Tinc VPN configuration example WebUI: Difference between revisions
No edit summary |
|||
| (18 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
<p style="color:red">The information on this page is updated in accordance with the [https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads'''00.07.11.3'''] firmware version.</p> | <p style="color:red">The information on this page is updated in accordance with the [https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads'''00.07.11.3'''] firmware version.</p> | ||
__TOC__ | |||
==Introduction== | ==Introduction== | ||
| Line 13: | Line 13: | ||
*At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers and gateways. | *At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers and gateways. | ||
*(Optional) A second end device to configure and test remote LAN access | *(Optional) A second end device to configure and test remote LAN access | ||
*Matching configuration name instances should be used on VPN configuration instance and remote host configuration. | *'''Matching configuration name instances should be used on VPN configuration instance and remote host configuration.''' | ||
==Topology== | ==Topology== | ||
[[File: | [[File:Topo-Tunelis.png|border|class=tlt-border|center|1000x1000px]] | ||
This Tinc network configuration will connect two different devices with encrypted connection over the tunnel utilizing RSA keys and allowing LAN-to-LAN communication via the encrypted tunnel. | This Tinc network configuration will connect two different devices with encrypted connection over the tunnel utilizing RSA keys and allowing LAN-to-LAN communication via the encrypted tunnel. | ||
===Installing Tinc VPN package on your devices=== | ===Installing Tinc VPN package on your devices=== | ||
---- | ---- | ||
Open WebUI -> System -> Package Manager, select and install Tinc VPN package on both devices that are going to be using Tinc VPN to communicate. | Open '''WebUI -> System -> Package Manager''', select and install Tinc VPN package on both devices that are going to be using Tinc VPN to communicate. | ||
[[File:Tinc_VPN_WebUI_1.png.png|border|class=tlt-border|center|1000x1000px]] | [[File:Tinc_VPN_WebUI_1.png.png|border|class=tlt-border|center|1000x1000px]] | ||
===Generating VPN key pairs using router CLI=== | ===Generating VPN key pairs using router CLI=== | ||
---- | ---- | ||
| Line 36: | Line 37: | ||
====Generating Server Certificates==== | ====Generating Server Certificates==== | ||
---- | ---- | ||
Execute this command: '''tincd --generate-keys''' | Execute this command to generate keys: | ||
'''tincd --generate-keys''' | |||
Enter the key names: | Enter the key names: | ||
Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: '''Server.pem''' | |||
Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: '''Server.pem''' | |||
Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: '''pubServer.pem''' | Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: '''pubServer.pem''' | ||
[[File:Tinc_VPN_WebUI_Cert_1.png|border|class=tlt-border| | [[File:Tinc_VPN_WebUI_Cert_1.png|none|border|left|class=tlt-border|700x700px]] | ||
====Generating Client Certificates==== | ====Generating Client Certificates==== | ||
---- | ---- | ||
Execute this command: | Execute this command to generate keys: | ||
'''tincd --generate-keys''' | '''tincd --generate-keys''' | ||
Enter the key names: | Enter the key names: | ||
Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: '''Client.pem''' | Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: '''Client.pem''' | ||
Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: '''pubClient.pem''' | Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: '''pubClient.pem''' | ||
[[File:Tinc_VPN_WebUI_Cert_2.png|none|border|left|class=tlt-border|700x700px]] | |||
[[File:Tinc_VPN_WebUI_Cert_2.png|border|class=tlt-border | |||
====Exporting Certificates From The Router==== | ====Exporting Certificates From The Router==== | ||
| Line 72: | Line 68: | ||
Certificates should be displayed in the root directory; you can export them by using '''[https://wiki.teltonika-networks.com/view/Upload_%26_Download_Files_from_RutOS WinSCP]''' | Certificates should be displayed in the root directory; you can export them by using '''[https://wiki.teltonika-networks.com/view/Upload_%26_Download_Files_from_RutOS WinSCP]''' | ||
[[File: | [[File:Tinc_VPN_WebUI_Cert_3_1.png|none|border|left|class=tlt-border|800x800px]] | ||
==Router Configuration== | ==Router Configuration== | ||
| Line 158: | Line 154: | ||
This command should display if VPN session is established with the client and the server | This command should display if VPN session is established with the client and the server. | ||
====Server Session Testing==== | ====Server Session Testing==== | ||
| Line 173: | Line 169: | ||
---- | ---- | ||
[[File:Tinc_VPN_WebUI_14.png|border|class=tlt-border | [[File:Tinc_VPN_WebUI_14.png|none|border|left|class=tlt-border|500x500px]] | ||
====End Device 2 Testing==== | ====End Device 2 Testing==== | ||
---- | ---- | ||
[[File:Tinc_VPN_WebUI_15.png|border|class=tlt-border | [[File:Tinc_VPN_WebUI_15.png|none|border|left|class=tlt-border| 450x450px]] | ||
==External links== | |||
#https://wiki.teltonika-networks.com/view/Tinc_VPN_configuration_examples | |||
#https://www.tinc-vpn.org/docs/ | |||
Latest revision as of 12:30, 30 January 2025
The information on this page is updated in accordance with the 00.07.11.3 firmware version.
Introduction
Tinc is a Virtual Private Network (VPN) daemon that uses tunneling and encryption to create a secure private network between hosts on the Internet. Tinc is Free Software and licensed under the GNU General Public License version 2 or later. Because the VPN appears to the IP level network code as a normal network device, there is no need to adapt any existing software. This allows VPN sites to share information with each other over the Internet without exposing any information to others. This article provides an extensive configuration example with details on how to create a tunnel connection between two tinc instances, both of which are configured on Teltonika routers and gateways.
Configuration overview and prerequisites
Prerequisites:
- Two Teltonika routers or gateways of any type.
- At least one router must have a Public Static or Public Dynamic IP address
- At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers and gateways.
- (Optional) A second end device to configure and test remote LAN access
- Matching configuration name instances should be used on VPN configuration instance and remote host configuration.
Topology
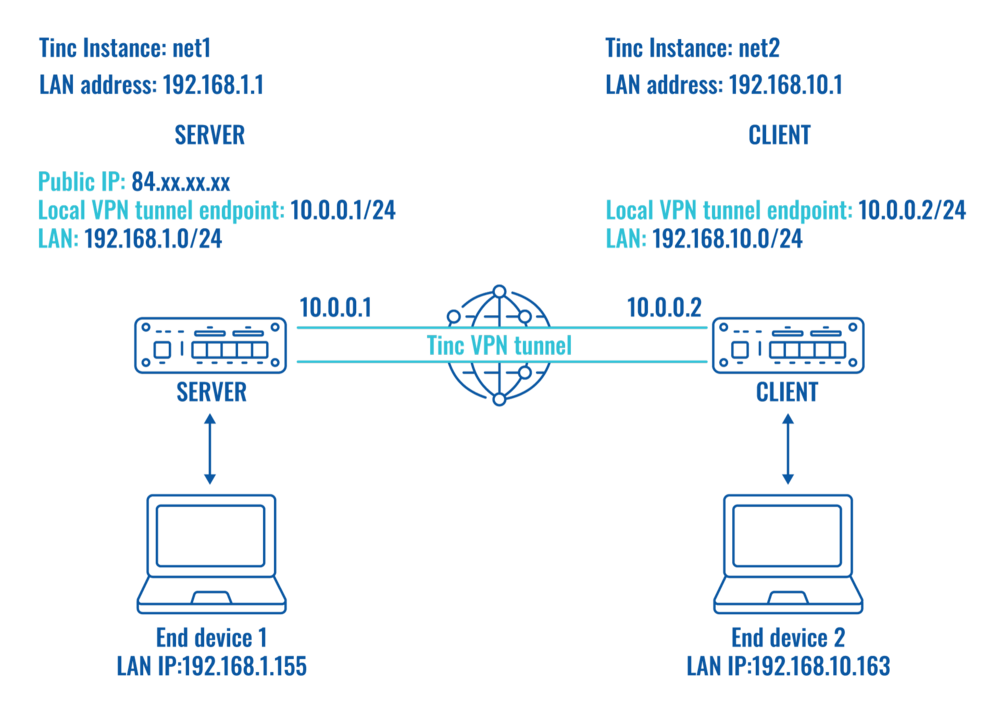
This Tinc network configuration will connect two different devices with encrypted connection over the tunnel utilizing RSA keys and allowing LAN-to-LAN communication via the encrypted tunnel.
Installing Tinc VPN package on your devices
Open WebUI -> System -> Package Manager, select and install Tinc VPN package on both devices that are going to be using Tinc VPN to communicate.
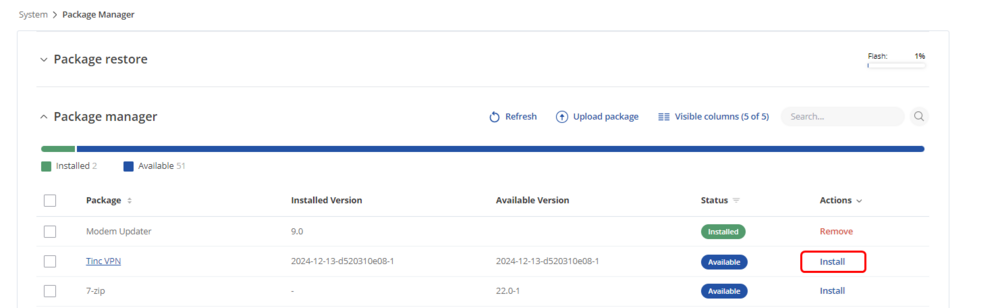
Generating VPN key pairs using router CLI
Generating certificates requires connecting to the routers' CLI.
Open WebUI -> System -> Maintenance -> CLI
How to connect to CLI
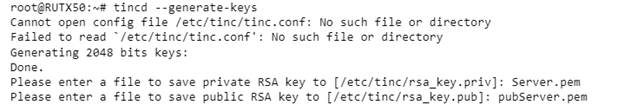
Generating Server Certificates
Execute this command to generate keys:
tincd --generate-keys
Enter the key names:
Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: Server.pem
Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: pubServer.pem
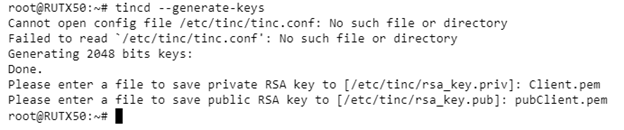
Generating Client Certificates
Execute this command to generate keys:
tincd --generate-keys
Enter the key names:
Please enter a file to save private RSA key to [/etc/tinc/rsa_key.priv]: Client.pem
Please enter a file to save public RSA key to [/etc/tinc/rsa_key.pub]: pubClient.pem
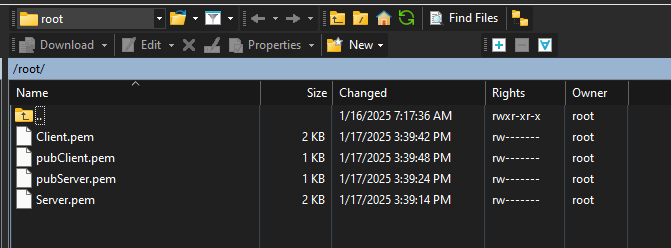
Exporting Certificates From The Router
Certificates should be displayed in the root directory; you can export them by using WinSCP
Router Configuration
Tinc VPN Server configuration
Open WebUI -> Services -> VPN -> Tinc, enter configuration name and create new instance.

General Setup configuration
After creating a new Tinc VPN tunnel instance in the new window under General Setup, configure the following:

- Enable: on
- Enter local tunnel endpoint IP: 10.0.0.1/24
- Enter subnet (Local LAN): 192.168.1.0/24
- Select private key: Server.pem
- Select public key: pubServer.pem
Hosts Configuration
Under the same tab after applying General Setup changes add new Hosts configuration instance

After creating new Tinc VPN Host instance in the new window under Tinc host net2 configure the following:

- Enable: on
- Enter subnet (Remote LAN): 192.168.10.0/24
- Select Public Key: pubClient.pem
Session Selection
In the General Setup Tinc VPN configuration window select the host that the server will establish a session with:

1. Select Host to Connect to: net1
Tinc VPN Client configuration
Open WebUI -> Services -> VPN -> Tinc, enter configuration name and create new instance.

General Setup configuration
After creating new Tinc VPN tunnel instance in the new window under General Setup configure the following:

- Enable: on
- Enter local tunnel endpoint IP: 10.0.0.2/24
- Enter subnet (Local LAN): 192.168.10.0/24
- Select private key: Client.pem
- Select public key: pubClient.pem
Hosts Configuration
Under the same tab after applying General Setup changes add new Hosts configuration instance

After creating new Tinc VPN Host instance in the new window under Tinc host net1 configure the following:

- Enable: on
- Enter Address (Server address): 84.xx.xx.xx
- Enter subnet (Remote LAN): 192.168.1.0/24
- Select Public Key: pubServer.pem
Session Selection
In the General Setup Tinc VPN configuration window select the host that client will establish session with:

1. Select Host to Connect to: net1
Testing if VPN session is established successfully
If all the steps previously mentioned were followed accordingly, you should have established a VPN session between the two network devices.
Open WebUI -> System -> Maintenance -> CLI
Execute the following command in CLI: logread | grep tinc
This command should display if VPN session is established with the client and the server.
Server Session Testing

Client Session Testing
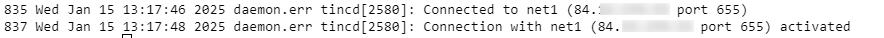
Additionally, you can test VPN connectivity by using the PING command if tunnel addresses and remote network devices are accessible via VPN from the end device.
End Device 1 Testing

End Device 2 Testing

