L2TP over IPsec RutOS
Introduction
Because of the lack of confidentiality inherent in the Layer 2 Networking Protocol (L2TP) protocol, Internet Protocol Security (IPsec) is often used to secure L2TP packets by providing confidentiality, authentication and integrity. The combination of these two protocols is generally known as L2TP over IPsec (or simply L2TP/IPsec).
This article provides a guide on how to configure L2TP/IPsec on RUTxxx routers. It should also be noted that this guide is aimed at more advanced users and, therefore, skips some of the more self-explanatory steps in order to preserve the overall coherence of the article. For example, instead of showing how to add new instances step by step, it is only mentioned in a short sentence. If you feel this lack of information impedes your ability to configure the setup, we suggest you check out our separate configuration guides on IPsec and L2TP for reference.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- Two RUTxxx routers of any type
- At least one router with a Public Static or Public Dynamic IP addresses
- At least one end device (PC, Laptop, Tablet, Smartphone) to configure the routers
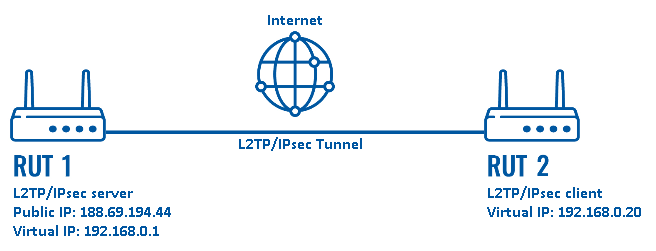
Configuration scheme:
The figure above depicts the L2TP/IPsec scheme. It is fairly similar to the L2TP and IPsec configuration schemes - the router with the Public IP address (RUT1) acts as the L2TP/IPsec server and the other router (RUT2) acts a client. L2TP connects the networks of RUT1 and RUT2 and IPsec provides the encryption for the L2TP tunnel.
When the scheme is realized, L2TP packets between the endpoints are encapsulated by IPsec. Since the L2TP packet itself is wrapped and hidden within the IPsec packet, the original source and destination IP address is encrypted within the packet.
RUT1 Configuration(Server)
As mentioned in the prerequisites section, the router that acts as the server must have a Public Static or Public Dynamic IP address (more information on the subject can be found here). If that is in order, we should start configuring the server.
L2TP
|
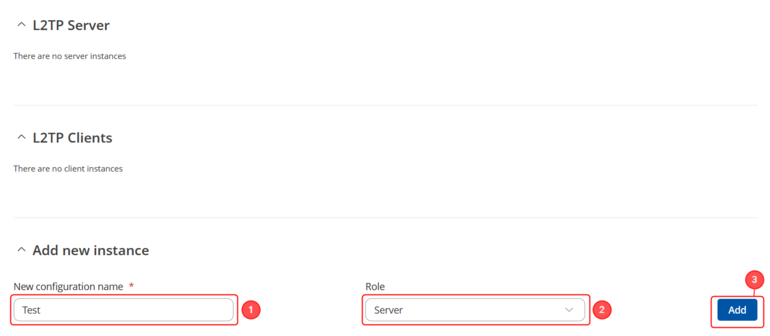
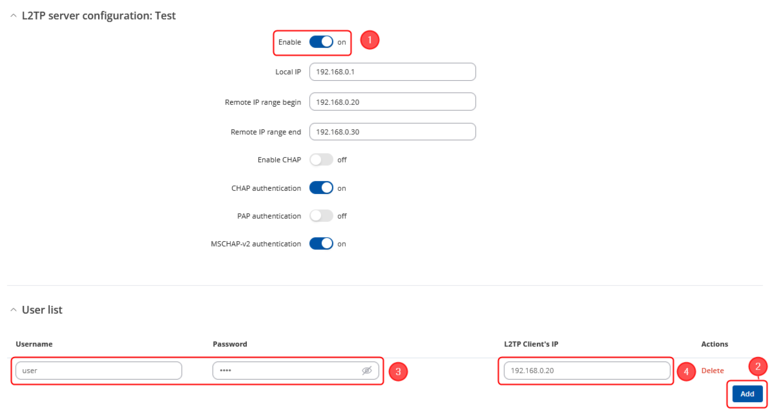
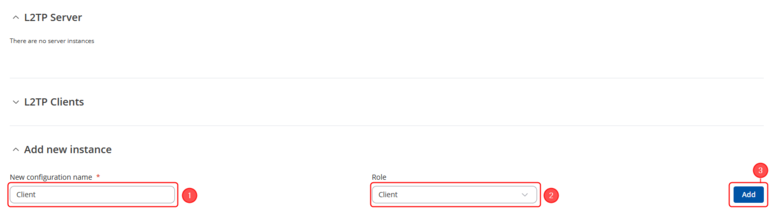
Login to the router's WebUI and navigate to the Services → VPN → L2TP page and do the following:
|
|
IPsec
|
Go to the Services → VPN → IPsec page and do the following:
|
|
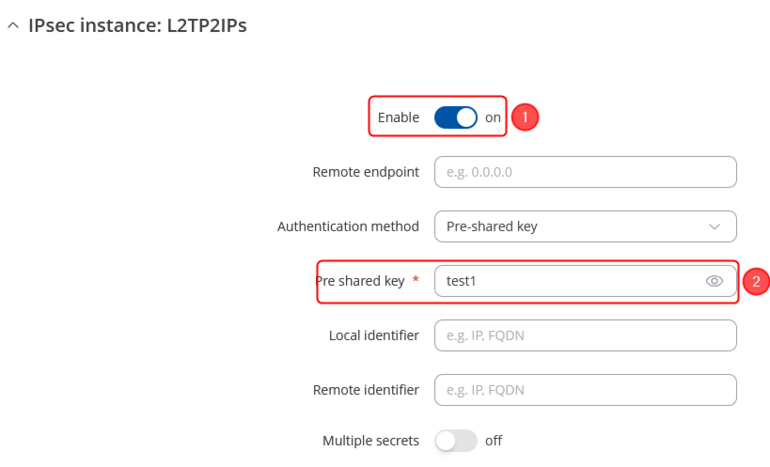
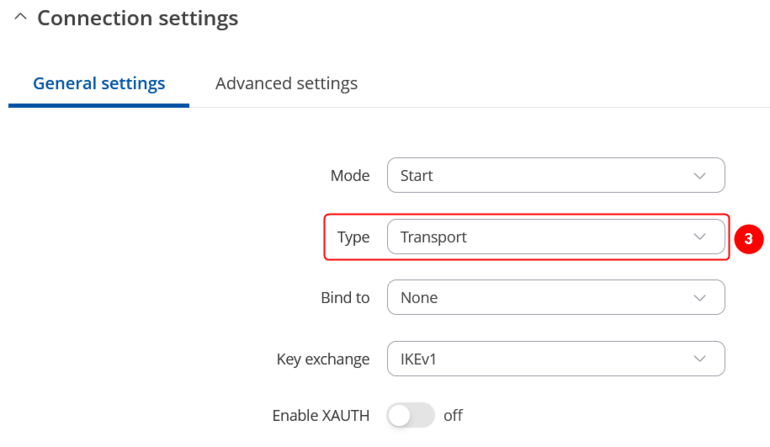
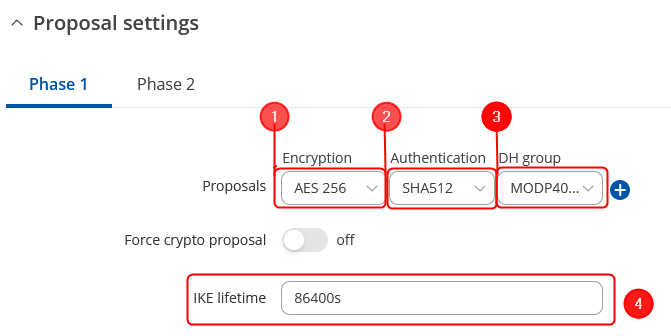
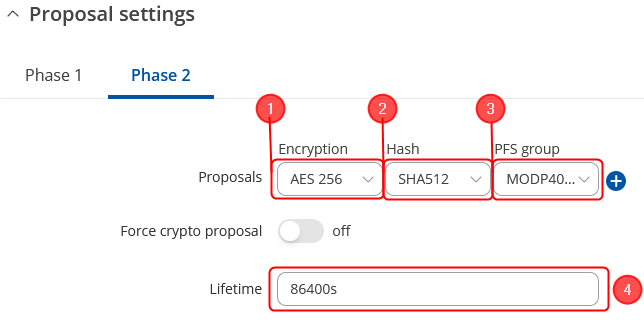
In the IPsec Configuration page, do the following (and leave the rest as defaults, unless your specific configuration requires otherwise):
|
Do not forget to Save changes. |
Note: This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.
Make the following changes:
|
|
RUT2 Configuration(client)
Now let's configure the L2TP/IPsec Client.
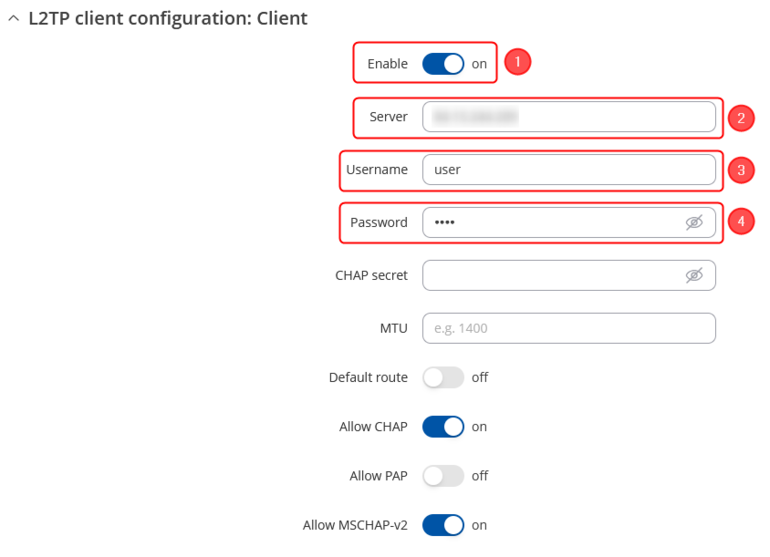
L2TP
|
Login to the router's WebUI and navigate to the Services → VPN → L2TP page and do the following:
|
|
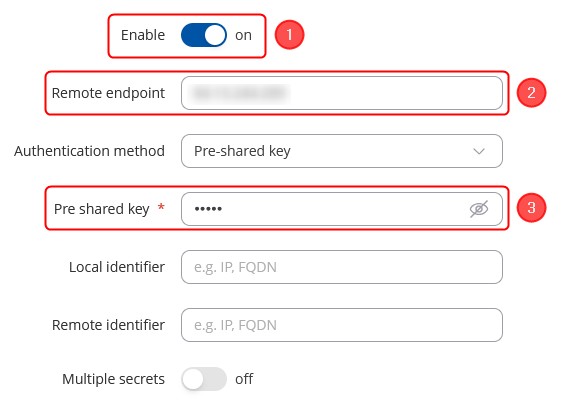
IPsec
|
Go to the Services → VPN → IPsec page and do the following:
|
|
In the IPsec Configuration page, do the following (and leave the rest as defaults, unless your specific configuration requires otherwise):
|
Do not forget to Save changes. |
Note: This is only an example of a secure configuration. Other algorithms or even combinations of them could be used. However, we strongly recommend refraining from using older encryption and hashing algorithms unless support for certain legacy systems is required.
Make the following changes:
|
|
Testing the setup
If you've followed all the steps presented above, your configuration should be finished. But as with any other configuration, it is always wise to test the setup in order to make sure that it works properly.
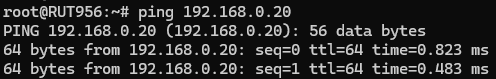
To test an L2TP connection, login to one of the routers' WebUIs and go to Services → CLI. Login with user name: root and the router's admin password. You should then be able to ping the opposite instance, i.e., if you logged in to the server's CLI, you should be able to ping the client's virtual IP address, and vice versa. To use a ping command, type ping <ip_address> and press the "Enter" key on your keyboard:
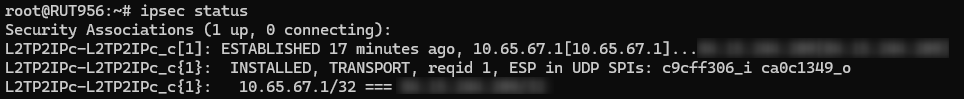
Using the ipsec status or we can use ipsec statusall command for a more verbose output. With these commands we can see that the IPsec tunnel is successfully established on RUT router. The command output on a RUT device:
If the ping requests are successful and ipsec status shows information, congratulations, your setup works! If not, we suggest that you review all steps once more.
See also
- Other types of VPNs suported by RUTxxx devices: