Difference between revisions of "DMVPN with IPsec Phase 3"
PauliusRug (talk | contribs) |
m |
||
| (44 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | |||
| − | |||
==Introduction== | ==Introduction== | ||
| Line 9: | Line 7: | ||
'''DMVPN''' has three phases that route data differently: | '''DMVPN''' has three phases that route data differently: | ||
| − | Phase 1: All traffic | + | Phase 1: All traffic flows from the spoke to and through the hub. |
| − | Phase 2: | + | Phase 2: Start with Phase 1 then allows spoke-to-spoke tunnels based on demand and triggers. Phase 2 has different routing, where packet forwarding is being done using the IP routing table. |
| − | Phase 3: | + | Phase 3: Starts with Phase 1 and improves the scalability and has fewer restrictions than Phase 2. Phase 3 allows the summarization of routes from hub to spokes. So again spokes wouldn’t need specific routes to other spokes networks. |
| Line 23: | Line 21: | ||
<ul> | <ul> | ||
| − | <li>2 Teltonika Routers for | + | <li>2 Teltonika Routers for SPOKES</li> |
| − | <li>1 Teltonika Router for | + | <li>1 Teltonika Router for HUB with a public IP address</li> |
<li>A PC to configure the routers</li> | <li>A PC to configure the routers</li> | ||
</ul> | </ul> | ||
| + | ==HUB configuration== | ||
| − | + | This section contains information on how to configure DMVPN <b>HUB</b>. Firstly, we'll configure the DMVPN instance to make the connection possible. Then we'll set the <b>Border Gateway Protocol</b> (<b>BGP</b>) parameters as our dynamic routing solution. | |
| − | |||
| + | <b>Note</b>: at the moment, BGP is the only stable dynamic routing solution that can work with DMVPN. | ||
| − | == | + | ===HUB configuration: DMVPN=== |
| + | ---- | ||
| + | Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | ||
| − | + | <b>Step 1</b>: create a new DMVPN instance: | |
| − | + | - Select your HUB interface in the Tunnel source field | |
| − | - | + | - Set Local GRE interface IP address (for example, 10.0.0.254) |
| − | - | + | - Set GRE interface netmask to 255.255.255.0 (for entire subnet or according to how many spokes we expect to connect to this hub) |
| − | - | + | - Set GRE MTU value to 1420 (or even slightly lower - 1400 if a mobile interface is used) |
| − | |||
| − | + | - Outbound/inbound keys are optional, for this example we will leave it at default | |
| + | |||
| + | - Set IPsec Pre-shared key (we used simple 123456 for this example) | ||
| + | |||
| + | <br>[[File:Dmvpn phase3 example1.png|alt=|border]] | ||
---- | ---- | ||
| − | + | <b>Step 2</b>: configure DMVPN Phase 1 parameters: | |
| + | |||
| + | - Encryption algorithm - AES 128 | ||
| − | + | - Authentication SHA1 | |
| − | + | - DH group - MODP1024 | |
| − | |||
| − | + | <nowiki>###</nowiki> I don't recommend these parameters, they are not secure. Anything at or below the following shouldn't be used: | |
| − | + | <nowiki>###</nowiki> AES-128 | |
| − | + | <nowiki>###</nowiki> Auth SHA256 | |
| − | + | <nowiki>###</nowiki> DH group - MODP3072 or ECP256 | |
| − | <br>[[File:HUB | + | <br>[[File:DMVP HUB phase3 example2.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step | + | <b>Step 3</b>: configure DMVPN Phase 2 parameters: |
| − | |||
| − | |||
| − | + | - Encryption algorithm - 3DES | |
| − | + | - Hash algorithm - MD5 | |
| − | + | - PFS group -MODP768 | |
| − | - | ||
| − | |||
| − | |||
| − | + | <nowiki>###</nowiki> Same story here, try to increase security level here to a more secure solution. | |
| − | + | <nowiki>###</nowiki> IPsec Phase 2 settings generally uses slightly lower parameters, because those algorithms are responsible for encrypting actual data traffic that we want to send over the IPsec tunnel | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 example3.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 4</b>: configure | + | <b>Step 4</b>: configure DMVPN NHRP parameters: |
| − | + | <nowiki>###</nowiki> Highlight the importance of "Redirect option here". This is essentially what makes P3 possible. | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 example4.png|border|class=tlt-border]] |
---- | ---- | ||
<b>Step 5</b>: save changes | <b>Step 5</b>: save changes | ||
| − | ===Hub configuration: BGP === | + | ===Hub configuration: BGP=== |
Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | ||
| − | <b>Step 1</b>: enable | + | <b>Step 1</b>: enable BGP and configure General section: |
| − | + | - Enable vty | |
| − | + | - Set AS to 65000 | |
| − | + | - Set announcement network(s). Routes to these networks will be shared over BGP. We used 192.168.1.0/24 | |
| − | + | <nowiki>###</nowiki> Highlight the fact that "NHRP routes" selection should exist under "Redistribution options" | |
| − | + | <nowiki>###</nowiki> Probably a good idea to set BGP router ID here using GRE interface IPs to avoid confusion and make troubleshooting easier | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 example5.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 2</b>: Create | + | <b>Step 2</b>: Create BGP Peer Group: |
| − | - Add | + | - Add Neighbor address (We used 10.0.0.1 and 10.0.0.2) |
| − | - | + | <nowiki>###</nowiki> Explanation needed what these IP addresses are - this might not be clear enough for end-users that this is spoke devices GRE IP address |
| − | <br>[[File: | + | <nowiki>###</nowiki> Also need to quickly mention about other settings |
| + | |||
| + | <nowiki>###</nowiki> Remote AS is empty here - I don't remember now, but is this intended? | ||
| + | |||
| + | <br>[[File:DMVPN HUB Phase3 example6.png|border|class=tlt-border]] | ||
---- | ---- | ||
| − | <b>Step 3</b>: Add two | + | <b>Step 3</b>: Add two BGP peers for each spoke: |
| − | + | <nowiki>###</nowiki> Need to mention that "Let's move on to spokes BGP configuration now.", because it looks a bit confusing | |
Peer 1. | Peer 1. | ||
| Line 139: | Line 143: | ||
- Set Remote address as 10.0.0.2 | - Set Remote address as 10.0.0.2 | ||
| − | + | <nowiki>###</nowiki> Briefly mention that other fields are not mandatory, but changes can be done if needed (aka "we will keep other settings as their default values for this configuration example" statement) | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 example7.png|border|class=tlt-border]] |
---- | ---- | ||
| − | [[File: | + | [[File:DMVPN HUB Phase3 example8.png|border|class=tlt-border]] |
---- | ---- | ||
| − | === Spoke 1 configuration: DMVPN=== | + | ===Spoke 1 configuration: DMVPN=== |
---- | ---- | ||
| + | <nowiki>###</nowiki> I think this should be done before dynamic routing configuration on each spoke, just to have IPsec tunnel and GRE IPs set for us | ||
| Line 155: | Line 160: | ||
<b>Step 1</b>: create a new DMVPN instance: | <b>Step 1</b>: create a new DMVPN instance: | ||
| − | + | <nowiki>###</nowiki> I recommend to explain each step here in detail, for example: | |
| − | + | - Add HUB address ### - this is the public IP address of previously configured hub device | |
| − | + | - Select Tunnel source ### - this is the egress interface, which will be able to reach hub device's public IP address over the internet | |
| − | + | - Add Local GRE interface IP address ### - this is the GRE IP address of "Spoke 1". It should be unique in the entire VPN network | |
| − | + | - Add Remote GRE interface IP address ### - this is the GRE IP address of the previously configured hub device | |
| − | + | - Set GRE MTU ### - this value should be set to the same value that was configured on the hub device. In our case, it is "1400" | |
| − | <br>[[File: | + | - Set Local identifier, Remote identifier as %any and input same Pre-shared key ### brief explanation why this is needed would be nice as well |
| + | |||
| + | <br>[[File:DMVPN HUB Phase3 spoke1 example1.png|border|class=tlt-border]] | ||
---- | ---- | ||
| − | <b>Step 2</b>: configure | + | <b>Step 2</b>: configure DMVPN Phase 1 parameters: |
| − | + | - Select Encryption algorithm - AES 128 | |
| − | + | - Select Authentication SHA1 | |
| − | + | - Select DH group MODP1024 | |
| − | <br>[[File: | + | |
| + | <nowiki>###</nowiki> Same comment from hub section applies, increase security level | ||
| + | |||
| + | <br>[[File:DMVPN HUB Phase3 spoke example2.png|border|class=tlt-border]] | ||
---- | ---- | ||
| − | <b>Step 3</b>: configure | + | <b>Step 3</b>: configure DMVPN Phase 2 parameters: |
| + | |||
| + | - Select Encryption algorithm 3DES | ||
| + | |||
| + | - Select Hash algorithm MD5 | ||
| − | + | - Select PFS group MODP768 | |
| − | |||
| − | + | <nowiki>###</nowiki> Same comment from hub section applies, increase security level | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 spoke example3.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 4</b>: configure | + | <b>Step 4</b>: configure DMVPN NHRP parameters: |
| − | |||
| − | |||
- Leave everything by default | - Leave everything by default | ||
| − | <br>[[File: | + | <nowiki>###</nowiki> Once again, highlight importance of "Redirect" option here<br>[[File:DMVPN HUB Phase3 spoke example4.png|border|class=tlt-border]] |
---- | ---- | ||
<b>Step 5</b>: save changes | <b>Step 5</b>: save changes | ||
| − | ===Spoke 1 configuration: BGP === | + | ===Spoke 1 configuration: BGP=== |
Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | ||
| − | <b>Step 1</b>: enable | + | <b>Step 1</b>: enable BGP and configure General section: |
| − | + | - Enable vty | |
| − | + | - Set AS to 65001 | |
| − | + | - Set Network to 192.168.10.0/24 | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 spoke example5.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 2</b>: Create | + | <b>Step 2</b>: Create BGP Peer: |
- Set Remote AS to 65000 | - Set Remote AS to 65000 | ||
| − | - Set | + | - Set Remote address to 10.0.0.254 |
| − | - | + | <br>[[File:DMVPN HUB Phase3 spoke example6.png|border|class=tlt-border]] |
| − | + | ===Spoke 2 configuration: DMVPN=== | |
| − | + | <nowiki>###</nowiki> Same points and comments apply here just as it was in Spoke 1 config section | |
Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | ||
| − | <b>Step 1</b>: create a new DMVPN instance: | + | <b>Step 1</b>: create a new DMVPN instance: |
| − | + | - Input your HUB address | |
| − | + | - Select Tunnel source interface | |
| − | + | - Set Local GRE interface address to 10.0.0.2 | |
| − | + | - Set Remote GRE interface IP address to 10.0.0.254 | |
| − | + | - Set GRE MTU to 1476 | |
| − | + | <br>[[File:DMVPN HUB Phase3 spoke2 example1.png|border|class=tlt-border]] | |
| − | |||
| − | <br>[[File: | ||
---- | ---- | ||
| − | <b>Step 2</b>: configure | + | <b>Step 2</b>: configure DMVPN Phase 1 parameters: |
| − | + | - Select Encryption algorithm - AES 128 | |
| − | + | - Select Authentication SHA1 | |
| − | + | - Select DH group MODP1024 | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 spoke2 example2.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 3</b>: configure | + | <b>Step 3</b>: configure DMVPN Phase 2 parameters: |
| − | + | - Select Encryption algorithm 3DES | |
| − | + | - Select Hash algorithm MD5 | |
| − | + | - Select PFS group MODP768 | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 spoke2 example3.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 4</b>: configure | + | <b>Step 4</b>: configure DMVPN NHRP parameters: |
| − | + | <br>[[File:DMVPN HUB Phase3 spoke2 example4.png|border|class=tlt-border]] | |
| − | |||
| − | |||
| − | |||
| − | <br>[[File: | ||
---- | ---- | ||
<b>Step 5</b>: save changes | <b>Step 5</b>: save changes | ||
| − | ===Spoke 2 configuration: BGP === | + | ===Spoke 2 configuration: BGP=== |
Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | Navigate to the <b>Network → Routing → Dynamic Routes → BGP Protocol</b> page and follow the instructions provided below. | ||
| − | <b>Step 1</b>: enable | + | <b>Step 1</b>: enable BGP and configure General section: |
| − | + | - Enable vty | |
| − | + | - Set AS to 65002 | |
| − | + | - Set Network to 192.168.20.0/24 | |
| − | <br>[[File: | + | <br>[[File:DMVPN HUB Phase3 spoke2 example5.png|border|class=tlt-border]] |
---- | ---- | ||
| − | <b>Step 2</b>: Create | + | <b>Step 2</b>: Create BGP Peer: |
- Set Remote AS to 65000 | - Set Remote AS to 65000 | ||
| Line 307: | Line 312: | ||
- Set Remote address to 10.0.0.254 | - Set Remote address to 10.0.0.254 | ||
| − | - | + | <br>[[File:DMVPN HUB Phase3 spoke2 example6.png|border|class=tlt-border]] |
| − | |||
| − | |||
| − | |||
===Important Note=== | ===Important Note=== | ||
| − | |||
| − | + | <nowiki>###</nowiki> Explanation why this is needed is recommended, because naturally a question comes to mind "why" this is needed | |
| − | + | For HUB in Network > Firewall GRE zone change from REJECT to ACCEPT on FORWARD. | |
| − | = | + | ---- |
| + | [[File:DMVPN HUB Phase3 example Firewall.png|border|class=tlt-border]] | ||
| + | ---- | ||
| − | |||
| − | + | For setups behind NAT specify Local identifier in the <b>Services → VPN → DMVPN → IPsec section </b> | |
| − | + | <nowiki>###</nowiki> Didn't we already set this during spoke configuration? It's a good point to mention/explain, but I don't think this should be at the bottom of the article, but instead should be next to IPsec config of each spoke | |
| − | + | ---- | |
| − | + | [[File:DMVPN HUB Phase3 example Behind NAT.png|border|class=tlt-border]] | |
| − | - | ||
| − | |||
| − | [[File: | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | <nowiki>###</nowiki> Need to show working configuration with pings or something. Also to verify that Phase 3 DMVPN condition is actually working. | |
Revision as of 09:43, 11 January 2023
Main Page > General Information > Configuration Examples > VPN > DMVPN with IPsec Phase 3Introduction
DMVPN (Dynamic Multipoint Virtual Private Network) is a dynamic tunneling form of a virtual private network capable of creating a VPN network without having pre-configure all possible tunnel end-point peers. DMVPN is initially configured to build out a HUB and SPOKE network, where each new SPOKE can join the network with minimal effort. The main benefits of DMVPN would be that it simplifies router configuration, has high scalability, good performance with better bandwidth, and secure routing when used in combination with IPsec.
DMVPN has three phases that route data differently:
Phase 1: All traffic flows from the spoke to and through the hub.
Phase 2: Start with Phase 1 then allows spoke-to-spoke tunnels based on demand and triggers. Phase 2 has different routing, where packet forwarding is being done using the IP routing table.
Phase 3: Starts with Phase 1 and improves the scalability and has fewer restrictions than Phase 2. Phase 3 allows the summarization of routes from hub to spokes. So again spokes wouldn’t need specific routes to other spokes networks.
This article contains instructions on how to configure DMVPN Phase 3 between a "Hub" and two "Spokes" using Teltonika devices.
Prerequisites and overview
You will need:
- 2 Teltonika Routers for SPOKES
- 1 Teltonika Router for HUB with a public IP address
- A PC to configure the routers
HUB configuration
This section contains information on how to configure DMVPN HUB. Firstly, we'll configure the DMVPN instance to make the connection possible. Then we'll set the Border Gateway Protocol (BGP) parameters as our dynamic routing solution.
Note: at the moment, BGP is the only stable dynamic routing solution that can work with DMVPN.
HUB configuration: DMVPN
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
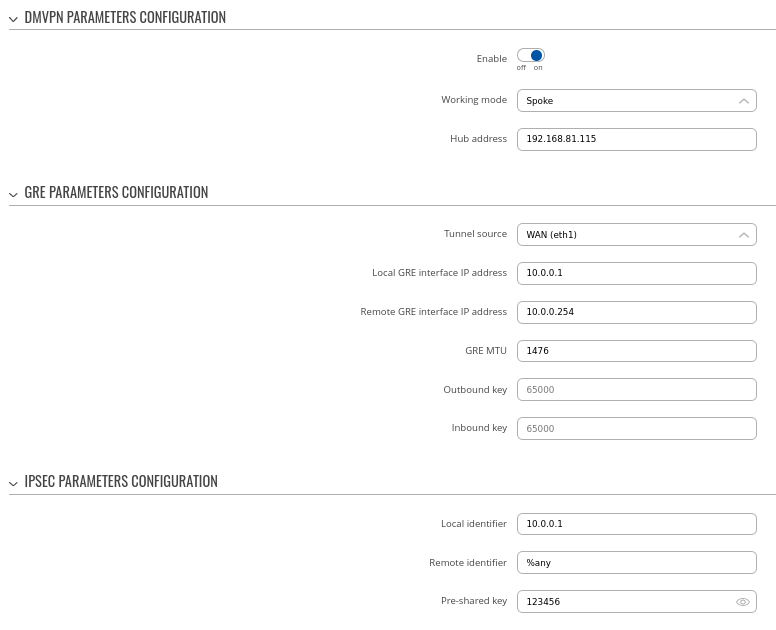
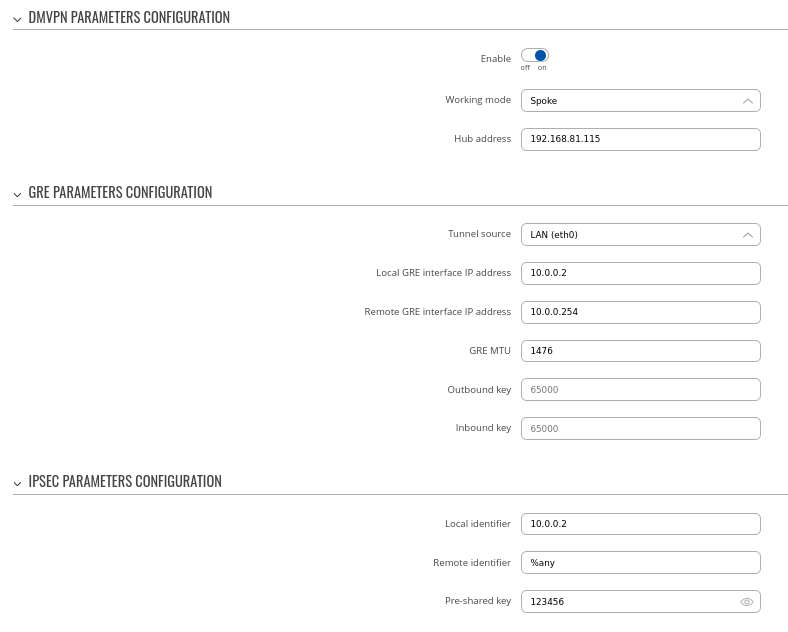
Step 1: create a new DMVPN instance:
- Select your HUB interface in the Tunnel source field
- Set Local GRE interface IP address (for example, 10.0.0.254)
- Set GRE interface netmask to 255.255.255.0 (for entire subnet or according to how many spokes we expect to connect to this hub)
- Set GRE MTU value to 1420 (or even slightly lower - 1400 if a mobile interface is used)
- Outbound/inbound keys are optional, for this example we will leave it at default
- Set IPsec Pre-shared key (we used simple 123456 for this example)
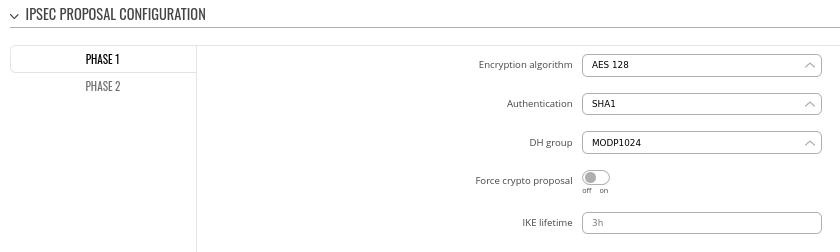
Step 2: configure DMVPN Phase 1 parameters:
- Encryption algorithm - AES 128
- Authentication SHA1
- DH group - MODP1024
### I don't recommend these parameters, they are not secure. Anything at or below the following shouldn't be used:
### AES-128
### Auth SHA256
### DH group - MODP3072 or ECP256
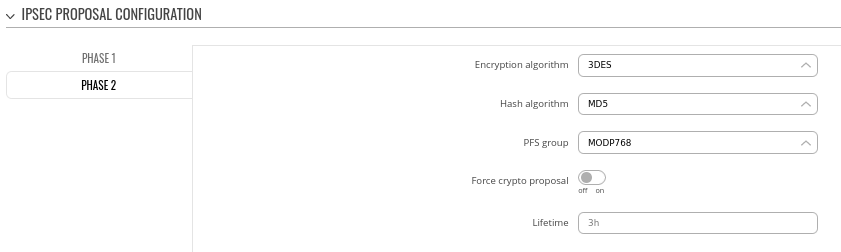
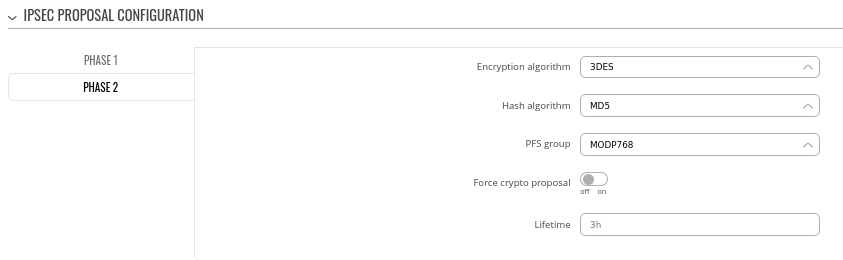
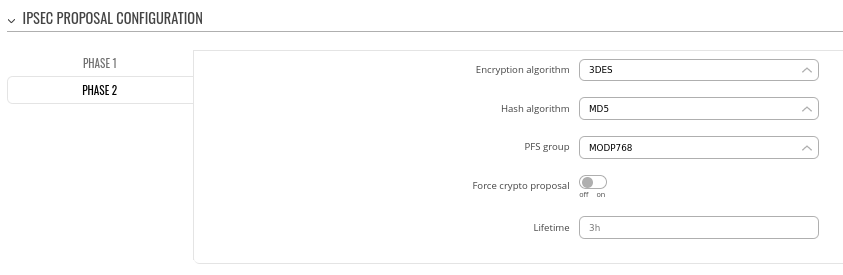
Step 3: configure DMVPN Phase 2 parameters:
- Encryption algorithm - 3DES
- Hash algorithm - MD5
- PFS group -MODP768
### Same story here, try to increase security level here to a more secure solution.
### IPsec Phase 2 settings generally uses slightly lower parameters, because those algorithms are responsible for encrypting actual data traffic that we want to send over the IPsec tunnel
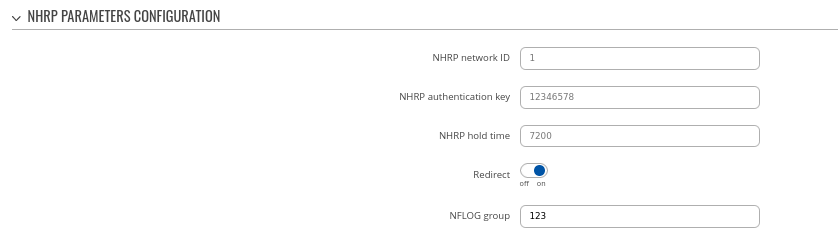
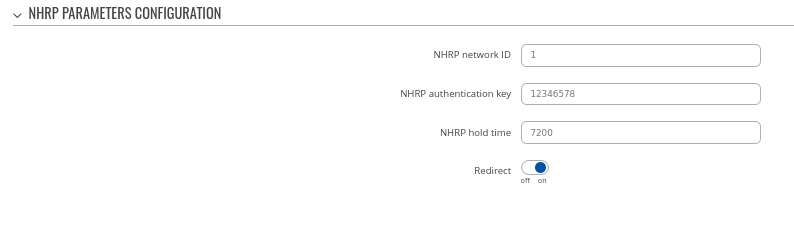
Step 4: configure DMVPN NHRP parameters:
### Highlight the importance of "Redirect option here". This is essentially what makes P3 possible.
Step 5: save changes
Hub configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
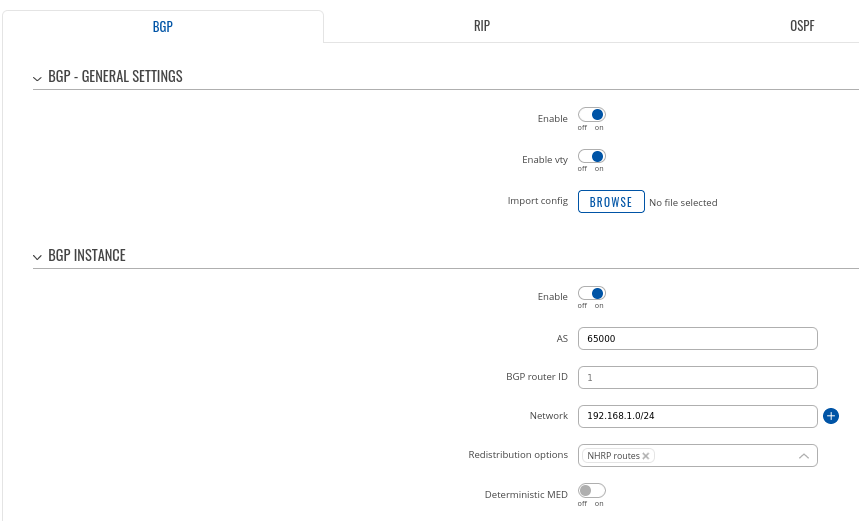
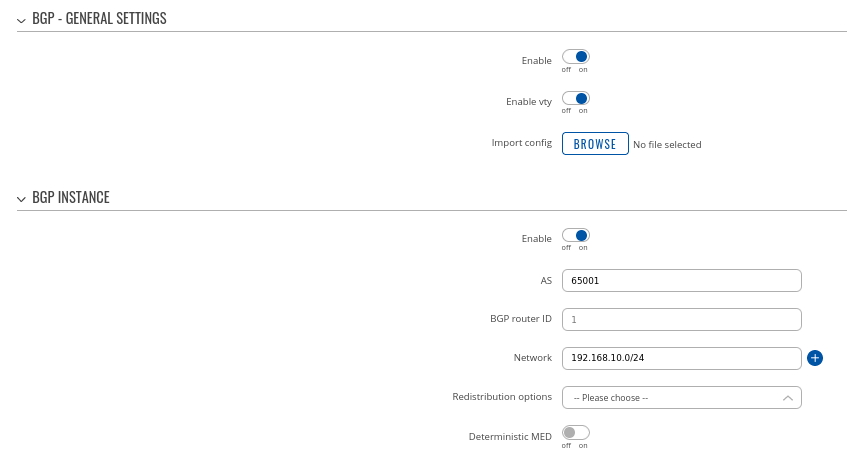
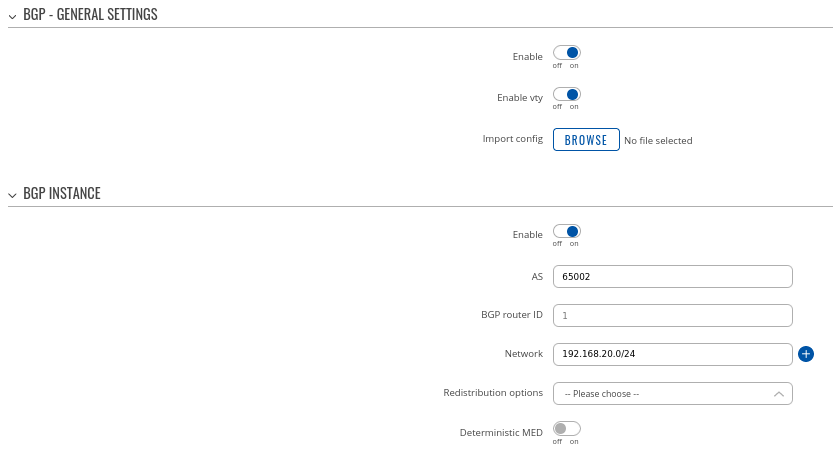
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65000
- Set announcement network(s). Routes to these networks will be shared over BGP. We used 192.168.1.0/24
### Highlight the fact that "NHRP routes" selection should exist under "Redistribution options"
### Probably a good idea to set BGP router ID here using GRE interface IPs to avoid confusion and make troubleshooting easier
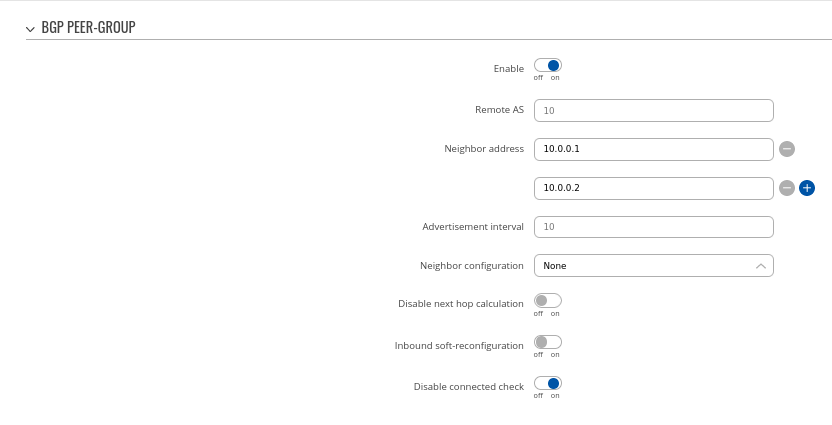
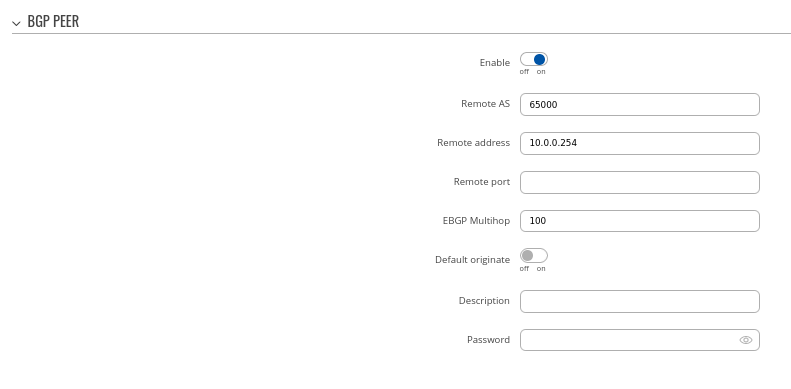
Step 2: Create BGP Peer Group:
- Add Neighbor address (We used 10.0.0.1 and 10.0.0.2)
### Explanation needed what these IP addresses are - this might not be clear enough for end-users that this is spoke devices GRE IP address
### Also need to quickly mention about other settings
### Remote AS is empty here - I don't remember now, but is this intended?
Step 3: Add two BGP peers for each spoke:
### Need to mention that "Let's move on to spokes BGP configuration now.", because it looks a bit confusing
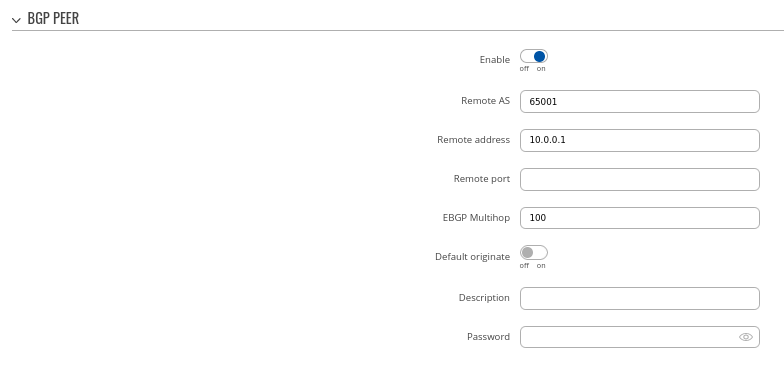
Peer 1.
- Set Remote AS to 65001
- Set Remote address as 10.0.0.1
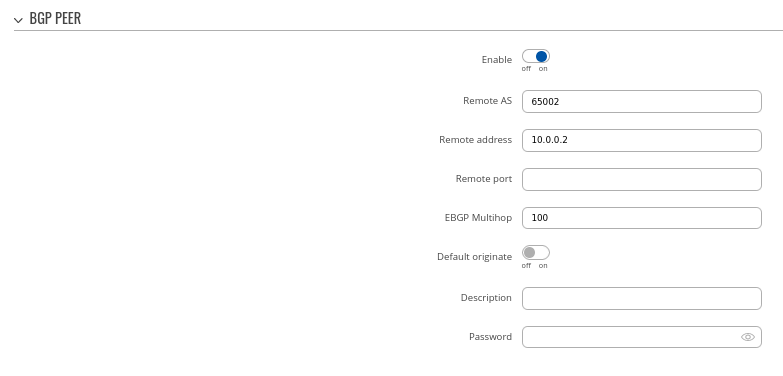
Peer 2.
- Set Remote AS to 65002
- Set Remote address as 10.0.0.2
### Briefly mention that other fields are not mandatory, but changes can be done if needed (aka "we will keep other settings as their default values for this configuration example" statement)
Spoke 1 configuration: DMVPN
### I think this should be done before dynamic routing configuration on each spoke, just to have IPsec tunnel and GRE IPs set for us
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
Step 1: create a new DMVPN instance:
### I recommend to explain each step here in detail, for example:
- Add HUB address ### - this is the public IP address of previously configured hub device
- Select Tunnel source ### - this is the egress interface, which will be able to reach hub device's public IP address over the internet
- Add Local GRE interface IP address ### - this is the GRE IP address of "Spoke 1". It should be unique in the entire VPN network
- Add Remote GRE interface IP address ### - this is the GRE IP address of the previously configured hub device
- Set GRE MTU ### - this value should be set to the same value that was configured on the hub device. In our case, it is "1400"
- Set Local identifier, Remote identifier as %any and input same Pre-shared key ### brief explanation why this is needed would be nice as well
Step 2: configure DMVPN Phase 1 parameters:
- Select Encryption algorithm - AES 128
- Select Authentication SHA1
- Select DH group MODP1024
### Same comment from hub section applies, increase security level
Step 3: configure DMVPN Phase 2 parameters:
- Select Encryption algorithm 3DES
- Select Hash algorithm MD5
- Select PFS group MODP768
### Same comment from hub section applies, increase security level
Step 4: configure DMVPN NHRP parameters:
- Leave everything by default
### Once again, highlight importance of "Redirect" option here
Step 5: save changes
Spoke 1 configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65001
- Set Network to 192.168.10.0/24
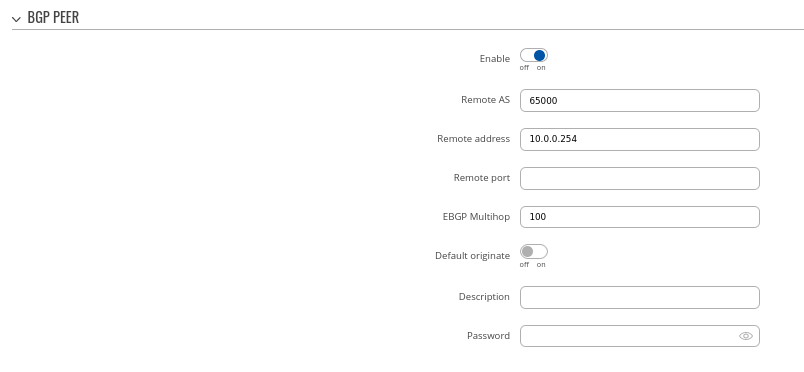
Step 2: Create BGP Peer:
- Set Remote AS to 65000
- Set Remote address to 10.0.0.254
Spoke 2 configuration: DMVPN
### Same points and comments apply here just as it was in Spoke 1 config section
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
Step 1: create a new DMVPN instance:
- Input your HUB address
- Select Tunnel source interface
- Set Local GRE interface address to 10.0.0.2
- Set Remote GRE interface IP address to 10.0.0.254
- Set GRE MTU to 1476
Step 2: configure DMVPN Phase 1 parameters:
- Select Encryption algorithm - AES 128
- Select Authentication SHA1
- Select DH group MODP1024
Step 3: configure DMVPN Phase 2 parameters:
- Select Encryption algorithm 3DES
- Select Hash algorithm MD5
- Select PFS group MODP768
Step 4: configure DMVPN NHRP parameters:
Step 5: save changes
Spoke 2 configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65002
- Set Network to 192.168.20.0/24
Step 2: Create BGP Peer:
- Set Remote AS to 65000
- Set Remote address to 10.0.0.254
Important Note
### Explanation why this is needed is recommended, because naturally a question comes to mind "why" this is needed
For HUB in Network > Firewall GRE zone change from REJECT to ACCEPT on FORWARD.
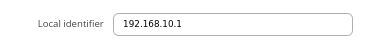
For setups behind NAT specify Local identifier in the Services → VPN → DMVPN → IPsec section
### Didn't we already set this during spoke configuration? It's a good point to mention/explain, but I don't think this should be at the bottom of the article, but instead should be next to IPsec config of each spoke
### Need to show working configuration with pings or something. Also to verify that Phase 3 DMVPN condition is actually working.