OpenVPN over Stunnel RutOS: Difference between revisions
No edit summary |
No edit summary |
||
| (11 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
==Introduction== | |||
| | <b>Stunnel</b> is an open-source proxy service that adds TLS encryption to clients and servers already existing on a VPN network. TLS encryption provided by Stunnel can be used as an additional layer of encryption for data sent by OpenVPN. This procedure increases the security of the established connection and provides higher chances of passing a Deep packet inspection (DPI) check. | ||
| | This article contains instructions on how to configure an OpenVPN over the Stunnel topology. | ||
| | |||
==Overview== | |||
| | <b>You will need</b> | ||
| | |||
<ul> | |||
<li>two routers of the RUTxxx series (except RUT850);</li> | |||
<li>at least one router (server) with a public IP;</li> | |||
<li>TLS certificates for the server and the client (<i>for instructions on generating TLS certificates, [[How to generate TLS certificates (Windows)?|click here]]</i>).</li> | |||
</ul> | |||
---- | |||
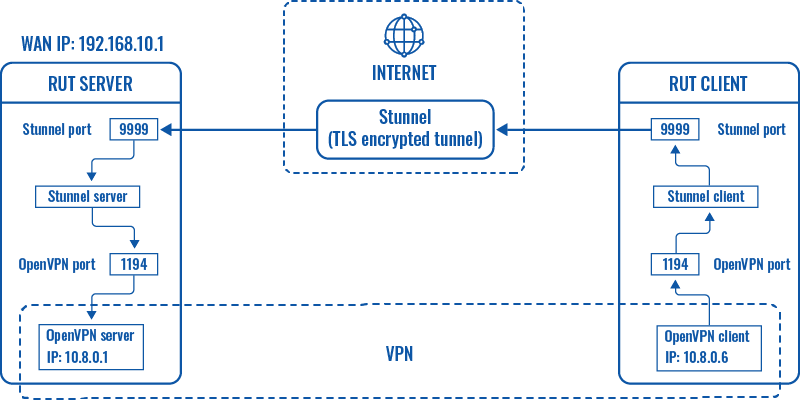
<b>Topology</b> | |||
[[File:Networking_device_vpn_stunnel_working_scheme_v4.png]] | |||
<b>Explanation</b> | |||
An OpenVPN client is connected to an OpenVPN server (both hosted on RUT routers) via a TLS encrypted Stunnel connection. This allows the transfer of data between remote private networks (LAN A and LAN B) and adds a TLS security layer for the connection. | |||
==Server configuration== | |||
First, configure the OpenVPN and Stunnel servers. The Stunnel server will listen for incoming client connections on the specified TCP port (<i>9999</i> in this example) and connect them to the OpenVPN server running on the local host. | |||
The logic of the connection can be visualized like this: | |||
[[File:Networking_device_vpn_stunnel_server_working_scheme_v2.png]] | |||
===OpenVPN server=== | |||
---- | |||
Navigate to the <b>Services → VPN → OpenVPN</b> page. Select <i>Role: Server</i>, enter a custom name and click the 'Add New' button. An OpenVPN server instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the server instance. | |||
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=330; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:Open_VPN_server_configuration_part_1.jpg|border|class=tlt-border]] | |||
[[File:Open_VPN_server_configuration_part_2.jpg|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
# '''Enable''' the instance | |||
# Select ''''''TCP'''''' protocol | |||
# Select port '''1194'''. | |||
# '''TLS''' cipher select All | |||
# Set Virtual network IP address | |||
# Set virtual network '''Netmask''' | |||
# (Optional) push a route to make Lan network available to clients | |||
# Upload '''TLS''' certificates | |||
# Upload Diffie Hellman parameters | |||
</td> | |||
</tr> | |||
</table> | |||
Don't forget to click the <b>Save</b> button located at the bottom-right side of the page. | |||
===Stunnel server=== | |||
---- | |||
To create a new Stunnel instance, enter a custom name for it and click the 'Add' button. A new instance with the given name will appear in the "Stunnel Configuration" list. To begin configuration, click the 'Edit' button next to the instance. | |||
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=330; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:Stunnel_Server_configuration.png|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
