Difference between revisions of "DMVPN with IPsec Phase 3"
(Added comments. CTRL+F and search for "###" until no matches are found. Delete comments afterwards.) |
|||
| Line 2: | Line 2: | ||
This article contains instructions on how to configure DMVPN Phase 3 between a "Hub" and two "Spokes" using Teltonika devices. | This article contains instructions on how to configure DMVPN Phase 3 between a "Hub" and two "Spokes" using Teltonika devices. | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Some description about what is DMVPN and benefits of phase 3 would be nice to have here. Probably don't need much, but a summary about what it is should be here. | ||
| + | |||
| + | <nowiki>###</nowiki> Most notably how phase 3 is beneficial - would be great to have a comparison of phase 2 vs phase 3 | ||
==Prerequisites and overview== | ==Prerequisites and overview== | ||
| Line 12: | Line 17: | ||
<li>HUB must have a Public IP address</li> | <li>HUB must have a Public IP address</li> | ||
</ul> | </ul> | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Recommended to segment spokes and hub requirements here. At a minimum we will need 2 spokes to demonstrate this issue, and as a separate requirement, at least 1 hub with a public IP address. | ||
==HUB configuration== | ==HUB configuration== | ||
| Line 17: | Line 25: | ||
This section contains information on how to configure DMVPN <b>HUB</b>. Firstly, we'll configure the DMVPN instance to make the connection possible. Then we'll set the <b>Border Gateway Protocol</b> (<b>BGP</b>) parameters as our dynamic routing solution. | This section contains information on how to configure DMVPN <b>HUB</b>. Firstly, we'll configure the DMVPN instance to make the connection possible. Then we'll set the <b>Border Gateway Protocol</b> (<b>BGP</b>) parameters as our dynamic routing solution. | ||
| − | <b>Note</b>: at the moment, BGP is the only stable dynamic routing solution that can work with | + | <b>Note</b>: at the moment, BGP is the only stable dynamic routing solution that can work with DMVPN. |
===HUB configuration: DMVPN=== | ===HUB configuration: DMVPN=== | ||
| Line 28: | Line 36: | ||
- Set Local GRE interface IP address (for example, 10.0.0.254) | - Set Local GRE interface IP address (for example, 10.0.0.254) | ||
| + | |||
| + | <nowiki>###</nowiki> GRE netmask should be an entire subnet, /24 or however many spokes we expect to connect to this hub | ||
| + | |||
| + | <nowiki>###</nowiki> We can still use 10.0.0.254, but with a netmask of 255.255.255.0 for example | ||
- Set GRE MTU value to 1476 | - Set GRE MTU value to 1476 | ||
| − | - Set Pre-shared key (we used simple 123456 for this example) | + | <nowiki>###</nowiki> One note - if we use mobile, I recommend using lower MTU value, maybe 1420 or even lower, down to 1400 or so. I think using 1420 in this example would be better |
| + | |||
| + | <nowiki>###</nowiki> There have been situations when mobile MTU is not consistent, depending on carrier, which would break connections when packets had to be fragmented | ||
| + | |||
| + | <nowiki>###</nowiki> Outbound/inbound keys are optional, but worth to mention why they are here and what they are for | ||
| + | |||
| + | - Set IPsec Pre-shared key (we used simple 123456 for this example) | ||
<br>[[File:DMVP_HUB_phase3_example1.png|border|class=tlt-border]] | <br>[[File:DMVP_HUB_phase3_example1.png|border|class=tlt-border]] | ||
| Line 42: | Line 60: | ||
- DH group - MODP1024 | - DH group - MODP1024 | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> I don't recommend these parameters, they are not secure. Anything at or below the following shouldn't be used: | ||
| + | |||
| + | <nowiki>###</nowiki> AES-128 | ||
| + | |||
| + | <nowiki>###</nowiki> Auth SHA256 | ||
| + | |||
| + | <nowiki>###</nowiki> DH group - MODP3072 or ECP256 | ||
<br>[[File:DMVP HUB phase3 example2.png|border|class=tlt-border]] | <br>[[File:DMVP HUB phase3 example2.png|border|class=tlt-border]] | ||
| Line 52: | Line 79: | ||
- PFS group -MODP768 | - PFS group -MODP768 | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Same story here, try to increase security level here to a more secure solution. | ||
| + | |||
| + | <nowiki>###</nowiki> IPsec Phase 2 settings generally uses slightly lower parameters, because those algorithms are responsible for encrypting actual data traffic that we want to send over the IPsec tunnel | ||
<br>[[File:DMVPN HUB Phase3 example3.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 example3.png|border|class=tlt-border]] | ||
---- | ---- | ||
<b>Step 4</b>: configure DMVPN NHRP parameters: | <b>Step 4</b>: configure DMVPN NHRP parameters: | ||
| + | |||
| + | <nowiki>###</nowiki> Highlight the importance of "Redirect option here". This is essentially what makes P3 possible. | ||
<br>[[File:DMVPN HUB Phase3 example4.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 example4.png|border|class=tlt-border]] | ||
| Line 72: | Line 106: | ||
- Set announcement network(s). Routes to these networks will be shared over BGP. We used 192.168.1.0/24 | - Set announcement network(s). Routes to these networks will be shared over BGP. We used 192.168.1.0/24 | ||
| + | |||
| + | <nowiki>###</nowiki> Highlight the fact that "NHRP routes" selection should exist under "Redistribution options" | ||
| + | |||
| + | <nowiki>###</nowiki> Probably a good idea to set BGP router ID here using GRE interface IPs to avoid confusion and make troubleshooting easier | ||
<br>[[File:DMVPN HUB Phase3 example5.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 example5.png|border|class=tlt-border]] | ||
| Line 80: | Line 118: | ||
- Add Neighbor address (We used 10.0.0.1 and 10.0.0.2) | - Add Neighbor address (We used 10.0.0.1 and 10.0.0.2) | ||
| + | |||
| + | <nowiki>###</nowiki> Explanation needed what these IP addresses are - this might not be clear enough for end-users that this is spoke devices GRE IP address | ||
| + | |||
| + | <nowiki>###</nowiki> Also need to quickly mention about other settings | ||
| + | |||
| + | <nowiki>###</nowiki> Remote AS is empty here - I don't remember now, but is this intended? | ||
<br>[[File:DMVPN HUB Phase3 example6.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 example6.png|border|class=tlt-border]] | ||
| Line 86: | Line 130: | ||
<b>Step 3</b>: Add two BGP peers for each spoke: | <b>Step 3</b>: Add two BGP peers for each spoke: | ||
| + | |||
| + | <nowiki>###</nowiki> Need to mention that "Let's move on to spokes BGP configuration now.", because it looks a bit confusing | ||
Peer 1. | Peer 1. | ||
| Line 98: | Line 144: | ||
- Set Remote address as 10.0.0.2 | - Set Remote address as 10.0.0.2 | ||
| + | |||
| + | <nowiki>###</nowiki> Briefly mention that other fields are not mandatory, but changes can be done if needed (aka "we will keep other settings as their default values for this configuration example" statement) | ||
<br>[[File:DMVPN HUB Phase3 example7.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 example7.png|border|class=tlt-border]] | ||
| Line 107: | Line 155: | ||
===Spoke 1 configuration: DMVPN=== | ===Spoke 1 configuration: DMVPN=== | ||
---- | ---- | ||
| + | <nowiki>###</nowiki> I think this should be done before dynamic routing configuration on each spoke, just to have IPsec tunnel and GRE IPs set for us | ||
| + | |||
| + | |||
Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | ||
<b>Step 1</b>: create a new DMVPN instance: | <b>Step 1</b>: create a new DMVPN instance: | ||
| − | + | <nowiki>###</nowiki> I recommend to explain each step here in detail, for example: | |
| − | - | + | - Add HUB address ### - this is the public IP address of previously configured hub device |
| − | - | + | - Select Tunnel source ### - this is the egress interface, which will be able to reach hub device's public IP address over the internet |
| − | - Add | + | - Add Local GRE interface IP address ### - this is the GRE IP address of "Spoke 1". It should be unique in the entire VPN network |
| − | - | + | - Add Remote GRE interface IP address ### - this is the GRE IP address of the previously configured hub device |
| − | - Set Local identifier, Remote identifier as %any and input same Pre-shared key | + | - Set GRE MTU ### - this value should be set to the same value that was configured on the hub device. In our case, it is "1400" |
| + | |||
| + | - Set Local identifier, Remote identifier as %any and input same Pre-shared key ### brief explanation why this is needed would be nice as well | ||
<br>[[File:DMVPN HUB Phase3 spoke1 example1.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 spoke1 example1.png|border|class=tlt-border]] | ||
| Line 134: | Line 187: | ||
- Select DH group MODP1024 | - Select DH group MODP1024 | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Same comment from hub section applies, increase security level | ||
<br>[[File:DMVPN HUB Phase3 spoke example2.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 spoke example2.png|border|class=tlt-border]] | ||
| Line 146: | Line 202: | ||
- Select PFS group MODP768 | - Select PFS group MODP768 | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Same comment from hub section applies, increase security level | ||
<br>[[File:DMVPN HUB Phase3 spoke example3.png|border|class=tlt-border]] | <br>[[File:DMVPN HUB Phase3 spoke example3.png|border|class=tlt-border]] | ||
| Line 155: | Line 214: | ||
- Leave everything by default | - Leave everything by default | ||
| − | <br>[[File:DMVPN HUB Phase3 spoke example4.png|border|class=tlt-border]] | + | <nowiki>###</nowiki> Once again, highlight importance of "Redirect" option here<br>[[File:DMVPN HUB Phase3 spoke example4.png|border|class=tlt-border]] |
---- | ---- | ||
<b>Step 5</b>: save changes | <b>Step 5</b>: save changes | ||
| Line 184: | Line 243: | ||
===Spoke 2 configuration: DMVPN=== | ===Spoke 2 configuration: DMVPN=== | ||
| + | |||
| + | <nowiki>###</nowiki> Same points and comments apply here just as it was in Spoke 1 config section | ||
Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | Navigate to the <b>Services → VPN → DMVPN</b> page and follow the instructions provided below. | ||
| Line 256: | Line 317: | ||
===Important Note=== | ===Important Note=== | ||
| + | |||
| + | <nowiki>###</nowiki> Explanation why this is needed is recommended, because naturally a question comes to mind "why" this is needed | ||
For HUB in Network > Firewall GRE zone change from REJECT to ACCEPT on FORWARD. | For HUB in Network > Firewall GRE zone change from REJECT to ACCEPT on FORWARD. | ||
| Line 265: | Line 328: | ||
For setups behind NAT specify Local identifier in the <b>Services → VPN → DMVPN → IPsec section </b> | For setups behind NAT specify Local identifier in the <b>Services → VPN → DMVPN → IPsec section </b> | ||
| + | |||
| + | <nowiki>###</nowiki> Didn't we already set this during spoke configuration? It's a good point to mention/explain, but I don't think this should be at the bottom of the article, but instead should be next to IPsec config of each spoke | ||
---- | ---- | ||
[[File:DMVPN HUB Phase3 example Behind NAT.png|border|class=tlt-border]] | [[File:DMVPN HUB Phase3 example Behind NAT.png|border|class=tlt-border]] | ||
| + | |||
| + | |||
| + | <nowiki>###</nowiki> Need to show working configuration with pings or something. Also to verify that Phase 3 DMVPN condition is actually working. | ||
Revision as of 16:06, 10 January 2023
Main Page > General Information > Configuration Examples > VPN > DMVPN with IPsec Phase 3Introduction
This article contains instructions on how to configure DMVPN Phase 3 between a "Hub" and two "Spokes" using Teltonika devices.
### Some description about what is DMVPN and benefits of phase 3 would be nice to have here. Probably don't need much, but a summary about what it is should be here.
### Most notably how phase 3 is beneficial - would be great to have a comparison of phase 2 vs phase 3
Prerequisites and overview
You will need:
- 2 Teltonika Routers for "Spokes" and one for "Hub"
- A PC to configure the routers
- HUB must have a Public IP address
### Recommended to segment spokes and hub requirements here. At a minimum we will need 2 spokes to demonstrate this issue, and as a separate requirement, at least 1 hub with a public IP address.
HUB configuration
This section contains information on how to configure DMVPN HUB. Firstly, we'll configure the DMVPN instance to make the connection possible. Then we'll set the Border Gateway Protocol (BGP) parameters as our dynamic routing solution.
Note: at the moment, BGP is the only stable dynamic routing solution that can work with DMVPN.
