Template:Networking rut configuration example l2tp over ipsec work use case default gateway
|
|
Configuration overview and prerequisites
Prerequisites:
- One RUTxxx routers of any type (excluding RUT850)
- A Public Static or Public Dynamic IP addresses
- At least one end device with Windows 10
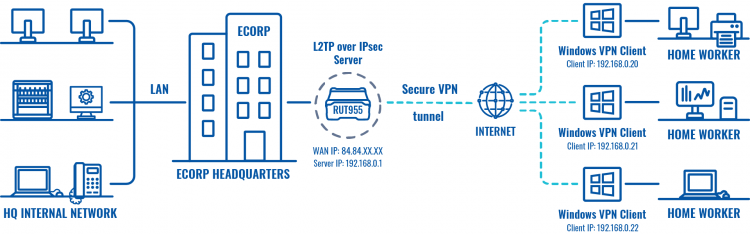
The topology above depicts the L2TP/IPsec scheme. - The router with the Public IP address (RUT955) acts as the L2TP/IPsec server and the Windows 10 device acts as client. L2TP connects the networks of RUT955 and Windows 10 client, IPsec provides the encryption for the L2TP tunnel.
When the scheme is realized, home workers will be able to reach corporation’s internal network with all internal systems, allowing working from home to be possible. All of the home worker's LAN and WAN traffic is going to go through that tunnel.
Configuring HQ corporation router
L2TP
|
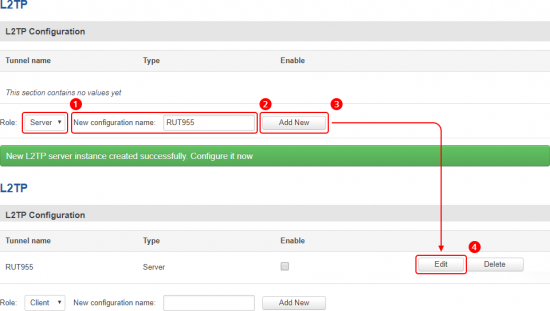
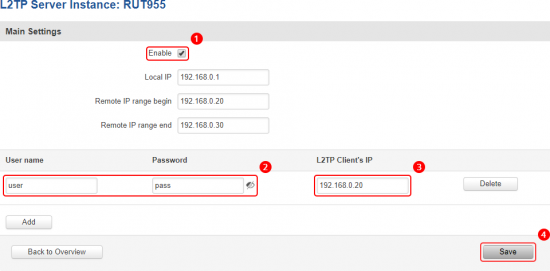
Login to the router's WebUI and navigate to the Services → VPN → L2TP page and do the following:
|
|
IPsec
|
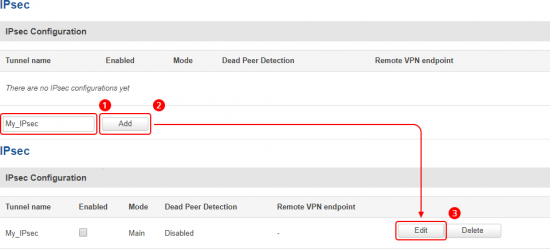
Go to the Services → VPN → IPsec page and do the following:
|
|
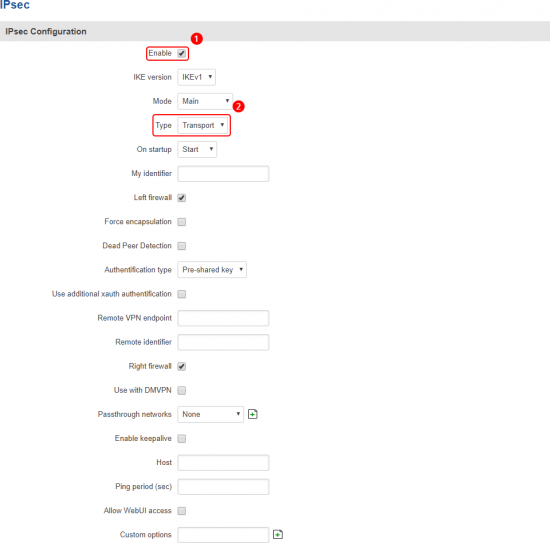
In the IPsec Configuration page, do the following (and leave the rest as defaults, unless your specific configuration requires otherwise):
|
|
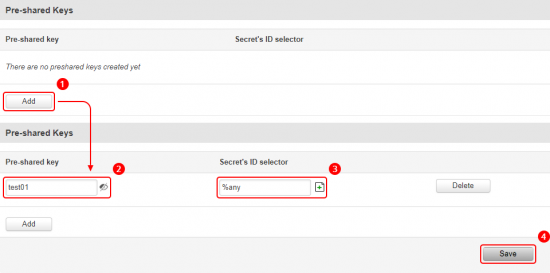
After saving the changes, you will be redirected back to the main IPsec page. While there, locate the Pre-shared Keys section and do the following:
|
Firewall
|
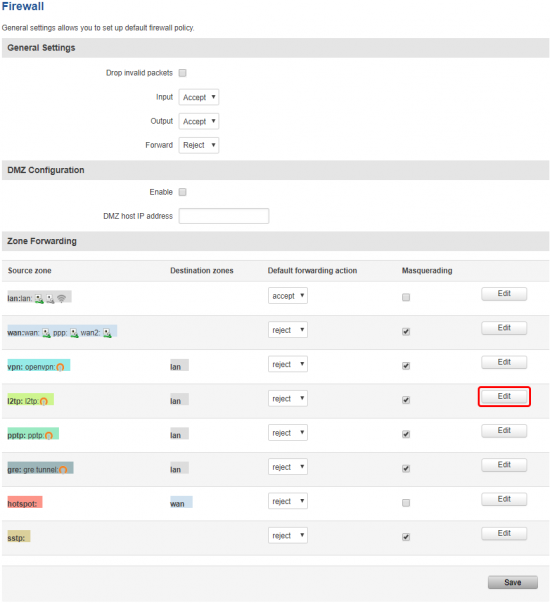
Go to the Network → Firewall → General Settings and press edit next to the L2TP zone forwarding rule: |
|
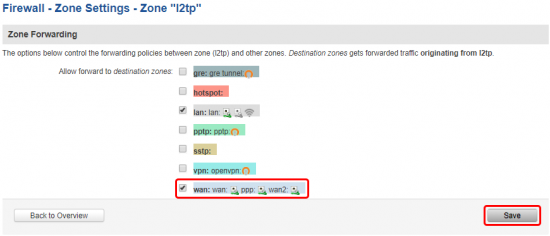
Allow L2TP forward to WAN and click the Save button: |
Home worker’s computer
|
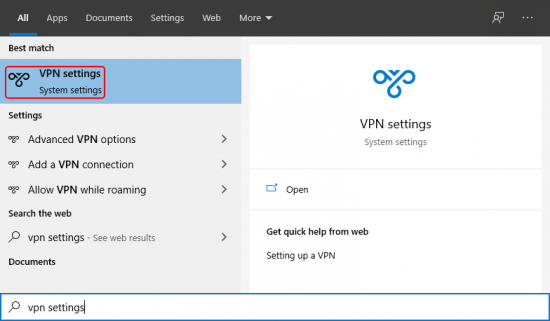
Type VPN settings in the Windows search bar: |
|
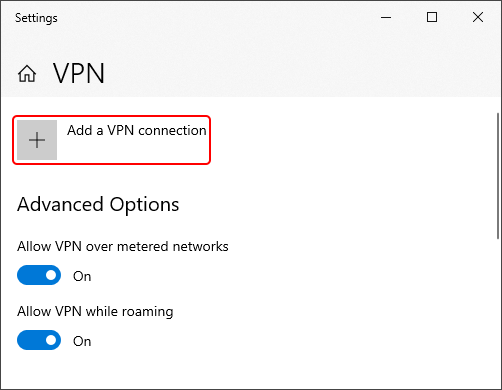
Click the Add a VPN connection button: |
|
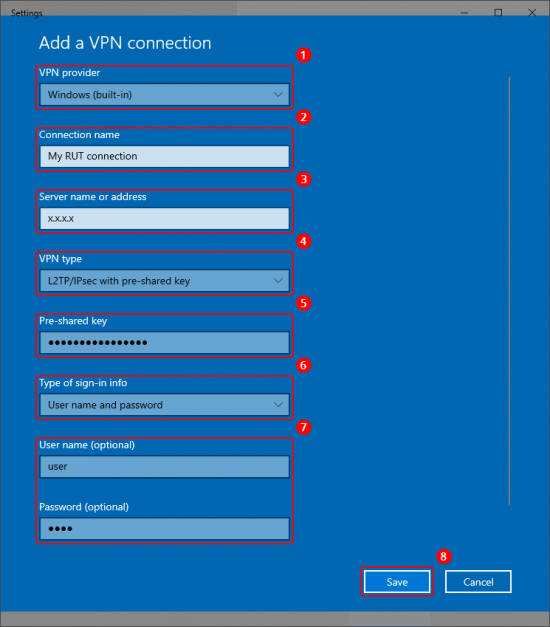
Configure the following parameters:
|
|
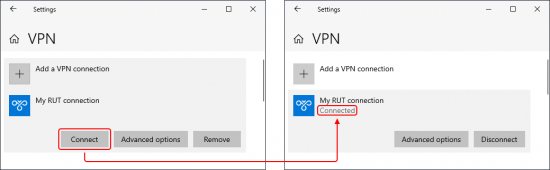
After you are redirected back to the VPN settings page, locate your new connection and click the Connect button. If the connection was successful, you should see the word "connected" appear under the connection name: |
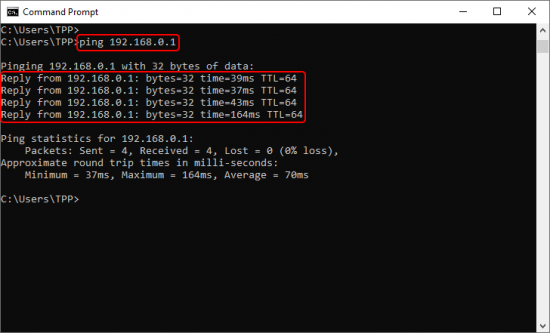
Results
|
Home worker should now be able to access HQ network resources. To verify the connection you can ping some internal HQ server and if you get a reply, you have successfully connected to HQ‘s internal network. |