Bridged office network with a separate Guest WiFi: Difference between revisions
(Created page with "{{Template:Networking rutos configuration example openvpn bridge wifi ap use case}}") |
PauliusRug (talk | contribs) No edit summary |
||
| (2 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
{{Template:Networking rutos configuration example openvpn bridge wifi ap use case}} | {{Template:Networking rutos configuration example openvpn bridge wifi ap use case}} | ||
[[Category:Use cases]] | |||
Latest revision as of 14:07, 2 August 2023
Main Page > General Information > Configuration Examples > Use cases > Bridged office network with a separate Guest WiFi
 |
|
|---|---|
|
|
Configuration overview and prerequisites
Prerequisites:
- Two RUTX routers (only the versions, which have WiFi)
- A Public Static or Public Dynamic IP address
- An end device to configure the router (PC, Laptop, Tablet, Smartphone)
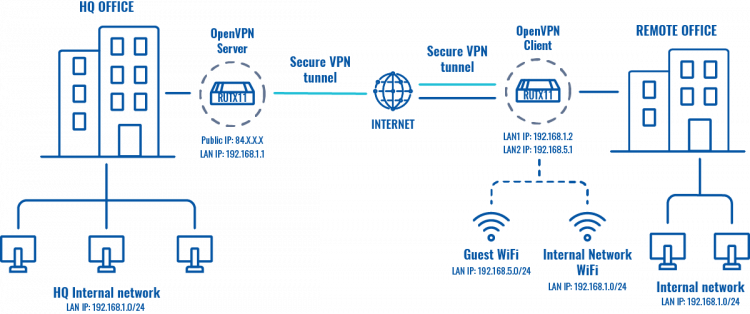
The topology above depicts the OpenVPN scheme. The router with the Public IP address (RUTX) acts as the OpenVPN server and other RUTX acts as client. OpenVPN connects the networks of HQ Office and Remote Office. Remote Office will also have a separate WiFi AP for guests.
When the scheme is realized, remote office workers will be able to reach HQ’s internal network with all internal systems by connecting to the router via LAN port or by connecting to a WiFi AP, which is used for work. All traffic apart guest WiFi is going to travel through VPN tunnel. Guest network traffic will go directly to WAN, it will give visitors access to the Internet connection, but nothing else making your company a lot more secure.
Configuring HQ office router
If you're having trouble finding this page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Advanced" button, located at the top of the WebUI.

Note: You will need to do that in both, HQ and remote office routers.
OpenVPN
Generating TLS Certificates
Refer to the TLS Certificates Wiki guide to generate the necessary certificates for the OpenVPN configuration.
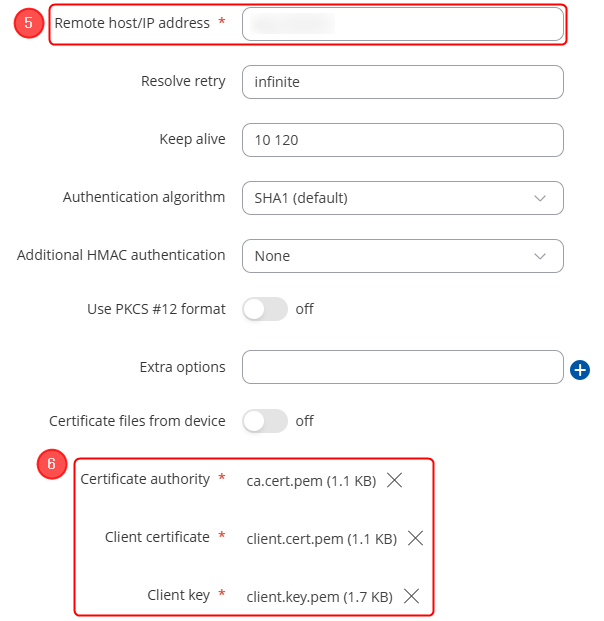
Configuring OpenVPN server
  |
|
|---|---|
|
Now apply the following configuration:
|
Configuring remote office router
Before you start configuring the remote office router, set a static IP address on the device you are configuring the router with (e.g. 192.168.1.10). You can find instructions on how to do that here:
Note: make sure to switch back to automatic DNS and IP address obtaining when you are done configuring the router.
OpenVPN
LAN
 |
|
|---|---|
|
Go to Network → LAN and press Edit next to your LAN interface: |
 |
|
|---|---|
|
Apply the following steps:
|
Configuring OpenVPN client
Guest WiFi
Creating a new WiFi AP
 |
|
|---|---|
|
Go to Network → Wireless → SSIDs. There create a new WiFi Access Point by pressing Add button. Then you will be forwarded to the configuration window. |
 |
|
|---|---|
|
Apply the following steps:
|
 |
|
|---|---|
|
Now go to Network → LAN and press Edit next to your newly created LAN interface: |
 |
|
|---|---|
|
Now apply the following steps:
|
Editing Firewall rules
 |
|
|---|---|
|
Navigate to Network → Firewall → General Settings. There create a new Zone rule by pressing Add button. Then you will be forwarded to the configuration window. |
 |
|
|---|---|
|
Now apply the following steps:
|