TLS Certificates: Difference between revisions
No edit summary |
No edit summary |
||
| (48 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
<p style="color:red">The information in this page is updated in accordance with '''00.07. | <p style="color:red">The information in this page is updated in accordance with [https://wiki.teltonika-networks.com/view/FW_%26_SDK_Downloads'''00.07.17.2'''] firmware version.</p> | ||
==Summary== | ==Summary== | ||
| Line 6: | Line 6: | ||
==Certificate Generation== | ==Certificate Generation== | ||
If | If using a third-party service that requires TLS, all necessary files should be supplied by that service provider. However, if setting up your own solution, the following <b>TLS certificate generation methods</b> may be useful. | ||
===Teltonika Networks device=== | ===Teltonika Networks device=== | ||
| Line 18: | Line 18: | ||
====Generation of Certificate Authority (CA) Certificate & Key==== | ====Generation of Certificate Authority (CA) Certificate & Key==== | ||
---- | ---- | ||
The first step is to generate a Certificate Authority (CA) certificate, which will be used to sign both server and client certificates. | The first step is to generate a Certificate Authority (CA) certificate, which will be used to sign both server and client certificates. | ||
#Choose the file type as '''CA'''. | #Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | ||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | |||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#<li value="3">Choose the file type as '''CA'''. | |||
#On Teltonika routers, users can select from four '''Key Size''' options, ranging from '''512 bits to 4096 bits.''' | #On Teltonika routers, users can select from four '''Key Size''' options, ranging from '''512 bits to 4096 bits.''' | ||
#Enter the '''Common Name'''. This usually represents the fully qualified domain name (FQDN) of the server (e.g., example.com), but it can be any name of your choice. | #Enter the '''Common Name'''. This usually represents the fully qualified domain name (FQDN) of the server (e.g., example.com), but it can be any name of your choice. | ||
[[File:Tls certificates ca.png| | |||
#<li value=" | [[File:Tls certificates rutos create certificate ca pt1.png|border]] | ||
#<li value="6">By enabling '''Subject Information''', you can provide details about the entity to which the certificate is issued (Optional): | |||
::A. '''Country Code (CC)''': The two-letter country code (e.g., LT for Lithuania). | ::A. '''Country Code (CC)''': The two-letter country code (e.g., LT for Lithuania). | ||
::B. '''State or Province Name (ST)''': The name of the state or province (e.g., California). | ::B. '''State or Province Name (ST)''': The name of the state or province (e.g., California). | ||
| Line 29: | Line 38: | ||
::D. '''Organization Name (O)''': The name of the organization or company (e.g., Teltonika). | ::D. '''Organization Name (O)''': The name of the organization or company (e.g., Teltonika). | ||
::E. '''Organizational Unit Name (OU)''': The name of the department or unit within the organization (e.g., IT Department). | ::E. '''Organizational Unit Name (OU)''': The name of the department or unit within the organization (e.g., IT Department). | ||
::''These fields help to clearly identify the organization or individual associated with the certificate.'' | ::''These fields help to clearly identify the organization or individual associated with the certificate.'' | ||
[[File:Tls certificates ca | [[File:Tls certificates rutos create certificate ca pt2.png|border]] | ||
#<li value=" | #<li value="7"> Select the "'''On'''" option next to "'''Sign the Certificate'''." If not enabled, the Root CA will not sign or generate the new CA certificate. | ||
#Enter the period of how long CA certificate will be valid | #Enter the period of how long CA certificate will be valid | ||
#"'''Delete Signing Request'''" can be enabled, as it is not required after generation. | #"'''Delete Signing Request'''" can be enabled, as it is not required after generation. | ||
#Click [[File:Tls certificates | #Click the [[File:Tls certificates rutos create certificate ca create button.png|62px]] button | ||
[[File:Tls certificates ca | [[File:Tls certificates rutos create certificate ca pt3.png|border]] | ||
====Generation of Server Certificate & Key==== | ====Generation of Server Certificate & Key==== | ||
| Line 45: | Line 55: | ||
A server certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the server and facilitate secure, encrypted communications with clients. Generating a server certificate follows similar steps to those for creating a CA certificate. | A server certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the server and facilitate secure, encrypted communications with clients. Generating a server certificate follows similar steps to those for creating a CA certificate. | ||
#Select '''Server''' file type. | #Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | ||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | |||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#<li value="3">Select '''Server''' file type. | |||
#Select '''Key Size''' | #Select '''Key Size''' | ||
#Enter '''Common Name''' of the '''Server''' | #Enter '''Common Name''' of the '''Server''' | ||
| Line 53: | Line 68: | ||
#The system should automatically detect the CA certificate and key files from "Certificates Manager" tab. | #The system should automatically detect the CA certificate and key files from "Certificates Manager" tab. | ||
#"'''Delete Signing Request'''" (Optional) | #"'''Delete Signing Request'''" (Optional) | ||
#Click [[File:Tls certificates | #Click the [[File:Tls certificates rutos create certificate ca create button.png|58px]] button | ||
[[File:Tls certificates server.png| | |||
[[File:Tls certificates rutos create server certificate ca pt1.png|border]] | |||
====Generation of Client Certificate & Key==== | ====Generation of Client Certificate & Key==== | ||
