Setting up a Site-to-Site IPsec Tunnel between Teltonika Networks and Microsoft Azure
Summary
This article will guide you through configuring a Site-to-Site IPsec Tunnel between Teltonika routers/gateways and Microsodt Azure VPN gateway.
Prerequisite
The user needs an Azure account with an active subscription.
Azure Platform
Create a VPN Gateway on the Azure Platform
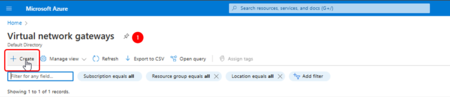
Log into the Azure portal, search for "Virtual Network Gateways" and click on "Create".
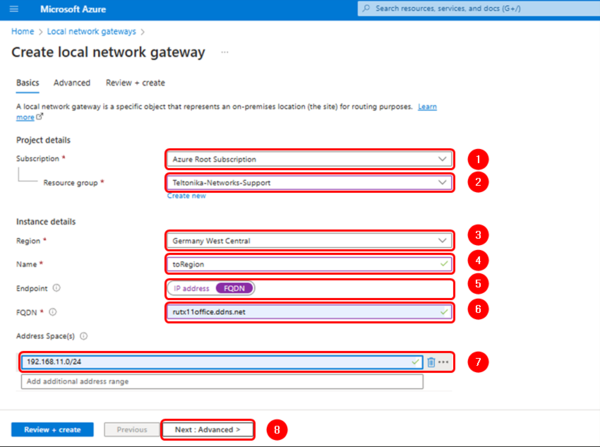
Use the information and images below as reference to complete the settings:
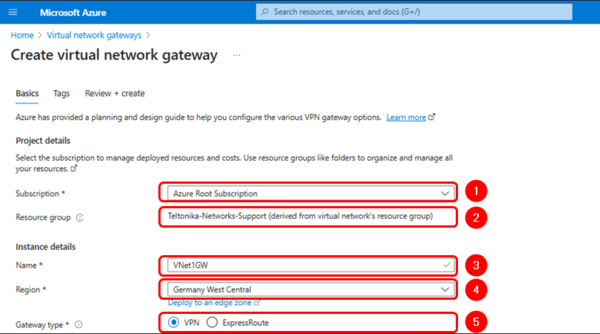
Projects details
- Suscription: Your suscription
- Resource Group: Your resource group.
Instance details
- Name: VNet1GW
- Region: Your prefered Region
- Gateway type: VPN
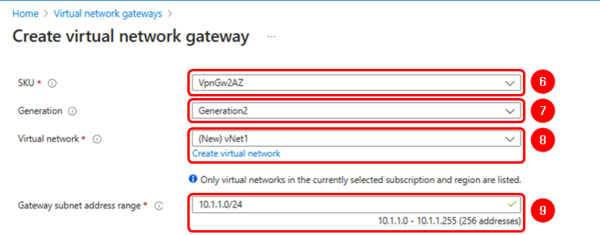
- SKU: VpnGW2AZ
- Generation: Generation2 (mandatory)
- Virtual Network: Select or create a new one.
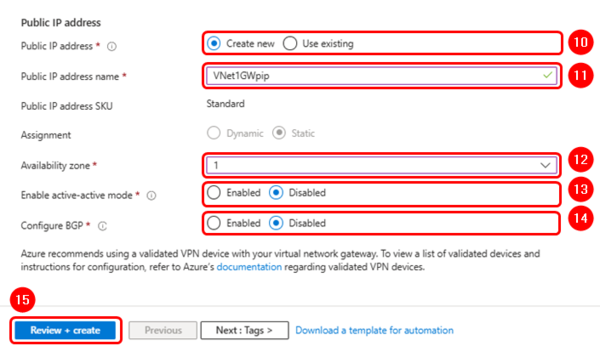
Public IP address
- Public IP address: Create new one.
- Public IP address name: "Vnet1GWpip"
- Assigment: Static
- Enable active-active mode: Disabled
- Configure BGP: Disabled
Create a Virtual Network
In case you do not have a previously created virtual network, click on the blue URL link to create one:
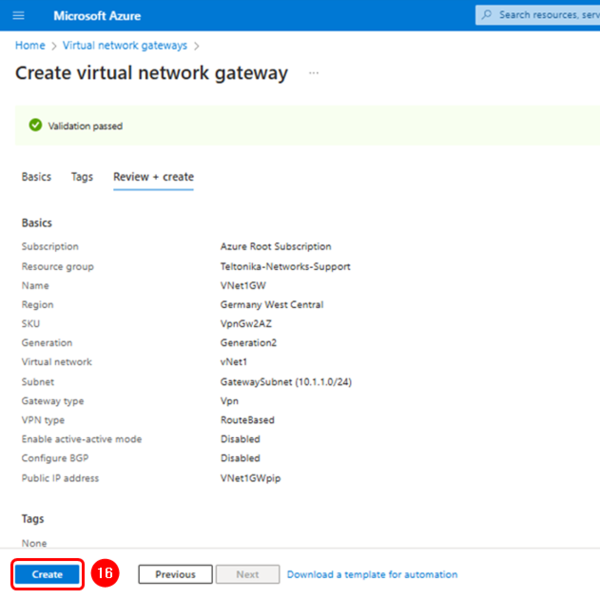
Finish the VPN gateway configuration
After finishing the previous configuration, you can continue with the tags. This section is not mandatory; therefore, we’ll leave it as default.
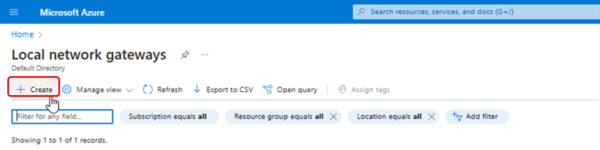
Create a local network Gateway
Click on "Review + create", check that the network gateway has the parameters as shown below, and click on the "Create" button to finish.