HUB configuration: DMVPN
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
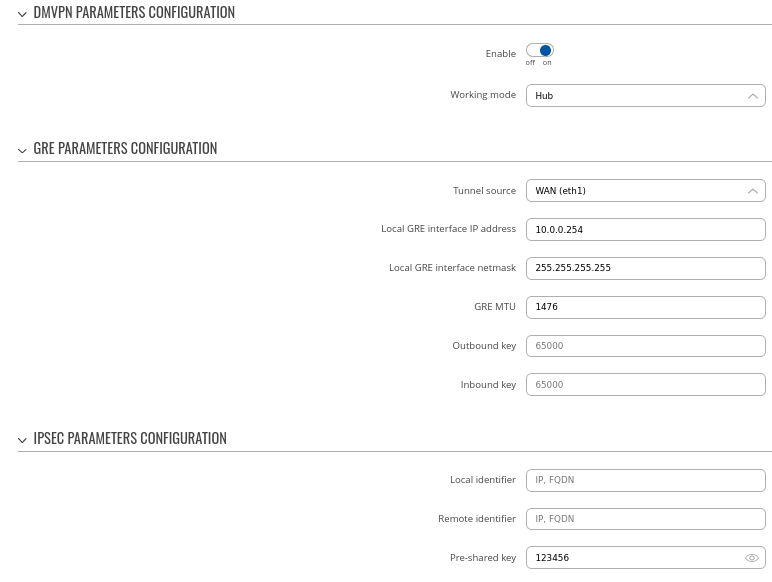
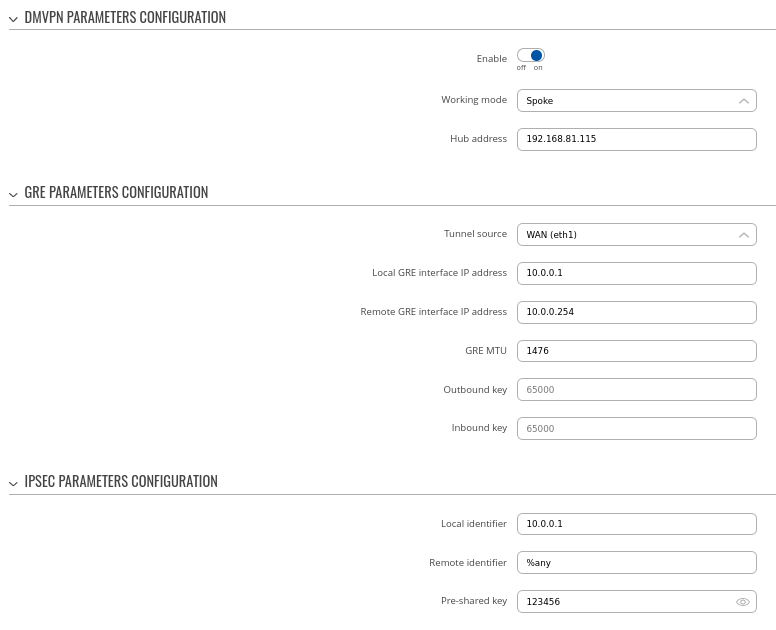
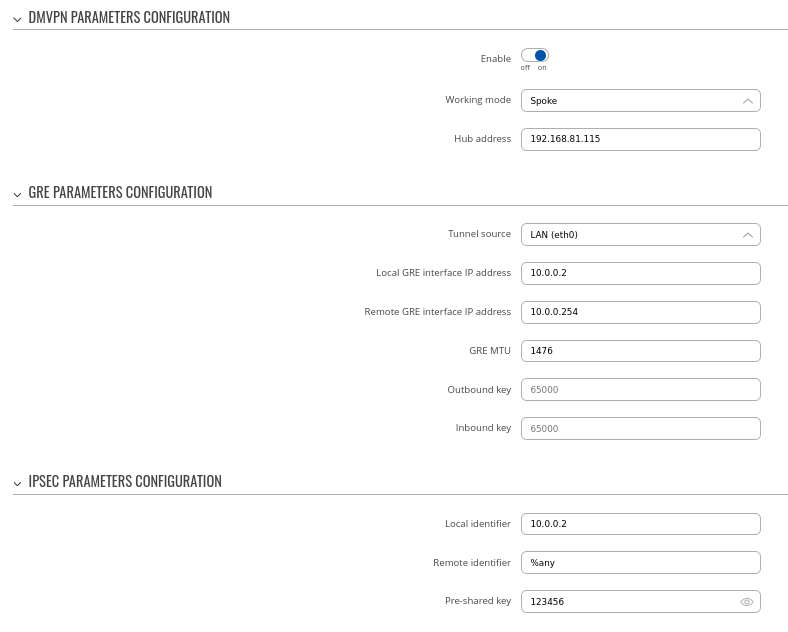
Step 1: create a new DMVPN instance:
- Select your HUB interface in the Tunnel source field
- Set Local GRE interface IP address (for example, 10.0.0.254)
### GRE netmask should be an entire subnet, /24 or however many spokes we expect to connect to this hub
### We can still use 10.0.0.254, but with a netmask of 255.255.255.0 for example
- Set GRE MTU value to 1476
### One note - if we use mobile, I recommend using lower MTU value, maybe 1420 or even lower, down to 1400 or so. I think using 1420 in this example would be better
### There have been situations when mobile MTU is not consistent, depending on carrier, which would break connections when packets had to be fragmented
### Outbound/inbound keys are optional, but worth to mention why they are here and what they are for
- Set IPsec Pre-shared key (we used simple 123456 for this example)
