UCI command usage
Unified Configuration Interface (UCI) is a small utility written in C (a shell script-wrapper is available as well) and is intended to centralize the whole configuration of a device running on OpenWrt.
Summary
UCI commands provide the user with the maximum degree of control since they can be issued via many different forms of router monitoring and administration (SSH, CLI, SMS, JSON-RPC) and can be used to set or get any router parameter. This chapter is a guide on how to use UCI commands with RUT devices.
Obtaining parameters
This section will overview uci get and uci show commands used to obtain router parameters as well as provide some basic knowledge on configuration hierarchy needed to successfully use most uci commands.
Configuration hierarchy
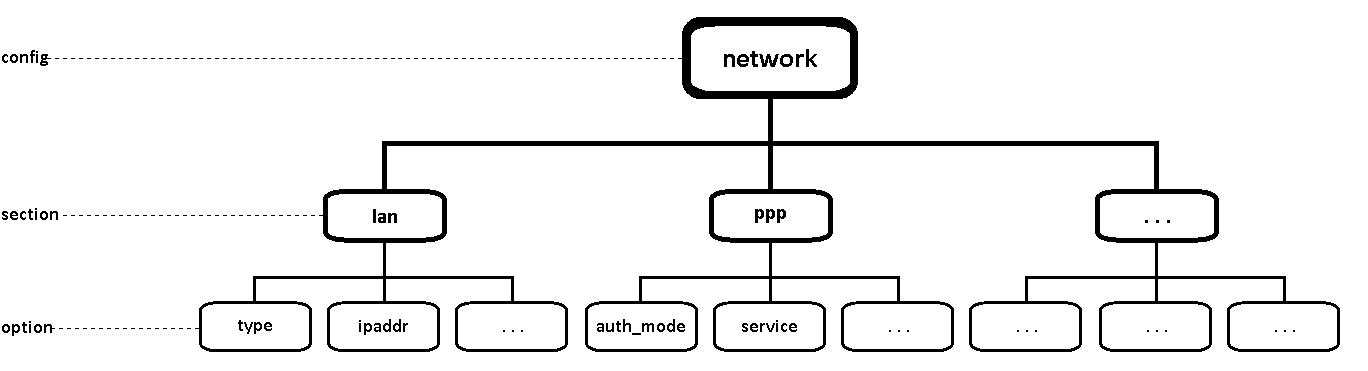
UCI commands can be used to set and obtain parameters, but to do so, one has to first know the names of the config file, its section and the option that they are trying to interact with. Different configurations for different router functions and services are stored in config files. These config files have sections and section usually store multiple options
The elements in the UCI model are:
- config: main configuration groups like network, system, firewall. Each configuration group has it's own file in /etc/config
- sections: a config is divided into sections. A section can either be named or unnamed
- types: a section can have a type. E.g, in the network config we typically have sections of the type "interface"
- options: each section has options that hold configuration values
- values: value of an option
Sections
Sections deserve some extra explanation in regard to naming. A section can be named or unnamed. Unnamed sections will get an autogenerated ID/CFGID (like "cfg023579") and be presented with an anonymous-name (like "@wifi-iface[0]")
Example of anonymous-name (cmd: uci show wireless):
... wireless.@wifi-iface[0]=wifi-iface wireless.@wifi-iface[0].device=radio0 wireless.@wifi-iface[0].network=lan wireless.@wifi-iface[0].mode=ap ...
Example of autogenerated ID/CFGID (cmd: uci show wireless.@wifi-iface[0]):
... wireless.cfg023579=wifi-iface wireless.cfg023579.device=radio0 wireless.cfg023579.network=lan wireless.cfg023579.mode=ap ...
UCI get
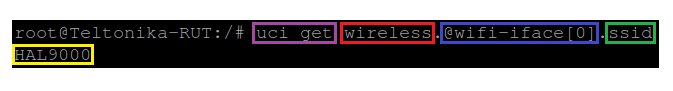
The uci get command returns values for specific options. When using uci get, you have provide the correct path to the option that you are looking for. For example, in order to obtain the Wi-Fi Access Point's SSID you would have to use a command that looks like this:
# uci get wireless.@wifi-iface[0].ssid
Response:
The command above returns the Wi-Fi Access Point's SSID. As you can see the uci get command is used. What follows after the command is the path to the value that we're looking for (SSID, in this case). The SSID value can be found in the wireless config, the @wifi-iface[0] section, stored in an option called ssid. So the basic syntax for a uci get command is this:
# uci get <config>.<section>[.<option>]
UCI show
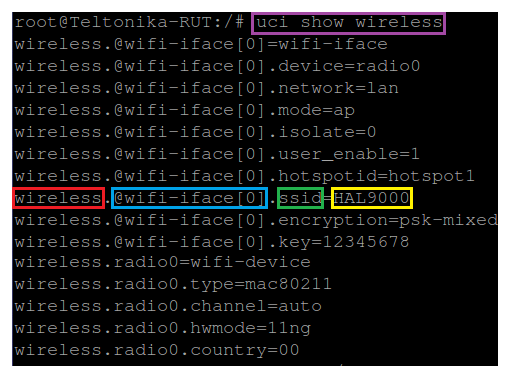
If you don't know what the exact option is called and in which section of what config file it is stored, you can use the uci show command. uci show can also be used to obtain values of specific options, but it is more commonly used to display the contents of entire sections or configs. Lets modify the example above by saying that want to find out the SSID value but don't know the exact section or option under which the value is stored. In this case we'll the uci show command to view the contents of the entire wireless config:
# uci show wireless
Response:
As you can see, this time the response shows the entire wireless config and instead of just showing values (like in the case of uci get) you can see the config name, section name and option name before each one.
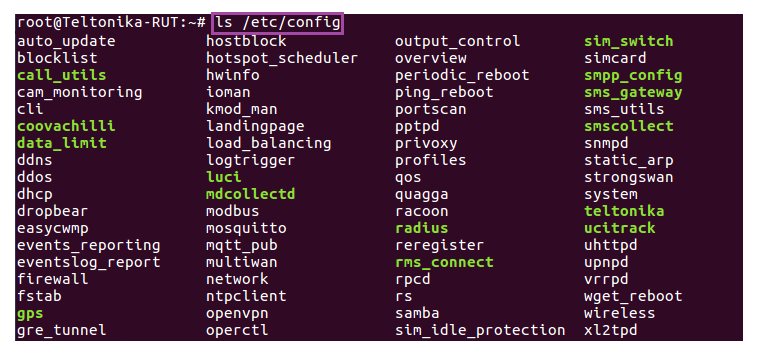
Most config file names are simple. Wireless config is called wireless, OpenVPN config is called openvpn, etc. But even so one doesn't necessarily have to know what a config file is called, especially before interacting with it. To see the names of all config files you can use the ls command. Since RUT configs ar stored in /etc/config, the full commands should look like this:
# ls /etc/config
The ls command is used to view the contents of a directory. Here is an example of the /etc/config directory of a RUT955 router:
Setting parameters
UCI can also be used to set parameters, add lists of parameters and even add entire sections to config files.
UCI set
The uci set command is used to set the values of specific options. It can set only one option at a time. For example, this time lets try changing the Wi-Fi Access Point's SSID to wifi_set_by_uci:
# uci set wireless.@wifi-iface[0].ssid=wifi_set_by_uci
As you may have noticed, the command is very similar to uci get, except it has an equals to ('=') sign added at the end and after the sign is the value that we want to assign to the option.
The next step is to commit the changes by using the uci commit command and to restart all the services relevant to our configuration by using the luci-reload command:
# uci commit wireless # luci-reload
After this, your changes will be applied and in use. Notice that when using uci commit you can specify the config file for which you want to commit changes (you can even specify the exact section and option). This is useful when making changes to multiple options in case you make any mistakes, because before committing any changes you can easily undo them with the uci revert command. The command by itself will undo all the changes made by uci up until the last commit. It can also be used on specific config files, sections and options in order to undo specific changes.
UCI add_list
Some variables hold more than one value unlike options. These variables are called lists. For example, if you use MAC filter on your Wi-Fi Acsess point, the MAC addresses are saved not as options but as a list.
Example of maclist (cmd: uci show wireless):
... wireless.@wifi-iface[0].macfilter=deny wireless.@wifi-iface[0].maclist=15:15:12:64:66:14 15:15:12:64:66:15 15:15:12:64:66:16 ...
As an add_list usage example, lets add these MAC addresses to the list: 11:11:11:11:11:11, 22:22:22:22:22:22, 33:33:33:33:33:33
# uci add_list wireless.@wifi-iface[0].maclist=11:11:11:11:11:11 # uci add_list wireless.@wifi-iface[0].maclist=22:22:22:22:22:22 # uci add_list wireless.@wifi-iface[0].maclist=33:33:33:33:33:33 # uci commit wireless # luci-reload
Notice that you have to use a separate command for adding each value and as with uci set you have to use uci commit and luci-reload in order for the changes to take effect.
Extensive example
With all that we have learned lets try a more complicated example: lets you want to create an OpenVPN server. The server will be called MyServer, will use a TUN type interface and TLS authentication. In order to create this server we will first have to create a section for the server in the openvpn config:
# uci uci add openvpn server_MyServer # uci set openvpn.server_MyServer=openvpn
The first line creates a section called server_MyServer, the second line specifies the section type, in this case - openvpn. Now lets add the rest of the configurations:
# uci set openvpn.server_MyServer.persist_key=1 # uci set openvpn.server_MyServer.port=1194 # uci set openvpn.server_MyServer.keepalive=10 120 # uci set openvpn.server_MyServer.persist_tun=1 # uci set openvpn.server_MyServer.status=/tmp/openvpn-status_server_MyServer.log # uci set openvpn.server_MyServer.verb=5 # uci set openvpn.server_MyServer.proto=udp # uci set openvpn.server_MyServer.dev=tun_s_MyServer # uci set openvpn.server_MyServer.enable=1 # uci set openvpn.server_MyServer.comp_lzo=yes # uci set openvpn.server_MyServer.cipher=BF-CBC # uci set openvpn.server_MyServer._auth=tls # uci set openvpn.server_MyServer._tls_cipher=all # uci set openvpn.server_MyServer.server=10.0.0.0 255.255.255.0 # uci set openvpn.server_MyServer.ca=/lib/uci/upload/cbid.openvpn.server_MyServer.ca # uci set openvpn.server_MyServer.cert=/lib/uci/upload/cbid.openvpn.server_MyServer.cert # uci set openvpn.server_MyServer.key=/lib/uci/upload/cbid.openvpn.server_MyServer.key # uci set openvpn.server_MyServer.dh=/lib/uci/upload/cbid.openvpn.server_MyServer.dh # uci set openvpn.server_MyServer.client_config_dir=/etc/openvpn/ccd # uci add_list openvpn.server_MyServer.push="route 192.168.1.0 255.255.255.0" # uci add_list openvpn.server_MyServer.push="route 192.168.56.0 255.255.255.0'
And don't forget to uci commit and luci-reload:
# uci commit openvpn # luci-reload
A few notes about the configuration:
- The options that go into an OpenVPN server are standard OpenWRT OpenVPN server options. If you do not posses all the required information needed to create an OpenVPN server, visit this OpenWRT guide: OpenVPN Setup Guide for Beginners.
- Note that I added two values to the list named push. As mentioned before, when adding values to list-type parameters use separate commands for separate values. If the value has a space in it (as in the example above) use quotation marks around the value ("<value>").
- Depending on your chosen authentication, the OpenVPN server instance might use certificate files for authentication with clients. A TLS server, as in our case, uses Certificate authority (.crt), Server certificate (.crt), Server key (.key) and Diffie Hellman Parameters (.pem) files for authentication. A Static Key server uses a Static Key (.key) file for authentication. In the example above I had all the files upload beforehand to /lib/uci/upload, so the commands that I used only provided the server's config with the paths to the files. When creating your own OpenVPN server you will have to generate your own certificates and upload the to /lib/uci/upload (the default directory for certificates) or somewhere else, but make sure to specify the correct path. To upload files to the router use the scp command if you're working with a Linux type OS or use software called WinSCP if you are using Windows OS. Or use Easy-RSA to create certificates within the router. The newly created certificates will appear in /etc/easy-rsa/keys. You can create certificates with these commands:
build-ca build-dh build-key-server my-server build-key-pkcs12 my-client
Additional examples
If the examples and explanations provided above did not suffice, we are providing this section of some additional ones in hopes to give you a better grasp of the syntax of UCI command usage.
Site Blocking
This example will provide instructions on how to enable RUT routers' Site Blocking feature and how to add hostnames to the Blacklist or Whitelist. Let's say for the sake of our example that you want to create a Blacklist that excludes access to all sites contained within the list. The sites in question are www.facebook.com, www.youtube.com and 9gag.com.
To achieve such a task, the first relevant piece of required information is the config name, hostblock, where all the necessary configuration lines are stored. The next important thing to know is that each different website must be stored in a separate section of the type block. So we'll need to create a new section and enable each added element. Let's start:
First element:
# uci add hostblock block # uci set hostblock.@block[0].host=www.facebook.com # uci set hostblock.@block[0].enabled=1
Second element:
# uci add hostblock block # uci set hostblock.@block[1].host=www.youtube.com # uci set hostblock.@block[1].enabled=1
Third element:
# uci add hostblock block # uci set hostblock.@block[2].host=9gag.com # uci set hostblock.@block[2].enabled=1
Enabling Site Blocking:
# uci set hostblock.config.enabled=1
Last steps:
# uci commit hostblock # luci-reload