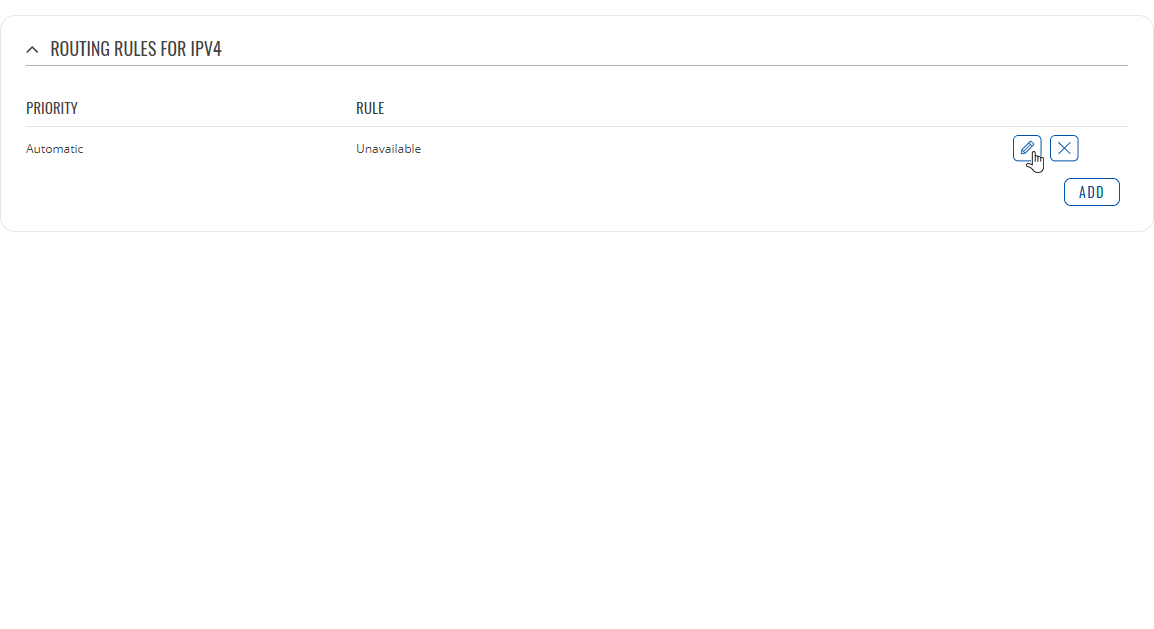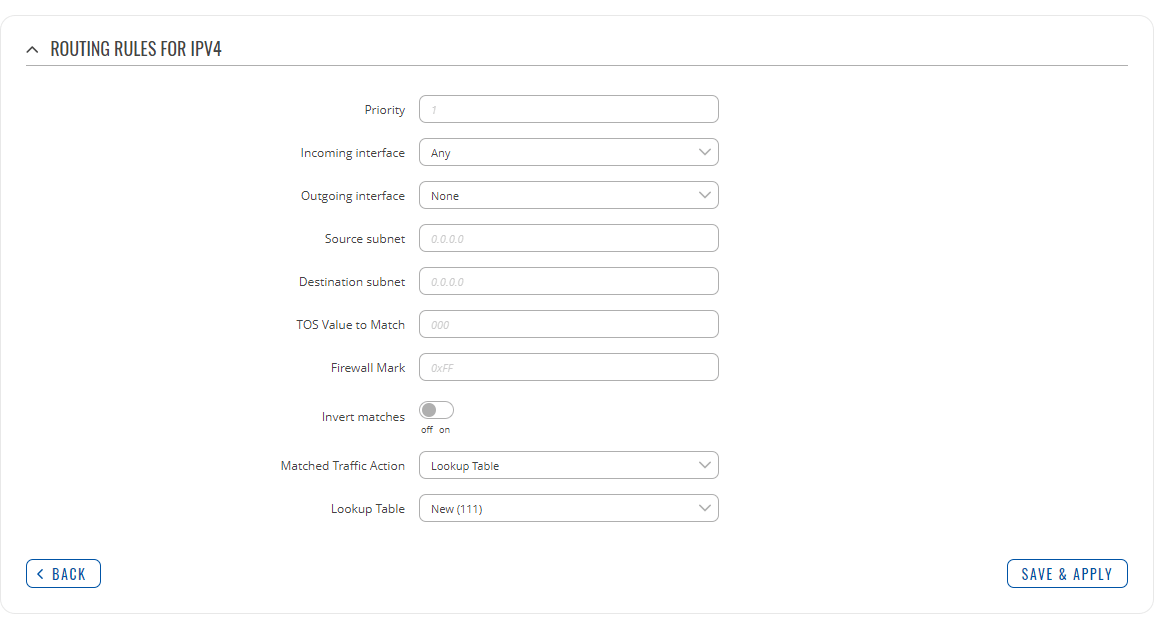
Routing Rules For IPv4
Routing Rules provide a way to route certain packets with exceptions, i.e., in accordance to a rule. 'Routing Rules For IPv4' displays user defined routing rules. It is empty by default. To create a new rule, click the 'Add' button and begin editing by clicking the 'Edit' button located to the right of the newly created rule.
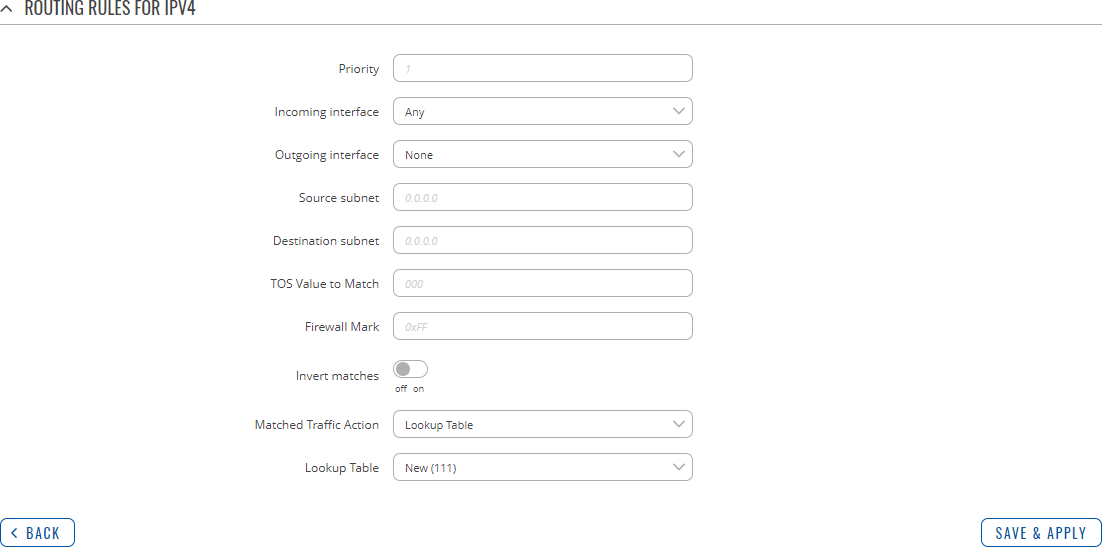
Refer to table below for information on each configuration field.
| Field | Value | Description |
|---|---|---|
| Priority | integer [0..65535]; default: none | Controls the order of IP rules. Rules with a lower priority value will be checked first. |
| Incoming interface | network interface | Any; default: Any | Logical interface name for incoming traffic. Select 'Any' to make the rule apply to all network interfaces. |
| Outgoing interface | network interface | None; default: None | Logical interface name for incoming traffic. Select 'None' to ignore outgoing interface. |
| Source subnet | netmask; default: none | Source subnet to match the rule. |
| Destination subnet | netmask; default: none | Destination subnet to match the rule. |
| TOS Value to Match | integer [0..255]; default: none | The type of service (ToS) value to match in IP headers. |
| Firewall Mark | integer [0..255] | hex [0x00..0xFF]; default: none | Specifies the fwmark and optionally its mask to match. For example, 0xFF to match mark 255 or 0x0/0x1 to match any even mark value. |
| Invert matches | off | on; default: off | If enabled, the meaning of the match options (Firewall Mark, TOS Value, Source and Destination subnets) is inverted. |
| Matched Traffic Action | Lookup Table | Jump to rule | Routing Action; default: Lookup Table | When network traffic matches this rule, the device will take an action specified in this field:
|
| Lookup Table | routing table; default: none | Specifies a table for routing traffic that matches this rule. This field is visible only when 'Matched Traffic Action' is set to Lookup Table. |
| Jump to rule | rule priority number; default: none | Specifies a another rule to follow for traffic that matches this rule. This field is visible only when 'Matched Traffic Action' is set to Jump to rule. |
| Routing Action | Prohibit | Unreachable | Blackhole | Throw; default: Prohibit | When traffic matches this rule, the action specified in this field will be executed. This field is visible only when 'Matched Traffic Action' is set to Routing Action. |
[[Category:{{{name}}} Network section]]