OpenVPN traffic split: Difference between revisions
Undo revision 72693 by 212.23.138.56 (talk) Tag: Undo |
Changed most of instruction |
||
| Line 10: | Line 10: | ||
'''Prerequisites''': | '''Prerequisites''': | ||
* | * Working OpenVPN connection with OpenVPN server with zone allowing traffic to internet | ||
* At least one end device (PC, Laptop) to configure the routers and test the set up | * At least one end device (PC, Laptop) to configure the routers and test the set up | ||
---- | ---- | ||
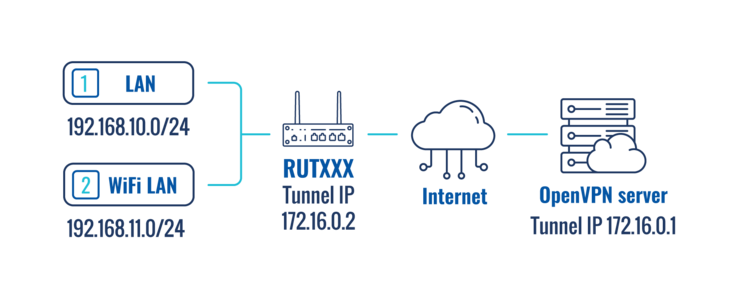
''' | '''Topology scheme''': | ||
[[File: | [[File:OpenVpn schema.png|alt=|749x749px]] | ||
The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client (virtual IP: ''' | The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client (virtual IP: '''172.16.0.2''') that is connected to a remote OpenVPN server (virtual IP '''172.16.0.1'''). The routers LAN/WiFi LAN IP addresses range from 192.168.1x.1 to 192.168.1x.254. | ||
When the scheme is realized, Devices in the | When the scheme is realized, Devices in the LAN range reach the Internet via the router's WAN and devices in the WiFi LAN range reach the Internet via the OpenVPN server effectively "adopting" the server's Public IP address. | ||
==Router configuration== | ==Router configuration== | ||
| Line 29: | Line 29: | ||
* First, you must create an OpenVPN client instance on your router. You can do this either via command line or from the router's WebUI, '''Services → VPN → OpenVPN''' section. We will not go into further detail on this because the client's configuration will depend on the OpenVPN server that you are connecting to. You can find detailed instructions on how to create and configure an OpenVPN client instance in our '''[[OpenVPN configuration examples]]''' article, which also contains information on how to configure an OpenVPN server on a RUTxxx router, if that is what you are using for this configuration. | * First, you must create an OpenVPN client instance on your router. You can do this either via command line or from the router's WebUI, '''Services → VPN → OpenVPN''' section. We will not go into further detail on this because the client's configuration will depend on the OpenVPN server that you are connecting to. You can find detailed instructions on how to create and configure an OpenVPN client instance in our '''[[OpenVPN configuration examples]]''' article, which also contains information on how to configure an OpenVPN server on a RUTxxx router, if that is what you are using for this configuration. | ||
---- | ---- | ||
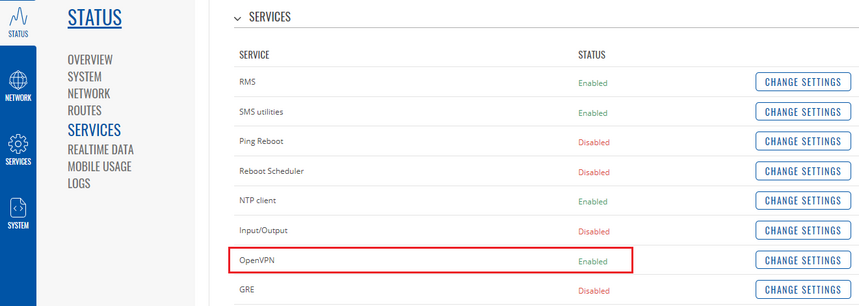
* Once you have configured your OpenVPN client, you should probably test whether the OpenVPN connection is operational as this will make troubleshooting easier later on. The easiest way to do so is to login to the router's WebUI and check OpenVPN status in '''Status → | * Once you have configured your OpenVPN client, you should probably test whether the OpenVPN connection is operational as this will make troubleshooting easier later on. The easiest way to do so is to login to the router's WebUI and check OpenVPN status in '''Status → Services:''': | ||
[[File: | [[File:OpenVPN.png|alt=|859x859px]] | ||
---- | ---- | ||
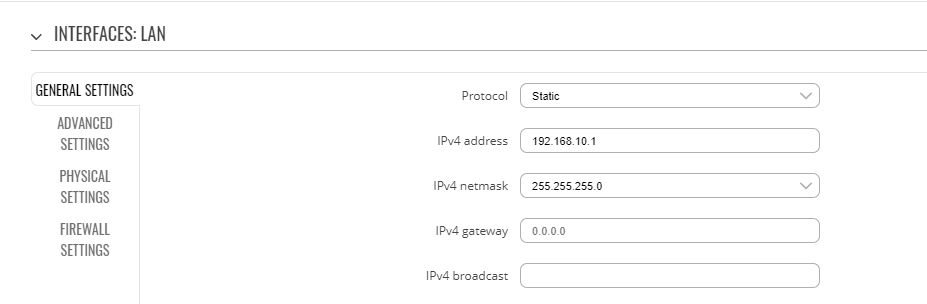
* If the connection was successful, we can start the traffic split configuration. First, we'll need to | * If the connection was successful, we can start the traffic split configuration. First, we'll need to Edit LAN network to use IP address 192.168.10.1. It can be done in section '''Network''' '''→ Interfaces → General settings:''' [[File:LAN.png]] | ||
---- | ---- | ||
* Next, we'll need to | * Next, we'll need to create wireless interface to use a custom network (wifi_lan) and disable encryption for convenience. In order to do this, navigate '''Network''' '''→ Wireless''' and click '''edit:''' | ||
<ul> | <ul> | ||
<li> | <li> | ||
Revision as of 12:18, 6 September 2021
Main Page > General Information > Configuration Examples > VPN > OpenVPN traffic splitIntroduction
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
This article provides a guide on how to configure an OpenVPN client on a RUTxxx router in such a way that a part of the router's LAN clients reach the Internet through the OpenVPN server (web proxy) and the other part reaches the Internet through the router's WAN (mobile, wired or WiFi connection). It should also be noted that this guide is aimed at more advanced users and, therefore, skips some of the more self-explanatory steps in order to preserve the overall coherence of the article. For example, the step-by-step configuration of the OpenVPN client instance will be left out and only comments on certain relevant parameters will be provided. If you feel this lack of information impedes your ability to configure the setup, we suggest you check out our OpenVPN configuration examples for reference and our guide on generating TLS certificates.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- Working OpenVPN connection with OpenVPN server with zone allowing traffic to internet
- At least one end device (PC, Laptop) to configure the routers and test the set up
Topology scheme:
The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client (virtual IP: 172.16.0.2) that is connected to a remote OpenVPN server (virtual IP 172.16.0.1). The routers LAN/WiFi LAN IP addresses range from 192.168.1x.1 to 192.168.1x.254.
When the scheme is realized, Devices in the LAN range reach the Internet via the router's WAN and devices in the WiFi LAN range reach the Internet via the OpenVPN server effectively "adopting" the server's Public IP address.
Router configuration
Most of the router's configuration will be done via a command line interface. You can find detailed instruction on all command line interfaces supported by RUTxxx routers here. Choose one that is available or most preferred by you and you will still be able to follow the guide step-by-step regardless of which method you chose as the commands used will remain identical.
OpenVPN client
- First, you must create an OpenVPN client instance on your router. You can do this either via command line or from the router's WebUI, Services → VPN → OpenVPN section. We will not go into further detail on this because the client's configuration will depend on the OpenVPN server that you are connecting to. You can find detailed instructions on how to create and configure an OpenVPN client instance in our OpenVPN configuration examples article, which also contains information on how to configure an OpenVPN server on a RUTxxx router, if that is what you are using for this configuration.
- Once you have configured your OpenVPN client, you should probably test whether the OpenVPN connection is operational as this will make troubleshooting easier later on. The easiest way to do so is to login to the router's WebUI and check OpenVPN status in Status → Services::
- If the connection was successful, we can start the traffic split configuration. First, we'll need to Edit LAN network to use IP address 192.168.10.1. It can be done in section Network → Interfaces → General settings:
- Next, we'll need to create wireless interface to use a custom network (wifi_lan) and disable encryption for convenience. In order to do this, navigate Network → Wireless and click edit:
- When you're finished, press the "Esc" button and type :wq to save the changes and exit the editor (Control + Z to exit without saving). The values highlighted in red are dependent on your configuration and will most likely need to be changed:
-
option ifname 'tun_c_MyClient' - your OpenVPN interface's name. You can check it with this command: ifconfig | grep tun. The response should look something like this:
tun_c_MyClient Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
NOTE: if the response is empty, your OpenVPN connection might be down.
- option gateway '10.0.0.5' - your virtual remote endpoint (or P-t-P). You can check it with this command: ifconfig tun_c_MyClient. Replace the MyClient part with your own OpenVPN interface name. The response should look something like this:
tun_c_MyClient Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 inet addr:10.0.0.6 P-t-P:10.0.0.5 Mask:255.255.255.255 UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1 RX packets:62249 errors:0 dropped:0 overruns:0 frame:0 TX packets:62698 errors:0 dropped:1 overruns:0 carrier:0 collisions:0 txqueuelen:100 RX bytes:53341014 (50.8 MiB) TX bytes:11974147 (11.4 MiB) - option src '192.168.1.128/25' - devices from this IP range will use the OpenVPN server as the default gateway to the Internet.
- Next, we'll need to create short custom script /etc/openvpn/up.sh, that would add a route which makes the specified LAN range reach the Internet via the OpenVPN server:
echo -e '#!/bin/ash'"\n"'ip route add default via 10.0.0.5 table rt' > /etc/openvpn/up.sh
- Next, we'll need to grant executable permissions to newly created script:
chmod +x /etc/openvpn/up.sh
- Finally, we'll need to edit router's OpenVPN script /etc/init.d/openvpn, so that it would execute previously created /etc/openvpn/up.sh script each time OpenVPN tunnel is established. Type vi /etc/init.d/openvpn and press the "I" button on your keyboard to begin editing. Scroll down until you will find start_instance() function. Add the following lines, highlighted in red, at the end of start_instance() function:
start_instance() {
local s="$1"
.....
.....
.....
config_list_foreach "$s" "_extra" append_extended_params
openvpn_add_instance "$s" "/var/etc" "openvpn-$s.conf" "/tmp/openvpn-$s.status"
echo 'script-security 2' >> $OPENVPN_CONFIG
echo 'up /etc/openvpn/up.sh' >> $OPENVPN_CONFIG
}
When you're finished, press the "Esc" button and type :wq to save the changes and exit the editor (Control + Z to exit without saving).
- When your done with the configuration, don't forget to restart the relevant services. You can do this by restarting the entire router (reboot command) or just restart the network and openvpn services:
/etc/init.d/network restart /etc/init.d/openvpn restart
NOTE: restarting the network service will cause a brief data connection loss.
Testing the setup
If you've followed the steps presented above, your configuration should be finished. But as with any other configuration, it is always wise to test the setup in order to make sure that it works properly. In order to test this particular configuration, a few steps have to be taken:
- Check the newly created routing table with the ip route show table rt command (where rt is table's name). If everything is in order, the response should contain this line (values highlighted in red should be from your own configuration):
default via 10.0.0.5 dev tun_c_MyClient proto static
- Check whether the correct IP rule has been added. You can do this with the ip rule. The response should look something like this (the rule from our configuration is highlighted in red):
0: from all lookup local
10: from 192.168.1.128/25 iif br-lan lookup rt
32766: from all lookup main
32767: from all lookup default
- Check whether devices with IPs from different ranges reach the Internet through the default gateway. If you only have one device at your disposal at the time, you can configure a static IP address (guide for Linux users here; for Windows here) for that device in one range and later in the other. According to our configuration, if a device's IP falls in the range of 192.168.1.1 - 192.168.1.127, its Public IP should be that of the router's; if the IP falls in the range of 192.168.1.128 - 192.168.1.254, its Public IP should be that of the OpenVPN server. You can check the Public IP address in this website.
If all of the above is in order, congratulations, your configuration works!
See also
- Other OpenVPN related articles from our wiki:
- How to generate TLS certificates (Windows)? - a guide on generating TLS certificates for Windows users
- OpenVPN Manual section - OpenVPN section of the router's manual
- OpenVPN configuration examples - basic OpenVPN configuration scenarios with detailed examples
- OpenVPN client on Windows - an example describing how to configure an OpenVPN client on a Windows computer
- OpenVPN server on Windows - an example describing how to configure an OpenVPN server on a Windows computer
External links
- http://www.whatsmyip.org/ - for checking your Public IP address