Static Routing with Teltonika Devices Configuration: Difference between revisions
Keith.Mafuwe (talk | contribs) No edit summary |
Keith.Mafuwe (talk | contribs) No edit summary |
||
| (23 intermediate revisions by the same user not shown) | |||
| Line 13: | Line 13: | ||
== Configuration topology == | == Configuration topology == | ||
[[File:Static-Routing-Topology.png|frameless|654x654px]] | |||
RUT1 – This device will be connected RUT2 via a point-to-point WAN connection. The WAN IP on RUT is a static private '''192.168.1.1/30'''. | '''RUT1''' – This device will be connected RUT2 via a point-to-point WAN connection. The WAN IP on RUT is a static private '''192.168.1.1/30'''. | ||
RUT2 – This device will be connected to RUT1 via a point-to-point WAN connection and RUT3 via WAN port (A LAN port is configured as WAN port in this configuration example), The WAN Port has a private Static IP '''192.168.1.2/30''' and the WAN2 (LAN as WAN interface) has a | '''RUT2''' – This device will be connected to RUT1 via a point-to-point WAN connection and RUT3 via WAN port (A LAN port is configured as WAN port in this configuration example), The WAN Port has a private Static IP '''192.168.1.2/30''' and the WAN2 (LAN as WAN interface) has a private static IP of '''192.168.3.1/30''' | ||
RUT3 – This router is connected to RUT2 via a point-to-point WAN connection. The WAN IP on this device is a private static IP '''192.168.3.2/30''' | '''RUT3''' – This router is connected to RUT2 via a point-to-point WAN connection. The WAN IP on this device is a private static IP '''192.168.3.2/30''' | ||
== RUT1 Configuration == | == RUT1 Configuration == | ||
| Line 33: | Line 33: | ||
Leave all the parameters as default and click on '''"Save and Apply"''' | Leave all the parameters as default and click on '''"Save and Apply"''' | ||
[[File: | |||
[[File:R1_Routes-2.png|frameless|1000x1000px]] | |||
==== Firewall Configuration: ==== | ==== Firewall Configuration: ==== | ||
| Line 46: | Line 47: | ||
# Select “'''LAN'''” as the destination zone | # Select “'''LAN'''” as the destination zone | ||
# Click on the “'''Add'''” button | # Click on the “'''Add'''” button | ||
[[File: | [[File:R1_Firewall_Rule-2.png|frameless|900x900px]] | ||
In the Traffic rule page, do the following (and leave the rest as defaults, unless your specific configuration requires specific changes): | In the Traffic rule page, do the following (and leave the rest as defaults, unless your specific configuration requires specific changes): | ||
| Line 72: | Line 68: | ||
* Navigate to '''Network → Routing → Static Routes''' and click on “'''Add'''” | * Navigate to '''Network → Routing → Static Routes''' and click on “'''Add'''” | ||
Route '''10.0.0.0/24''' via '''192.168.2.1''' | # Route '''10.0.0.0/24''' via '''192.168.2.1''' | ||
# Route '''192.168.10.0/24''' via '''192.168.3.1''' | |||
Route '''192.168.10.0/24''' via '''192.168.3.1''' | |||
[[File:R2 Routes fixed.png|frameless|891x891px]] | [[File:R2 Routes fixed.png|frameless|891x891px]] | ||
| Line 84: | Line 79: | ||
Navigate to '''Network → Firewall → Traffic Rules''' and configure the following traffic rules | Navigate to '''Network → Firewall → Traffic Rules''' and configure the following traffic rules | ||
# '''Enable''' the rule | <table class="nd-othertables_2"> | ||
# Select '''ICMP protocol''' (Or any other protocol suited to your use case) | |||
# Select '''WAN''' as the ''' | <tr> | ||
# | <td> | ||
# | #'''Enable''' the rule | ||
# Select “'''Accept''' | #Add the '''name''' of your rule | ||
#Select '''ICMP protocol''' (Or any other protocol suited to your use case) | |||
#Select '''WAN''' as your '''Source Zone''' | |||
#Enter your Source IP '''192.168.2.1''' (RUT1 WAN IP) | |||
#Select '''WAN''' as your '''Destination Zone''' | |||
#Enter your '''Destination Address 192.168.10.0/24''' (RUT3 LAN Network) | |||
#Select "'''Accept'''" as the action </td> | |||
<td> | |||
[[File:R2 Firewall rule 1.png]] | |||
</td> | |||
</tr></table> | |||
---- | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<td> | |||
#'''Enable''' the rule | |||
#Add the '''name''' of your rule | |||
#Select '''ICMP protocol''' (Or any other protocol suited to your use case) | |||
