Difference between revisions of "IPSec Tunnel w/CA Certs Configuration"
ChaseHarler (talk | contribs) |
|||
| Line 1: | Line 1: | ||
| − | [ | + | <p style="color:red">The information in this page is updated in accordance with [https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads'''00.07.08'''] firmware version.</p> |
==Introduction== | ==Introduction== | ||
| − | In computing, '''Internet Protocol Security''' ('''IPsec''') is a secure network protocol suite of IPv4 that authenticates and encrypts the packets of data sent over an IPv4 network. IPsec includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPsec can protect data flows between a pair of hosts (host-to-host), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host). Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data | + | In computing, '''Internet Protocol Security''' ('''IPsec''') is a secure network protocol suite of IPv4 that authenticates and encrypts the packets of data sent over an IPv4 network. IPsec includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPsec can protect data flows between a pair of hosts (host-to-host), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host). Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data origin authentication, data integrity, data confidentiality (encryption), and replay protection. |
| − | This article provides an extensive configuration example with details on how to create a tunnel connection authenticating with X.509 Certs between two IPsec instances, both of which configured on RUTxxx routers. | + | This article provides an extensive configuration example with details on how to create a tunnel connection authenticating with X.509 Certs between two IPsec instances, both of which are configured on RUTxxx routers. |
==Configuration overview and prerequisites== | ==Configuration overview and prerequisites== | ||
| Line 12: | Line 12: | ||
'''Prerequisites''': | '''Prerequisites''': | ||
| − | * Two RUTxxx routers of any type | + | * Two RUTxxx routers of any type; |
| − | * Both RUTxxx routers must be accessible from each other's WAN connection | + | * One RUTxxx router with public IP address; |
| − | * Firmware for the devices must be 00.07.xx.x or above. This is in part to make sure the StrongSwan service is U5.9.6 | + | * Both RUTxxx routers must be accessible from each other's WAN connection; |
| − | * An end device (PC, Laptop) for configuration | + | * Firmware for the devices must be 00.07.xx.x or above. This is in part to make sure the StrongSwan service is at least version U5.9.6; |
| − | * (Optional) A second end device to test remote LAN access | + | * An end device (PC, Laptop) for configuration; |
| + | * (Optional) A second end device to test remote LAN access; | ||
---- | ---- | ||
| Line 27: | Line 28: | ||
We will start our configuration with RUT1. | We will start our configuration with RUT1. | ||
| − | + | To generate certificates via router, you can refer to this link, whereas we will cover: [https://wiki.teltonika-networks.com/view/RUTX11_Administration#Certificates Generating certificate via router] | |
| − | === | + | ===IPsec RUT1 Config=== |
---- | ---- | ||
| + | * Make sure that you have your certificates generated both for '''RUT1''' and '''RUT2''' routers. | ||
| + | * Login to the router's WebUI and go to '''System → Services → VPN -> IPsec''' | ||
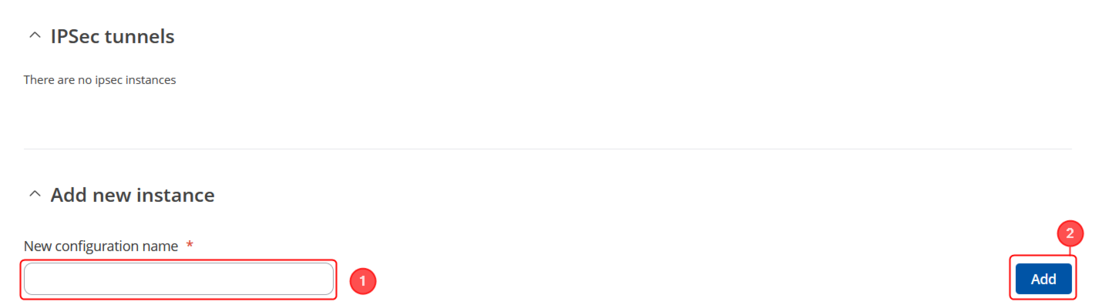
| + | * Add a new instance with your desired name, in my case I will be using '''RUT1''' | ||
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec.png|border|center|class=tlt-border|1102px]] | |
| − | ==== | + | Start by configuring the '''RUT''' device. Login to the WebUI, navigate to '''Services → VPN → IPsec and add a new IPsec instance.''' Configure everything as follows. |
| + | '''Note:''' ''Not specified fields can be left as is or changed according to your needs.'' | ||
| + | ====Instance configuration==== | ||
| + | ---- | ||
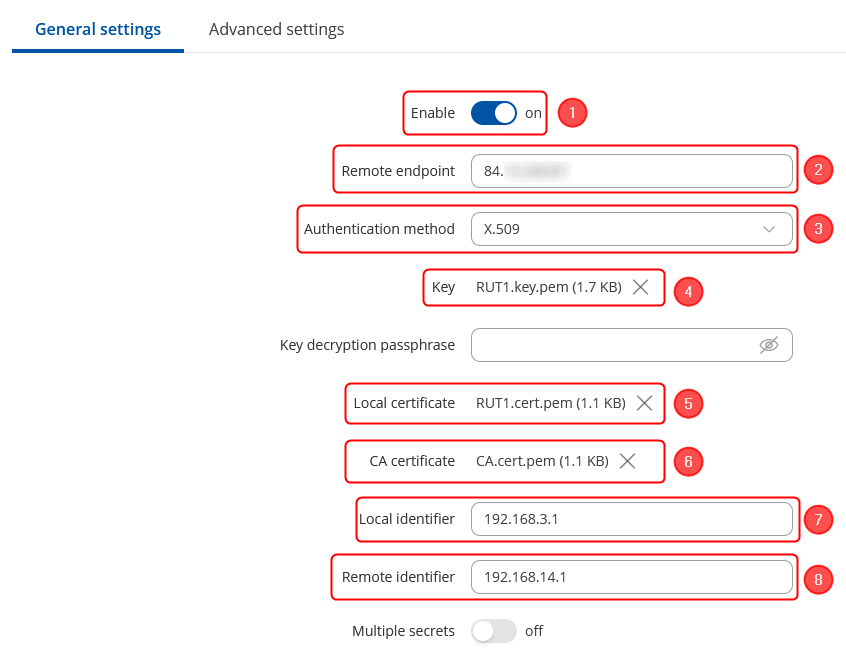
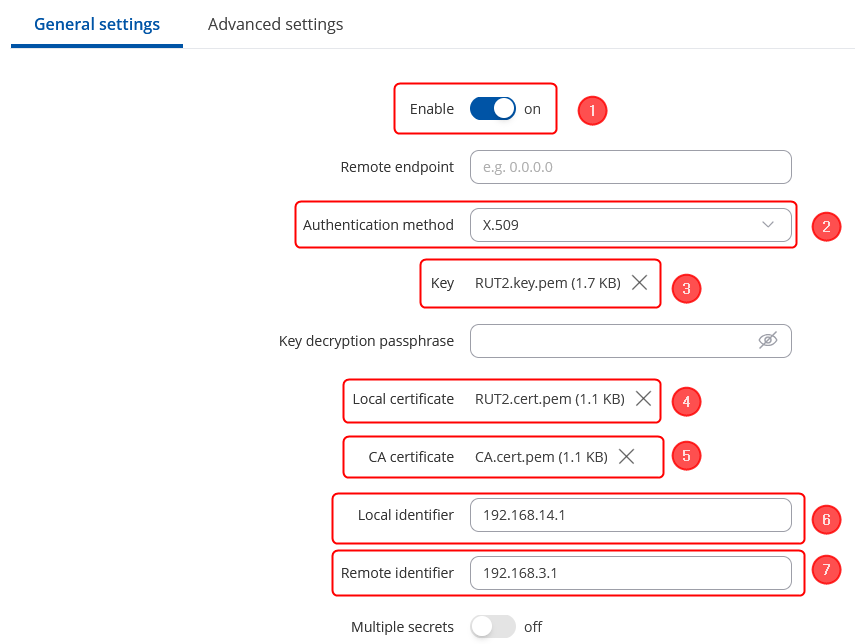
| + | Make the following changes: | ||
| + | # '''''Enable''''' instance; | ||
| + | # Remote endpoint - '''''RUT2 WAN IP;''''' | ||
| + | # Authentication method - '''''X.509;''''' | ||
| + | # Key - the '''''RUT1.key.pem''''' that you have generated from certificates; | ||
| + | # Local certificate - the '''''RUT1.cert.pem''''' that you have generated from certificates; | ||
| + | # CA certificate - the '''''CA.cert.pem''''' that you have generated from certificates; | ||
| + | # Local identifier – '''''RUT1 LAN IP, which is 192.168.3.1 in this case;''''' | ||
| + | # Remote identifier – '''''RUT2 LAN IP, which is 192.168.14.1 in this case''''' | ||
| + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_general_instnace.png|border|class=tlt-border|center]] | ||
| + | ---- | ||
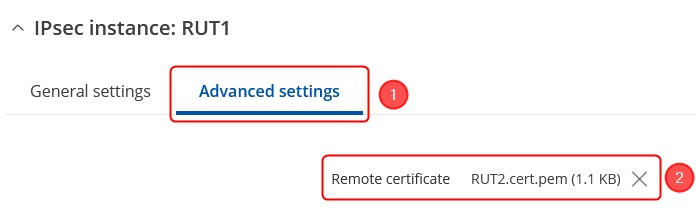
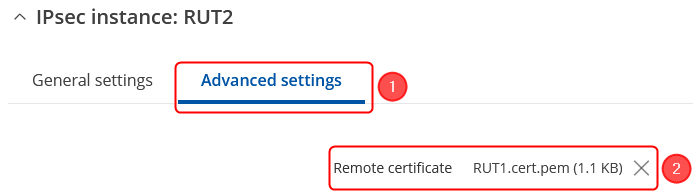
| + | We will need to add RUT2 certificate in the '''Advanced settings''': | ||
| + | # Click on '''Advanced settings''' in the IPsec instance section; | ||
| + | # Remote certificate - the '''''RUT2.cert.pem''''' that you have generated from certificates; | ||
| + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_general_instnace_advanced.png|border|class=tlt-border|center]] | ||
| + | ====Connection general section configuration==== | ||
---- | ---- | ||
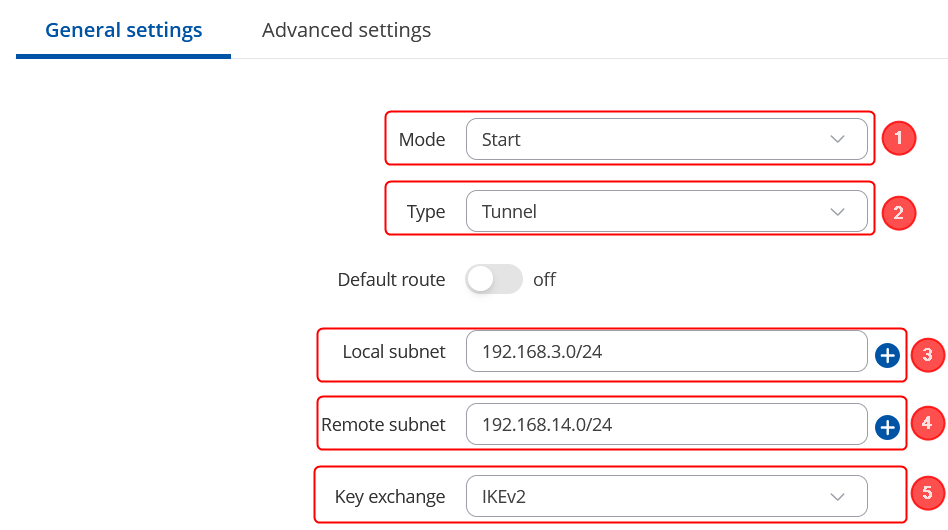
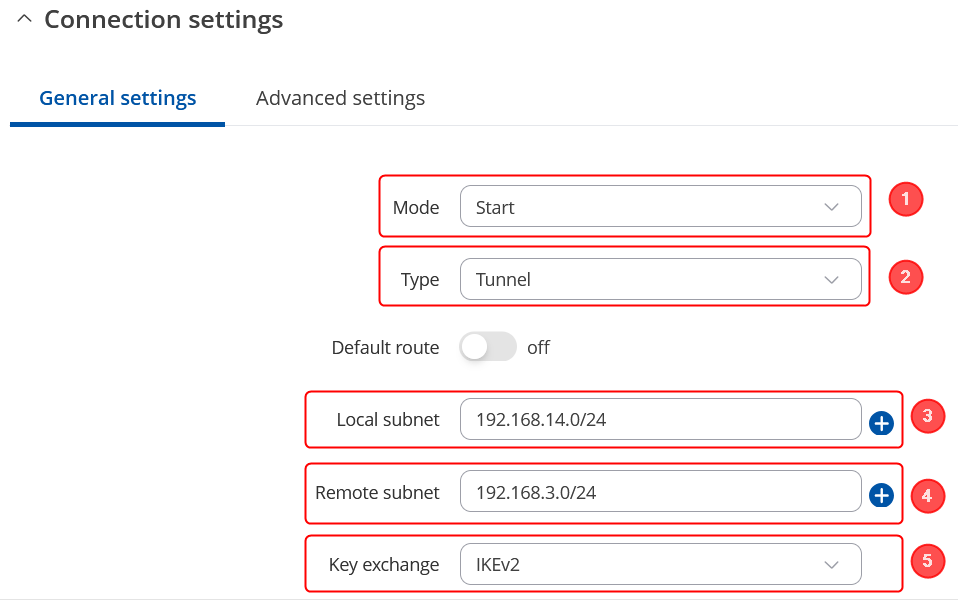
| + | Make the following changes: | ||
| + | # Mode - '''''Start;''''' | ||
| + | # Type - '''''Tunnel;''''' | ||
| + | # Local subnet – '''''192.168.3.0/24;''''' | ||
| + | # Remote subnet – '''''192.168.14.0/24;''''' | ||
| + | # Key exchange - '''''IKEv2;''''' | ||
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection.png|border|class=tlt-border|center]] | |
| − | + | ====Connection advanced section configuration==== | |
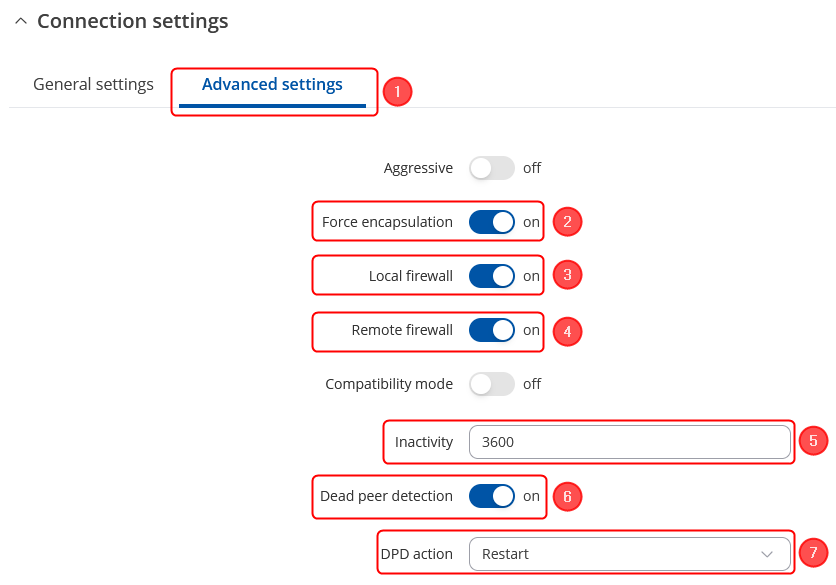
| − | + | ---- | |
| − | + | Make the following changes: | |
| − | + | # Open '''Advanced settings'''; | |
| − | + | # '''''Enable Force encapsulation'''''; | |
| − | + | # '''''Enable Local firewall'''''; | |
| − | + | # '''''Enable Remote firewall'''''; | |
| − | + | # Inactivity: '''''3600''''' - Defines the timeout interval, after which the connection is closed; | |
| − | + | # '''''Enable Dead peer detection'''''; | |
| − | + | # DPD action – '''''Restart'''''; | |
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection_advanced.png|border|class=tlt-border|center]] | |
| − | + | ====Proposal configuration==== | |
| − | + | '''Important:''' Both the RUT1 and RUT2 Encryptions must match in order for this configuration to work. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
---- | ---- | ||
| + | '''Note:''' ''This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.'' | ||
| − | + | Make the following changes: | |
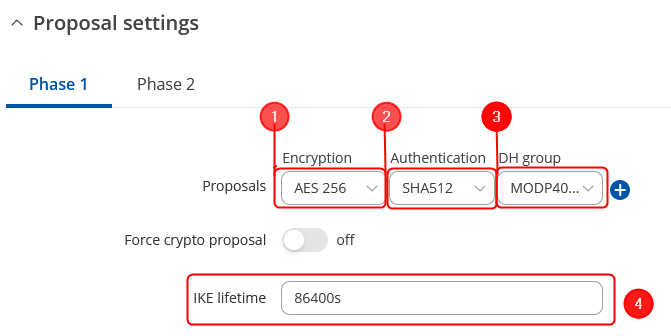
| − | + | <table class="nd-othertables_2"> | |
| − | + | <tr> | |
| − | + | <th width=330; style="border-bottom: 1px solid white;></th> | |
| − | + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:Networking_webui_manual_IPsec_configuration_proposal_phase1_settings_v1.png|border|class=tlt-border|671x336px|center]]</th> | |
| − | + | </tr> | |
| − | + | <tr> | |
| − | + | <td style="border-bottom: 4px solid white> | |
| − | + | # Encryption - '''''AES256;''''' | |
| − | + | # Authentication - '''''SHA512;''''' | |
| − | + | # DH group - '''''MODP4096;''''' | |
| − | + | # IKE lifetime - '''86400s'''. | |
| − | + | </td> | |
| − | + | </tr> | |
| − | + | </table> | |
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | < | ||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
---- | ---- | ||
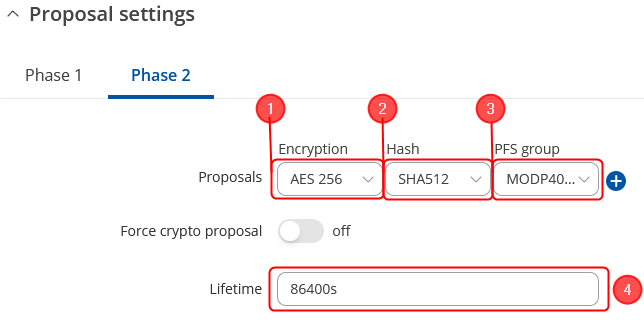
| + | <table class="nd-othertables_2"> | ||
| + | <tr> | ||
| + | <th width=330; style="border-bottom: 1px solid white;></th> | ||
| + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:Networking_webui_manual_IPsec_configuration_proposal_phase2_settings_v1.png|border|class=tlt-border|644x331px|center]]</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td style="border-bottom: 4px solid white> | ||
| + | # Encryption - '''''AES256;''''' | ||
| + | # Authentication - '''''SHA512;''''' | ||
| + | # PFS group - '''''MODP4096;''''' | ||
| + | # Lifetime – '''''86400s;''''' | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | ===IPsec RUT2 Config=== | |
| − | |||
| − | |||
| − | |||
| − | === | ||
---- | ---- | ||
| − | + | * Make sure that you have your certificates generated both for '''RUT1''' and '''RUT2''' routers. | |
* Login to the router's WebUI and go to '''System → Services → VPN -> IPsec''' | * Login to the router's WebUI and go to '''System → Services → VPN -> IPsec''' | ||
| − | * Add a new instance | + | * Add a new instance with your desired name, in my case I will be using '''RUT2''' |
| − | |||
| − | [[File: | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec.png|border|center|class=tlt-border|1102px]] |
| − | + | Start by configuring the '''RUT''' device. Login to the WebUI, navigate to '''Services → VPN → IPsec and add a new IPsec instance.''' Configure everything as follows. | |
| − | + | '''Note:''' ''Not specified fields can be left as is or changed according to your needs.'' | |
| − | + | ====Instance configuration==== | |
| − | + | ---- | |
| + | Make the following changes: | ||
| + | # '''''Enable''''' instance; | ||
| + | # Authentication method - '''''X.509;''''' | ||
| + | # Key - the '''''RUT2.key.pem''''' that you have generated from certificates; | ||
| + | # Local certificate - the '''''RUT2.cert.pem''''' that you have generated from certificates; | ||
| + | # CA certificate - the '''''CA.cert.pem''''' that you have generated from certificates; | ||
| + | # Local identifier – '''''RUT2 LAN IP, which is 192.168.14.1 in this case;''''' | ||
| + | # Remote identifier – '''''RUT1 LAN IP, which is 192.168.3.1 in this case''''' | ||
| + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection_rut2.png|border|class=tlt-border|center]] | ||
| + | ---- | ||
| + | We will need to add RUT2 certificate in the '''Advanced settings''': | ||
| + | # Click on '''Advanced settings''' in the IPsec instance section; | ||
| + | # Remote certificate - the '''''RUT1.cert.pem''''' that you have generated from certificates; | ||
| + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection_advanced_rut2.png|border|class=tlt-border|center]] | ||
| + | ====Connection general section configuration==== | ||
| + | ---- | ||
| + | Make the following changes: | ||
| + | # Mode - '''''Start;''''' | ||
| + | # Type - '''''Tunnel;''''' | ||
| + | # Local subnet – '''''192.168.14.0/24;''''' | ||
| + | # Remote subnet – '''''192.168.3.0/24;''''' | ||
| + | # Key exchange - '''''IKEv2;''''' | ||
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection_rut2_general.png|border|class=tlt-border|center]] | |
| − | + | ====Connection advanced section configuration==== | |
| + | ---- | ||
| + | Make the following changes: | ||
| + | # Open '''Advanced settings'''; | ||
| + | # '''''Enable Force encapsulation'''''; | ||
| + | # '''''Enable Local firewall'''''; | ||
| + | # '''''Enable Remote firewall'''''; | ||
| + | # Inactivity: '''''3600''''' - Defines the timeout interval, after which the connection is closed; | ||
| + | # '''''Enable Dead peer detection'''''; | ||
| + | # DPD action – '''''Restart'''''; | ||
| + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_add_ipsec_config_connection_advanced.png|border|class=tlt-border|center]] | ||
| + | ====Proposal configuration==== | ||
| + | '''Important:''' Both the RUT1 and RUT2 Encryptions must match in order for this configuration to work. | ||
| + | ---- | ||
| + | '''Note:''' ''This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.'' | ||
| − | - | + | Make the following changes: |
| + | <table class="nd-othertables_2"> | ||
| + | <tr> | ||
| + | <th width=330; style="border-bottom: 1px solid white;></th> | ||
| + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:Networking_webui_manual_IPsec_configuration_proposal_phase1_settings_v1.png|border|class=tlt-border|671x336px|center]]</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td style="border-bottom: 4px solid white> | ||
| + | # Encryption - '''''AES256;''''' | ||
| + | # Authentication - '''''SHA512;''''' | ||
| + | # DH group - '''''MODP4096;''''' | ||
| + | # IKE lifetime - '''86400s'''. | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
---- | ---- | ||
| + | <table class="nd-othertables_2"> | ||
| + | <tr> | ||
| + | <th width=330; style="border-bottom: 1px solid white;></th> | ||
| + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:Networking_webui_manual_IPsec_configuration_proposal_phase2_settings_v1.png|border|class=tlt-border|644x331px|center]]</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td style="border-bottom: 4px solid white> | ||
| + | # Encryption - '''''AES256;''''' | ||
| + | # Authentication - '''''SHA512;''''' | ||
| + | # PFS group - '''''MODP4096;''''' | ||
| + | # Lifetime – '''''86400s;''''' | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
| − | + | ==Testing the configuration== | |
| − | + | If you have followed all the above steps, your configuration should be finished. But as with any other configuration, it is always wise to test the setup in order to make sure that it works properly. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
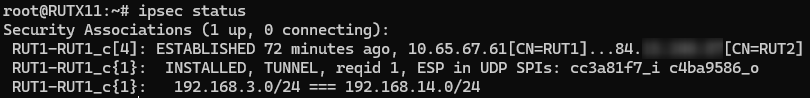
| − | + | Using the <code><span class="highlight">'''ipsec status'''</span></code> or we can use <code><span class="highlight">'''ipsec statusall'''</span></code> command for a more verbose output. With these commands we can see that the IPsec tunnel is successfully established on RUTxxx router. The command output on a '''RUT1''' device: | |
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_ipsec_status.png|border|class=tlt-border|center]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
---- | ---- | ||
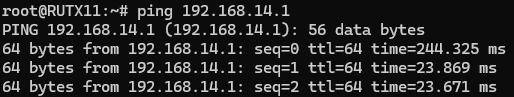
| − | + | Also, we can try to ping the RUT2 device by executing this command <code><span class="highlight" >'''ping 192.168.14.1'''</span></code>, by which you should get a response if the IPsec tunnel has been established properly. | |
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_ipsec_ping_rut1_to_rut2.png|border|class=tlt-border|center]] | |
---- | ---- | ||
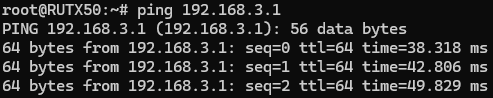
| − | + | To check if IPsec tunnel is working properly from '''RUT2''', we can try pinging our '''RUT1''' device by using this command in command line interface on RUT2<code><span class="highlight" >'''ping 192.168.3.1'''</span></code>: | |
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_ipsec_ping_rut2_to_rut1.png|border|class=tlt-border|center]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | < | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
---- | ---- | ||
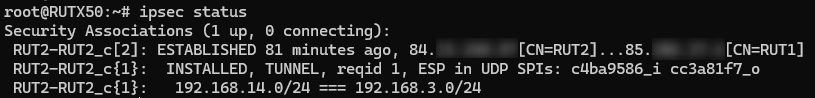
| − | + | Also we can check it by executing the <code><span class="highlight">'''ipsec status'''</span></code> or we can use <code><span class="highlight">'''ipsec statusall'''</span></code> command for a more verbose output. With these commands we can see that the IPsec tunnel is successfully established on RUTxxx router. The command output on a '''RUT2''' device: | |
| − | + | [[File:RutOS_IPsec_tunnel_with_certificates_7.8_ipsec_status_rut2.png|border|class=tlt-border|center]] | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
Latest revision as of 14:26, 6 August 2024
The information in this page is updated in accordance with 00.07.08 firmware version.
Introduction
In computing, Internet Protocol Security (IPsec) is a secure network protocol suite of IPv4 that authenticates and encrypts the packets of data sent over an IPv4 network. IPsec includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPsec can protect data flows between a pair of hosts (host-to-host), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host). Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data origin authentication, data integrity, data confidentiality (encryption), and replay protection.
This article provides an extensive configuration example with details on how to create a tunnel connection authenticating with X.509 Certs between two IPsec instances, both of which are configured on RUTxxx routers.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- Two RUTxxx routers of any type;
- One RUTxxx router with public IP address;
- Both RUTxxx routers must be accessible from each other's WAN connection;
- Firmware for the devices must be 00.07.xx.x or above. This is in part to make sure the StrongSwan service is at least version U5.9.6;
- An end device (PC, Laptop) for configuration;
- (Optional) A second end device to test remote LAN access;
The figure above depicts two RUTxxx routers (RUT1 and RUT2) connected by an IPsec tunnel via their WAN interfaces.
Router configuration
We will start our configuration with RUT1.
To generate certificates via router, you can refer to this link, whereas we will cover: Generating certificate via router
IPsec RUT1 Config
- Make sure that you have your certificates generated both for RUT1 and RUT2 routers.
- Login to the router's WebUI and go to System → Services → VPN -> IPsec
- Add a new instance with your desired name, in my case I will be using RUT1
Start by configuring the RUT device. Login to the WebUI, navigate to Services → VPN → IPsec and add a new IPsec instance. Configure everything as follows. Note: Not specified fields can be left as is or changed according to your needs.
Instance configuration
Make the following changes:
- Enable instance;
- Remote endpoint - RUT2 WAN IP;
- Authentication method - X.509;
- Key - the RUT1.key.pem that you have generated from certificates;
- Local certificate - the RUT1.cert.pem that you have generated from certificates;
- CA certificate - the CA.cert.pem that you have generated from certificates;
- Local identifier – RUT1 LAN IP, which is 192.168.3.1 in this case;
- Remote identifier – RUT2 LAN IP, which is 192.168.14.1 in this case
We will need to add RUT2 certificate in the Advanced settings:
- Click on Advanced settings in the IPsec instance section;
- Remote certificate - the RUT2.cert.pem that you have generated from certificates;
Connection general section configuration
Make the following changes:
- Mode - Start;
- Type - Tunnel;
- Local subnet – 192.168.3.0/24;
- Remote subnet – 192.168.14.0/24;
- Key exchange - IKEv2;
Connection advanced section configuration
Make the following changes:
- Open Advanced settings;
- Enable Force encapsulation;
- Enable Local firewall;
- Enable Remote firewall;
- Inactivity: 3600 - Defines the timeout interval, after which the connection is closed;
- Enable Dead peer detection;
- DPD action – Restart;
Proposal configuration
Important: Both the RUT1 and RUT2 Encryptions must match in order for this configuration to work.
Note: This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.
Make the following changes:
|
|
IPsec RUT2 Config
- Make sure that you have your certificates generated both for RUT1 and RUT2 routers.
- Login to the router's WebUI and go to System → Services → VPN -> IPsec
- Add a new instance with your desired name, in my case I will be using RUT2
Start by configuring the RUT device. Login to the WebUI, navigate to Services → VPN → IPsec and add a new IPsec instance. Configure everything as follows. Note: Not specified fields can be left as is or changed according to your needs.
Instance configuration
Make the following changes:
- Enable instance;
- Authentication method - X.509;
- Key - the RUT2.key.pem that you have generated from certificates;
- Local certificate - the RUT2.cert.pem that you have generated from certificates;
- CA certificate - the CA.cert.pem that you have generated from certificates;
- Local identifier – RUT2 LAN IP, which is 192.168.14.1 in this case;
- Remote identifier – RUT1 LAN IP, which is 192.168.3.1 in this case
We will need to add RUT2 certificate in the Advanced settings:
- Click on Advanced settings in the IPsec instance section;
- Remote certificate - the RUT1.cert.pem that you have generated from certificates;
Connection general section configuration
Make the following changes:
- Mode - Start;
- Type - Tunnel;
- Local subnet – 192.168.14.0/24;
- Remote subnet – 192.168.3.0/24;
- Key exchange - IKEv2;
Connection advanced section configuration
Make the following changes:
- Open Advanced settings;
- Enable Force encapsulation;
- Enable Local firewall;
- Enable Remote firewall;
- Inactivity: 3600 - Defines the timeout interval, after which the connection is closed;
- Enable Dead peer detection;
- DPD action – Restart;
Proposal configuration
Important: Both the RUT1 and RUT2 Encryptions must match in order for this configuration to work.
Note: This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.
Make the following changes:
|
|
Testing the configuration
If you have followed all the above steps, your configuration should be finished. But as with any other configuration, it is always wise to test the setup in order to make sure that it works properly.
Using the ipsec status or we can use ipsec statusall command for a more verbose output. With these commands we can see that the IPsec tunnel is successfully established on RUTxxx router. The command output on a RUT1 device:
Also, we can try to ping the RUT2 device by executing this command ping 192.168.14.1, by which you should get a response if the IPsec tunnel has been established properly.
To check if IPsec tunnel is working properly from RUT2, we can try pinging our RUT1 device by using this command in command line interface on RUT2ping 192.168.3.1:
Also we can check it by executing the ipsec status or we can use ipsec statusall command for a more verbose output. With these commands we can see that the IPsec tunnel is successfully established on RUTxxx router. The command output on a RUT2 device: