Domnev1: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
[ | <p style="color:red">The information on this page is updated in accordance with the [https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads'''00.07.09'''] firmware version .</p> | ||
__TOC__ | |||
==Summary== | |||
This article contains instructions on how to configure Port Foward functionality on most of the Teltonika Networks devices (with the exception of TAP and TSW series) | |||
<b>Port Forwarding</b> is the process of redirecting data packets to another destination. In Teltonika-Networks devices this is a feature of the iptables firewall, NAT table, PREROUTING chain. When a packet matches a port forwarding rule, the destination and/or port values are changed in the packet header. | |||
==Configuration overview & prerequisites== | |||
Before we begin, let's take a look at the configuration that we are attempting to achieve and the prerequisites that make it possible. | |||
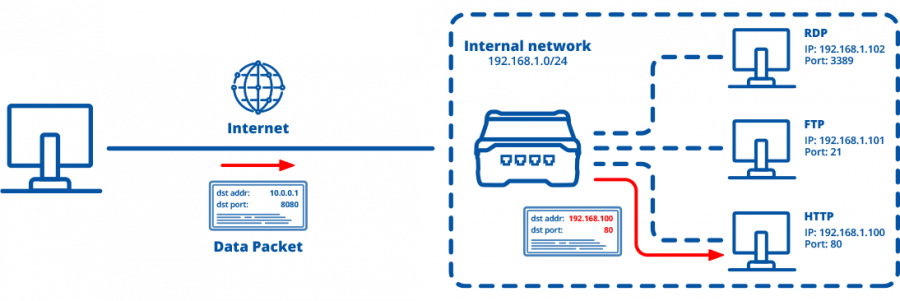
Configuring port forwarding on Teltonika devices is a simple process that involves just a few steps and can easily be replicated across various devices. The number of devices involved will depend on the specific use case, but the setup can be scaled seamlessly. In the example below, we will use the RUTX50 as the primary device with mobile internet connectivity, acting as the gateway and DHCP server. This setup allows us to remotely access third-party devices connected to RUTX50 over the internet. | |||
[[File:Networking_rutos_faq_port_forwarding_example_1_v1.png|900px]] | |||
'''Prerequisites''': | '''Prerequisites''': | ||
* | * A device from the RUT, RUTX, RUTM, RUTC or TRB series gateway; | ||
* | * A device which we will be reaching through port forward | ||
* | * A PC, Laptop, tablet or a smartphone | ||
* | * The Teltonika Networks device must have a SIM card with a Public Static or Public Dynamic IP address (more on IP address types '''[[Private and Public IP Addresses|here]]''') to make remote access possible | ||
* (Optional) | * (Optional) If the router's SIM card has a Public Dynamic IP address, you may want to additionally configure a '''[[Dynamic DNS]]''' hostname | ||
{{Template:Networking_rutos_manual_basic_advanced_webui_disclaimer | |||
| series = RUTX | |||
}} | |||
==Router configuration== | ==Router configuration== | ||
First, let's overview what configurations we'll be needing to set up: | |||
* Enable '''remote HTTP access''', so that the router can be reached from a remote location | |||
* Specify an '''Access Point Name''' ('''APN''') for the SIM card in use, so that the router will obtain a Public IP address | |||
* Configure a '''Port Forwarding''' rule that redirects all connections from one Port to the camera's IP address:Port | |||
* (Optional) Configure '''[[Dynamic DNS]]''' hostname | |||
=== | ===Enabling remote HTTP(S) access=== | ||
---- | ---- | ||
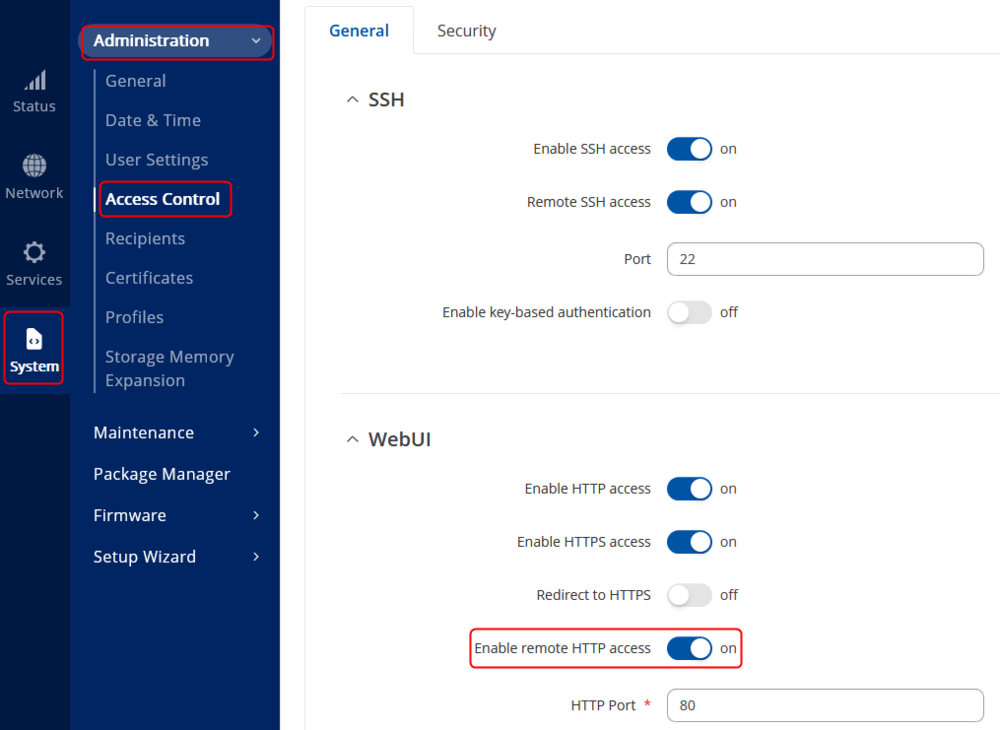
* To enable remote HTTP access, log in to the router's WebUI and navigate to the '''System → Administration → Access Control''' tab. Once in the '''Administration-Access Control''', find the '''Enable remote HTTP access''' field and put a check mark next to it: | |||
== | [[File:RutOS_remote_camera_access_7.8_1.png|border|class=tlt-border|alt=|1000px]] | ||
---- | ---- | ||
'''WARNING''': once you set up any type of remote access, your router becomes vulnerable to malicious attacks from unknown hosts throughout the Internet. It is highly recommended that once you enable remote access, you also change the router's default password to a string, custom password. You can change the router's password in '''[[RUT950_Administration#General|System → Administration → General → Administrator Password]]''' | |||
====Step 2: Set an APN==== | |||
---- | |||
'''Note:''' ''If you have a Public IP address already, you can skip this step.'' | |||
[[ | |||
- | |||
- | |||
---- | ---- | ||
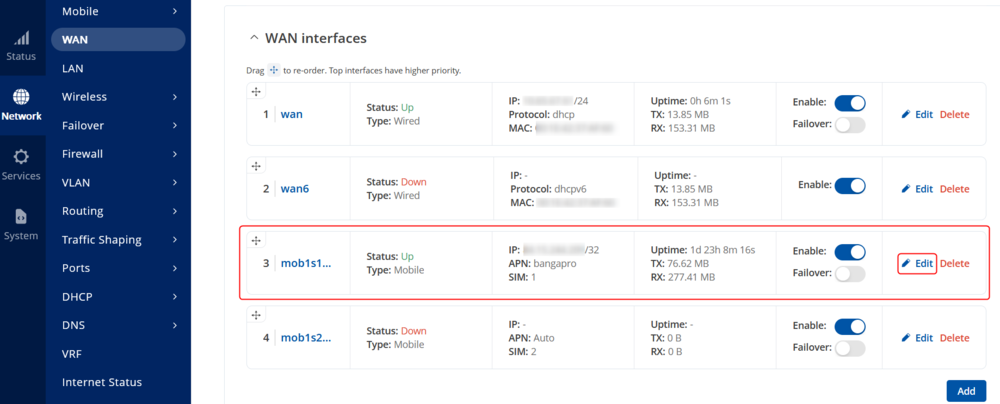
* To set the APN, while in the router's WebUI, navigate to the '''Network → WAN''': | |||
[[File:RutOS_remote_camera_access_7.8_2.png|border|class=tlt-border|alt=|1000x1000px]] | |||
---- | ---- | ||
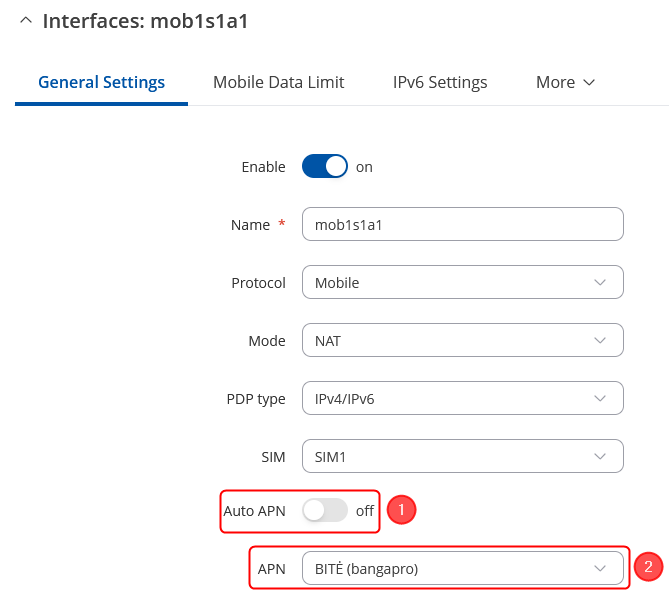
* Once in the '''WAN''' window, edit your mobile interface, find the '''APN''' field and enter you Internet Service Provider's APN: | |||
# '''Disable the Auto APN option''' | |||
# Choose the correct '''APN''', which gives out a public IP address (for more information about that contact your Internet Service Provider) | |||
[[File:RutOS_remote_camera_access_7.8_3.png|border|class=tlt-border]] | |||
[[File: | |||
* Additional notes on APN: | |||
** '''NOTE 1''': don't use the exact APN value as seen in the example above as it will not work with your SIM card. APN depends on your Internet Service Provider (ISP), therefore, your ISP should provide you with their APN or, in many case, you can find your ISP's APN with an online search. | |||
** '''NOTE 2''': furthermore, it should be noted that not all SIM cards support this functionality. Static or Dynamic Public IP addresses (obtained through APN) are a paid service and setting any APN value for a SIM card that doesn't support this service will most likely result in losing your data connection. If this is the case, it can be fixed by simply deleting the APN, but it also means that remote access through WAN IP will most likely not work on your SIM card. | |||
** '''NOTE 3''': in some cases the SIM card doesn't require an APN in order to obtain a Public IP address. If that is the case for you, simply check what your router's WAN IP address is - if it's already a Public IP address, then you don't need to set an APN. The easiest way to find what your WAN IP address is to log in to the router's WebUI and check the '''WAN''' widget in the '''Overview''' page. The WAN widget will be on the right side of the page, second widget from the top: | |||
[[File:WANpublic.png|alt=|border|center|frameless|660x660px]] | |||
===Step 3: Configure Port Forwarding=== | |||
=== | |||
---- | ---- | ||
* Navigate to the '''Port Forwards''' tab by going to '''Network → Firewall → Port Forwards''': | |||
* Scroll down to the bottom of the page and locate the '''New Port Forward Rule''' section. Set the following parameters: | |||
# Custom name for the port forward. | |||
# External port(s): '''8888''' (camera's HTTP port as set in the [[Hikvision:_remote_camera_access#Camera.27s_Web_User_Interface_.28WebUI.29|3.2]] section of this article) | |||
# Internal IP: '''192.168.1.64''' (camera's IP as set in the [[Hikvision:_remote_camera_access#Camera.27s_Web_User_Interface_.28WebUI.29|3.2]] section of this article) | |||
# Internal port(s): '''8888''' | |||
# Click on '''Add''' button. | |||
[[File:RutOS_remote_camera_access_7.8_4.png|border|class=tlt-border|alt=|1000px]] | |||
---- | ---- | ||
* If you plan viewing the camera's live stream via some sort of media player (for example, VLC), you should configure an additional Port Forwarding rule. Media players like VLC use the '''RTSP''' protocol. You can check the RTSP port in the camera's WebUI (as discussed in the [[Hikvision:_remote_camera_access#Camera.27s_Web_User_Interface_.28WebUI.29|3.2]] section of this article), but the RTSP default port is always '''554''' and there is no need to change it since by default the router doesn't use this port for any of its services (unless you use for some custom configuration. In that case, change the default RTSP port). So, once again make up a custom name for a new rule and set the following parameters: | |||
# Custom name for the port forward. | |||
# External port(s): '''554''' (camera's RTSP port) | |||
# Internal IP: '''192.168.1.64''' (camera's IP as set in the [[Hikvision:_remote_camera_access#Camera.27s_Web_User_Interface_.28WebUI.29|3.2]] section of this article) | |||
# Internal port(s): '''554''' | |||
# Click on '''Add''' button. | |||
[[File:RutOS_remote_camera_access_7.8_5.png|border|class=tlt-border|alt=|1000px]] | |||
[[File: | |||
---- | ---- | ||
* Don't forget to click '''Save & Apply''' after you've made the changes. After you have added the new rule, you will redirected to that rule's configuration window. Everything should already be in order so just click '''Save & Apply''' and your rule will be created. The new rule will appear at the bottom of the '''Port Forwarding Rules''' list, where you can check its status and make additional configurations if need be: | |||
[[File:RutOS_remote_camera_access_7.8_6.png|border|class=tlt-border|alt=|1000px]] | |||
'''FINAL NOTE''': as you can see, once you add the new rule, it is already enabled and ready for use. From this point no more additional configurations are required, as your remote camera monitoring configuration is fully set up. Unless you want to set up Dynamic DNS for your router, you can skip to the '''[[#Testing_the_set_up|Testing the set up]]''' part of this guide. | |||
===(Optional) Step 4: Configure Dynamic DNS=== | |||
---- | ---- | ||
'''[[Dynamic DNS]]''' ('''DDNS''' or '''DynDNS''') is a method of automatically updating a name server in the Domain Name System (DNS), often in real time, with the active DDNS configuration of its configured hostnames, addresses or other information. | |||
Dynamic DNS configuration is optional here, but it is recommended if your SIM card has a Dynamic Public IP address. You can find more information on what a Dynamic Public IP address is '''[[Private_and_Public_IP_Addresses#Dynamic_IP_address|here]]''', but in short it means that your WAN IP address is Dynamic and, therefore, it may change over time (usually when disconnecting/reconnecting or re-registering to a network). Dynamic DNS assigns a hostname to your IP address and constantly updates that hostname, which means that even if your IP address changes, DDNS will assign the same hostname to your new IP, making your router reachable via the same hostname at any time. | |||
You must use an external DDNS service to create a hostname and assign it to your IP. RUT routers support many such services. You can find a complete list of supported DDNS services in the '''Services → Dynamic DNS''' section of the router's WebUI. You can also find guides on how to configure some of these services in our wiki: | |||
[[ | * '''[[Dynu.com DDNS configuration]]''' | ||
* '''[[Dnsdynamic.org DDNS configuration]]''' | |||
* '''[[Noip.com DDNS configuration]]''' | |||
The guides contain information on how to configure both the router and the third party service. Choose one according to your liking. | |||
==Testing the set up== | |||
==See Also== | |||
Most Teltonika-Networks devices have the port forwarding feature. Configuration is described in the user manual Firewall page for each device. | |||
Revision as of 14:53, 4 September 2024
The information on this page is updated in accordance with the 00.07.09 firmware version .
Summary
This article contains instructions on how to configure Port Foward functionality on most of the Teltonika Networks devices (with the exception of TAP and TSW series)
Port Forwarding is the process of redirecting data packets to another destination. In Teltonika-Networks devices this is a feature of the iptables firewall, NAT table, PREROUTING chain. When a packet matches a port forwarding rule, the destination and/or port values are changed in the packet header.
Configuration overview & prerequisites
Before we begin, let's take a look at the configuration that we are attempting to achieve and the prerequisites that make it possible.
Configuring port forwarding on Teltonika devices is a simple process that involves just a few steps and can easily be replicated across various devices. The number of devices involved will depend on the specific use case, but the setup can be scaled seamlessly. In the example below, we will use the RUTX50 as the primary device with mobile internet connectivity, acting as the gateway and DHCP server. This setup allows us to remotely access third-party devices connected to RUTX50 over the internet.