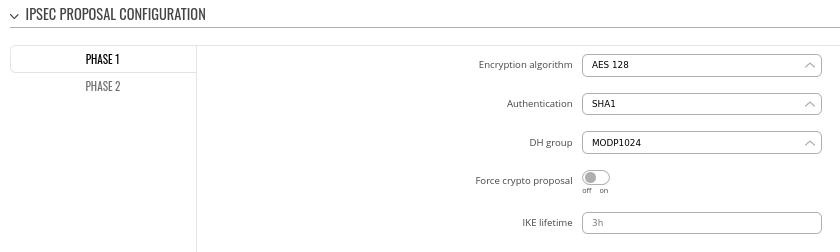
Step 2: configure DMVPN Phase 1 parameters:
- Encryption algorithm - AES 128
- Authentication SHA1
- DH group - MODP1024
### I don't recommend these parameters, they are not secure. Anything at or below the following shouldn't be used:
### AES-128
### Auth SHA256
### DH group - MODP3072 or ECP256
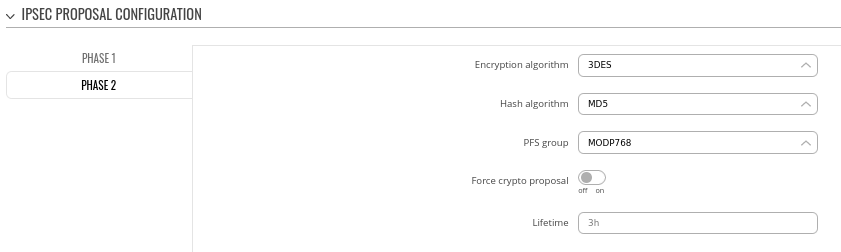
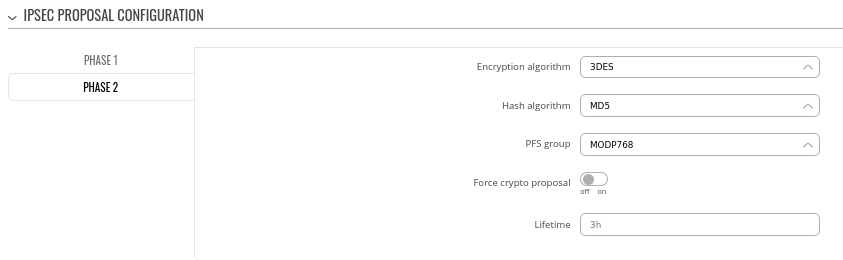
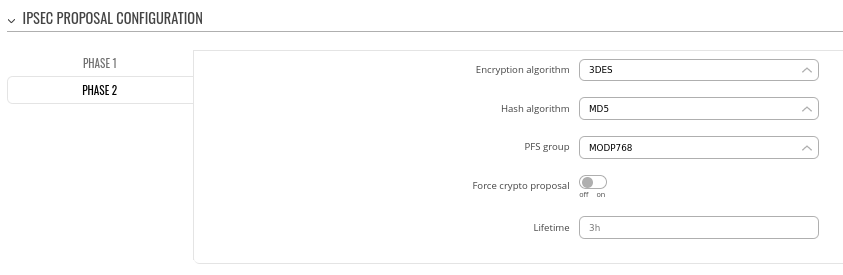
Step 3: configure DMVPN Phase 2 parameters:
- Encryption algorithm - 3DES
- Hash algorithm - MD5
- PFS group -MODP768
### Same story here, try to increase security level here to a more secure solution.
### IPsec Phase 2 settings generally uses slightly lower parameters, because those algorithms are responsible for encrypting actual data traffic that we want to send over the IPsec tunnel
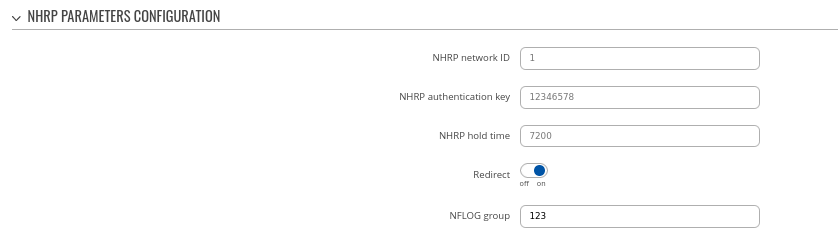
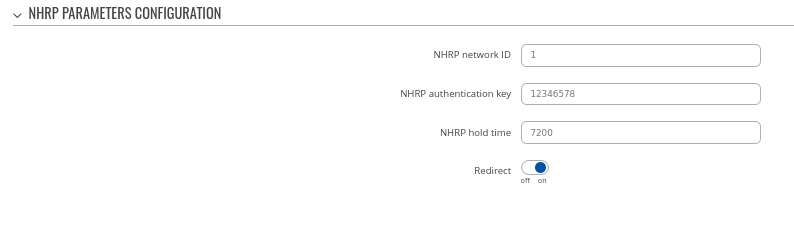
Step 4: configure DMVPN NHRP parameters:
### Highlight the importance of "Redirect option here". This is essentially what makes P3 possible.
Step 5: save changes
Hub configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
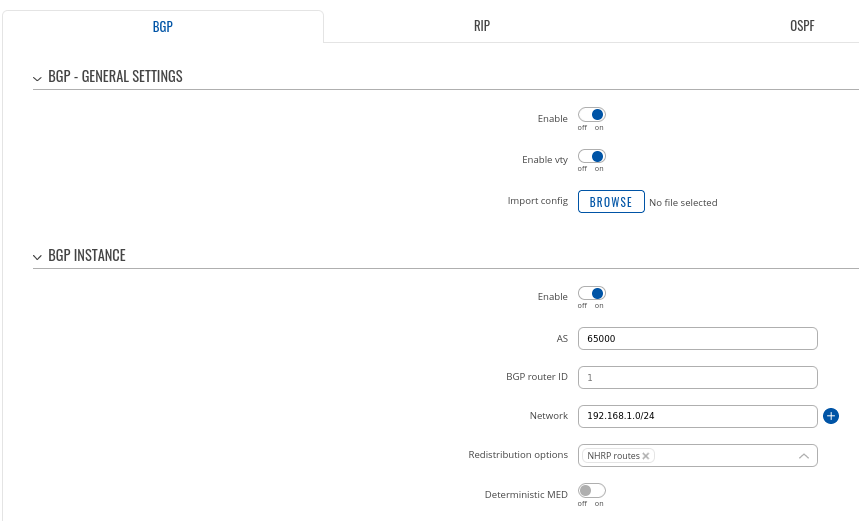
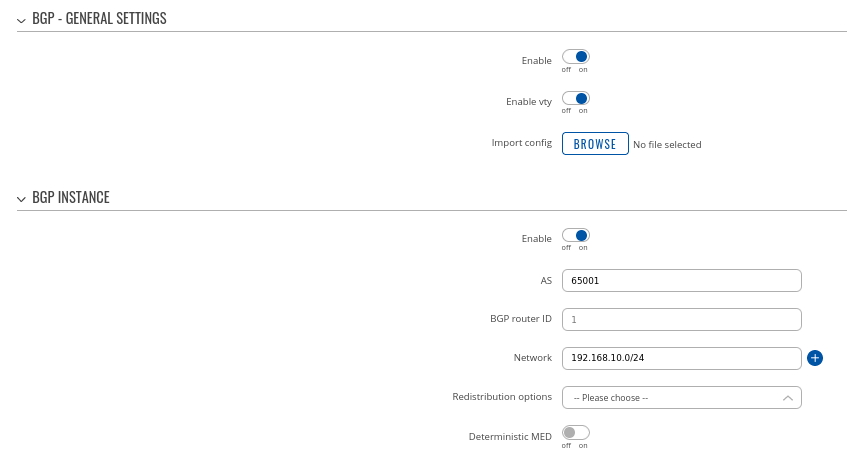
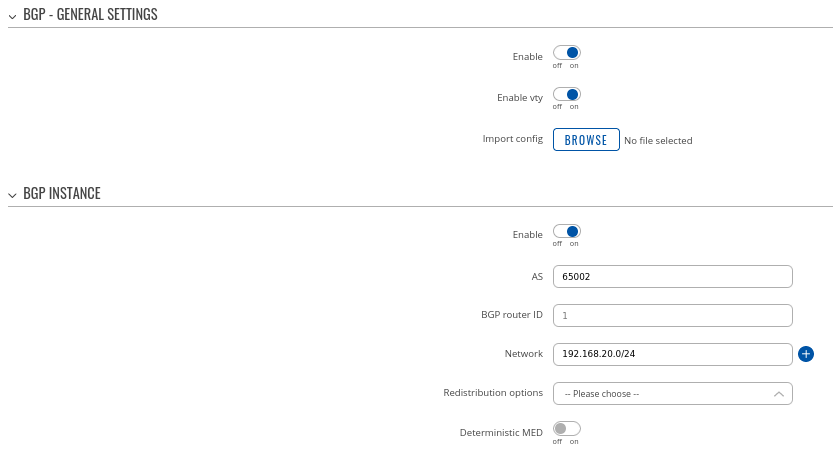
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65000
- Set announcement network(s). Routes to these networks will be shared over BGP. We used 192.168.1.0/24
### Highlight the fact that "NHRP routes" selection should exist under "Redistribution options"
### Probably a good idea to set BGP router ID here using GRE interface IPs to avoid confusion and make troubleshooting easier
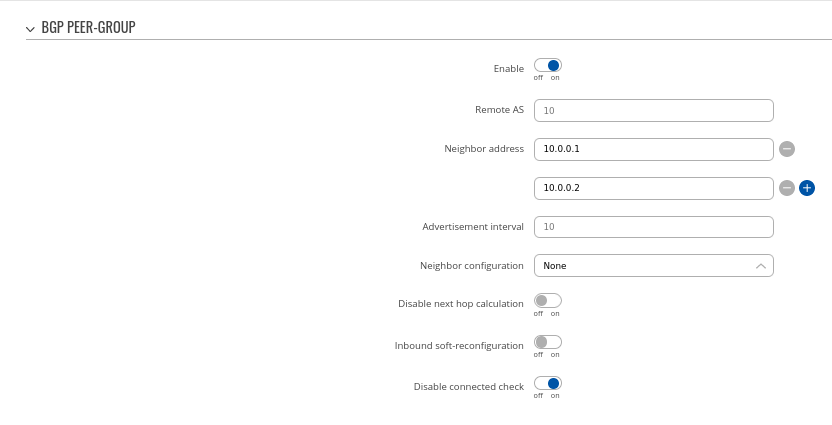
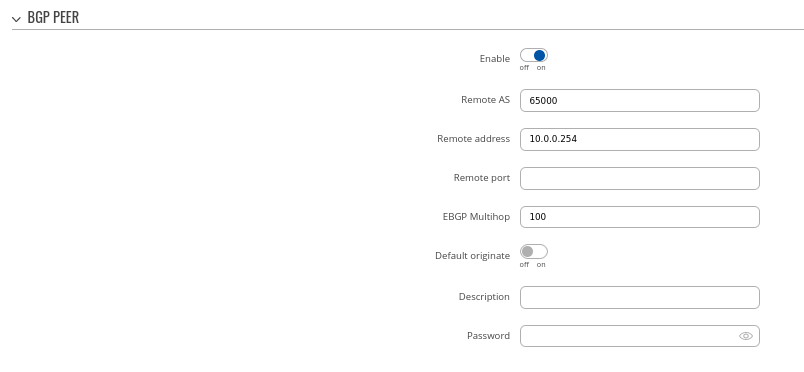
Step 2: Create BGP Peer Group:
- Add Neighbor address (We used 10.0.0.1 and 10.0.0.2)
### Explanation needed what these IP addresses are - this might not be clear enough for end-users that this is spoke devices GRE IP address
### Also need to quickly mention about other settings
### Remote AS is empty here - I don't remember now, but is this intended?
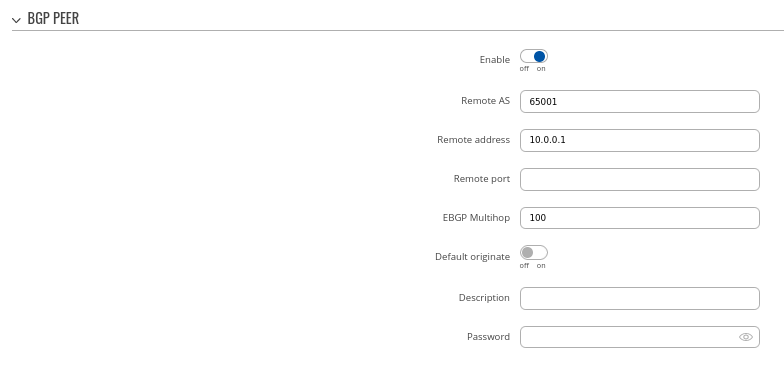
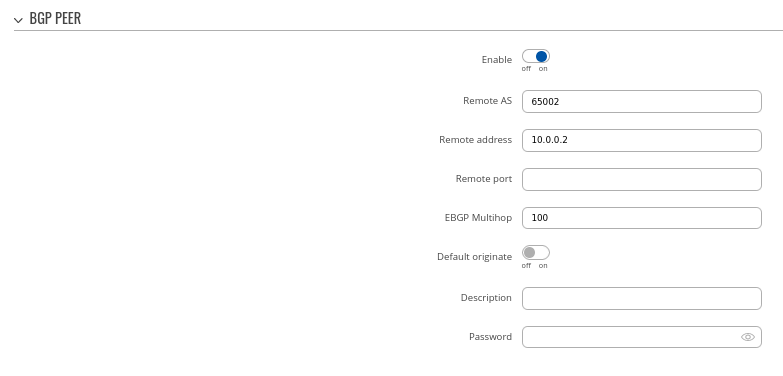
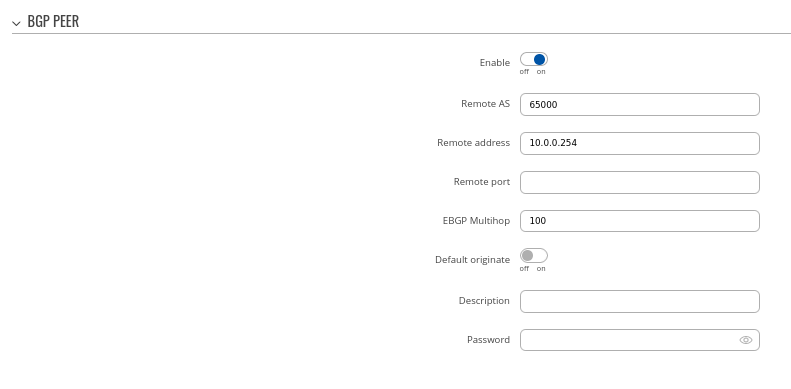
Step 3: Add two BGP peers for each spoke:
### Need to mention that "Let's move on to spokes BGP configuration now.", because it looks a bit confusing
Peer 1.
- Set Remote AS to 65001
- Set Remote address as 10.0.0.1
Peer 2.
- Set Remote AS to 65002
- Set Remote address as 10.0.0.2
### Briefly mention that other fields are not mandatory, but changes can be done if needed (aka "we will keep other settings as their default values for this configuration example" statement)
Spoke 1 configuration: DMVPN
### I think this should be done before dynamic routing configuration on each spoke, just to have IPsec tunnel and GRE IPs set for us
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
Step 1: create a new DMVPN instance:
### I recommend to explain each step here in detail, for example:
- Add HUB address ### - this is the public IP address of previously configured hub device
- Select Tunnel source ### - this is the egress interface, which will be able to reach hub device's public IP address over the internet
- Add Local GRE interface IP address ### - this is the GRE IP address of "Spoke 1". It should be unique in the entire VPN network
- Add Remote GRE interface IP address ### - this is the GRE IP address of the previously configured hub device
- Set GRE MTU ### - this value should be set to the same value that was configured on the hub device. In our case, it is "1400"
- Set Local identifier, Remote identifier as %any and input same Pre-shared key ### brief explanation why this is needed would be nice as well
Step 2: configure DMVPN Phase 1 parameters:
- Select Encryption algorithm - AES 128
- Select Authentication SHA1
- Select DH group MODP1024
### Same comment from hub section applies, increase security level
Step 3: configure DMVPN Phase 2 parameters:
- Select Encryption algorithm 3DES
- Select Hash algorithm MD5
- Select PFS group MODP768
### Same comment from hub section applies, increase security level
Step 4: configure DMVPN NHRP parameters:
- Leave everything by default
### Once again, highlight importance of "Redirect" option here
Step 5: save changes
Spoke 1 configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65001
- Set Network to 192.168.10.0/24
Step 2: Create BGP Peer:
- Set Remote AS to 65000
- Set Remote address to 10.0.0.254
Spoke 2 configuration: DMVPN
### Same points and comments apply here just as it was in Spoke 1 config section
Navigate to the Services → VPN → DMVPN page and follow the instructions provided below.
Step 1: create a new DMVPN instance:
- Input your HUB address
- Select Tunnel source interface
- Set Local GRE interface address to 10.0.0.2
- Set Remote GRE interface IP address to 10.0.0.254
- Set GRE MTU to 1476
Step 2: configure DMVPN Phase 1 parameters:
- Select Encryption algorithm - AES 128
- Select Authentication SHA1
- Select DH group MODP1024
Step 3: configure DMVPN Phase 2 parameters:
- Select Encryption algorithm 3DES
- Select Hash algorithm MD5
- Select PFS group MODP768
Step 4: configure DMVPN NHRP parameters:
Step 5: save changes
Spoke 2 configuration: BGP
Navigate to the Network → Routing → Dynamic Routes → BGP Protocol page and follow the instructions provided below.
Step 1: enable BGP and configure General section:
- Enable vty
- Set AS to 65002
- Set Network to 192.168.20.0/24
Step 2: Create BGP Peer:
- Set Remote AS to 65000
- Set Remote address to 10.0.0.254
Important Note
### Explanation why this is needed is recommended, because naturally a question comes to mind "why" this is needed
For HUB in Network > Firewall GRE zone change from REJECT to ACCEPT on FORWARD.
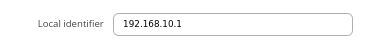
For setups behind NAT specify Local identifier in the Services → VPN → DMVPN → IPsec section
### Didn't we already set this during spoke configuration? It's a good point to mention/explain, but I don't think this should be at the bottom of the article, but instead should be next to IPsec config of each spoke
### Need to show working configuration with pings or something. Also to verify that Phase 3 DMVPN condition is actually working.