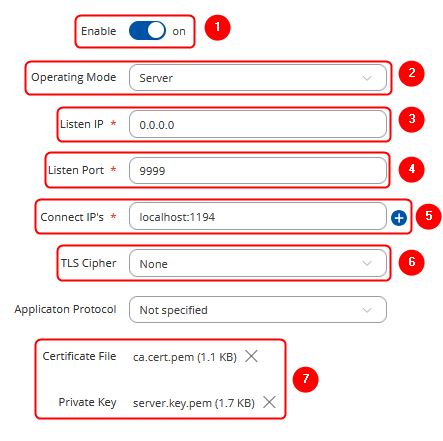
# '''Enable''' the instance | |||
# Choose operating mode ''''''Server''''''. | |||
# Enter '''0.0.0.0'''. | |||
# Enter '''9999''' (Stunnel port) | |||
# Enter localhost followed by the OpenVPN port ('localhost:1194' in this example) | |||
# Select '''Secure''' cipher | |||
# Upload certificate and key files | |||
</td> | |||
</tr> | |||
</table> | |||
Don't forget to click the <b>Save</b> button located at the bottom-right side of the page. | |||
===Open Stunnel port=== | |||
---- | |||
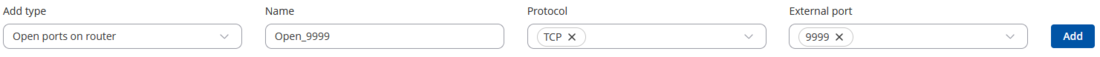
The OpenVPN default port (<i>1194</i>) is opened by default. But you will have manually open the select Stunnel port (<i>9999</i> in this example). | |||
To do this, navigate to the <b>Network → Firewall → Traffic Rules</b> page and scroll down until you see the <b>Open Ports On Router</b> section. Fill out the configuration fields as indicated in the figure above and click the 'Add' button: | |||
[[File:Traffic_rules_configuration.png|border|class=tlt-border|1100px]] | |||
==Client configuration== | |||
Configure the OpenVPN and Stunnel clients that will be connecting to the server. Unlike in the server, there is a reason to configure the Stunnel client before the OpenVPN client (the other way around will also work but an OpenVPN service restart may be required) so it is recommended to start with that. | |||
The OpenVPN client will connect to <i>TCP port 1194</i> of the local host and the Stunnel client will connect to the WAN IP and Stunnel port (<i>192.168.10.1:9999</i> in this example) of the server router. | |||
The logic of the entire connection can be visualized like this: | |||
[[File:Networking_device_vpn_stunnel_complete_configuration_scheme_v2.png]] | |||
===Stunnel client=== | |||
---- | |||
To create a new Stunnel instance, enter a custom name for it and click the 'Add' button. A new instance with the given name will appear in the "Stunnel Configuration" list. To begin configuration, click the 'Edit' button next to the instance. | |||
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=330; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:Stunnel_client_configuration.jpg|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
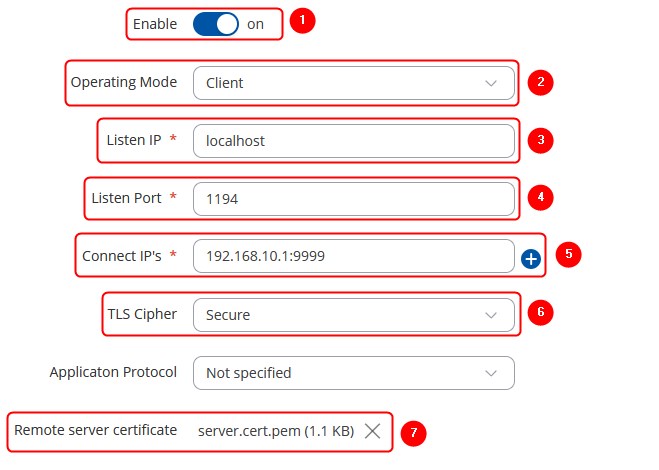
# '''Enable''' the instance | |||
# Select '''''Client''''' | |||
# Enter '''localhost'''. | |||
# Enter '''1194''' Open VPN port | |||
# Enter the server's Wan IP followed by Stunnel port number ('192.168.10.1.:9999' In this example) | |||
# Select '''Secure''' Cipher | |||
# Upload remote server certificate | |||
</td> | |||
</tr> | |||
</table> | |||
Don't forget to click the <b>Save</b> button located at the bottom-right side of the page. | |||
===OpenVPN client=== | |||
---- | |||
Navigate to the <b>Services → VPN → OpenVPN</b> page. Select <i>Role: Server</i>, enter a custom name and click the 'Add New' button. An OpenVPN client instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the client instance. | |||
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<th width=330; style="border-bottom: 1px solid white;></th> | |||
<th width=800; style="border-bottom: 1px solid white;" rowspan=2> | |||
[[File:Open VPN client configuration part 1.png|border|class=tlt-border]] | |||
[[File:Open_VPN_client_configuration_part_2.png|border|class=tlt-border]]</th> | |||