Prerequisites:
- A device from the RUT, RUTX, RUTM, RUTC or TRB series gateway;
- A device which we will be reaching through port forward
- A PC, Laptop, tablet or a smartphone
- The Teltonika Networks device must have a SIM card with a Public Static or Public Dynamic IP address (more on IP address types here) to make remote access possible
- (Optional) If the router's SIM card has a Public Dynamic IP address, you may want to additionally configure a Dynamic DNS hostname
If you're having trouble finding this page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Advanced" button, located at the top of the WebUI.
Router configuration
First, let's overview what configurations we'll be needing to set up:
- Enable remote HTTP access, so that the router can be reached from a remote location
- Specify an Access Point Name (APN) for the SIM card in use, so that the router will obtain a Public IP address
- Configure a Port Forwarding rule that redirects all connections from one Port to the camera's IP address:Port
- (Optional) Configure Dynamic DNS hostname
Enabling remote HTTP(S) access
- To enable remote HTTP access, log in to the router's WebUI and navigate to the System → Administration → Access Control tab. Once in the Administration-Access Control, find the Enable remote HTTP access field and put a check mark next to it:
WARNING: once you set up any type of remote access, your router becomes vulnerable to malicious attacks from unknown hosts throughout the Internet. It is highly recommended that once you enable remote access, you also change the router's default password to a string, custom password. You can change the router's password in System → Administration → General → Administrator Password
Step 2: Set an APN
Note: If you have a Public IP address already, you can skip this step.
- To set the APN, while in the router's WebUI, navigate to the Network → WAN:
- Once in the WAN window, edit your mobile interface, find the APN field and enter you Internet Service Provider's APN:
- Disable the Auto APN option
- Choose the correct APN, which gives out a public IP address (for more information about that contact your Internet Service Provider)
- Additional notes on APN:
- NOTE 1: don't use the exact APN value as seen in the example above as it will not work with your SIM card. APN depends on your Internet Service Provider (ISP), therefore, your ISP should provide you with their APN or, in many case, you can find your ISP's APN with an online search.
- NOTE 2: furthermore, it should be noted that not all SIM cards support this functionality. Static or Dynamic Public IP addresses (obtained through APN) are a paid service and setting any APN value for a SIM card that doesn't support this service will most likely result in losing your data connection. If this is the case, it can be fixed by simply deleting the APN, but it also means that remote access through WAN IP will most likely not work on your SIM card.
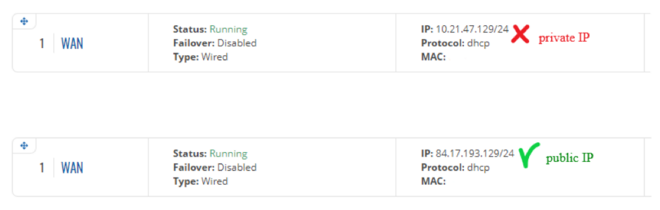
- NOTE 3: in some cases the SIM card doesn't require an APN in order to obtain a Public IP address. If that is the case for you, simply check what your router's WAN IP address is - if it's already a Public IP address, then you don't need to set an APN. The easiest way to find what your WAN IP address is to log in to the router's WebUI and check the WAN widget in the Overview page. The WAN widget will be on the right side of the page, second widget from the top:
Step 3: Configure Port Forwarding
- Navigate to the Port Forwards tab by going to Network → Firewall → Port Forwards:
- Scroll down to the bottom of the page and locate the New Port Forward Rule section. Set the following parameters:
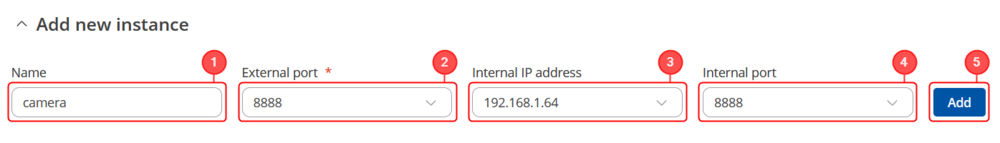
- Custom name for the port forward.
- External port(s): 8888 (camera's HTTP port as set in the 3.2 section of this article)
- Internal IP: 192.168.1.64 (camera's IP as set in the 3.2 section of this article)
- Internal port(s): 8888
- Click on Add button.
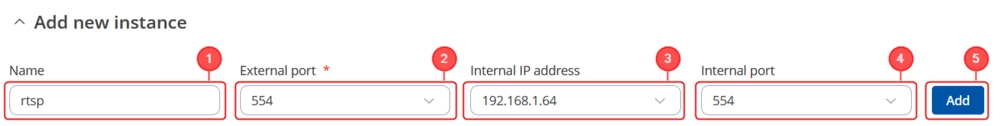
- If you plan viewing the camera's live stream via some sort of media player (for example, VLC), you should configure an additional Port Forwarding rule. Media players like VLC use the RTSP protocol. You can check the RTSP port in the camera's WebUI (as discussed in the 3.2 section of this article), but the RTSP default port is always 554 and there is no need to change it since by default the router doesn't use this port for any of its services (unless you use for some custom configuration. In that case, change the default RTSP port). So, once again make up a custom name for a new rule and set the following parameters:
- Custom name for the port forward.
- External port(s): 554 (camera's RTSP port)
- Internal IP: 192.168.1.64 (camera's IP as set in the 3.2 section of this article)
- Internal port(s): 554
- Click on Add button.
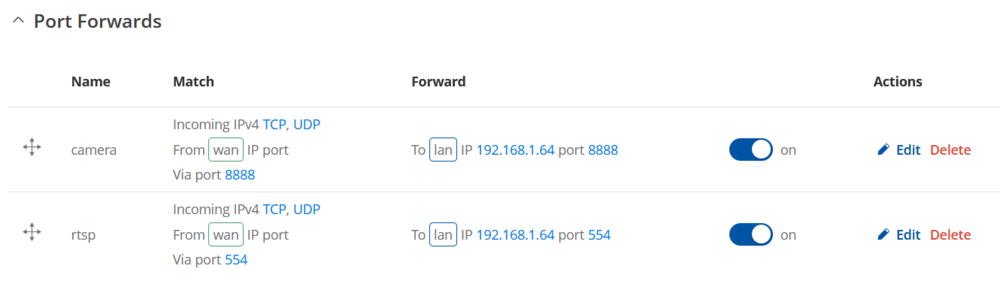
- Don't forget to click Save & Apply after you've made the changes. After you have added the new rule, you will redirected to that rule's configuration window. Everything should already be in order so just click Save & Apply and your rule will be created. The new rule will appear at the bottom of the Port Forwarding Rules list, where you can check its status and make additional configurations if need be:
FINAL NOTE: as you can see, once you add the new rule, it is already enabled and ready for use. From this point no more additional configurations are required, as your remote camera monitoring configuration is fully set up. Unless you want to set up Dynamic DNS for your router, you can skip to the Testing the set up part of this guide.
(Optional) Step 4: Configure Dynamic DNS
Dynamic DNS (DDNS or DynDNS) is a method of automatically updating a name server in the Domain Name System (DNS), often in real time, with the active DDNS configuration of its configured hostnames, addresses or other information.
Dynamic DNS configuration is optional here, but it is recommended if your SIM card has a Dynamic Public IP address. You can find more information on what a Dynamic Public IP address is here, but in short it means that your WAN IP address is Dynamic and, therefore, it may change over time (usually when disconnecting/reconnecting or re-registering to a network). Dynamic DNS assigns a hostname to your IP address and constantly updates that hostname, which means that even if your IP address changes, DDNS will assign the same hostname to your new IP, making your router reachable via the same hostname at any time.
You must use an external DDNS service to create a hostname and assign it to your IP. RUT routers support many such services. You can find a complete list of supported DDNS services in the Services → Dynamic DNS section of the router's WebUI. You can also find guides on how to configure some of these services in our wiki:
The guides contain information on how to configure both the router and the third party service. Choose one according to your liking.
Testing the set up
See Also
Most Teltonika-Networks devices have the port forwarding feature. Configuration is described in the user manual Firewall page for each device.