#Select '''WAN''' as your '''Source Zone''' | |||
#Enter your Source IP '''192.168.3.2''' (RUT3 WAN IP) | |||
#Select '''WAN''' as your '''Destination Zone''' | |||
#Enter your '''Destination Address 10.0.0.0/24''' (RUT1 LAN Network) | |||
#Select "'''Accept'''" as the action </td> | |||
<td> | |||
[[File:R2 Firewall rule 2.png|728x728px]] | |||
</td> | |||
</tr></table> | |||
---- | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<td> | |||
#'''Enable''' the rule | |||
#Add the '''name''' of your rule | |||
#Select '''ICMP protocol''' (Or any other protocol suited to your use case) | |||
#Select '''WAN''' as your '''Source Zone''' | |||
#Enter your Source IP '''192.168.2.1''' (RUT1 WAN IP) and '''192.168.3.2''' (RUT3 WAN IP) | |||
#Select '''LAN''' as your '''Destination Zone''' | |||
#Enter your '''Destination Address 172.16.1.0/24''' (RUT2 LAN Network) | |||
#Select "'''Accept'''" as the action </td> | |||
<td>[[File:R2_Firewall_rule_3.png|frameless|532x532px]]</td> | |||
</tr></table> | |||
== RUT 3 Configuration == | |||
The last step is to configure static routes and firewall traffic rules on the third router (RUT 3), to achieve this, follow the below steps: | |||
* Navigate to '''Network → Routing → Static Routes''' and click on “'''Add'''” | |||
# Route: '''172.16.1.0/24''' via '''192.168.3.1''' | |||
# Route: '''192.168.2.0/30''' via '''192.168.3.1''' | |||
# Route '''10.0.0.0/24''' via '''192.168.3.1''' | |||
Leave all the parameters as default and click on '''"Save and Apply"''' | |||
[[File:RUT3 Static Routes.png|frameless|1000x1000px]] | |||
==== Firewall Configuration: ==== | |||
---- | |||
After configuring the static routes on RUT2, we need to add traffic rules on RUT2. | |||
Navigate to '''Network → Firewall → Traffic Rules''' and configure the following traffic rules: | |||
# Select traffic rule type and choose “'''Add a new forward rule'''” | |||
# Input a name for your new rule, e.g. “'''ALLOW_ICMP_from_R2'''” | |||
# Select “'''WAN'''” as the Source zone | |||
# Select “'''LAN'''” as the destination zone | |||
# Click on the “'''Add'''” button | |||
[[File:R3 Firewall rule setup.png|1083x1083px]] | |||
In the Traffic rule page, do the following (and leave the rest as defaults, unless your specific configuration requires specific changes): | |||
<table class="nd-othertables_2"> | |||
<tr> | |||
<td> | |||
#'''Enable''' the rule | |||
#Add the '''name''' of your rule | |||
#Select '''ICMP protocol''' (Or any other protocol suited to your use case) | |||
#Select '''WAN''' as your '''Source Zone''' | |||
#Enter your Source IP '''192.168.3.1''' (RUT2 WAN IP) | |||
#Select '''LAN''' as your '''Destination Zone''' | |||
#Enter your '''Destination Address 192.168.10.0/24''' (RUT3 LAN Network) | |||
#Select "'''Accept'''" as the action </td> | |||
<td> | |||
[[File:R3 Firewall rules2.png|frameless|683x683px]] | |||
</td> | |||
</tr></table> | |||
== Testing the configuration == | |||
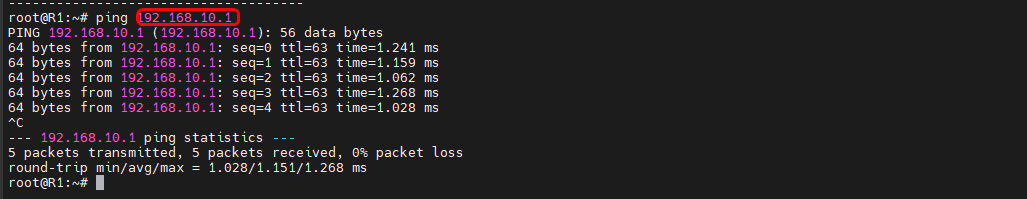
If you've followed all the steps presented above, your configuration should be finished. But as with any other configuration, it is always recommended to test the setup in order to make sure that it works properly. To confirm that this setup works you, you may log into '''RUT1''' CLI using the '''LAN IP''' and the device's username ('''root''') and password and run a Ping to the LAN networks on '''RUT2''' and '''RUT3''' and vice versa, as show below. | |||
'''Ping to RUT2 LAN:''' | |||
[[File:TEST to RUT2.png]] | |||
'''Ping to RUT3 LAN:''' | |||
[[File:TEST to RUT3.png]] | |||
If the ping requests are successful, congratulations, your setup works, If not, we suggest that you review all the steps once more. | |||
Latest revision as of 16:16, 21 January 2025
Introduction
Static routing is a method of configuring routing paths on a network by specifying fixed routes between networking devices. Static routing is simple and does not require any overhead or specific protocols and it offers more predictable approach to routing. Static routing is best suited for small, stable networks or specific routes within larger setups. however, lacks the ability to adapt to network changes.
Configuration overview and prerequisites:
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
- 3 RUTOS devices
- At least one end device to (PC, laptop, Smartphone or tablet) to configure the routers
If you're having trouble finding this page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Advanced" button, located at the top of the WebUI.
Configuration topology
RUT1 – This device will be connected RUT2 via a point-to-point WAN connection. The WAN IP on RUT is a static private 192.168.1.1/30.
RUT2 – This device will be connected to RUT1 via a point-to-point WAN connection and RUT3 via WAN port (A LAN port is configured as WAN port in this configuration example), The WAN Port has a private Static IP 192.168.1.2/30 and the WAN2 (LAN as WAN interface) has a private static IP of 192.168.3.1/30
RUT3 – This router is connected to RUT2 via a point-to-point WAN connection. The WAN IP on this device is a private static IP 192.168.3.2/30
RUT1 Configuration
The first step is to configure static Routing and firewall rules on RUT 1, to achieve this, follow these steps:
- Navigate to Network → Routing → Static Routes and click on “Add”
- Add the below IPv4 Routes:
- Route: 172.16.1.0/24 via 192.168.2.2
- Route: 192.168.3.0/30 via 192.168.2.2
- Route 192.168.10.0/24 via 192.168.2.2
Leave all the parameters as default and click on "Save and Apply"
Firewall Configuration:
After configuring the static routes on RUT1, we need to add traffic rules on RUT1's firewall.
Navigate to Network → Firewall → Traffic Rules and configure the following:
- Select traffic rule type and choose “Add a new forward rule”
- Input a name for your new rule, e.g. “Allow_Pings_From_R2”
- Select “WAN” as the Source zone
- Select “LAN” as the destination zone
- Click on the “Add” button
In the Traffic rule page, do the following (and leave the rest as defaults, unless your specific configuration requires specific changes):
- Enable the rule
- Select ICMP protocol (Or any other protocol suited to your use case)
- Input your Source address (RUT2 WAN)
- Input the Destination Address (RUT 1 LAN)
- Select “Accept” as the action
Leave all the other parameters as default and click on "Save and Apply"
RUT2 Configuration
The next step is to configure static Routing and firewall rules on RUT 2, to achieve this, follow these steps:
- First we need to configure an additional LAN port to function as a WAN port, this can be achieved by following the guideline outlined on here
- Once the additional LAN port has been configured, we need to procced and add the below routes on RUT2
- Navigate to Network → Routing → Static Routes and click on “Add”
- Route 10.0.0.0/24 via 192.168.2.1
- Route 192.168.10.0/24 via 192.168.3.1
Firewall Configuration
After configuring the static routes on RUT2, we need to add traffic rules on RUT2.
Navigate to Network → Firewall → Traffic Rules and configure the following traffic rules
|
|
RUT 3 Configuration
The last step is to configure static routes and firewall traffic rules on the third router (RUT 3), to achieve this, follow the below steps:
- Navigate to Network → Routing → Static Routes and click on “Add”
- Route: 172.16.1.0/24 via 192.168.3.1
- Route: 192.168.2.0/30 via 192.168.3.1
- Route 10.0.0.0/24 via 192.168.3.1
Leave all the parameters as default and click on "Save and Apply"
Firewall Configuration:
After configuring the static routes on RUT2, we need to add traffic rules on RUT2.
Navigate to Network → Firewall → Traffic Rules and configure the following traffic rules:
- Select traffic rule type and choose “Add a new forward rule”
- Input a name for your new rule, e.g. “ALLOW_ICMP_from_R2”
- Select “WAN” as the Source zone
- Select “LAN” as the destination zone
- Click on the “Add” button
In the Traffic rule page, do the following (and leave the rest as defaults, unless your specific configuration requires specific changes):
|
Testing the configuration
If you've followed all the steps presented above, your configuration should be finished. But as with any other configuration, it is always recommended to test the setup in order to make sure that it works properly. To confirm that this setup works you, you may log into RUT1 CLI using the LAN IP and the device's username (root) and password and run a Ping to the LAN networks on RUT2 and RUT3 and vice versa, as show below.
Ping to RUT2 LAN:
Ping to RUT3 LAN:
If the ping requests are successful, congratulations, your setup works, If not, we suggest that you review all the steps once more.