L2TP over IPsec PC: Difference between revisions
No edit summary |
No edit summary |
||
| Line 32: | Line 32: | ||
* '''Server configuration''': | * '''Server configuration''': | ||
[[File:L2tpoveripsecl2tpserverconfiguration new.png|left]] | [[File:L2tpoveripsecl2tpserverconfiguration new.png|left]] | ||
* '''Enable''' - when checked, enables the instance | |||
* '''Local IP''' - the server's virtual IP address | |||
* '''Remote IP range''' parameters - the range of virtual IP addresses that will be assigned to connecting clients | |||
* '''User name''' and '''Password''' - authentication information used to authenticate connecting clients | |||
---- | |||
===IPsec=== | |||
---- | |||
Next, you must configure a working IPsec transport connection. This subsection contains instructions on how to do just that. The relevant parameters will be encapsulated <span style="color:red">'''in red rectangles'''</span>. Explanations about these parameters will be provided under each example. Other used parameters will be defaults; you can find explanations for those parameters in the '''[[VPN#IPsec|VPN manual page, IPsec section]]'''. | |||
Login to the router's WebUI and navigate to '''Services → VPN → IPsec'''. Enter a custom name for your IPsec instance and click the "Add" button. Then click the "Edit" button located next to the newly created instance after which you will redirected to that instance's configuration window. Adhere to the configurations presented in the figure below: | |||
[[File:L2tpoveripsecserver1.png|left|L2tpoveripsecserver1]] | |||
[[File:L2tpoveripsecserver2.png|left|L2tpoveripsecserver2]] | |||
* '''Remote VPN endpoint''' - IP address or hostname of the remote IPsec instance. '''Leave empty''' for the server configuration | |||
* '''Enable''' - if checked, enables the IPsec instance | |||
* '''Authentication method''' - different authentication methods between the peers. For this configuration we select '''Pre-shared key''' | |||
* '''Pre shared key''' - a shared password used for authentication between the peers. The value of this field must match the other instance | |||
* '''Type''' - the type of the connection. '''Transport''' encrypts only the payload and Encapsulating Security Payload (ESP) trailer; so the IP header of the original packet is not encrypted. Transport mode is usually used when another tunneling protocol (such as [[VPN#GRE_Tunnel|GRE]], [[VPN#L2TP|L2TP]]) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets. NAT traversal is not supported with the transport mode. | |||
* '''Bind to''' - a shared password used for authentication between the peers. The value of this field must match the other instance | |||
Revision as of 22:51, 3 March 2022
Main Page > General Information > Configuration Examples > VPN > L2TP over IPsec PCIntroduction
Because of the lack of confidentiality inherent in the Layer 2 Networking Protocol (L2TP) protocol, Internet Protocol Security (IPsec) is often used to secure L2TP packets by providing confidentiality, authentication and integrity. The combination of these two protocols is generally known as L2TP over IPsec (or simply L2TP/IPsec).
This article provides a guide on how to configure L2TP/IPsec on RUTxxx routers, to establish a connection with clients on their personal computers. It should also be noted that this guide is aimed at more advanced users and, therefore, skips some of the more self-explanatory steps in order to preserve the overall coherence of the article. For example, instead of showing how to add new instances step by step, it is only mentioned in a short sentence. If you feel this lack of information impedes your ability to configure the setup, we suggest you check out our separate configuration guides on IPsec and L2TP for reference.
Click Here for a user's manual based on the old style WebUI (FW version RUT9XX_R_00.06.08.6 and earlier).
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- One RUTxxx router of any type (excluding RUT850) with a Public Static or Public Dynamic IP addresses
- At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers and connect to the VPN.
Configuration scheme:
The figure above shows the L2TP/IPsec scheme. It is quite similar to the L2TP and IPsec configuration schemes - the router with the public IP address (RUT) acts as the L2TP/IPsec server and a PC acts as the client. L2TP connects the RUT and PC networks and IPsec provides the encryption for the L2TP tunnel.
When the scheme is realized, the L2TP packets between the endpoints are encapsulated by IPsec. Since the L2TP packet itself is wrapped and hidden inside the IPsec packet, the original source and destination IP address is encrypted inside the packet.
Router configuration
If you have familiarized yourself with the configuration scheme and have all of the devices in order, we can start configuring the router using instructions provided in this section. To summarize, we'll be configuring an L2TP server and an IPsec Transport instance (server) on RUT; an L2TP/IPsec client on PC.
L2TP
First, it is recommended to start with the L2TP tunnel configuration. This subsection contains instructions on how to do just that. The relevant parameters will be encapsulated in red rectangles. Explanations about these parameters will be provided under each example. For more VPN manual page, IPsec section.
New L2TP instances can be created from the Services → VPN → L2TP section of the router's WebUI. Select Server role, enter a custom name and click the "Add" button to create a new instance. Then click the "Edit" button located next to the newly created instance to enter its configuration page.
- Server configuration:
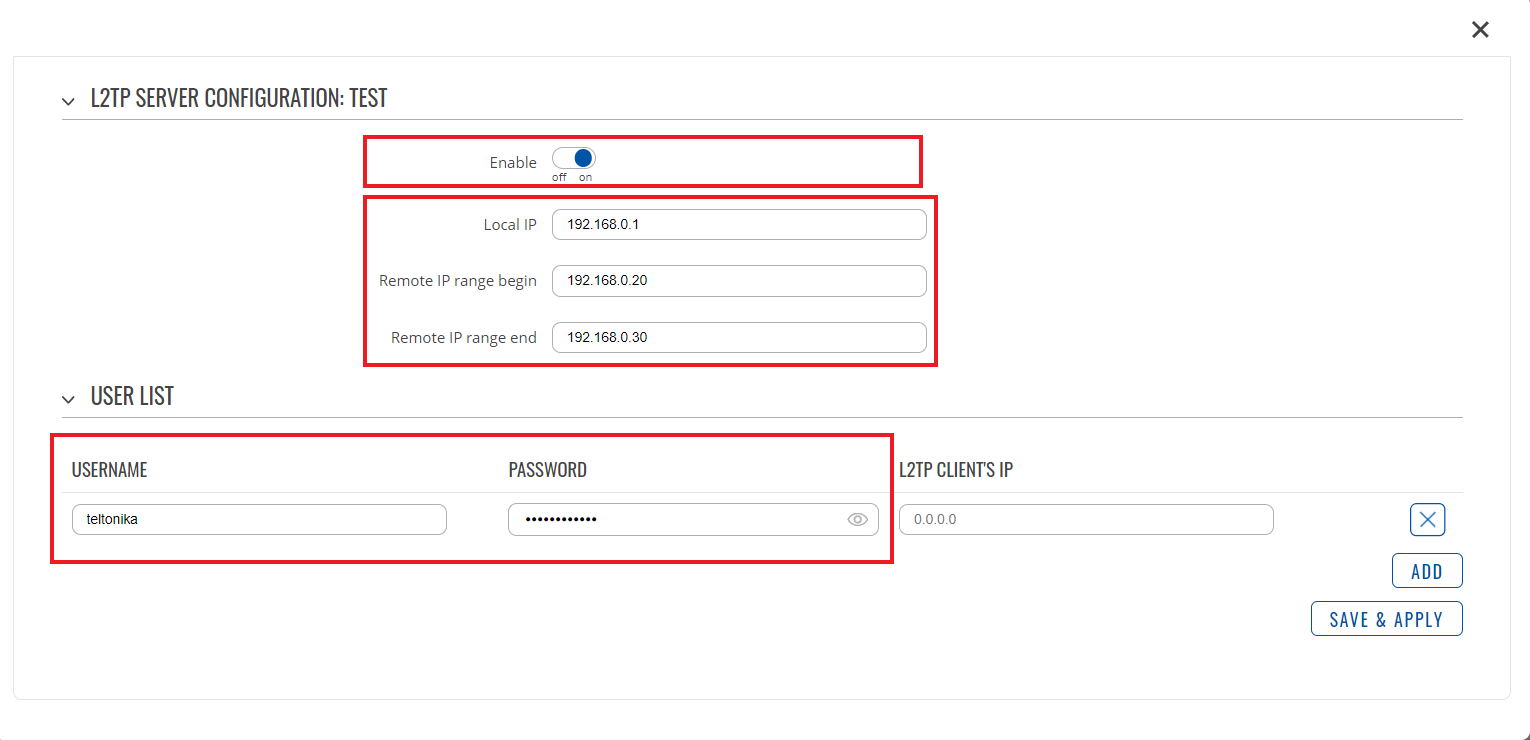
- Enable - when checked, enables the instance
- Local IP - the server's virtual IP address
- Remote IP range parameters - the range of virtual IP addresses that will be assigned to connecting clients
- User name and Password - authentication information used to authenticate connecting clients
IPsec
Next, you must configure a working IPsec transport connection. This subsection contains instructions on how to do just that. The relevant parameters will be encapsulated in red rectangles. Explanations about these parameters will be provided under each example. Other used parameters will be defaults; you can find explanations for those parameters in the VPN manual page, IPsec section.
Login to the router's WebUI and navigate to Services → VPN → IPsec. Enter a custom name for your IPsec instance and click the "Add" button. Then click the "Edit" button located next to the newly created instance after which you will redirected to that instance's configuration window. Adhere to the configurations presented in the figure below:
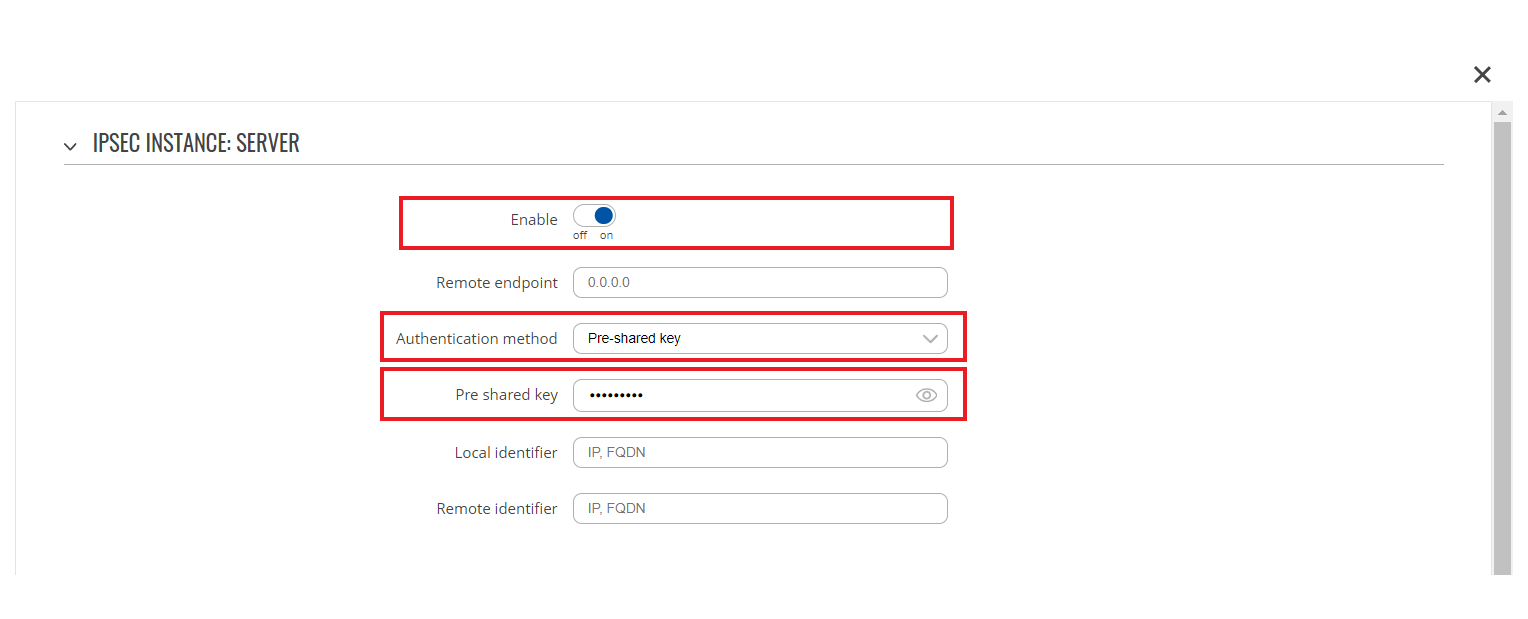
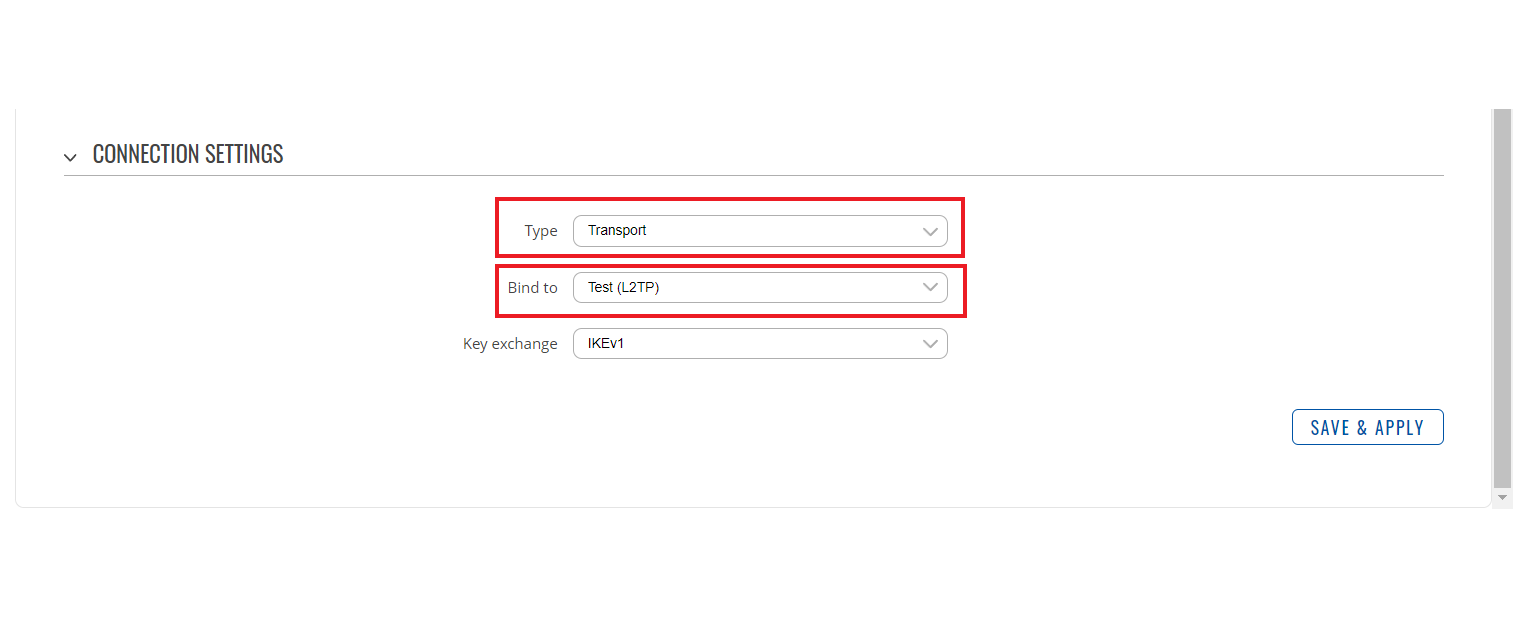
- Remote VPN endpoint - IP address or hostname of the remote IPsec instance. Leave empty for the server configuration
- Enable - if checked, enables the IPsec instance
- Authentication method - different authentication methods between the peers. For this configuration we select Pre-shared key
- Pre shared key - a shared password used for authentication between the peers. The value of this field must match the other instance
- Type - the type of the connection. Transport encrypts only the payload and Encapsulating Security Payload (ESP) trailer; so the IP header of the original packet is not encrypted. Transport mode is usually used when another tunneling protocol (such as GRE, L2TP) is used to first encapsulate the IP data packet, then IPsec is used to protect the GRE/L2TP tunnel packets. NAT traversal is not supported with the transport mode.
- Bind to - a shared password used for authentication between the peers. The value of this field must match the other instance