---- | ---- | ||
A client certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the client and facilitate secure, encrypted communications with other clients and servers. Generating a | A client certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the client and facilitate secure, encrypted communications with other clients and servers. Generating a client certificate follows similar steps to those for creating a CA certificate. | ||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | |||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#Select '''Client''' file type. | #<li value="3">Select '''Client''' file type. | ||
#Select '''Key Size''' | #Select '''Key Size''' | ||
#Enter '''Common Name''' of the Client | #Enter '''Common Name''' of the Client | ||
| Line 69: | Line 90: | ||
#"'''Delete Signing Request'''" (Optional) | #"'''Delete Signing Request'''" (Optional) | ||
#"'''Private Key Decryption password'''" (Optional) | #"'''Private Key Decryption password'''" (Optional) | ||
#Click [[File:Tls certificates | #Click the [[File:Tls certificates rutos create certificate ca create button.png|58px]] button | ||
[[File:Tls certificates client.png| | [[File:Tls certificates rutos create client certificate ca pt1.png|border]] | ||
====Generation of DH Parameters==== | ====Generation of DH Parameters==== | ||
| Line 76: | Line 97: | ||
The '''DH parameters''' refers to the parameters used in the Diffie-Hellman key exchange. This cryptographic protocol allows two parties to generate a shared secret over an untrusted communication channel securely. In practical use, such as with VPNs, TLS/SSL, or routers, DH parameters are used to securely generate session keys for encrypting data. Generating a DH Parameters follows similar steps: | The '''DH parameters''' refers to the parameters used in the Diffie-Hellman key exchange. This cryptographic protocol allows two parties to generate a shared secret over an untrusted communication channel securely. In practical use, such as with VPNs, TLS/SSL, or routers, DH parameters are used to securely generate session keys for encrypting data. Generating a DH Parameters follows similar steps: | ||
#Select '''DH Parameters''' file type. | The first step is to generate a Certificate Authority (CA) certificate, which will be used to sign both server and client certificates. | ||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | |||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#<li value="3">Select '''DH Parameters''' file type. | |||
#Select '''Key Size''' | #Select '''Key Size''' | ||
#Enter '''Common Name''' | #Enter '''Common Name''' | ||
#Click [[File:Tls certificates | #Click the [[File:Tls certificates rutos create certificate ca create button.png|58px]] button | ||
[[File:Tls certificates dh.png| | [[File:Tls certificates rutos create dh certificate pt1.png|border]] | ||
====Generation of "Let's Encrypt" Certificate & Key==== | ====Generation of "Let's Encrypt" Certificate & Key==== | ||
| Line 86: | Line 113: | ||
Let's Encrypt provides free SSL/TLS certificates that are widely used for securing web services, VPNs, and other network communications. In practical use, such as with websites, routers, or VPNs, the Let's Encrypt certificate and key enable HTTPS connections or secure tunnels. Generating a Let's Encrypt certificate and key follows similar steps: | Let's Encrypt provides free SSL/TLS certificates that are widely used for securing web services, VPNs, and other network communications. In practical use, such as with websites, routers, or VPNs, the Let's Encrypt certificate and key enable HTTPS connections or secure tunnels. Generating a Let's Encrypt certificate and key follows similar steps: | ||
#Select the "'''Let's Encrypt'''" file type. | #Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | ||
#Enter the '''Domain''' name | #Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | ||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#<li value="3">Select the "'''Let's Encrypt'''" file type. | |||
#Enter the '''Domain''' name that is linked to the device's e public IP address. | |||
#Enable '''Automatic renewal''' if you'd like the certificates to be automatically renewed every 60 days (Optional). | #Enable '''Automatic renewal''' if you'd like the certificates to be automatically renewed every 60 days (Optional). | ||
#Click [[File:Tls certificates | #Click the [[File:Tls certificates rutos create certificate ca create button.png|58px]] button | ||
[[File:Tls certificates lets encrypt.png| | [[File:Tls certificates rutos create lets encrypt certificate pt1.png|border]] | ||
====Generation of SCEP Certificate & Key==== | ====Generation of SCEP Certificate & Key==== | ||
---- | |||
SCEP (Simple Certificate Enrollment Protocol) automates the process of obtaining digital certificates from a certificate authority (CA). The client submits a certificate request to the SCEP server, which acts as an intermediary between the client and the CA. This protocol facilitates secure authentication and encryption, simplifying certificate management and renewal, especially in large-scale deployments. | SCEP (Simple Certificate Enrollment Protocol) automates the process of obtaining digital certificates from a certificate authority (CA). The client submits a certificate request to the SCEP server, which acts as an intermediary between the client and the CA. This protocol facilitates secure authentication and encryption, simplifying certificate management and renewal, especially in large-scale deployments. | ||
#Select '''SCEP''' as the '''File type''' | #Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | ||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Create</span>''' option | |||
[[File:Tls certificates rutos create certificate.png|border]] | |||
#<li value="3">Select '''SCEP''' as the '''File type''' | |||
#Select '''Key Size''' | #Select '''Key Size''' | ||
#Enter the '''Common name''' | #Enter the '''Common name''' | ||
#Enter URL address of the SCEP server | #Enter URL address of the SCEP server | ||
#Enter the '''Challenge''' passkey (the unique value generated by the server for each session) | #Enter the '''Challenge''' passkey (the unique value generated by the server for each session) | ||
#Click | #Click the [[File:Tls certificates rutos create certificate ca create button.png|58px]] button | ||
[[File:Tls certificates scep | [[File:Tls certificates rutos create scep certificate pt1.png|border]] | ||
===Windows & Linux systems=== | ===Windows & Linux systems=== | ||
| Line 114: | Line 152: | ||
[[Category:Security]] | [[Category:Security]] | ||
==Certificates | ==Signing Certificates== | ||
If the "Sign the certificate" option is not enabled while creating the certificate, the router generates only the private key and the certificate signing request. This request is not a valid certificate until it is signed later, either by the router using its own certificate authority or by an external source. The router can also import certificate requests from external devices and sign them before they are used for secure communication. | |||
[[File:Tls certificates rutos certificate request pt1.png|border]] | |||
'''To sign certificates:''' | |||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Sign</span>''' option | |||
[[File:Tls certificates rutos sign certificates pt1.png|border]] | |||
#<li value="3">Enter the '''name''' for the new certificate. | |||
#Select the type of the certificate that you want to sign. | |||
#Select the uploaded or on-router generated '''Certificate request file'''. | |||
#Define the timeframe for how long this certificate will be valid. | |||
#Select the '''CA file''' that will sign the new certificate. | |||
#Select the '''CA key''' corresponding to the selected CA file. | |||
#Enable the '''Delete signing request''' option if the request is no longer needed after signing the certificate. | |||
#Enter all '''Hostnames''', '''Domains''', and '''Subdomains''' you want to secure with this certificate. Each will be included as a Subject Alternative Name (SAN) in your certificate (Optional). | |||
#Enter all IP addresses you want to secure with this certificate. Each will be included as a Subject Alternative Name (SAN) in your certificate (Optional). | |||
#Click the [[File:Tls certificates rutos sign button.png|45px]] button | |||
[[File:Tls certificates rutos sign certificates pt3.png|border]] | |||
==Importing Certificates== | |||
The router creates a private key and a certificate signing request which is not a valid certificate until signed by a certificate authority. The router has a built-in feature that allows it to sign these requests using its own certificate authority. This way the certificate becomes valid and can be used for secure communication. | |||
'''To import certificates & keys:''' | |||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Import</span>''' option | |||
[[File:Tls certificates rutos import certificates pt1.png|border]] | |||
#<li value="3">Click '''<span style="color:#0455a4"; font-size: 1.2em;>Browse</span>''' to upload a certificate or key. | |||
[[File:Tls certificates rutos import certificates pt2.png|border]] | |||
==Configuring Root CA== | |||
The router initially has a built-in Root CA, which acts as the top-level trusted certificate authority. This Root CA is used to sign intermediate CA certificates, which then sign other certificates utilized by the router or connected devices. This hierarchical structure creates a chain of trust, enabling the router to securely verify certificates within the system. Uploading or configuring your own Root CA on the router allows customization of this trust anchor, providing flexibility for integrating with private or custom certificate infrastructures. | |||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Configure Root CA</span>''' option | |||
[[File:Tls certificates rutos configure root ca pt1.png|border]] | |||
#<li value="3">Enable '''Root CA file from the device''' option, if Root CA file has already been imported. | |||
#Click '''<span style="color:#0455a4"; font-size: 1.2em;>Browse</span>''' to upload and apply a new certificate. | |||
[[File:Tls certificates rutos configure root ca pt2.png|border]] | |||
==Moving keys to TPM2== | |||
Some of our routers and gateways include a feature that allows cryptographic keys to be stored securely in the Trusted Platform Module 2.0 (TPM 2.0). This ensures the keys remain protected within the TPM hardware, preventing any direct extraction or access. All cryptographic operations using these keys take place inside the TPM, binding them to the device and offering stronger protection against theft, tampering, or unauthorized use. This greatly enhances the overall security of the router or gateway. | |||
List of the devices that supports this feature: https://teltonika-networks.com/products?page=2&features=2038 | |||
'''''Note:''' This functionality is available only on specific RUTX model variants that include eSIM hardware. Other models support this feature regardless of eSIM presence. For exact details, please refer to the Ordering section of the selected RUTX series product page to confirm the supported hardware versions.'' | |||
'''To move Key to TPM 2:''' | |||
#Click on the '''<span style="color:#0455a4"; font-size: 1.2em;>Certificate actions</span>''' button. | |||
#Select the '''<span style="color:#0455a4"; font-size: 1.2em;>Move key to TPM2</span>''' option | |||
[[File:Tls certificates rutos tpm2 pt1.png|border]] | |||
#<li value="3">Select the key that you want to move to TPM2 | |||
#Click on '''<span style="color:#0455a4"; font-size: 1.2em;>Move selected</span>''' button. | |||
[[File:Tls certificates | [[File:Tls certificates rutos tpm2 pt2.png|border]] | ||
Latest revision as of 08:35, 3 September 2025
Main Page > FAQ > Security > TLS CertificatesThe information in this page is updated in accordance with 00.07.17.2 firmware version.
Summary
Some services (such as OpenVPN, MQTT, etc.) on Teltonika Networks devices can be secured using TLS for encryption and authentication. This page discusses where one can obtain TLS certificates and key for this purpose.
Certificate Generation
If using a third-party service that requires TLS, all necessary files should be supplied by that service provider. However, if setting up your own solution, the following TLS certificate generation methods may be useful.
Teltonika Networks device
The easiest way to generate certificates and keys is by using the Certificate Generation page that is available in the device's WebUI:
- System → Administration → Certificates
Generation of Certificate Authority (CA) Certificate & Key
The first step is to generate a Certificate Authority (CA) certificate, which will be used to sign both server and client certificates.
- Click on the Certificate actions button.
- Select the Create option
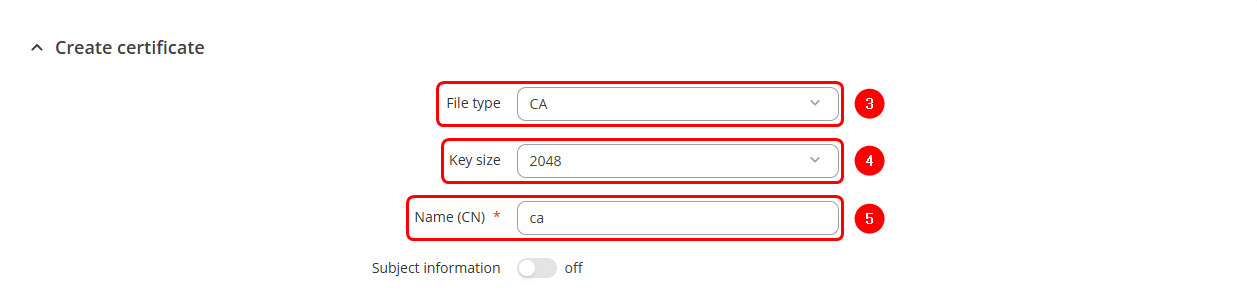
- Choose the file type as CA.
- On Teltonika routers, users can select from four Key Size options, ranging from 512 bits to 4096 bits.
- Enter the Common Name. This usually represents the fully qualified domain name (FQDN) of the server (e.g., example.com), but it can be any name of your choice.
- By enabling Subject Information, you can provide details about the entity to which the certificate is issued (Optional):
- A. Country Code (CC): The two-letter country code (e.g., LT for Lithuania).
- B. State or Province Name (ST): The name of the state or province (e.g., California).
- C. Locality Name (L): The city or locality (e.g., San Francisco).
- D. Organization Name (O): The name of the organization or company (e.g., Teltonika).
- E. Organizational Unit Name (OU): The name of the department or unit within the organization (e.g., IT Department).
- These fields help to clearly identify the organization or individual associated with the certificate.
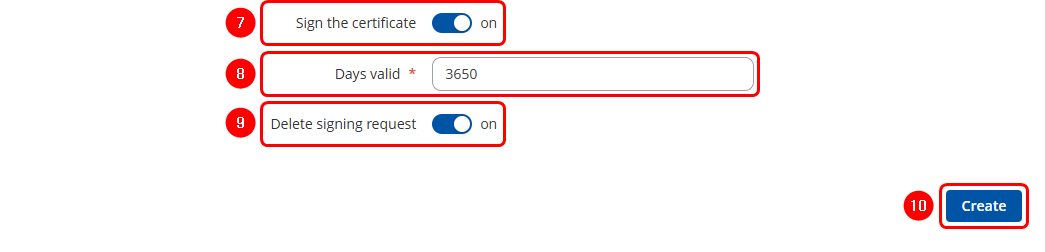
- Select the "On" option next to "Sign the Certificate." If not enabled, the Root CA will not sign or generate the new CA certificate.
- Enter the period of how long CA certificate will be valid
- "Delete Signing Request" can be enabled, as it is not required after generation.
- Click the
 button
button
Generation of Server Certificate & Key
A server certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the server and facilitate secure, encrypted communications with clients. Generating a server certificate follows similar steps to those for creating a CA certificate.
- Click on the Certificate actions button.
- Select the Create option
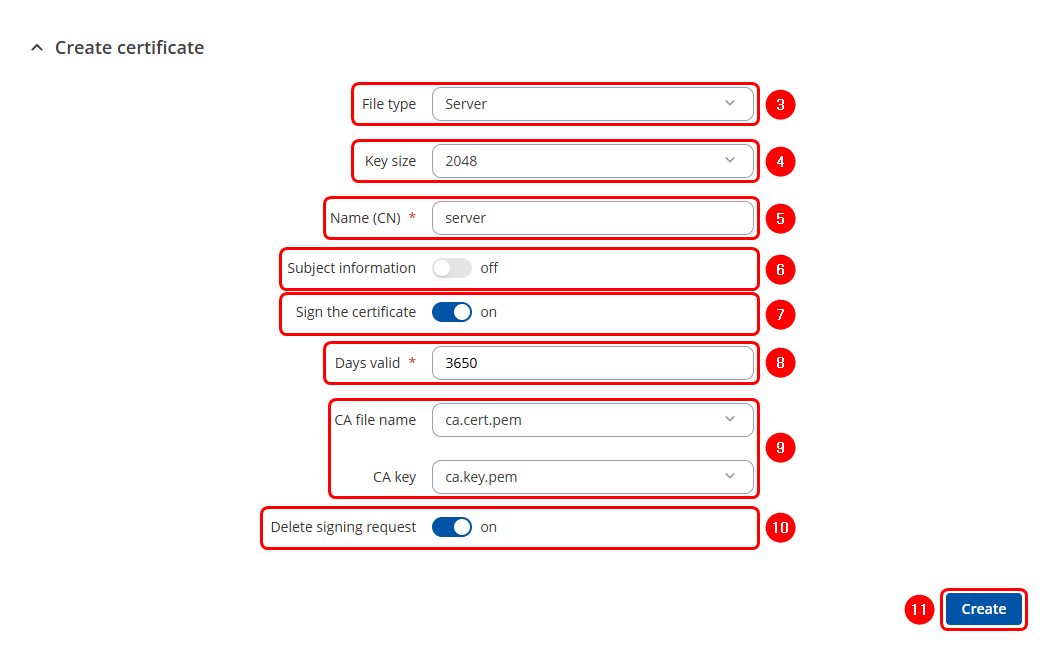
- Select Server file type.
- Select Key Size
- Enter Common Name of the Server
- Subject Information of the server(Optional)
- Select the "On" option next to "Sign the Certificate".
- Define how long the certificate will be valid.
- The system should automatically detect the CA certificate and key files from "Certificates Manager" tab.
- "Delete Signing Request" (Optional)
- Click the
 button
button
Generation of Client Certificate & Key
A client certificate, signed by a trusted Certificate Authority (CA), is used to authenticate the client and facilitate secure, encrypted communications with other clients and servers. Generating a client certificate follows similar steps to those for creating a CA certificate.
- Click on the Certificate actions button.
- Select the Create option
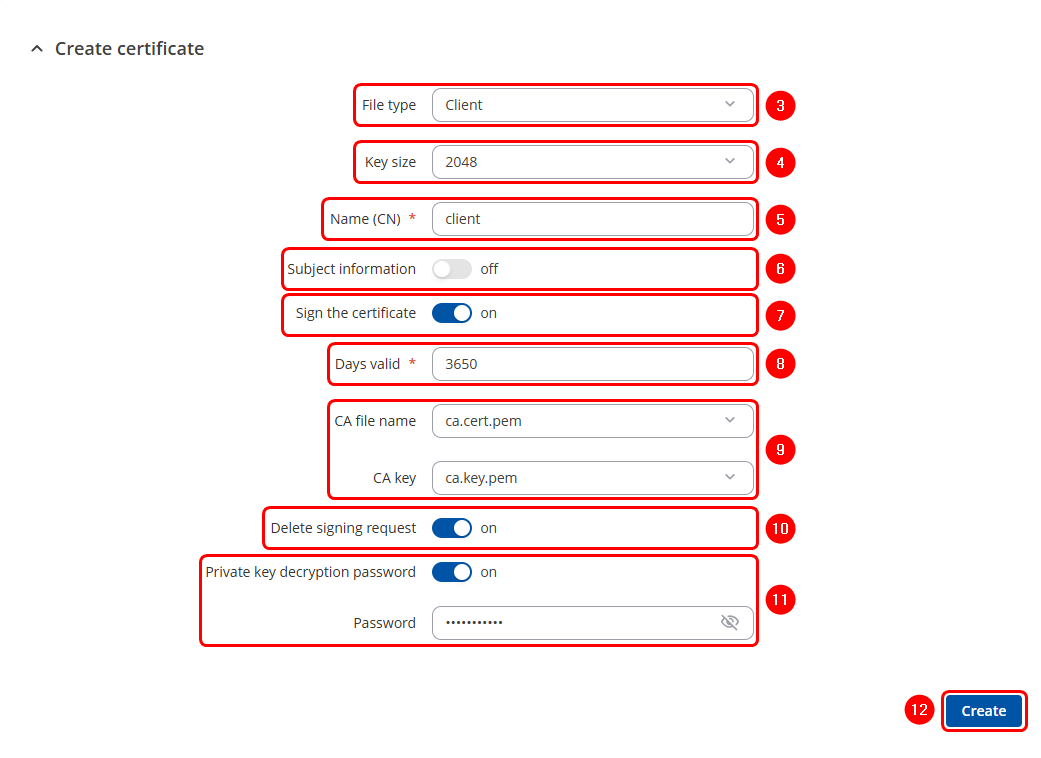
- Select Client file type.
- Select Key Size
- Enter Common Name of the Client
- Subject Information of the Client(Optional)
- Select the "On" option next to "Sign the Certificate".
- Define how long the certificate will be valid.
- The system should automatically detect the CA certificate and key files from the "Certificates Manager" tab.
- "Delete Signing Request" (Optional)
- "Private Key Decryption password" (Optional)
- Click the
 button
button
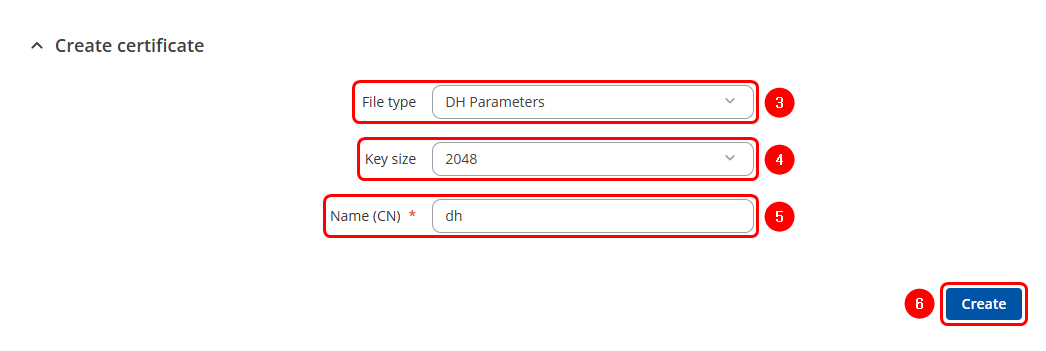
Generation of DH Parameters
The DH parameters refers to the parameters used in the Diffie-Hellman key exchange. This cryptographic protocol allows two parties to generate a shared secret over an untrusted communication channel securely. In practical use, such as with VPNs, TLS/SSL, or routers, DH parameters are used to securely generate session keys for encrypting data. Generating a DH Parameters follows similar steps:
The first step is to generate a Certificate Authority (CA) certificate, which will be used to sign both server and client certificates.
- Click on the Certificate actions button.
- Select the Create option
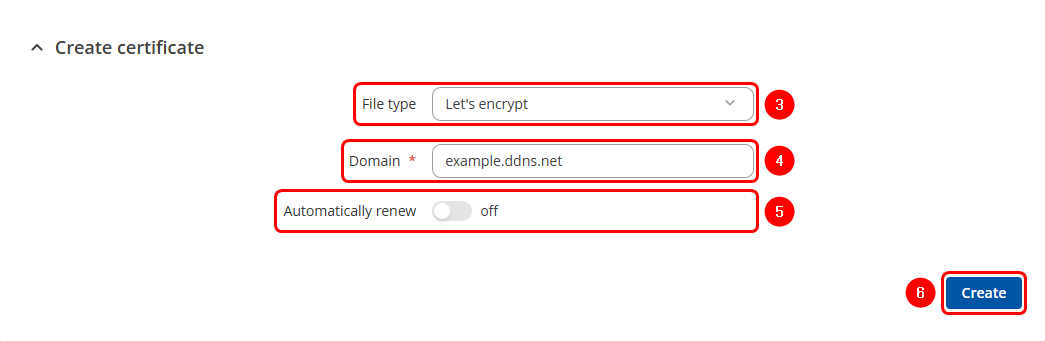
Generation of "Let's Encrypt" Certificate & Key
Let's Encrypt provides free SSL/TLS certificates that are widely used for securing web services, VPNs, and other network communications. In practical use, such as with websites, routers, or VPNs, the Let's Encrypt certificate and key enable HTTPS connections or secure tunnels. Generating a Let's Encrypt certificate and key follows similar steps:
- Click on the Certificate actions button.
- Select the Create option
- Select the "Let's Encrypt" file type.
- Enter the Domain name that is linked to the device's e public IP address.
- Enable Automatic renewal if you'd like the certificates to be automatically renewed every 60 days (Optional).
- Click the
 button
button
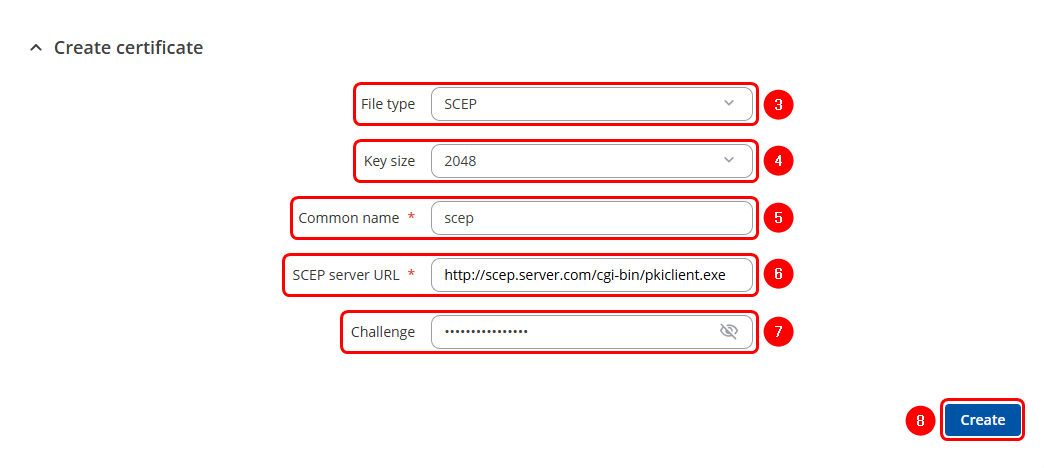
Generation of SCEP Certificate & Key
SCEP (Simple Certificate Enrollment Protocol) automates the process of obtaining digital certificates from a certificate authority (CA). The client submits a certificate request to the SCEP server, which acts as an intermediary between the client and the CA. This protocol facilitates secure authentication and encryption, simplifying certificate management and renewal, especially in large-scale deployments.
- Click on the Certificate actions button.
- Select the Create option
- Select SCEP as the File type
- Select Key Size
- Enter the Common name
- Enter URL address of the SCEP server
- Enter the Challenge passkey (the unique value generated by the server for each session)
- Click the
 button
button
Windows & Linux systems
You can also use third party software to generate the certificates on your computer. Guides are available for:
Signing Certificates
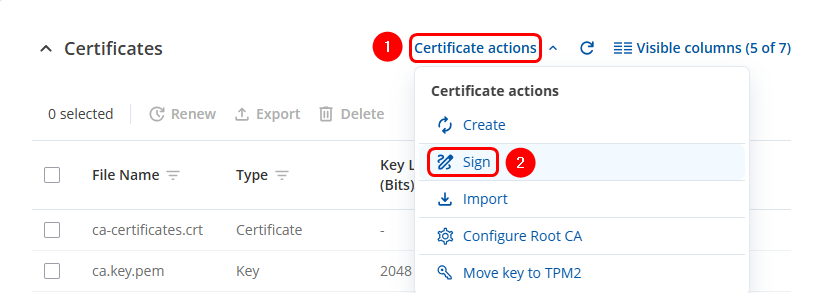
If the "Sign the certificate" option is not enabled while creating the certificate, the router generates only the private key and the certificate signing request. This request is not a valid certificate until it is signed later, either by the router using its own certificate authority or by an external source. The router can also import certificate requests from external devices and sign them before they are used for secure communication.

To sign certificates:
- Click on the Certificate actions button.
- Select the Sign option
- Enter the name for the new certificate.
- Select the type of the certificate that you want to sign.
- Select the uploaded or on-router generated Certificate request file.
- Define the timeframe for how long this certificate will be valid.
- Select the CA file that will sign the new certificate.
- Select the CA key corresponding to the selected CA file.
- Enable the Delete signing request option if the request is no longer needed after signing the certificate.
- Enter all Hostnames, Domains, and Subdomains you want to secure with this certificate. Each will be included as a Subject Alternative Name (SAN) in your certificate (Optional).
- Enter all IP addresses you want to secure with this certificate. Each will be included as a Subject Alternative Name (SAN) in your certificate (Optional).
- Click the
 button
button
Importing Certificates
The router creates a private key and a certificate signing request which is not a valid certificate until signed by a certificate authority. The router has a built-in feature that allows it to sign these requests using its own certificate authority. This way the certificate becomes valid and can be used for secure communication.
To import certificates & keys:
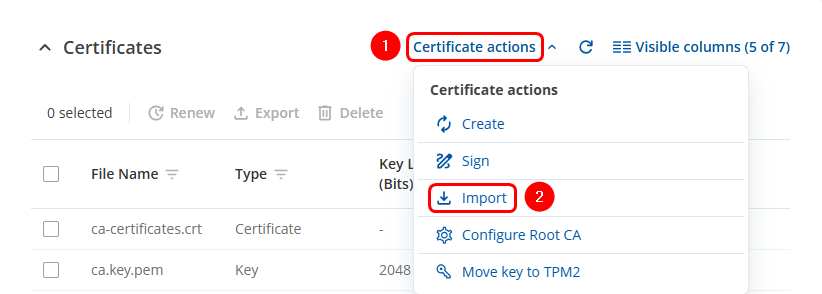
- Click on the Certificate actions button.
- Select the Import option
- Click Browse to upload a certificate or key.
Configuring Root CA
The router initially has a built-in Root CA, which acts as the top-level trusted certificate authority. This Root CA is used to sign intermediate CA certificates, which then sign other certificates utilized by the router or connected devices. This hierarchical structure creates a chain of trust, enabling the router to securely verify certificates within the system. Uploading or configuring your own Root CA on the router allows customization of this trust anchor, providing flexibility for integrating with private or custom certificate infrastructures.
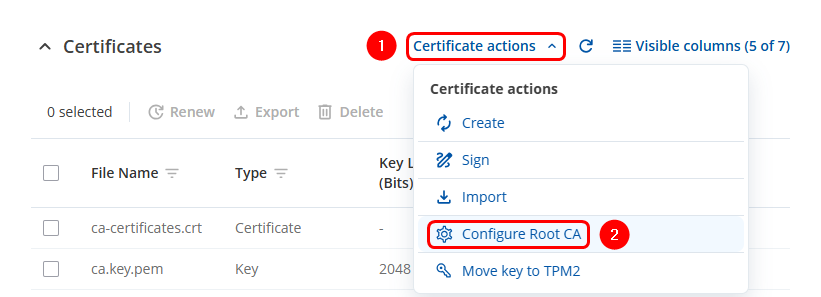
- Click on the Certificate actions button.
- Select the Configure Root CA option
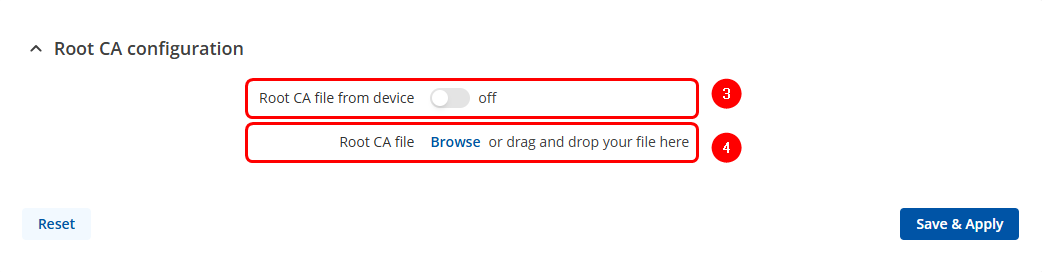
- Enable Root CA file from the device option, if Root CA file has already been imported.
- Click Browse to upload and apply a new certificate.
Moving keys to TPM2
Some of our routers and gateways include a feature that allows cryptographic keys to be stored securely in the Trusted Platform Module 2.0 (TPM 2.0). This ensures the keys remain protected within the TPM hardware, preventing any direct extraction or access. All cryptographic operations using these keys take place inside the TPM, binding them to the device and offering stronger protection against theft, tampering, or unauthorized use. This greatly enhances the overall security of the router or gateway.
List of the devices that supports this feature: https://teltonika-networks.com/products?page=2&features=2038
Note: This functionality is available only on specific RUTX model variants that include eSIM hardware. Other models support this feature regardless of eSIM presence. For exact details, please refer to the Ordering section of the selected RUTX series product page to confirm the supported hardware versions.
To move Key to TPM 2:
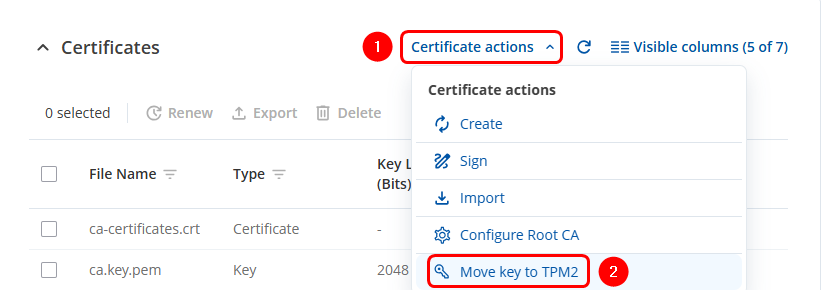
- Click on the Certificate actions button.
- Select the Move key to TPM2 option
- Select the key that you want to move to TPM2
- Click on Move selected button.