Setting up a Site-to-Site IPsec Tunnel between Teltonika Networks and Microsoft Azure
The information on this page is updated in accordance with the 00.07.13.1 firmware version .
Introduction
A site-to-site connection using an IPsec tunnel between Teltonika devices and an Azure Virtual Network Gateway is a secure method to link two separate networks over the internet. This setup ensures that data transmitted between the on-premises network, managed by Teltonika routers, and the Azure cloud environment is encrypted and secure.
Topology
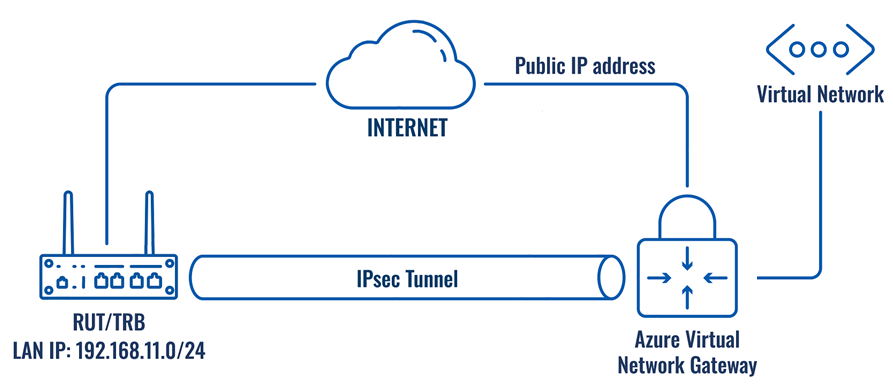
Prerequisite
The user needs an Azure account with an active subscription, at least one Resource Group already configured and a Teltonika Networks gateway or router to establish an IPsec VPN tunnel between the device and the VPN gateway in Azure.
Note: Teltonika Network devices do not necessarily require a static or dynamic public IP address on their WAN interface to establish communication through the VPN tunnel. As such, this configuration can be used even when the network operator or ISP employs Carrier-Grade NAT (CG-NAT) in their infrastructure.
Azure Platform
We will configure all the necessary resources on the Microsoft Azure side to create and establish an IPsec VPN tunnel between the router and the platform.
Create a VPN Gateway on the Azure Platform
First, we will create a Virtual Network Gateway (VNet Gateway), a resource that facilitates secure communication between an Azure Virtual Network (VNet) and other networks, including on-premises networks, other VNets, and even the internet, through VPN connections.
To proceed with the above, log into the Azure portal, search for Virtual Network Gateways and click on Create.

Then, fill in the settings accordingly to the images below:
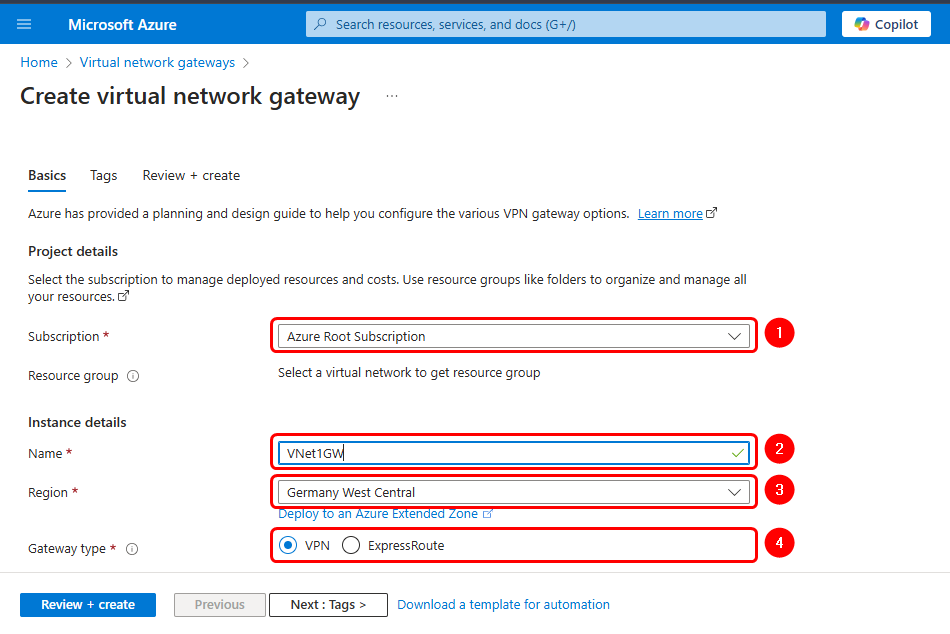
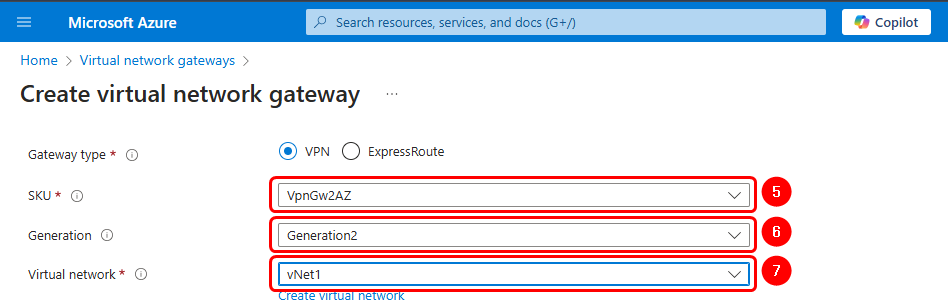
Create a Virtual Network
If you haven't previously created a virtual network, which is the network you use to manage your Azure resources, click on the blue URL link to create one by using the default settings as shown in the image below:
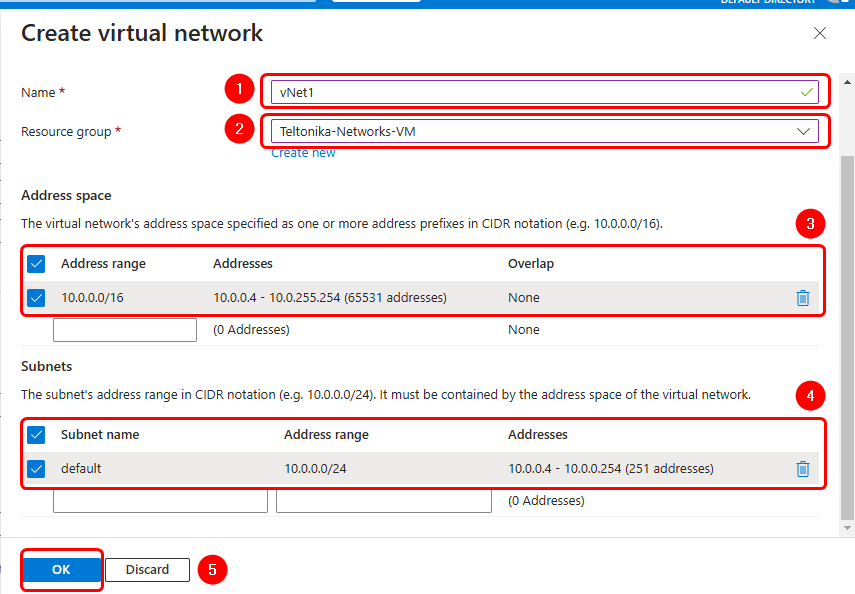
Continue and finish the VPN gateway configuration
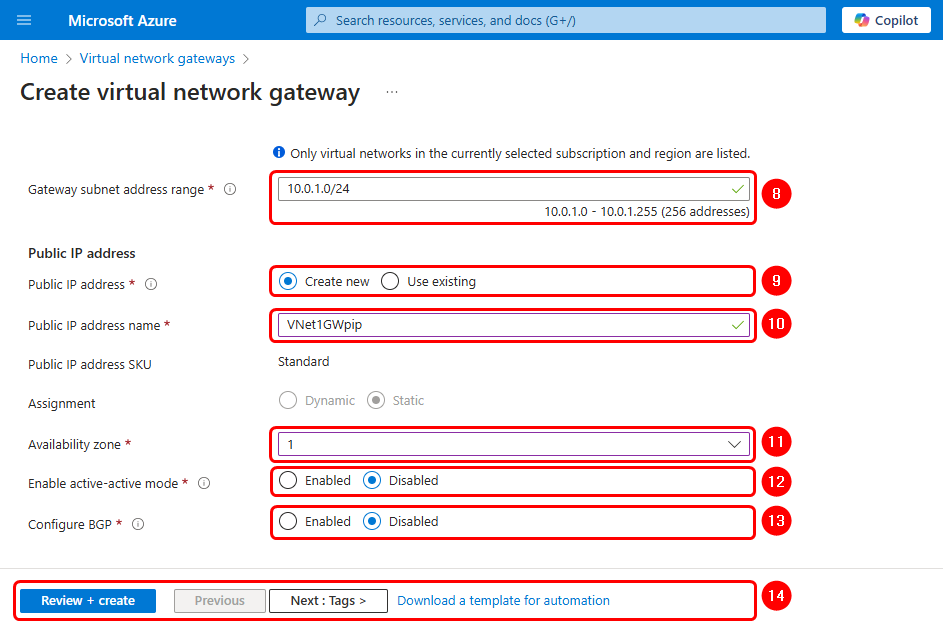
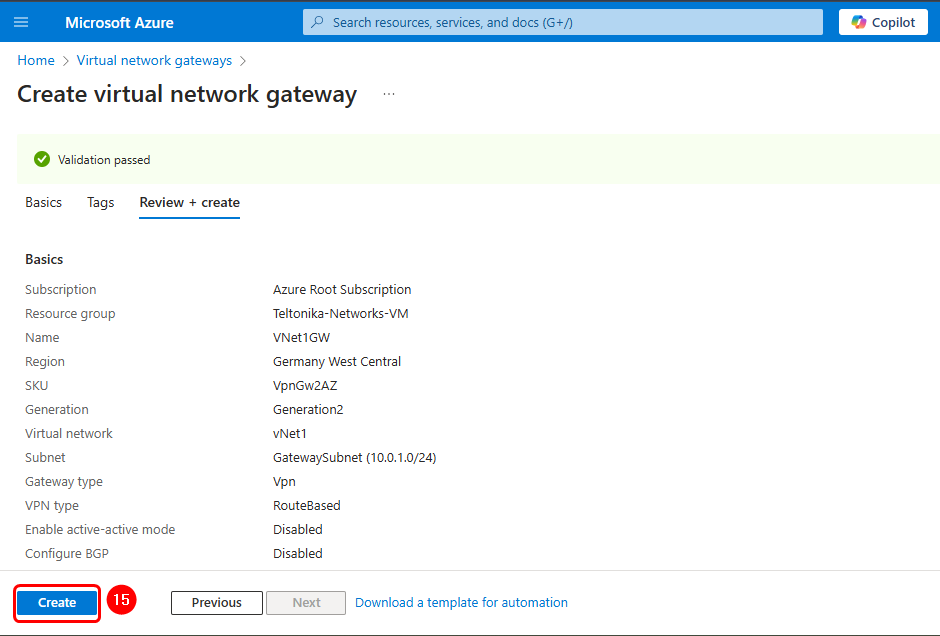
After finishing the previous configuration, you can continue with the tags. This section is not mandatory; therefore, we left it as default and clicked on Review + create to check that the network gateway has the parameters shown below, and then click on the Create button to finish the configuration.
List of settings:
Projects details
- Suscription: Your suscription.
- Resource Group: Your resource group.
Instance details
- Name: VNet1GW.
- Region: Your prefered Region.
- Gateway type: VPN.
- SKU: VpnGW2AZ.
- Generation: Generation2 (mandatory).
- Virtual Network: Select or create a new one.
- Gateway Subnet Address Range: 10.0.1.0/24 (if using Virtual Network default configuration).
Public IP address
- Public IP address: Create new.
- Public IP address name: Vnet1GWpip.
- Assigment: Static.
- Enable active-active mode: Disabled.
- Configure BGP: Disabled.
Create a local network Gateway
In Azure, a Local Network Gateway (LNG) represents the on-premises network that you want to connect to Azure via a VPN (Virtual Private Network) or other hybrid networking solutions. It is a resource in Azure that contains information about your local network, such as its IP address range and the public IP address of the on-premises VPN device or firewall.
Having the above in mind, in the search bar, look for Local Network Gateways and click on Create
Fill in the configuration fields accordingly to the images below and add the remote router address space (LAN network) and the FQDN if the router does not have a static public IP address on its WAN interface.
Note: If you select an FQDN (Fully Qualified Domain Name), you must specify the domain name you want to assign to your router, which will be used to map the dynamic public WAN IP address of your router when activating the DDNS service.
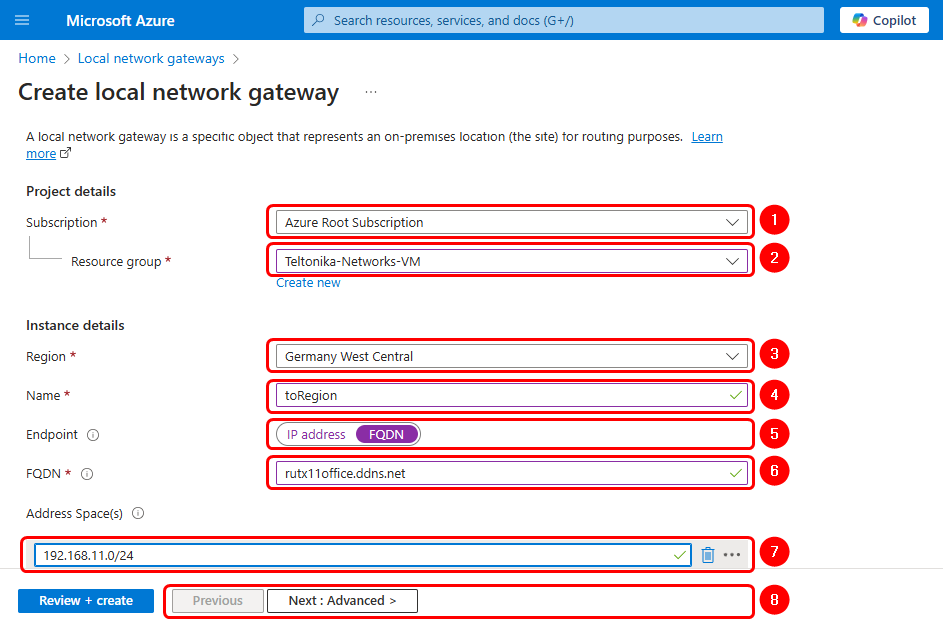
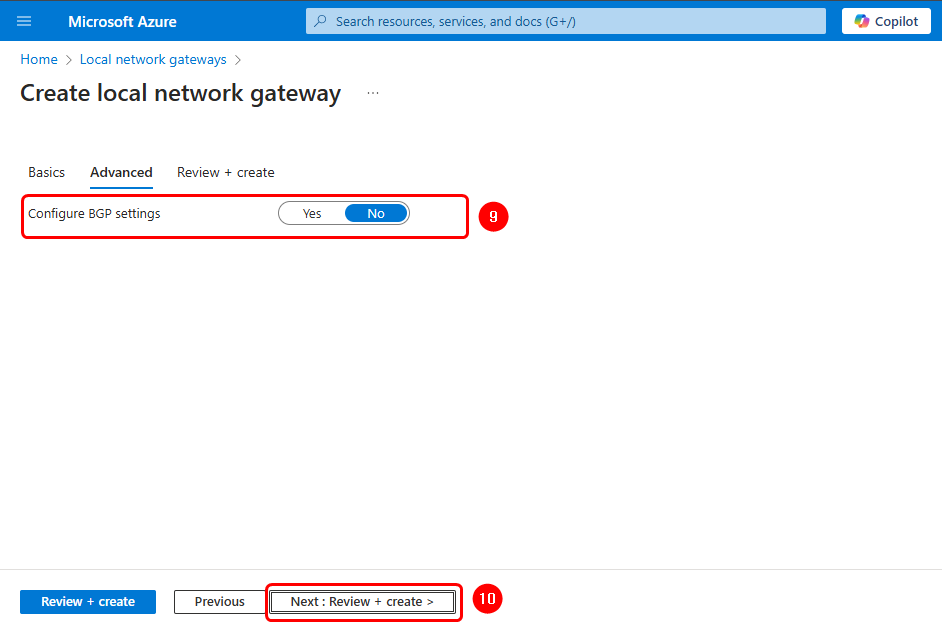
Verify the configuration and click on Create to finish.
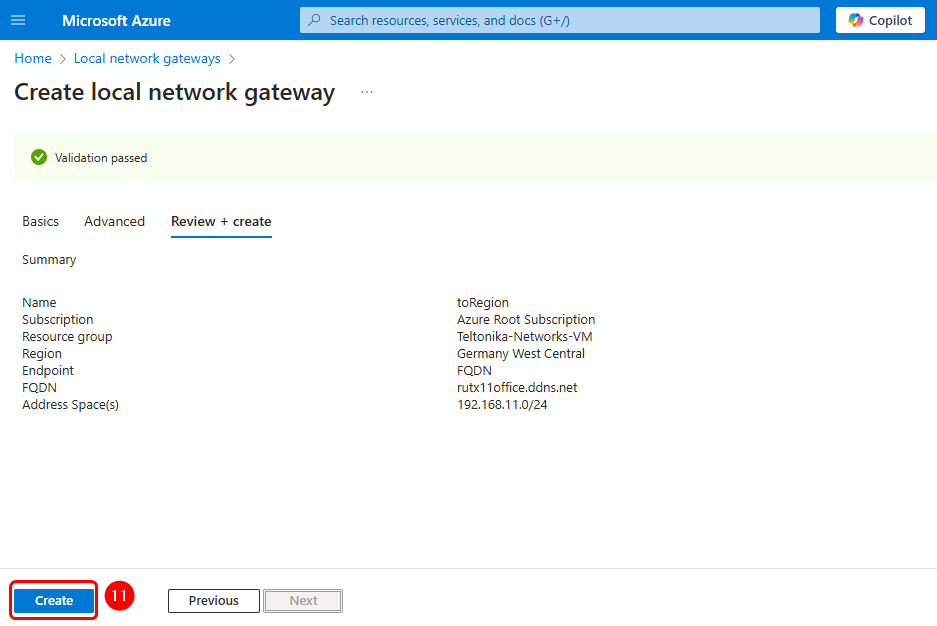
List of settings:
Projects details
- Suscription: Your suscription.
- Resource Group: Your resource group.
Instance details
- Region: Your prefered Region.
- Name: toRegion.
- Endpoint: FQDN.
- FQDN: The fully qualified domain name of the router's remote connection.
- Address Space: The router's LAN network(s)
- Configure BGP settings: No.
Create a connection
Now, we’ll configure the VPN connection on Azure, enabling the establishment of a Site-to-Site IPsec tunnel between the Teltonika router and the Azure platform. This connection will ensure secure, encrypted communication between your on-premises network and Azure resources.
So, the next step would be to search for Connections and create a new one:
Complete the configuration fields taking as a reference the images below:

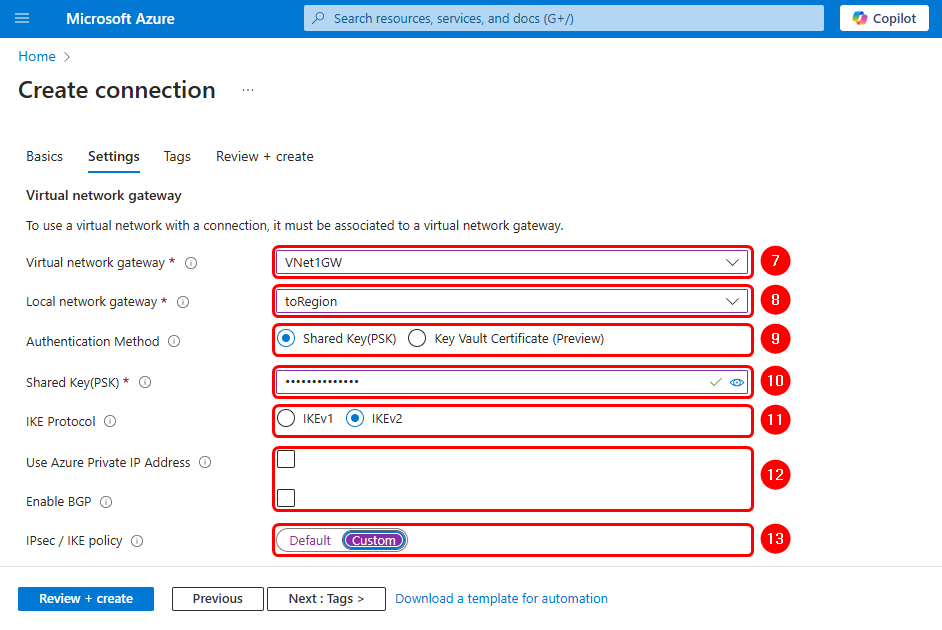
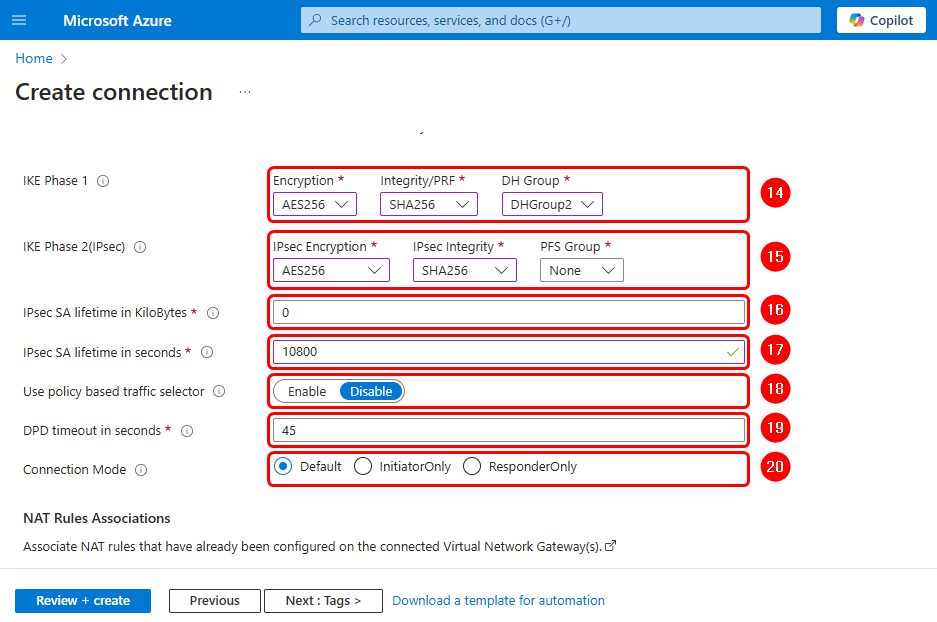
Note: You can use different crypto proposals; however, you must ensure that they match on the router.
Click on Review + Create, then verify the configuration and click on Create to finish.

List of settings:
Projects details
- Suscription: Your suscription.
- Resource Group: Your resource group.
Instance details
- Connection type: Site-to-Site (IPsec).
- Name: SiteToSite.
- Region: Your prefered Region (It must match the one selected above).
Virtual network Gateway
- Virtual network gateway: Vnet1GW.
- Local network gateway: toRegion.
- Shared Key(PSK): Your Pre-shared key (It must match the one in the router IPsec configuration).
- Use Azure Private IP Address: Unchecked.
- IPsec/IKE policy: Custom.
- IKE Phase 1: Encryption: AES256 , Integrity/PRF: SHA256 , DH Group: DHGroup2.
- IKE Phase 2: Encryption: AES256 , IPsec Integrity: SHA256 , PFS Group: None.
- IPsec SA lifetime in KiloBytes: 0.
- IPsec SA lifetime in seconds: 10800.
- Use policy based traffic selector: Disable.
- DPD timeout in seconds: 45.
- Connection mode Default or ResponderOnly.
NAT Rules Associations
- Ingress NAT Rules: unchecked.
- Egress NAT Rules: unchecked.
Teltonika Device Configuration
For this section, we will configure and activate the necessary services on the Teltonika router to establish a Site-to-Site IPsec tunnel with the Azure platform.
DDNS configuration
Whether you have a dynamic public IP address or a dynamic/static private IP address, you will need to enable this service to establish the tunnel, as Azure will use the FQDN (Fully Qualified Domain Name) or public IP address to validate the incoming connection.
Taking into consideration the above, follow the steps in this article to create an account with a DDNS service provider and register the domain name to be used by the router: DDNS Configuration Examples.
Then, log into the router via WebUI and proceed to configure the DDNS service as follows:
Path: WebUI → Services → Dynamic DNS.
Note: On devices other than the RUTX series, you will need to download the DDNS service from the Package Manager.

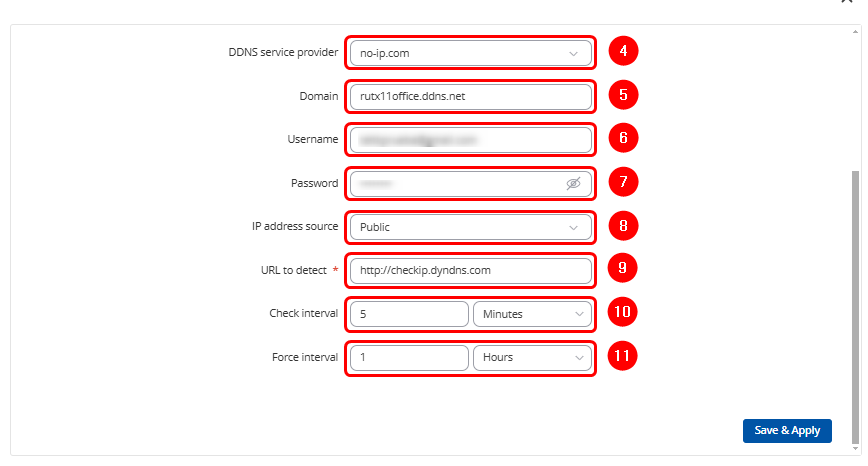
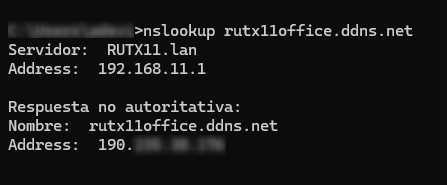
After finishing the configuration, you should get the public IP address of the created domain.
IPsec configuration
Now, we will configure the IPsec settings on the Teltonika router to establish a secure IPsec tunnel with Azure.
Following this, navigate to the following path: WebUI → Services → VPN → IPsec, and add a new instance as shown below:

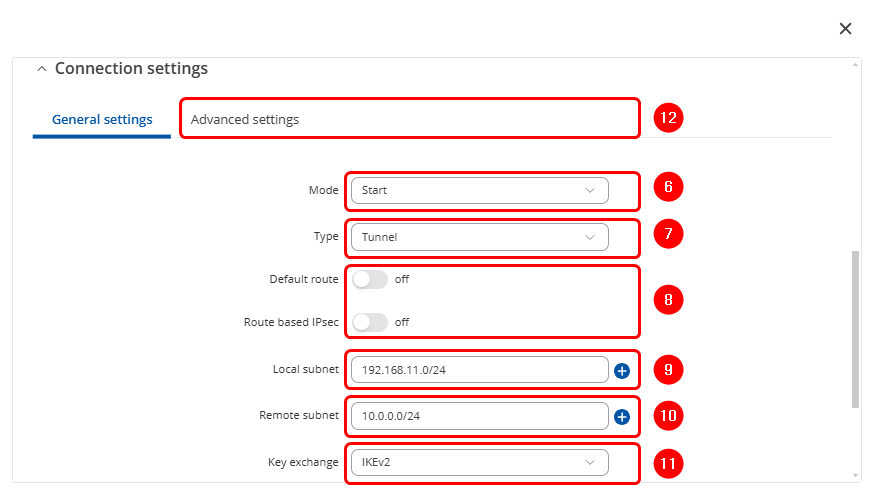
Note: in this example, we use DH Group equals to MODP1024 which is the same to Group 2 selected on the Azure platform.
List of Settings:
Instance details
- Enable: On.
- Remote Endpoint: Ms Azure Virtual Network Gateway public IP address.
- Authentication method: Pre-shared key.
- Pre-shared key: Your pre-shared key (must match the pre-shared key configured in the Azure platform's IPsec settings).
- Local Identifier: Empty.
- Remote Identifier: Empty.
General Settings
- Mode: Start.
- Type: Tunnel.
- Default route: off.
- Local Subnet: The router local network(s).
- Remote Subnet: The virtual network you want to access remotely hosted in your virtual environment in Azure.
- Key Exchange: IKEv2
Advanced Settings
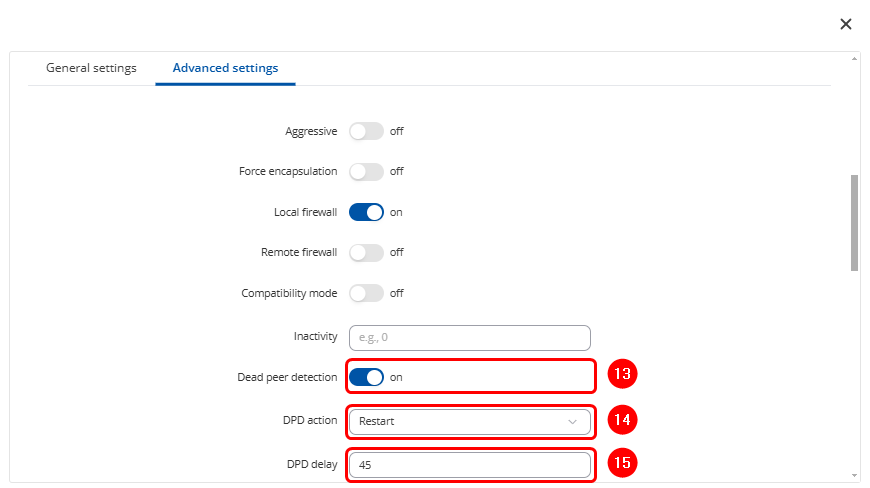
- Dead peer detection: On.
- DPD action: Restart.
- DPD delay: 45.
- Leave all other advanced settings as default.
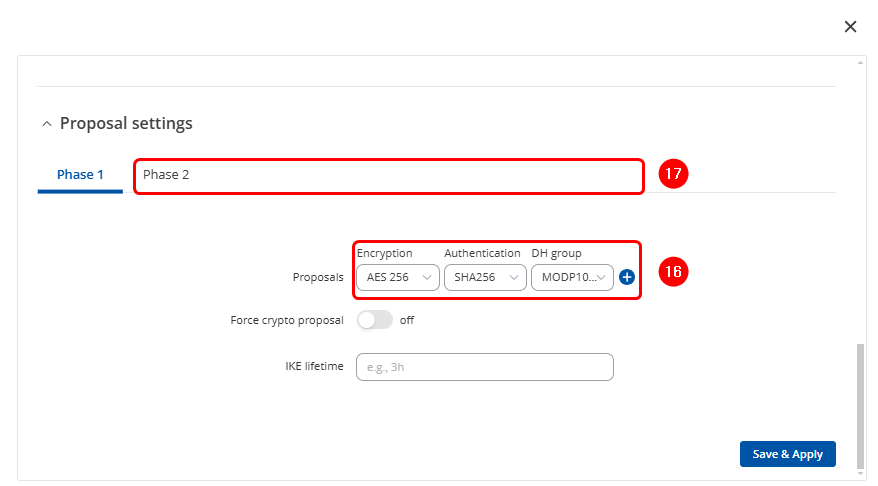
Proposal Settings
- Phase 1: Encryption: AES256 , Authentication: SHA56 , DH Group: MODP1024 (Group 2).
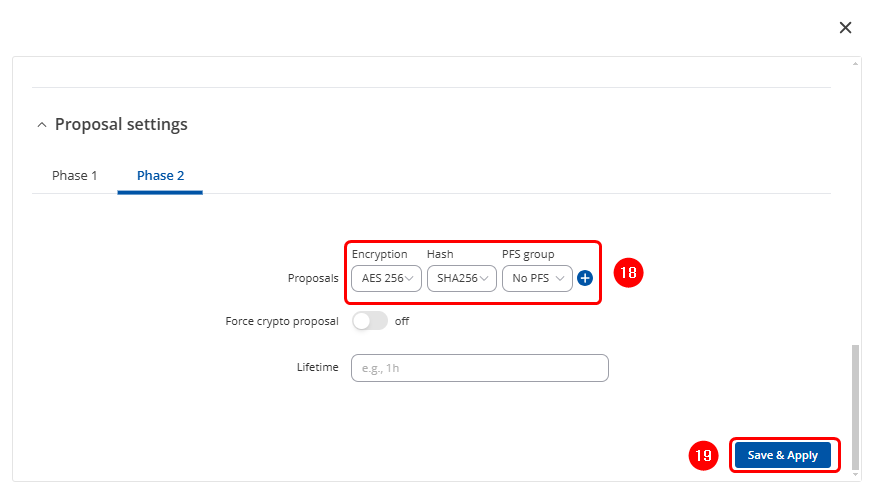
- Phase 2: Encryption: AES256 , Hash: SHA256 , PFS Group: No PFS.
- Force crypto Proposal: off.
- lifetimes: Empty.
Check Site to Site Communication
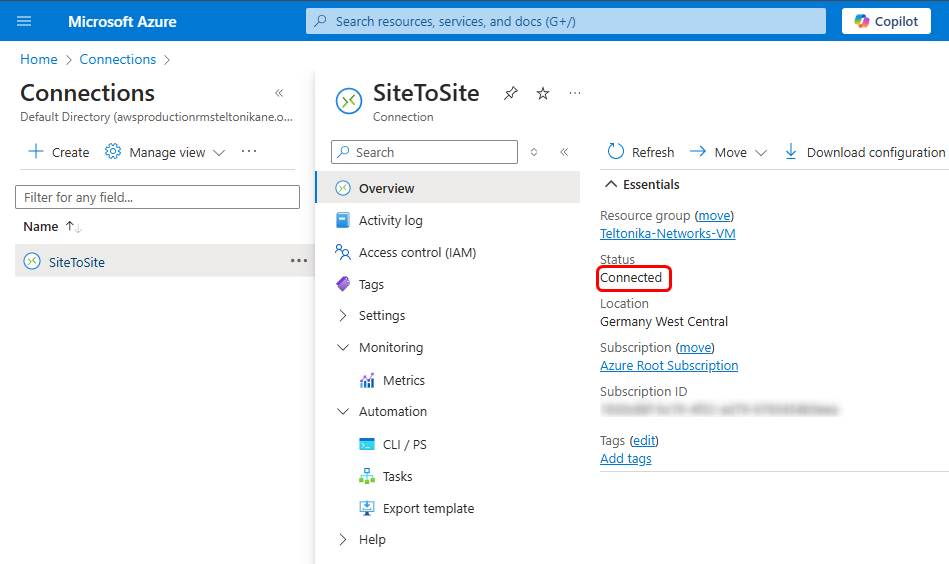
If you followed the configuration steps, you should see that the Site to Site connection has been successfully established.

You can also check in the Azure platform that the connection has been established:
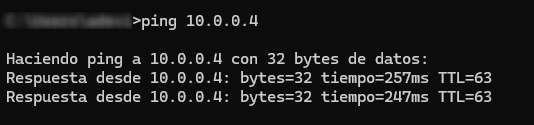
Check connectivity between the router LAN and a VM inside the Azure virtual network you may have:
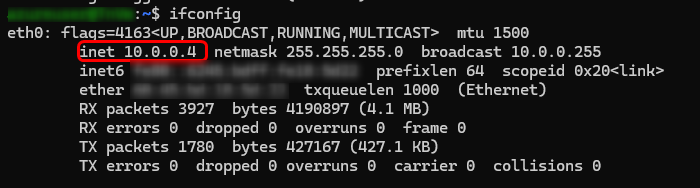
Test connectivity from a host in the router’s LAN to the VM:
See Also
- Dynamic DNS - general information on the DDNS service.
- DDNS Configuration Examples - additional examples for different DDNS providers.
