Difference between revisions of "L2 LAN bridging over internet using L2TPv2+EoIP"
| Line 44: | Line 44: | ||
Now we will add a new Firewall rule GRE Accept, for that you will need to execute these commands each one at a time(keep in mind that each command has to be executed in the order that has been provided below): | Now we will add a new Firewall rule GRE Accept, for that you will need to execute these commands each one at a time(keep in mind that each command has to be executed in the order that has been provided below): | ||
| − | uci add firewall rule | + | ''uci add firewall rule |
| + | |||
uci set firewall.@rule[-1].name=GRE | uci set firewall.@rule[-1].name=GRE | ||
| + | |||
uci set firewall.@rule[-1].target=ACCEPT | uci set firewall.@rule[-1].target=ACCEPT | ||
| + | |||
uci set firewall.@rule[-1].priority=14 | uci set firewall.@rule[-1].priority=14 | ||
| + | |||
uci set firewall.@rule[-1].src=l2tp | uci set firewall.@rule[-1].src=l2tp | ||
| + | |||
uci set firewall.@rule[-1].enabled=1 | uci set firewall.@rule[-1].enabled=1 | ||
| + | |||
uci set firewall.@rule[-1].proto=47 | uci set firewall.@rule[-1].proto=47 | ||
| + | |||
uci set firewall.@rule[-1].utc_time=0 | uci set firewall.@rule[-1].utc_time=0 | ||
| − | uci commit firewall && service firewall restart | + | |
| + | uci commit firewall && service firewall restart'' | ||
Revision as of 14:34, 18 April 2023
Main Page > General Information > Configuration Examples > VPN > L2 LAN bridging over internet using L2TPv2+EoIPThe information on this page is updated in accordance with 00.07.03 firmware version.
Introduction
In this configuration example we will use L2TP with Ethernet over IP (EoIP) to bridge LAN interfaces between MikroTik and Teltonika devices. EoIP is a MikroTik RouterOS protocol based on GRE RFC 1701 that creates an Ethernet tunnel between two routers on top of an IP connection. The EoIP tunnel may run over the IPIP tunnel, PPTP tunnel, or any other connection capable of transporting IP.
Topology
Placeholder
Prerequisites
- MikroTik device(with L2TP and EoIP support) with Public IP (in this example we use hAP lite TC)
- Teltonika router or Gateway with Public IP (in this example we use RUTX11)
- Firmware with EoIP for Teltonika device
- A computer for testing and configuring the setup
Configuration of the Teltonika Device
From the Teltonika router, we will configure L2TP Client, EoIP, and firewall rules in order to achieve a working setup.
L2TP configuration
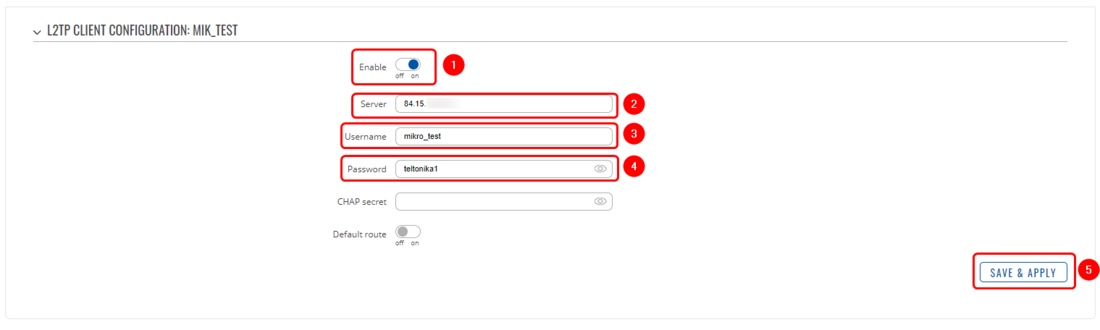
We will start by configuring the L2TP client. Open your device's WebUI and navigate to Services → VPN → L2TP, add a new L2TP client, once the configuration window opens, configure the client accordingly:
- Enable the configuration
- Server - input the MikroTik Public IP here
- Username - username configurated on MikroTik server
- Password - password configurated on MikroTik server 5.
- Save the configuration
Firewall configuration
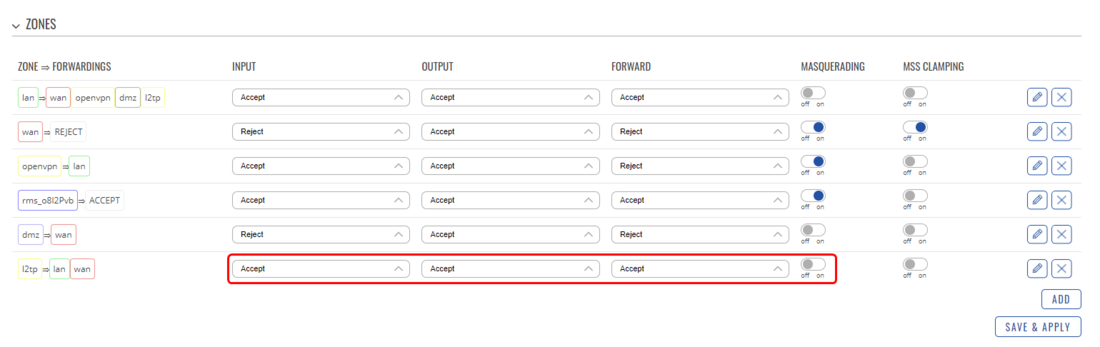
In order for our configuration to work, we will need to update the Firewall. Navigate to the Network → Firewall → General Settings in the Zones section and change the L2TP zone settings to INPUT: Accept; OUTPUT: Accept; FORWARD: Accept; and disable the Masquerading. Upon changing these settings the configuration window should look like this:
For the next part we will need access to the SSH/CLI of the device, we can reach device's CLI via System → CLI login with root username and password of your device.
Now we will add a new Firewall rule GRE Accept, for that you will need to execute these commands each one at a time(keep in mind that each command has to be executed in the order that has been provided below):
uci add firewall rule
uci set firewall.@rule[-1].name=GRE
uci set firewall.@rule[-1].target=ACCEPT
uci set firewall.@rule[-1].priority=14
uci set firewall.@rule[-1].src=l2tp
uci set firewall.@rule[-1].enabled=1
uci set firewall.@rule[-1].proto=47
uci set firewall.@rule[-1].utc_time=0
uci commit firewall && service firewall restart