</tr> | |||
<tr> | |||
<td style="border-bottom: 4px solid white> | |||
# '''Enable''' the instance | |||
# Select ''''''TCP'''''' protocol | |||
# Specify '''localhost'''. | |||
# Upload '''TLS''' Certificates | |||
</td> | |||
</tr> | |||
</table> | |||
Don't forget to click the <b>Save</b> button located at the bottom-right side of the page. | |||
==Testing and troubleshooting== | |||
If you have completed the steps presented above, your configuration is complete. This section provides tips on how to test and troubleshoot this <i>OpenVPN over Stunnel</i> connection. | |||
<ul> | |||
<li>Check whether remote side is reachable by sending ICMP requests. To do that, go to the <b>Services → CLI</b> page. Login (username: <i>root</i>; password: <i>router's password</i>) and ping the opposite instance: | |||
<pre>ping 10.8.0.6</pre>Is the response looks like this, then the connection was established successfully: | |||
<pre> | |||
64 bytes from 10.8.0.6: seq=0 ttl=64 time=101.214 ms | |||
64 bytes from 10.8.0.6: seq=1 ttl=64 time=91.018 ms | |||
64 bytes from 10.8.0.6: seq=2 ttl=64 time=88.974 ms | |||
64 bytes from 10.8.0.6: seq=3 ttl=64 time=502.781 ms | |||
</pre> | |||
</li> | |||
---- | |||
<li>If there is no response to the ping requests, check whether Stunnel and OpenVPN services are running on the device. For Stunnel use this command: | |||
<pre>ps | grep stunnel | grep -v grep</pre>The output should look similar to this: | |||
<pre> | |||
16122 root 2992 S /usr/bin/stunnel /tmp/stunnel.conf | |||
</pre>For OpenVPN use this command: | |||
<pre>ps | grep openvpn | grep -v grep</pre>The output should look similar to this: | |||
<pre>13034 root 3428 S /usr/sbin/openvpn --syslog openvpn(7365727665725F41)</pre> | |||
</li> | |||
---- | |||
<li>To restart OpenVPN or Stunnel services, use one of these commands: | |||
<pre>/etc/init.d/openvpn restart</pre> | |||
<pre>/etc/init.d/stunnel restart</pre> | |||
</li> | |||
---- | |||
<li> Double-check your configuration. Check for configuration mistakes, see if correct certificate files are uploaded onto each instance, make sure the Stunnel port is not used by another program, etc.</li> | |||
</ul> | |||
[[Category:VPN]] | |||
Latest revision as of 11:44, 29 October 2024
Main Page > General Information > Configuration Examples > VPN > OpenVPN over Stunnel RutOSIntroduction
Stunnel is an open-source proxy service that adds TLS encryption to clients and servers already existing on a VPN network. TLS encryption provided by Stunnel can be used as an additional layer of encryption for data sent by OpenVPN. This procedure increases the security of the established connection and provides higher chances of passing a Deep packet inspection (DPI) check.
This article contains instructions on how to configure an OpenVPN over the Stunnel topology.
Overview
You will need
- two routers of the RUTxxx series (except RUT850);
- at least one router (server) with a public IP;
- TLS certificates for the server and the client (for instructions on generating TLS certificates, click here).
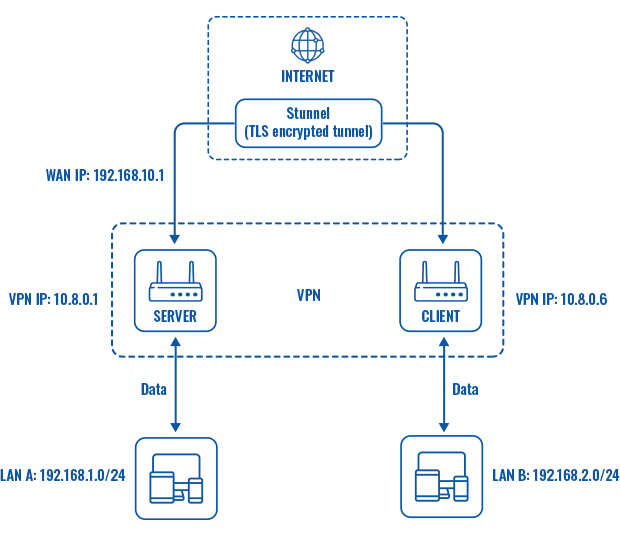
Topology
Explanation
An OpenVPN client is connected to an OpenVPN server (both hosted on RUT routers) via a TLS encrypted Stunnel connection. This allows the transfer of data between remote private networks (LAN A and LAN B) and adds a TLS security layer for the connection.
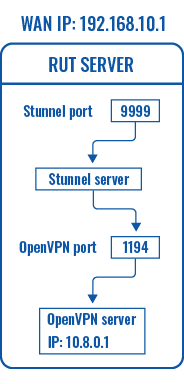
Server configuration
First, configure the OpenVPN and Stunnel servers. The Stunnel server will listen for incoming client connections on the specified TCP port (9999 in this example) and connect them to the OpenVPN server running on the local host.
The logic of the connection can be visualized like this:
OpenVPN server
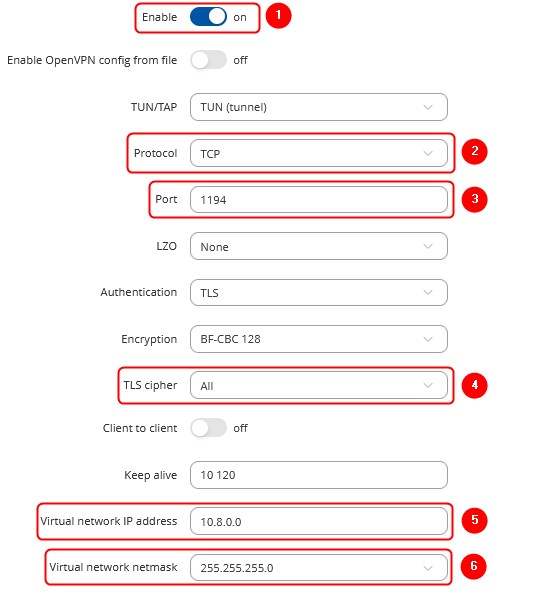
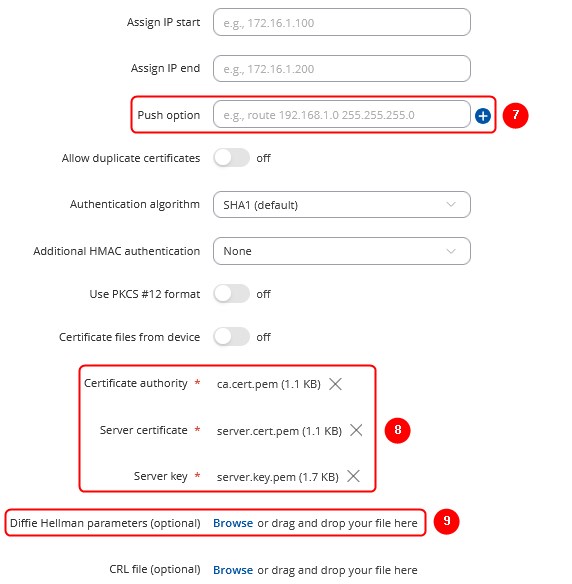
Navigate to the Services → VPN → OpenVPN page. Select Role: Server, enter a custom name and click the 'Add New' button. An OpenVPN server instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the server instance.
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value:
Don't forget to click the Save button located at the bottom-right side of the page.
Stunnel server
To create a new Stunnel instance, enter a custom name for it and click the 'Add' button. A new instance with the given name will appear in the "Stunnel Configuration" list. To begin configuration, click the 'Edit' button next to the instance.
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value:
Don't forget to click the Save button located at the bottom-right side of the page.
Open Stunnel port
The OpenVPN default port (1194) is opened by default. But you will have manually open the select Stunnel port (9999 in this example).
To do this, navigate to the Network → Firewall → Traffic Rules page and scroll down until you see the Open Ports On Router section. Fill out the configuration fields as indicated in the figure above and click the 'Add' button:
Client configuration
Configure the OpenVPN and Stunnel clients that will be connecting to the server. Unlike in the server, there is a reason to configure the Stunnel client before the OpenVPN client (the other way around will also work but an OpenVPN service restart may be required) so it is recommended to start with that.
The OpenVPN client will connect to TCP port 1194 of the local host and the Stunnel client will connect to the WAN IP and Stunnel port (192.168.10.1:9999 in this example) of the server router.
The logic of the entire connection can be visualized like this:
Stunnel client
To create a new Stunnel instance, enter a custom name for it and click the 'Add' button. A new instance with the given name will appear in the "Stunnel Configuration" list. To begin configuration, click the 'Edit' button next to the instance.
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value:
Don't forget to click the Save button located at the bottom-right side of the page.
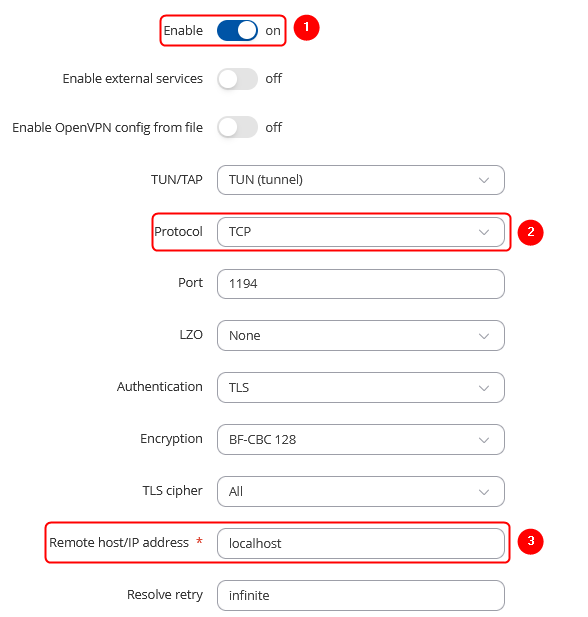
OpenVPN client
Navigate to the Services → VPN → OpenVPN page. Select Role: Server, enter a custom name and click the 'Add New' button. An OpenVPN client instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the client instance.
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value:
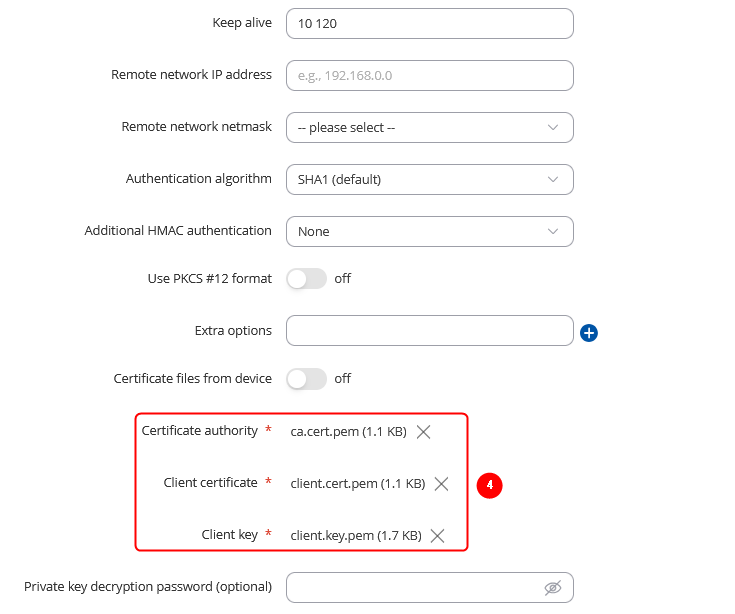 |
|
|---|---|
|
Don't forget to click the Save button located at the bottom-right side of the page.
Testing and troubleshooting
If you have completed the steps presented above, your configuration is complete. This section provides tips on how to test and troubleshoot this OpenVPN over Stunnel connection.
- Check whether remote side is reachable by sending ICMP requests. To do that, go to the Services → CLI page. Login (username: root; password: router's password) and ping the opposite instance:
ping 10.8.0.6
Is the response looks like this, then the connection was established successfully:64 bytes from 10.8.0.6: seq=0 ttl=64 time=101.214 ms 64 bytes from 10.8.0.6: seq=1 ttl=64 time=91.018 ms 64 bytes from 10.8.0.6: seq=2 ttl=64 time=88.974 ms 64 bytes from 10.8.0.6: seq=3 ttl=64 time=502.781 ms - If there is no response to the ping requests, check whether Stunnel and OpenVPN services are running on the device. For Stunnel use this command:
ps | grep stunnel | grep -v grep
The output should look similar to this:16122 root 2992 S /usr/bin/stunnel /tmp/stunnel.confFor OpenVPN use this command:ps | grep openvpn | grep -v grep
The output should look similar to this:13034 root 3428 S /usr/sbin/openvpn --syslog openvpn(7365727665725F41)
- To restart OpenVPN or Stunnel services, use one of these commands:
/etc/init.d/openvpn restart
/etc/init.d/stunnel restart
- Double-check your configuration. Check for configuration mistakes, see if correct certificate files are uploaded onto each instance, make sure the Stunnel port is not used by another program, etc.