OpenVPN over Stunnel RutOS: Difference between revisions
Created blank page |
No edit summary |
||
| Line 1: | Line 1: | ||
==Introduction== | |||
<b>Stunnel</b> is an open-source a proxy service that adds TLS encryption to clients and servers already existing on a VPN network. TLS encryption provided by Stunnel can be used as an additional layer of encryption for data sent by OpenVPN. This procedure increases the security of the established connection and provides higher chances of passing a Deep packet inspection (DPI) check. | |||
This article contains instructions on how to configure an OpenVPN over Stunnel topology. | |||
==Overview== | |||
<b>You will need</b> | |||
<ul> | |||
<li>two routers of the RUTxxx series (except RUT850);</li> | |||
<li>at least one router (server) with a public IP;</li> | |||
<li>TLS certificates for the server and the client (<i>for instructions on generating TLS certificates, [[How to generate TLS certificates (Windows)?|click here]]</i>).</li> | |||
</ul> | |||
---- | |||
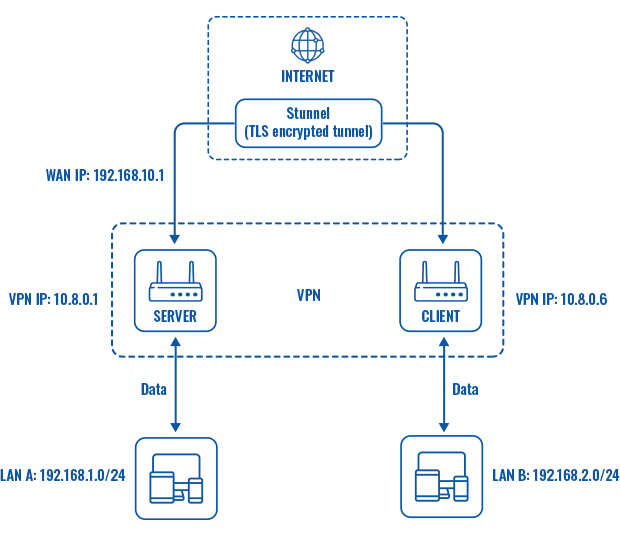
<b>Topology</b> | |||
[[File:Networking device vpn stunnel working scheme v4.png|border|class=tlt-border]] | |||
---- | |||
<b>Explanation</b> | |||
An OpenVPN client is connected to an OpenVPN server (both hosted on RUT routers) via a TLS encrypted Stunnel connection. This provides the possibility to transfer data between remote private networks (LAN A and LAN B) and adds an additional TLS security layer for the connection. | |||
==Server configuration== | |||
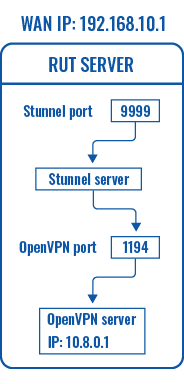
First, configure the OpenVPN and Stunnel servers. The Stunnel server will listen for incoming client connections on the specified TCP port (<i>9999</i> in this example) and connect them to the OpenVPN server running on the local host. | |||
The logic of the connection can be visualized like this: | |||
[[File:Networking device vpn stunnel server working scheme v2.png|border|class=tlt-border]] | |||
===OpenVPN server=== | |||
---- | |||
Navigate to the <b>Services → VPN → OpenVPN</b> page. Select <i>Role: Server</i>, enter a custom name and click the 'Add New' button. An OpenVPN server instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the server instance. | |||
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: | |||
Revision as of 07:43, 19 May 2022
Main Page > General Information > Configuration Examples > VPN > OpenVPN over Stunnel RutOSIntroduction
Stunnel is an open-source a proxy service that adds TLS encryption to clients and servers already existing on a VPN network. TLS encryption provided by Stunnel can be used as an additional layer of encryption for data sent by OpenVPN. This procedure increases the security of the established connection and provides higher chances of passing a Deep packet inspection (DPI) check.
This article contains instructions on how to configure an OpenVPN over Stunnel topology.
Overview
You will need
- two routers of the RUTxxx series (except RUT850);
- at least one router (server) with a public IP;
- TLS certificates for the server and the client (for instructions on generating TLS certificates, click here).
Topology
Explanation
An OpenVPN client is connected to an OpenVPN server (both hosted on RUT routers) via a TLS encrypted Stunnel connection. This provides the possibility to transfer data between remote private networks (LAN A and LAN B) and adds an additional TLS security layer for the connection.
Server configuration
First, configure the OpenVPN and Stunnel servers. The Stunnel server will listen for incoming client connections on the specified TCP port (9999 in this example) and connect them to the OpenVPN server running on the local host.
The logic of the connection can be visualized like this:
OpenVPN server
Navigate to the Services → VPN → OpenVPN page. Select Role: Server, enter a custom name and click the 'Add New' button. An OpenVPN server instance with the given name will appear in the "OpenVPN Configuration" list. To begin configuration, click the 'Edit' button next to the server instance.
The figure below displays the configuration used for our example. Take note of the comments that are provided next to fields that differ from the default value: