Difference between revisions of "Domnev"
| Line 108: | Line 108: | ||
===Instance configuration=== | ===Instance configuration=== | ||
---- | ---- | ||
| + | <table class="nd-othertables_2"> | ||
| + | <tr> | ||
| + | <th width=330; style="border-bottom: 1px solid white;></th> | ||
| + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:IPsec SPOKE.png|border|class=tlt-border|742x399px|right]]</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td style="border-bottom: 4px solid white> | ||
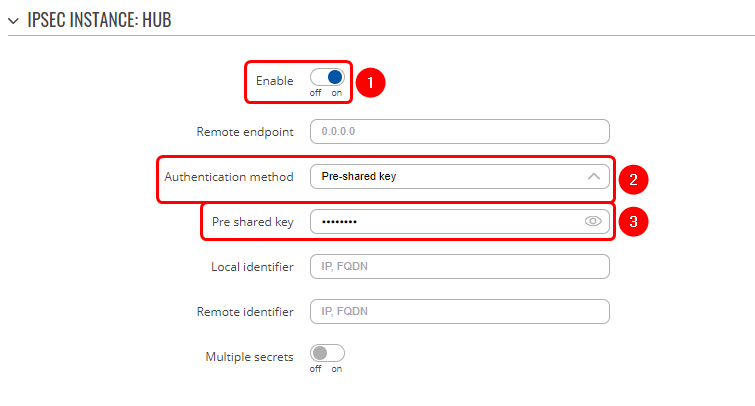
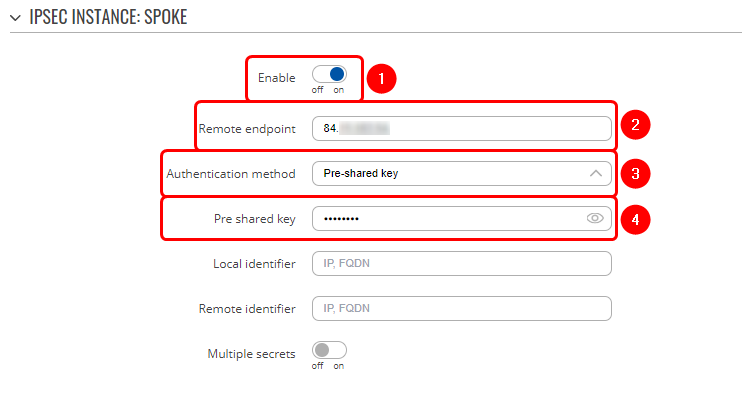
| + | # '''Enable''' instance; | ||
| + | # Remote endpoint - '''RUT1 public IP'''; | ||
| + | # Authentication method - '''Pre-shared key'''; | ||
| + | # Pre-shared key - the '''same password''' you have '''set on''' '''RUT1''' when configuring '''HUB instance'''; | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
===Connection configuration=== | ===Connection configuration=== | ||
---- | ---- | ||
| + | |||
| + | <table class="nd-othertables_2"> | ||
| + | <tr> | ||
| + | <th width=330; style="border-bottom: 1px solid white;></th> | ||
| + | <th width=800; style="border-bottom: 1px solid white;" rowspan=2>[[File:IPsec SPOKE Connection.png|border|class=tlt-border|761x280px|right]]</th> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | <td style="border-bottom: 4px solid white> | ||
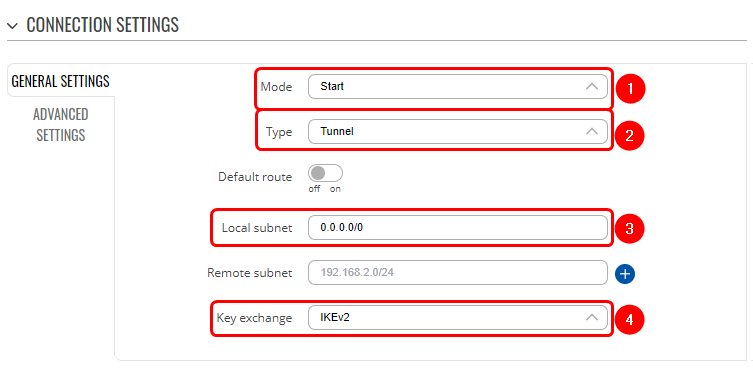
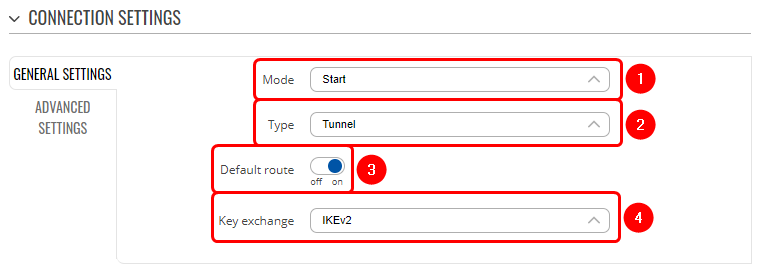
| + | # Mode - '''Start'''; | ||
| + | # Type - '''Tunnel'''; | ||
| + | # '''Enabled''' '''default route'''; | ||
| + | # Key exchange - '''IKEv2'''; | ||
| + | </td> | ||
| + | </tr> | ||
| + | </table> | ||
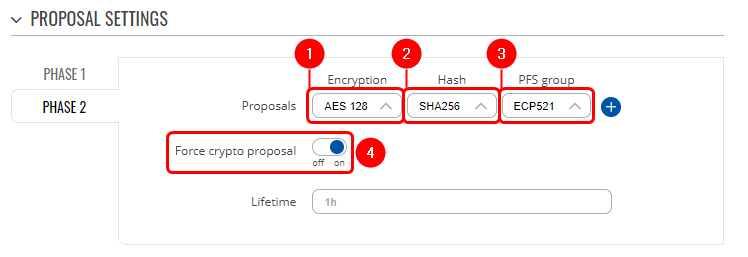
===Proposalconfiguration=== | ===Proposalconfiguration=== | ||
Revision as of 12:55, 21 March 2023
The information in this page is updated in accordance with 00.07.4 firmware version .
Introduction
Configuration overview and prerequisites
Before we begin, let's take a look at the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- Two RUT/RUTX series routers with RUTOS firmware;
- An end device (PC, Laptop) for configuration;
If you're having trouble finding any page or some of the parameters described here on your device's WebUI, you should turn on "Advanced WebUI" mode. You can do that by clicking the "Basic" button under "Mode," which is located at the top-right corner of the WebUI.
Topology
RUT1 - RUTX11 as a hub. It will be our "default gateway" for spoke device. RUTX11 has a LAN subnet of 192.168.11.0/24 configured on it, which should be reachable by the spoke.
RUT2 - RUT955 as a spoke. It will be connecting to a hub for basic internet access. RUT955 has a lan subnet of 192.168.9.0/24 configured on it, which should be reachable by the hub.
RUT1 (Hub) configuration
Start by configuring HUB (RUT1) device. Login to the WebUI, navigate to Services → VPN → IPsec and add a new IPsec instance. Configure everything as follows.
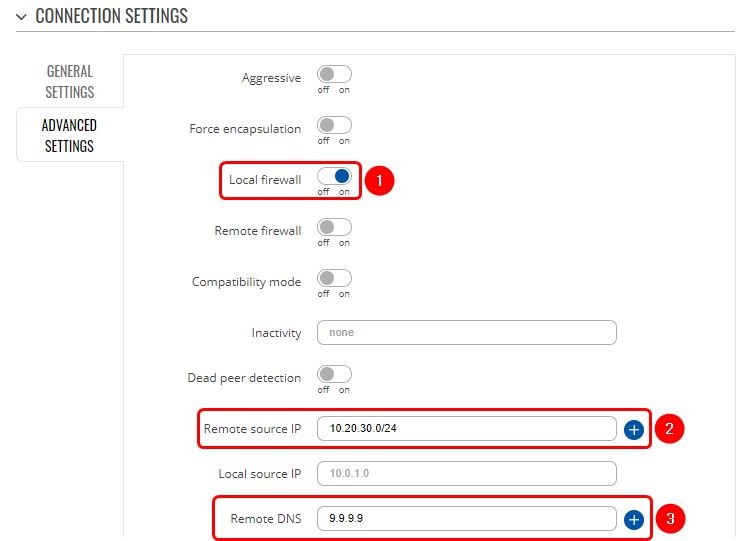
Note: Not specified fields can be left as-is or changed according to your needs.
Instance configuration
|
Connection configuration
|
|
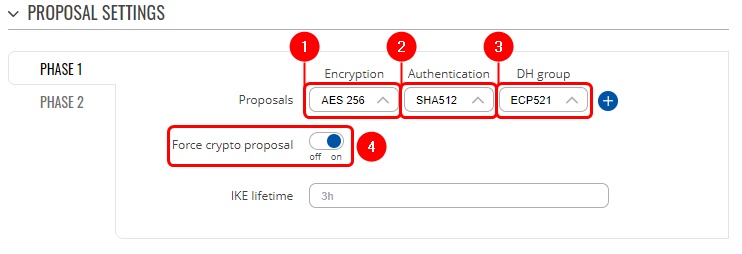
Proposal configuration
|
|
RUT2 (Spoke) configuration
Login to the RUT2 WebUI, navigate to Services → VPN → IPsec and add a new IPsec instance. Configure everything as follows.
Instance configuration
|
Connection configuration
|
Proposalconfiguration
|
|