TAP200 VPN
The information in this page is updated in accordance with firmware version TAP200_R_00.07.20.1.
Summary
Virtual Private Network (VPN) is a method of connecting multiple private networks across the Internet. VPNs can serve to achieve many different goals, but some of its main purposes are:
- access between remote private networks;
- data encryption;
- anonymity when browsing the Internet.
This page is an overview of the different types of VPNs supported by TAP200 devices.
OpenVPN
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It is often regarded as being the most universal VPN protocol because of its flexibility, support of SSL/TLS security, multiple encryption methods, many networking features and compatibility with most OS platforms.
Note: OpenVPN DCO kernel module moved to package manager on some devices. Please visit System → Package Manager page.
OpenVPN Client
An OpenVPN client is an entity that initiates a connection to an OpenVPN server.
| Client status | Value | Description |
|---|---|---|
| Export | -(interactive button) | Exports the instance configuration to .ovpn file. |
| Edit | -(interactive button) | Opens the instance configuration window. |
| Delete | -(interactive button) | Removes an instance. |
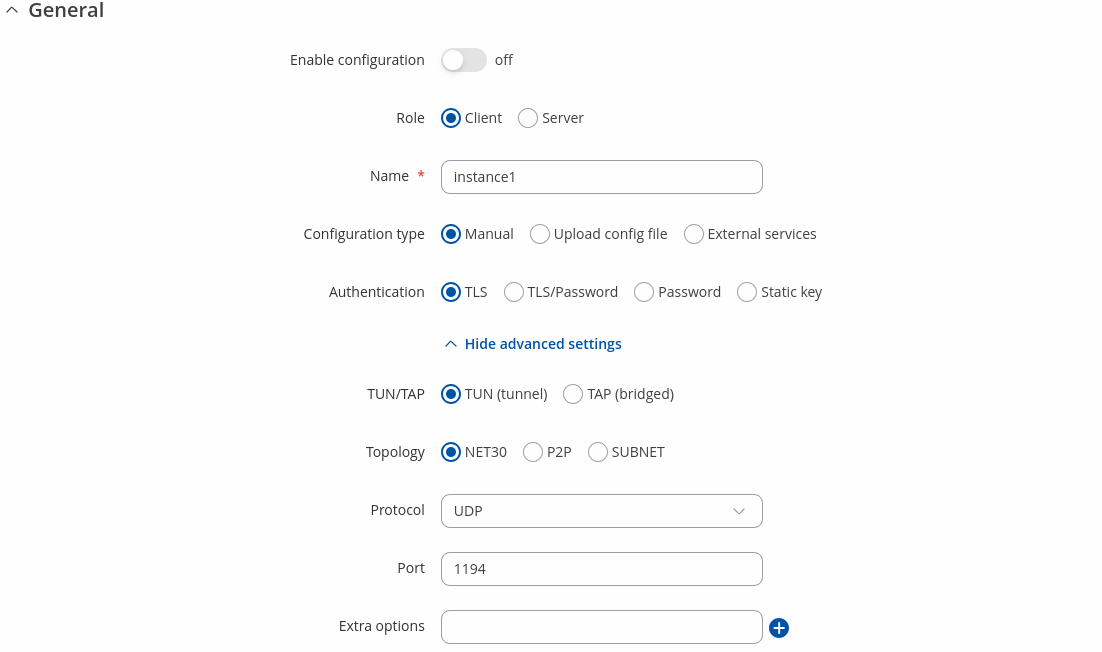
To begin configuration, click 'Add' button, select Role: Client. Refer to the figure and table below for information on the OpenVPN client's configuration fields:
| General section | Value | Description |
|---|---|---|
| Enable configuration | off | on; default: off | Enable current configuration. |
| Role | Client | Server; default: Client | Choose a role for OpenVPN isntance. |
| Name | string; default: instance1 | Name of the OpenVPN instance. |
| Configuration type | Manual | Upload config file | External services; default: Manual | Choose configuration type. |
| VPN providers | Express VPN | Nord VPN; default: Nord VPN | Represents a list of available VPN providers. |
| VPN servers | United Kingdom | USA | Australia | South Africa | Custom; default: United Kingdom | Represents a list of available VPN servers. |
| Username | string; default: none | Username used for authentication to the VPN server. |
| Password | string; default: none | Password used for authentication to the VPN server. |
| Enable parsing | off | on; default: off | By enabling parsing, you can modify the configuration in the future. |
| OpenVPN configuration file | -(interactive button) | Upload OpenVPN configuration. Warning! This will overwrite your current configuration. |
| Authentication | TLS | TLS/Password | Password | Static key; default: TLS | Choose a method to authenticate your OpenVPN network. |
| TUN/TAP | TUN (tunnel) | TAP (bridged); default: TUN (tunnel) | Virtual VPN interface type. |
| Topology | NET30 | P2P | SUBNET (not shown with Static key); default: NET30 | Virtual addressing topology determines how IP addressing and routing are handled between the server and clients. |
| Protocol | UDP | TCP | UDP4 | TCP4 | UDP6 | TCP6; default: UDP | The transport protocol used for the connection. Note: UDP and TCP do not support IPv6 connections, use UDP6 or TCP6 instead. |
| Port | integer [0..65535]; default: 1194 | TCP/UDP port for both local and remote endpoints. Make sure that this port is open in the firewall. |
| Extra options | string; default: none | Enter any additional options to be added to the OpenVPN configuration. If an option is already in use, the new option will take precedence. |
| Network section | Value | Description |
|---|---|---|
| Static key: Local tunnel endpoint IP | ip; default: none | IP address of the virtual local network interface. |
| Static key: Remote tunnel endpoint IP | ip; default: none | IP address of the virtual remote network interface. |
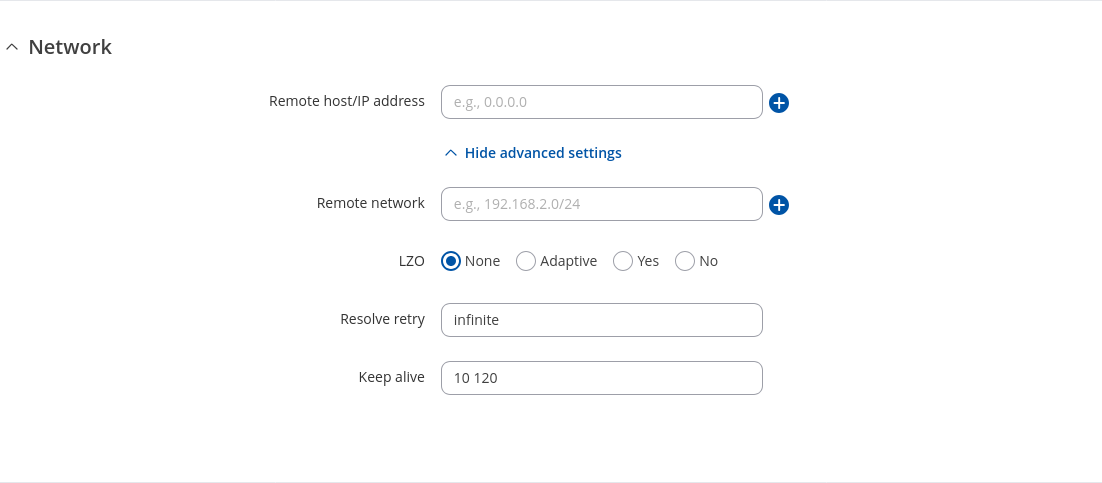
| Remote host/IP address | ip; default: none | IP address or domain name of the OpenVPN server. |
| Remote network | ip4; default: none | IP address of the remote LAN. |
| TAP (bridged): Bridge | lan | none; default: lan | Assign a TAP interface to a bridge.. |
| Static key: Local tunnel endpoint IPv6 | ip; default: none | IPv6 address of the virtual local network interface. |
| Static key: Remote tunnel endpoint IPv6 | ip; default: none | IPv6 address of the virtual remote network interface. |
| LZO | None | Adaptive | Yes | No; default: None | Use fast LZO compression. With LZO compression, your VPN connection will generate less network traffic. |
| Resolve retry | integer | infinite; default: infinite | Try to resolve the server hostname for X seconds before giving up. |
| Keep alive | two integers separated by a space; default: none | Try to keep the connection alive. Two values are required: ping_interval and ping_restart, e.g., 10 120. |
| Security section | Value | Description |
|---|---|---|
| TLS/Password/Password: User name | string; default: none | VPN client username. |
| TLS/Password/Password: Password | string; default: none | VPN client password. |
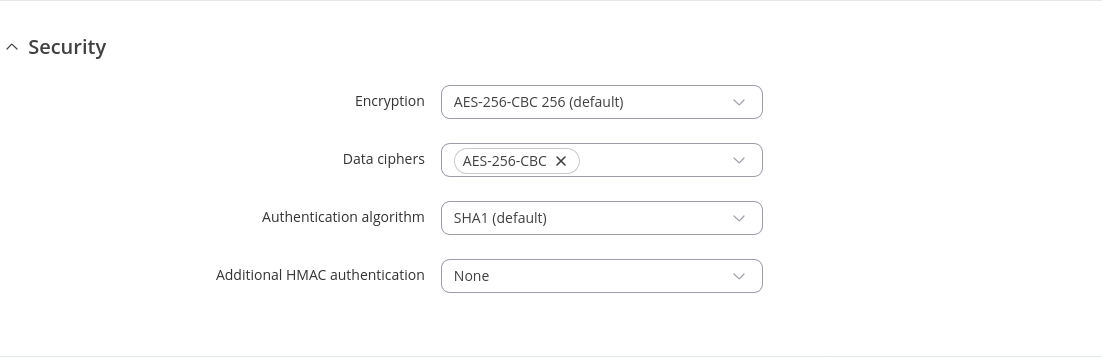
| Encryption | DES-CBC 64 | RC2-CBC 128 | DES-EDE-CBC 128 | DES-EDE3-CBC 192 | DESX-CBC 192 | BF-CBC 128 | RC2-40-CBC 40 | CAST5-CBC 128 | RC2-64CBC 64 | AES-128-CBC 128 | AES-128-CFB 128 | AES-128-CFB1 128 | AES-128-CFB8 128 | AES-128-OFB 128 | AES-128-GCM 128 | AES-192-CBC 192 | AES-192-CFB 192 | AES-192-CFB1 192 | AES-192-CFB8 192 | AES-192-OFB 192 | AES-192-GCM 192 | AES-256-CBC 256 | AES-256-CFB 256 | AES-256-CFB1 256 | AES-256-CFB8 256 | AES-256-OFB 256 | AES-256-GCM 256 | none; default: AES-256-CBC 256 | Packet encryption algorithm (cipher). |
| Data ciphers | depends on authentication; default: AES-256-CBC | Select allowed data ciphers from the list; add a custom value if needed. |
| Authentication algorithm | none | MD5 | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | HMAC authentication algorithm type. |
| TLS/TLS/Password/Password:Additional HMAC authentication | None | Authentication only (tls-auth) | Authentication only (tls-auth); default: None | Add an additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks. |
| TLS/TLS/Password/Password: HMAC key direction | 0 | 1; default: 1 | The HMAC authentication key direction value is arbitrary and must be opposite between communicating parties (or omitted entirely). |
| Certificates section | Value | Description |
|---|---|---|
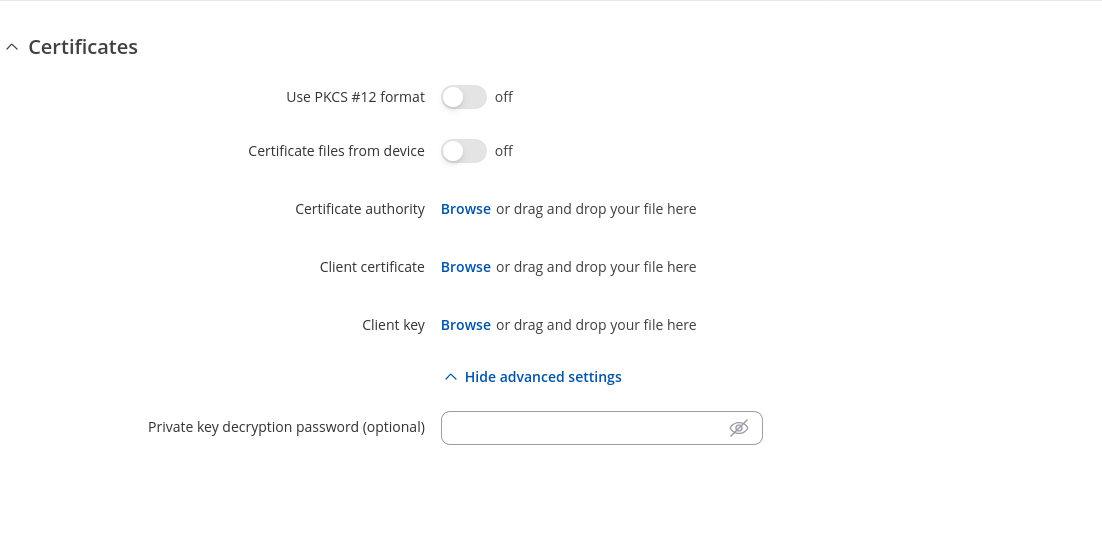
| TLS/TLS/Password/Password:Use PKCS #12 format | off | on; default: off | Use PKCS #12 archive file format to bundle all the members of a chain of trust. |
| TLS/TLS/Password/Password: PKCS #12 certificate chain | -(interactive button) | Uploads a PKCS #12 certificate chain file. |
| TLS/TLS/Password/Password: PKCS #12 passphrase | string; default: none | Passphrase to decrypt PKCS #12 certificates. |
| TLS/TLS/Password/Password: Certificate files from device | off | on; default: off | Choose this option if you want to select certificate files from the device. |
| TLS/TLS/Password/Password: Certificate authority | .ca file; default: none | The digital certificate verifies the ownership of a public key by the named subject of the certificate. |
| TLS/TLS/Password: Client certificate | .crt file; default: none | Identify a client or a user, authenticating the client to the server and establishing precisely who they are. |
| TLS/TLS/Password: Client key | .key file; default: none | It has been generated for the same purpose as a client certificate. |
| TLS/TLS/Password: Private key decryption password (optional) | string; default: none | Decrypt private key with password (Optional). |
| Static key: Static pre-shared key | .key file; default: none | A pre-shared key (PSK) is a shared secret that was previously shared between two parties using some secure channel before it needs to be used. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Authentication: TLS
- Olive for Authentication: TLS/Password
- Purple for Authentication: Static key
- Blue for Authentication: Password
- Brown for OpenVPN config from file
- After changing any of the parameters, don't forget to click the Save & Apply button located at the bottom-right side of the page.
OpenVPN Server
An OpenVPN server is an entity that waits for incoming connections from OpenVPN clients. Only one OpenVPN server instance is allowed to be added.
A server needs to have a public IP address in order to be available from the public network (the Internet).
| Server status | Value | Description |
|---|---|---|
| Export | -(interactive button) | Exports the instance configuration to .ovpn file. |
| Edit | -(interactive button) | Opens the instance configuration window. |
| Delete | -(interactive button) | Removes an instance. |
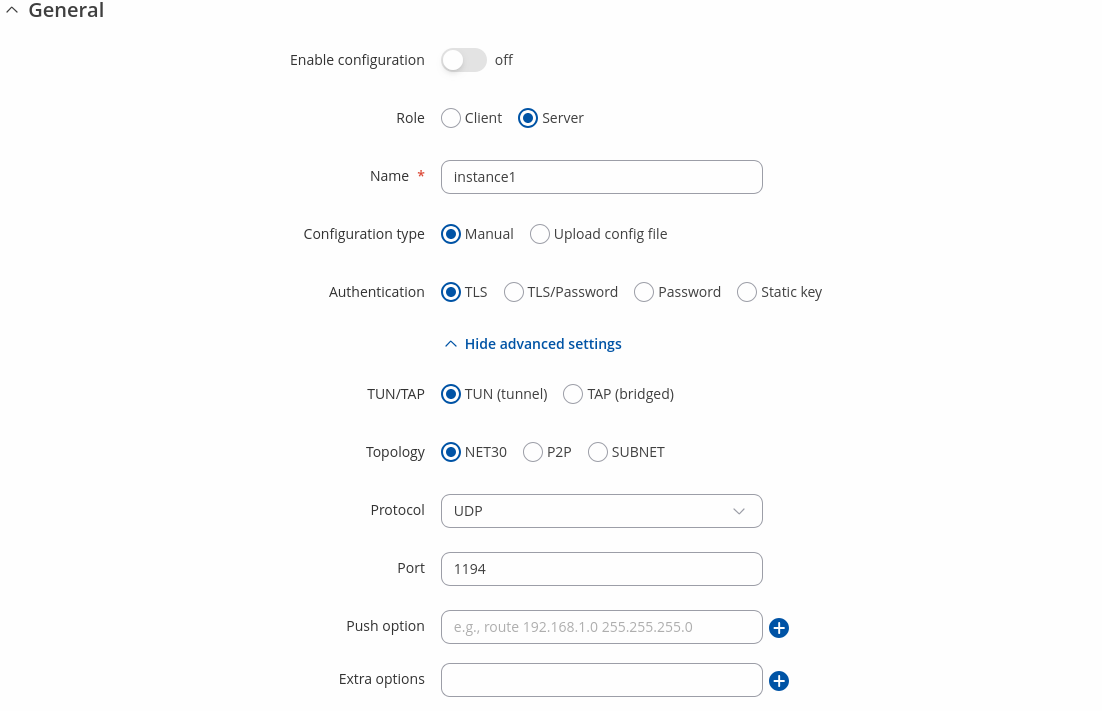
To begin configuration, click 'Add' button, select Role: Server. Refer to the figure and table below for information on the OpenVPN server's configuration fields:
| General section | Value | Description |
|---|---|---|
| Enable configuration | off | on; default: off | Enable current configuration. |
| Role | Client | Server; default: Server | Choose a role for OpenVPN isntance. |
| Name | string; default: instance1 | Name of the OpenVPN instance. |
| Configuration type | Manual | Upload config file; default: Manual | Choose configuration type. |
| Enable parsing | off | on; default: off | By enabling parsing, you can modify the configuration in the future. |
| OpenVPN configuration file | -(interactive button) | Upload OpenVPN configuration. Warning! This will overwrite your current configuration. |
| Authentication | TLS | TLS/Password | Password | Static key; default: TLS | Choose a method to authenticate your OpenVPN network. |
| TUN/TAP | TUN (tunnel) | TAP (bridged); default: TUN (tunnel) | Virtual VPN interface type. |
| Topology | NET30 | P2P | SUBNET (not shown with Static key); default: NET30 | Virtual addressing topology determines how IP addressing and routing are handled between the server and clients. |
| Protocol | UDP | TCP | UDP4 | TCP4 | UDP6 | TCP6; default: UDP | The transport protocol used for the connection. Note: UDP and TCP do not support IPv6 connections, use UDP6 or TCP6 instead. |
| Port | integer [0..65535]; default: 1194 | TCP/UDP port for both local and remote endpoints. Make sure that this port is open in the firewall. |
| Push option (not shown with Static key) | string; default: none | Push a configuration option back to the client for remote execution. |
| Extra options | string; default: none | Enter any additional options to be added to the OpenVPN configuration. If an option is already in use, the new option will take precedence. |
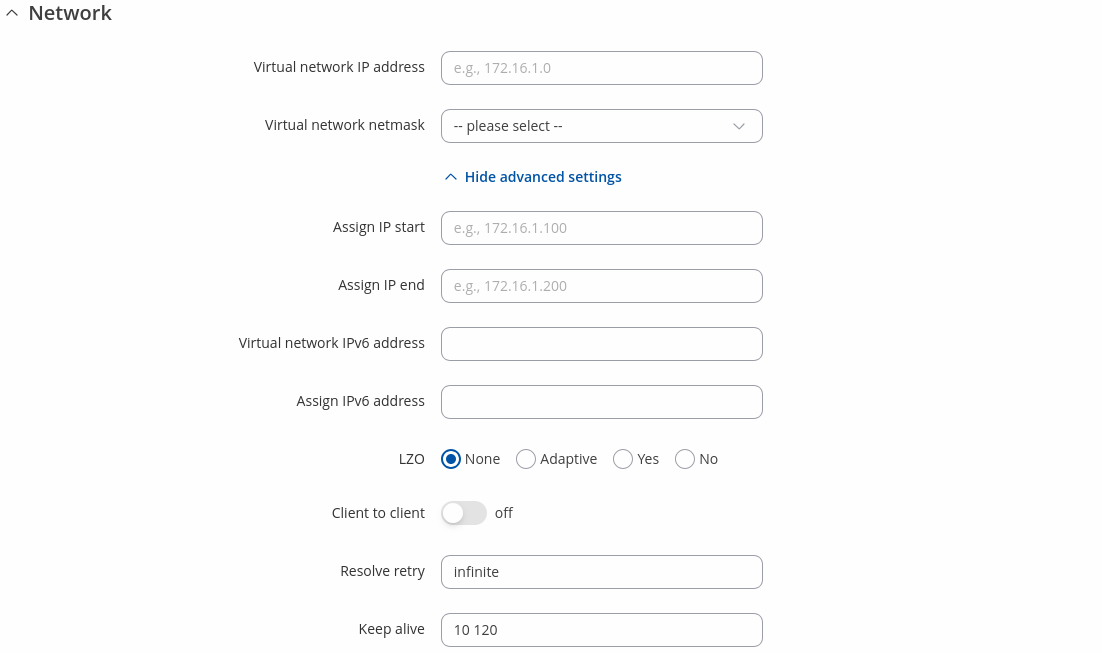
| Network section | Value | Description |
|---|---|---|
| TLS/TLS/Password/Password: Virtual network IP address | ip4; default: none | IP address used for the virtual network. |
| TLS/TLS/Password/Password: Virtual network netmask | netmask; default: none | Subnet mask used for the virtual network. |
| Static key: Local tunnel endpoint IP | ip; default: none | IP address of the virtual local network interface. |
| Static key: Remote tunnel endpoint IP | ip; default: none | IP address of the virtual remote network interface. |
| TLS/TLS/Password/Password: Assign IP start | IP; default: none | Assign IP addresses starting from a pool of subnets to be dynamically allocated to connecting clients. |
| TLS/TLS/Password/Password: Assign IP end | IP; default: none | Assign IP addresses ending at a pool of subnets to be dynamically allocated to connecting clients. |
| TLS/TLS/Password/Password: Virtual network IPv6 address | ip6; default: none | IPv6 address used for the virtual network. |
| TLS/TLS/Password/Password: Assign IPv6 address | ip6; default: none | Specify an IPv6 address pool for dynamic assignment to clients. |
| Static key: Local tunnel endpoint IPv6 | ip; default: none | IPv6 address of the virtual local network interface. |
| Static key: Remote tunnel endpoint IPv6 | ip; default: none | IPv6 address of the virtual remote network interface. |
| TAP (bridged): Bridge | lan | none; default: lan | Assign a TAP interface to a bridge.. |
| LZO | None | Adaptive | Yes | No; default: None | Use fast LZO compression. With LZO compression, your VPN connection will generate less network traffic. |
| Client to client | off | on; default: off | Allow client-to-client traffic. |
| Resolve retry | integer | infinite; default: infinite | Try to resolve the server hostname for X seconds before giving up. |
| Keep alive | two integers separated by a space; default: none | Try to keep the connection alive. Two values are required: ping_interval and ping_restart, e.g., 10 120. |
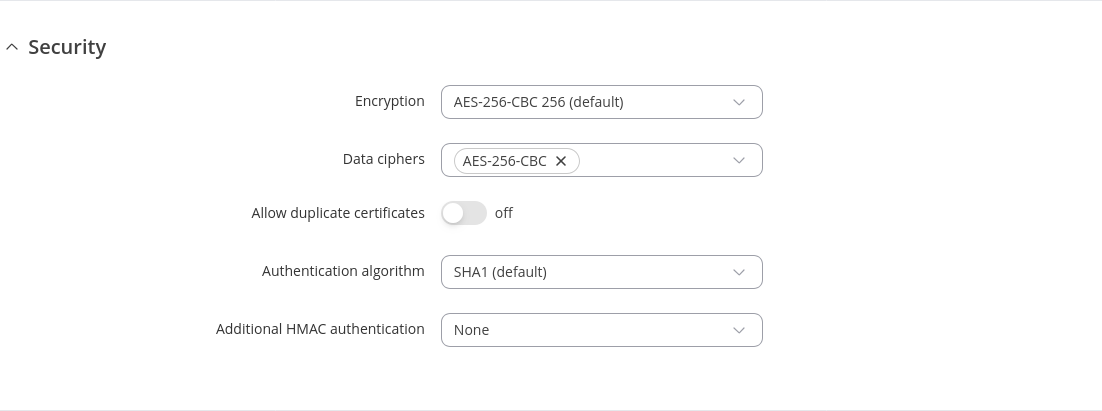
| Security section | Value | Description |
|---|---|---|
| TLS/Password/Password: Usernames & Passwords | -(interactive button) | File containing usernames and passwords against which the server can authenticate clients. Each username and password pair should be placed on a single line and separated by a space. |
| Encryption | DES-CBC 64 | RC2-CBC 128 | DES-EDE-CBC 128 | DES-EDE3-CBC 192 | DESX-CBC 192 | BF-CBC 128 | RC2-40-CBC 40 | CAST5-CBC 128 | RC2-64CBC 64 | AES-128-CBC 128 | AES-128-CFB 128 | AES-128-CFB1 128 | AES-128-CFB8 128 | AES-128-OFB 128 | AES-128-GCM 128 | AES-192-CBC 192 | AES-192-CFB 192 | AES-192-CFB1 192 | AES-192-CFB8 192 | AES-192-OFB 192 | AES-192-GCM 192 | AES-256-CBC 256 | AES-256-CFB 256 | AES-256-CFB1 256 | AES-256-CFB8 256 | AES-256-OFB 256 | AES-256-GCM 256 | none; default: AES-256-CBC 256 | Packet encryption algorithm (cipher). |
| Data ciphers | depends on authentication; default: AES-256-CBC | Select allowed data ciphers from the list; add a custom value if needed. |
| TLS/TLS/Password/Password: Allow duplicate certificates | off | on; default: off | All clients can have the same certificates. |
| Authentication algorithm | none | MD5 | SHA1 | SHA256 | SHA384 | SHA512; default: SHA1 | HMAC authentication algorithm type. |
| TLS/TLS/Password/Password:Additional HMAC authentication | None | Authentication only (tls-auth) | Authentication only (tls-auth); default: None | Add an additional layer of HMAC authentication on top of the TLS control channel to protect against DoS attacks. |
| TLS/TLS/Password/Password: HMAC key direction | 0 | 1; default: 1 | The HMAC authentication key direction value is arbitrary and must be opposite between communicating parties (or omitted entirely). |
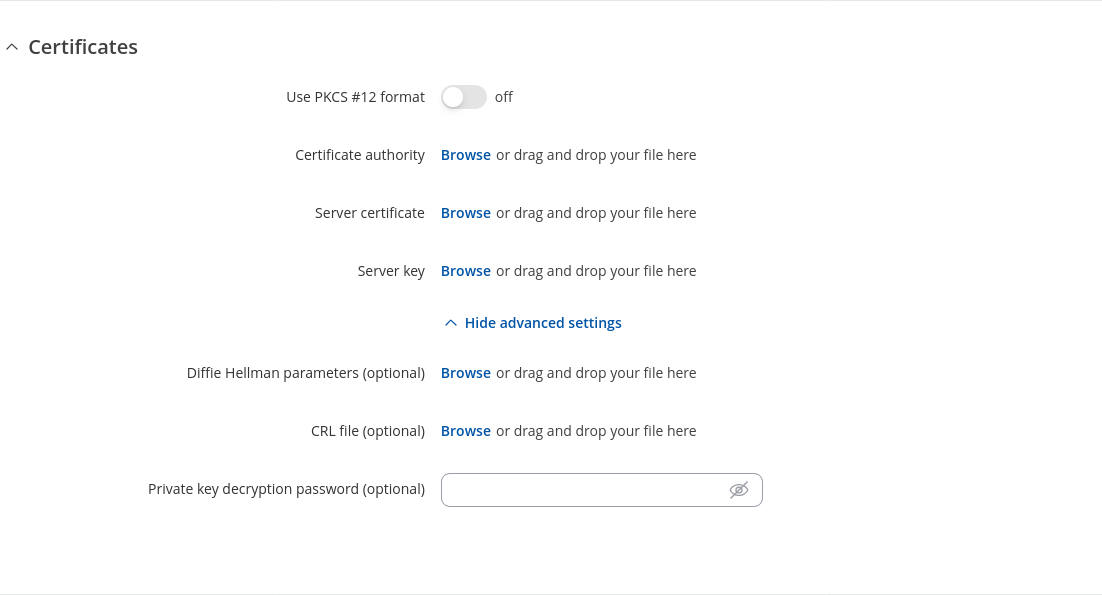
| Certificates section | Value | Description |
|---|---|---|
| TLS/TLS/Password/Password:Use PKCS #12 format | off | on; default: off | Use PKCS #12 archive file format to bundle all the members of a chain of trust. |
| TLS/TLS/Password/Password: PKCS #12 certificate chain | -(interactive button) | Uploads a PKCS #12 certificate chain file. |
| TLS/TLS/Password/Password: Certificate authority | .ca file; default: none | The digital certificate verifies the ownership of a public key by the named subject of the certificate. |
| TLS/TLS/Password/Password: Server certificate | .crt file; default: none | Certificate servers validate or certify keys as part of a public key infrastructure. |
| TLS/TLS/Password/Password: Server key | .key file; default: none | It has been generated for the same purpose as the server certificate. |
| TLS/TLS/Password/Password: Diffie Hellman parameters | .pem file; default: none | Diffie-Hellman key exchange is a specific method of exchanging cryptographic keys. |
| TLS/TLS/Password/Password: CRL file (optional) | .pem file | .crl file; Default: none | Revoking a certificate means to invalidate a previously signed certificate so that it can no longer be used for authentication purposes. Upload a .pem revocation file. |
| TLS/TLS/Password/Password: PKCS #12 passphrase | string; default: none | Passphrase to decrypt PKCS #12 certificates. |
| TLS/TLS/Password/Password: Private key decryption password (optional) | string; default: none | Decrypt private key with password (Optional). |
| Static key: Static pre-shared key | -(interactive button) | A pre-shared key (PSK) is a shared secret that was previously shared between two parties using some secure channel before it needs to be used. |
Additional notes:
- Some configuration fields become available only when certain other parameters are selected. The names of the parameters are followed by a prefix that specifies the authentication type under which they become visible. Different color codes are used for different prefixes:
- Red for Authentication: TLS
- Olive for Authentication: TLS/Passwords
- Purple for Authentication: Static key
- Blue for Authentication: Password
- Brown for OpenVPN config from file
- After changing any of the parameters, don't forget to click the Save & Apply button located at the bottom-right side of the page.
TLS Clients
TLS Clients is a way to differentiate clients by their Common Names (CN), which are found in the client certificate file. It can be used to assign specific VPN addresses to corresponding clients and bind them to their LAN addresses, making the server aware of which client has which LAN IP address.
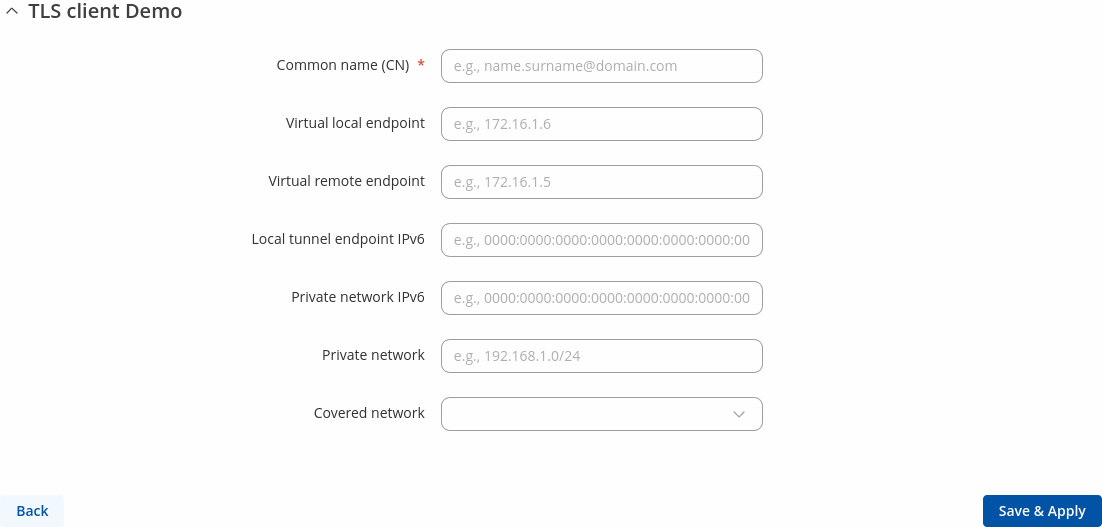
The TLS Clients section can be found in the OpenVPN Server configuration window, provided that the OpenVPN server uses TLS or TLS/Password authentication methods. To create a new TLS client, type in the new client‘s name in the text field found bellow the TLS Clients tab and click the 'Add' button. Refer to the figure and table below for information on the TLS Clients' configuration fields:
| Field | Value | Description |
|---|---|---|
| Common name (CN) | string; default: none | Client certificate CN field (e.g.,s [email protected]). |
| Virtual local endpoint | ip; default: none | Client’s local address in the virtual network. |
| Virtual remote endpoint | ip; default: none | Client’s remote address in the virtual network. |
| Local tunnel endpoint IPv6 | ip; default: none | IPv6 address of virtual local network interface. |
| Private network IPv6 | ip; default: none | Client’s private network (LAN) IPv6 address. |
| Private network | ip; default: none | Client’s private network (LAN) IP address. |
| Covered Network | network(); default: none | Selects which networks should be made accessible to this client. |
OpenVPN Server Brute-force Prevention
OpenVPN Servers with Authentication set to TLS/Password or Password, Protocol set to UDP and running on Port 1194 have a feature where after a client attempts to connect to the server 10 times with incorrect credentials (password and/or username) they are then blocked from the server.
To check which addresses are blocked one first needs to connect to their device's CLI.
After connecting to your device's CLI use the command ipset list and find the section named ipb_port. There under Members you should see all IP addresses that are blocked.
Name: ipb_port Type: hash:ip,port Revision: 5 Header: family inet hashsize 1024 maxelem 65536 Size in memory: 164 References: 2 Number of entries: 1 Members: 188.XXX.XXX.XXX,udp:1194
Another way to check blocked IP addresses is to use the command ubus call ip_block show. This will show all ip addresses that failed to connect to your device. If the counter atribute of the IP address entry is larger or equal then max_attempt_count then that IP address is blocked.
{
"globals": {
"max_attempt_count": 10
},
"ip_blockd 188.XXX.XXX.XXX": {
"ip": "188.XXX.XXX.XXX",
"port": "udp:1194",
"counter": "1"
},
"ip_blockd 188.XXX.XXX.XXX": {
"ip": "188.XXX.XXX.XXX",
"port": "udp:1194",
"counter": "10"
}
}
To unblock a blocked client's IP address use the command ubus call ip_block unblock '{"ip":"<blocked_ip_address>","port":"udp:1194"} (replace <blocked_ip_address> inside the quotes with your blocked IP address). If the IP address was unblocked succesfully you should see a similar response:
{
"unblocked": {
"ip": "188.XXX.XXX.XXX",
"port": "udp:1194"
}
}