Difference between revisions of "OpenVPN traffic split"
| Line 11: | Line 11: | ||
'''Prerequisites''': | '''Prerequisites''': | ||
| − | * A single RUTxxx router (excluding [[RUT850]]) that will act as the OpenVPN client | + | * A single RUTxxx router (excluding [[RUT850]]) with an active internet connection that will act as the OpenVPN client |
* At least one end device (PC, Laptop) to configure the routers and test the set up | * At least one end device (PC, Laptop) to configure the routers and test the set up | ||
---- | ---- | ||
| Line 18: | Line 18: | ||
[[File:Openvpn traffic split configuration scheme demo.png]] | [[File:Openvpn traffic split configuration scheme demo.png]] | ||
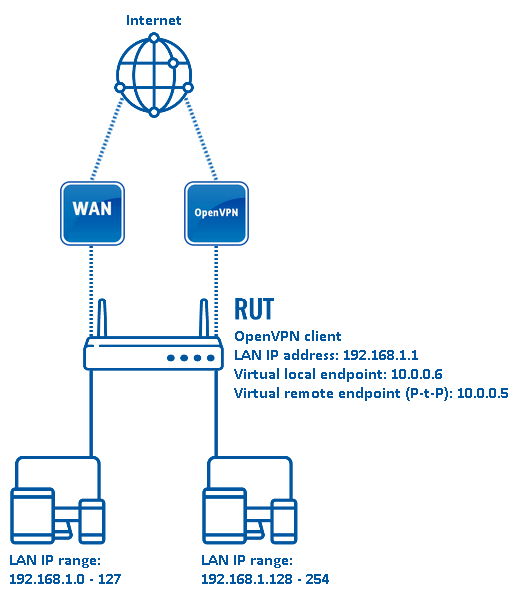
| − | The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client | + | The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client (virtual IP: '''10.0.0.6'''; P-t-P: '''10.0.0.5''') that is connected to a remote OpenVPN server. The routers LAN IP addresses range from 192.168.1.1 to 192.168.1.254. |
| − | When the scheme is realized, | + | When the scheme is realized, Devices in the 192.168.1.1 to 192.168.1.127 IP range reach the Internet via the router's WAN and devices in the 192.168.1.128 to 192.168.1.254 IP range reach the Internet via the OpenVPN server effectively "adopting" the server's Public IP address. |
Revision as of 09:19, 14 June 2018
Main Page > General Information > Configuration Examples > VPN > OpenVPN traffic splitIntroduction
OpenVPN is an open-source software application that implements virtual private network (VPN) techniques for creating secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities.
This article provides a guide on how to configure an OpenVPN client on a RUTxxx router in such a way that a part of the router's LAN clients reach the Internet through the OpenVPN server (web proxy) and the other part reaches the Internet through the router's WAN (mobile, wired or WiFi connection). It should also be noted that this guide is aimed at more advanced users and, therefore, skips some of the more self-explanatory steps in order to preserve the overall coherence of the article. For example, the step-by-step configuration of the OpenVPN client instance will be left out and only comments on certain relevant parameters will be provided. If you feel this lack of information impedes your ability to configure the setup, we suggest you check out our configuration guides on how to generate TLS sertificates and OpenVPN configuration examples for reference.
Configuration overview and prerequisites
Before we begin, let's overview the configuration that we are attempting to achieve and the prerequisites that make it possible.
Prerequisites:
- A single RUTxxx router (excluding RUT850) with an active internet connection that will act as the OpenVPN client
- At least one end device (PC, Laptop) to configure the routers and test the set up
Configuration scheme:
The figure above depicts the OpenVPN traffic split scheme. A RUTxxx router acts as an OpenVPN client (virtual IP: 10.0.0.6; P-t-P: 10.0.0.5) that is connected to a remote OpenVPN server. The routers LAN IP addresses range from 192.168.1.1 to 192.168.1.254.
When the scheme is realized, Devices in the 192.168.1.1 to 192.168.1.127 IP range reach the Internet via the router's WAN and devices in the 192.168.1.128 to 192.168.1.254 IP range reach the Internet via the OpenVPN server effectively "adopting" the server's Public IP address.