VLAN Inter-Zone accessibility control configuration example: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
<p style="color:red">The information | <p style="color:red">The information on this page is updated in accordance with firmware version '''[https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads 00.07.13.1]'''. | ||
==Introduction== | ==Introduction== | ||
In this example we will show how to manage VLAN to VLAN communication with either '''one''' firewall zone or '''multiple''' firewall zones. | In this example we will show how to manage VLAN to VLAN communication with either '''one''' firewall zone or '''multiple''' firewall zones. | ||
==Setting up VLANs== | ==Setting up VLANs== | ||
In this example, we are assuming that the VLANs are already set up | In this example, we are assuming that the VLANs are already set up; we will configure the firewall accordingly. If you need information on how to create VLANs on your device, please refer to this article: [[VLAN_Set_Up|VLAN set up]]. For this article, we have 3 separate VLANs created: | ||
*lan | IP 192.168.1.1/24 | *lan | IP 192.168.1.1/24 | ||
*lan2 | IP 192.168.2.1/24 | *lan2 | IP 192.168.2.1/24 | ||
| Line 29: | Line 26: | ||
[[File:Allowlan1tolan2pingoriginal.png|border|class=tlt-border|]] | [[File:Allowlan1tolan2pingoriginal.png|border|class=tlt-border|]] | ||
To disable VLAN to VLAN communication, navigate to '''Network -> Firewall -> | To disable VLAN to VLAN communication, navigate to '''Network -> Firewall -> Zones'''. Press '''Edit''' on the '''LAN''' zone (lan => wan). | ||
[[File: | [[File:Editfwzonev2.png|border|1100x1100px]] | ||
Click on ''' | Click on '''Intra zone forward''' and select '''Drop or Reject'''. Make sure that all created VLANs are added in the Covered networks tab: | ||
[[File: | [[File:Disablevlan2vlandefaultv3.png|border]] | ||
Now if we try to reach lan2 from lan, the devices are not able to communicate: | Now if we try to reach lan2 from lan, the devices are not able to communicate: | ||
| Line 47: | Line 44: | ||
[[File:3zonetopology.png|600px|border|class=tlt-border]] | [[File:3zonetopology.png|600px|border|class=tlt-border]] | ||
To start with, we will need to create new firewall zones: LAN1, LAN2 and LAN3. To add new zones, navigate to '''Network -> Firewall -> | To start with, we will need to create new firewall zones: LAN1, LAN2 and LAN3. To add new zones, navigate to '''Network -> Firewall -> Zones'''. In the Zones section, press [[File:Add Button.png|60x90px]] to add a new zone. | ||
[[File: | [[File:Addnewfwzone1v2.png|border|1100x1100px]] | ||
A new window will open, there configure the settings according to the points below and press [[File:Save & Apply.png|100x30px]].: | A new window will open, there configure the settings according to the points below and press [[File:Save & Apply.png|100x30px]].: | ||
| Line 55: | Line 52: | ||
<tr> | <tr> | ||
<th width=400; style="border-bottom: 1px solid white;></th> | <th width=400; style="border-bottom: 1px solid white;></th> | ||
<th width=600; style="border-bottom: 1px solid white"; rowspan=2>[[File: | <th width=600; style="border-bottom: 1px solid white"; rowspan=2>[[File:Interzonecreationv3.png|border|right]]</th> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
| Line 62: | Line 59: | ||
# Input: '''Accept''' | # Input: '''Accept''' | ||
# Output: '''Accept''' | # Output: '''Accept''' | ||
# | # Intra zone forward: '''Reject''' | ||
# Covered networks: '''lan''' | # Covered networks: '''lan''' | ||
</td> | </td> | ||
</tr> | </tr> | ||
</table> | </table> | ||
'''Note''': By setting the Input and Output zones to '''Accept''' traffic is allowed to enter and leave the zone. ''' | '''Note''': By setting the Input and Output zones to '''Accept''' traffic is allowed to enter and leave the zone. '''Intra zone forward: Reject''' blocks communication between zones - this is a default policy. '''Inter-zone forwarding''' section can be used to modify the default behavior of the Forward zone and allow communication between zones. | ||
---- | ---- | ||
| Line 78: | Line 75: | ||
* Input: '''Accept''' | * Input: '''Accept''' | ||
* Output: '''Accept''' | * Output: '''Accept''' | ||
* | * Intra zone forward: '''Reject''' | ||
* Covered networks: '''lan2''' | * Covered networks: '''lan2''' | ||
| Line 86: | Line 83: | ||
* Input: '''Accept''' | * Input: '''Accept''' | ||
* Output: '''Accept''' | * Output: '''Accept''' | ||
* | * Intra zone forward: '''Reject''' | ||
* Covered networks: '''lan3''' | * Covered networks: '''lan3''' | ||
| Line 96: | Line 93: | ||
==Inter-zone forwarding use examples== | ==Inter-zone forwarding use examples== | ||
To customize communication between VLANs, we will need to edit Inter-zone forwarding rules. Navigate back to the firewall settings ('''Network -> Firewall -> | To customize communication between VLANs, we will need to edit Inter-zone forwarding rules. Navigate back to the firewall settings ('''Network -> Firewall -> Zones''') and edit zones according to your needs. | ||
---- | ---- | ||
| Line 104: | Line 101: | ||
<tr> | <tr> | ||
<th width=400; style="border-bottom: 1px solid white;></th> | <th width=400; style="border-bottom: 1px solid white;></th> | ||
<th width=600; style="border-bottom: 1px solid white"; rowspan=2>[[File: | <th width=600; style="border-bottom: 1px solid white"; rowspan=2>[[File:Intervlanzoneforwardv3.png|border|right]]</th> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
Latest revision as of 15:38, 7 March 2025
Main Page > General Information > Configuration Examples > Router control and monitoring > VLAN Inter-Zone accessibility control configuration exampleThe information on this page is updated in accordance with firmware version 00.07.13.1.
Introduction
In this example we will show how to manage VLAN to VLAN communication with either one firewall zone or multiple firewall zones.
Setting up VLANs
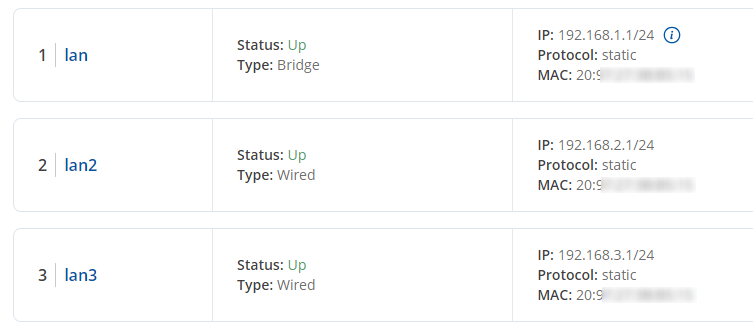
In this example, we are assuming that the VLANs are already set up; we will configure the firewall accordingly. If you need information on how to create VLANs on your device, please refer to this article: VLAN set up. For this article, we have 3 separate VLANs created:
- lan | IP 192.168.1.1/24
- lan2 | IP 192.168.2.1/24
- lan3 | IP 192.168.3.1/24
Created VLANs in the WebUI should look similar to this:
VLAN to VLAN communication with one firewall zone
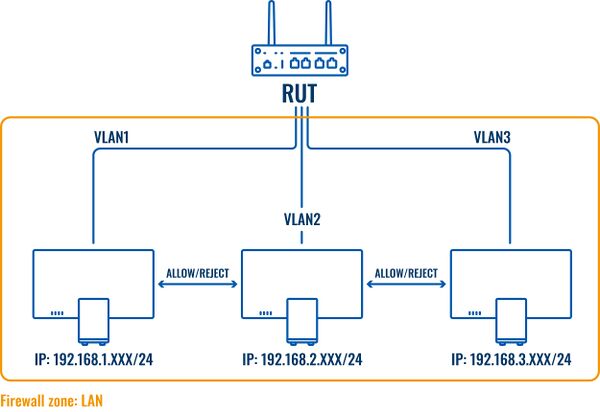
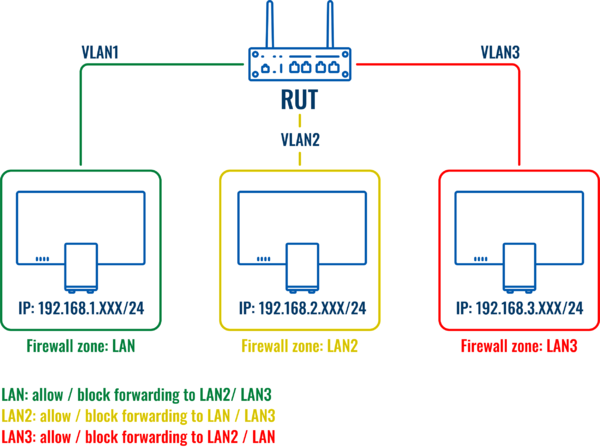
Once VLANs are created - they lay under one firewall zone, here is a Topology of the network and the zone which covers all 3 of VLANs:
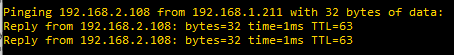
Initially, when we create VLAN interfaces, all VLANs are able to communicate with each other, for example pinging from lan to lan2:
To disable VLAN to VLAN communication, navigate to Network -> Firewall -> Zones. Press Edit on the LAN zone (lan => wan).
Click on Intra zone forward and select Drop or Reject. Make sure that all created VLANs are added in the Covered networks tab:
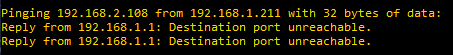
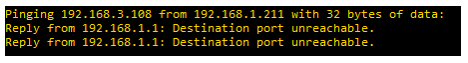
Now if we try to reach lan2 from lan, the devices are not able to communicate:
VLAN to VLAN communication with inter-zone forwarding
In order to get more control over VLANs, an inter-zone forwarding functionality should be used. Here is a network topology with firewall zones and an explanation.
To start with, we will need to create new firewall zones: LAN1, LAN2 and LAN3. To add new zones, navigate to Network -> Firewall -> Zones. In the Zones section, press ![]() to add a new zone.
to add a new zone.
A new window will open, there configure the settings according to the points below and press ![]() .:
.:
 |
|
|---|---|
|
Note: By setting the Input and Output zones to Accept traffic is allowed to enter and leave the zone. Intra zone forward: Reject blocks communication between zones - this is a default policy. Inter-zone forwarding section can be used to modify the default behavior of the Forward zone and allow communication between zones.
Follow the same steps to create Firewall Zones lan2 and lan3.
lan2 zone settings:
- Name: Enter desired name
- Input: Accept
- Output: Accept
- Intra zone forward: Reject
- Covered networks: lan2
lan3 zone settings:
- Name: Enter desired name
- Input: Accept
- Output: Accept
- Intra zone forward: Reject
- Covered networks: lan3
Newly created firewall zones should look like this:
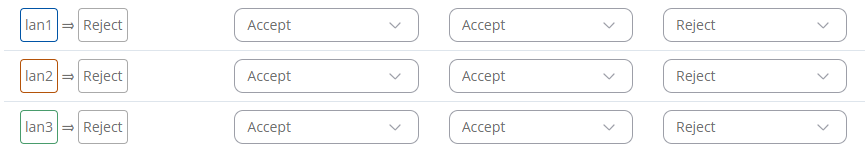
Inter-zone forwarding use examples
To customize communication between VLANs, we will need to edit Inter-zone forwarding rules. Navigate back to the firewall settings (Network -> Firewall -> Zones) and edit zones according to your needs.
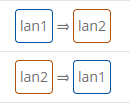
Example: lan1 wants to communicate only with lan2:
 |
|
|---|---|
|
lan1 settings:
No need to change settings for the lan2 zone |
If lan1 to lan2 communication is allowed, zone settings should look like this:
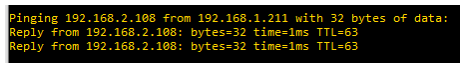
Testing the communication between lan1 and lan2:
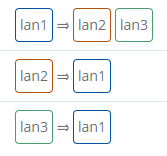
If we try to reach lan3 from lan1, where the forwarding is not set, the result would be this:
To reach lan3 from lan1, edit lan3 zone accordingly:
- allow forward to destination zones: lan1
- allow forward from source zones: lan1
Zone settings after these changes should look like this:
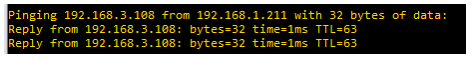
Now the communication between lan1 and lan3 works:
Using these examples as a base, you can allow / reject VLAN to VLAN communication between different VLANs according to your needs.